As executives allocate an increasing amount of funds to security efforts, they want tangible evidence that their investment is worthwhile. However, this poses a challenge for security teams because when programs are successful, there’s often nothing to report, such as data breaches, email outages, loss of service, or locked out users. This makes it hard for security teams to demonstrate their effectiveness.

To make matters worse, many security teams may exacerbate the issue by using metrics that don’t provide executives with a thorough understanding of the work being done. Instead, by shifting reporting metrics to focus on response times, security teams can garner more program buy-in while improving their organization’s security overall.
Drawbacks of Commonly Used Metrics
There’s a fallacy with security program metrics that bigger numbers are better, and security teams often incorrectly focus their reporting on identifying the total numbers of weaknesses in systems, databases, and applications thinking it will influence decision makers to allocate greater resources for repair. However, the number of vulnerabilities found—no matter how great—don’t necessarily reflect the effectiveness of risk mitigation efforts, which is what matters most.
Teams also commonly share the number of vulnerabilities they’ve fixed—and the number still remaining. The problem with this is that new vulnerabilities emerge constantly, and often the number of new vulnerabilities matches or exceeds the number that a team has fixed, so the amount of work that the program has accomplished is misrepresented.
While those in the trenches understand that the introduction of new vulnerabilities doesn’t necessarily reflect the effectiveness or productivity of a security team, nontechnical decision makers will likely see a reported increase in vulnerabilities and conclude that the security team isn’t successfully reducing them. In response, security teams often see a loss of political capital and buy-in from the business.
Value of Time-Based Metrics
Since we know that security isn’t truly a zero-sum game, instead of focusing on the raw numbers or the volume of work being done, prioritize quickly addressing vulnerabilities as they’re discovered. The speed of attacks and compromises continues to increase as more computing resources become available to attackers, and strong defense-in-depth programs help in slowing down the attack chain and gives defenders more time to respond. How quickly your teams respond to threats is a powerful metric that can provide executives with a more realistic understanding of the progress of the security program’s efforts.
Here are some metrics—and targets to hit—that can demonstrate a team’s response speed.
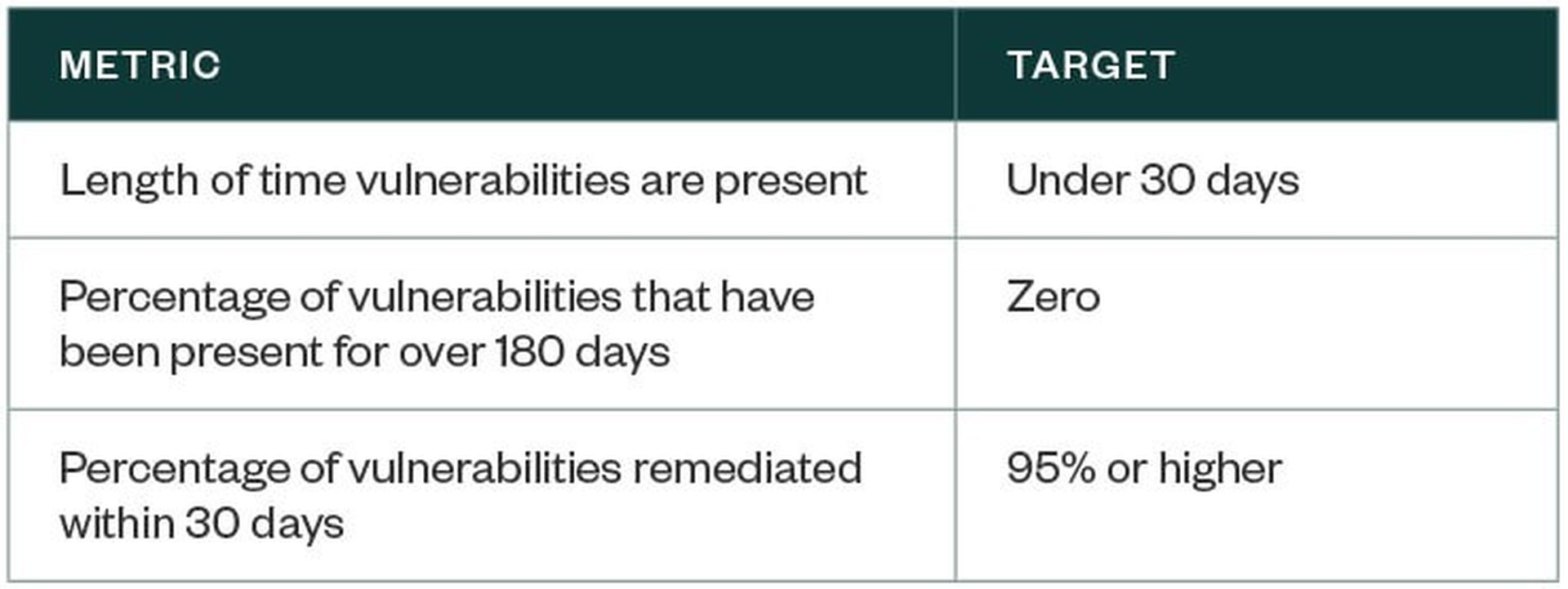
Additional Benefits
The challenge with using time-based metrics is that it requires detection and remediation efforts to occur on a near-constant basis—but that’s exactly what successful security programs must do, so a shift to this focus can improve an organization’s security overall. Faster responses to data breaches not only boost security but also help organizations comply with and prepare for regulations such as the General Data Protection Regulation (GDPR).
There’s evidence that organizations have significant room for improvement on the response time front—not just in terms of reporting but also in terms of program priorities. In 2016, FireEye released a report that referenced the global average as being 146 days. Likewise, in many organizations, vulnerabilities remain unpatched or unmitigated for months or even years, giving attackers ample opportunities to find and exploit those weaknesses.
Next Steps
Attackers move quickly, but by leveraging time-based metrics, teams can help contextualize the effectiveness and efficiency of security programs, generating the necessary support from management to bolster security efforts and stay ahead of the evolving risks posed by cyberthreats.
Kevin Villanueva has been in the information technology field since 1997. His areas of practice include IT security assessments, penetration testing, PCI Data Security Standard assessments, HIPAA compliance auditing, and strategic technology planning.



