Ransomware attacks now make up an huge chunk of all recorded security incidents, the Log4j vulnerability was used in 3 in 4 digital espionage campaigns and employees continue to pose more of a practical cyber threat to most organizations than the Russian GRU or Chinese Ministry of State Security.
Those are some of the conclusions gleaned from the latest annual Verizon Data Breach Investigations Report released this morning.
Verizon’s findings are drawn from 16,000 security incidents over the past year, including over 5,000 data breaches from Nov. 1, 2021 to Oct. 31, 2022.
A plurality of 15,000-plus incidents (42%) were distributed-denial-of-service (DDoS) attacks, which can disrupt service from or access to websites and other systems.
There are solid indicators that DDoS attacks are getting worse, or at least more intense, as the internet of things (IoT) give attackers billions of zombie devices to hijack and incorporate into botnets. Over the past two years, companies like Cloudflare and Yandex have observed increasingly larger and record-breaking DDoS attacks, while the U.S. Department of Justice recently highlighted its interest in the problem when it targeted and seized 13 domains used in various “DDoS for hire” operations earlier this year.
Ransomware holding steady
A number of threat intelligence and cybersecurity firms have said their internal data, gleaned from customers and incident responses, indicate that ransomware activity dropped off in 2022, before jumping back up in the first half of 2023. Verizon’s data shows a similar trend, with reported ransomware incidents plateauing over the past 24 months at 24%, after years of steady growth.
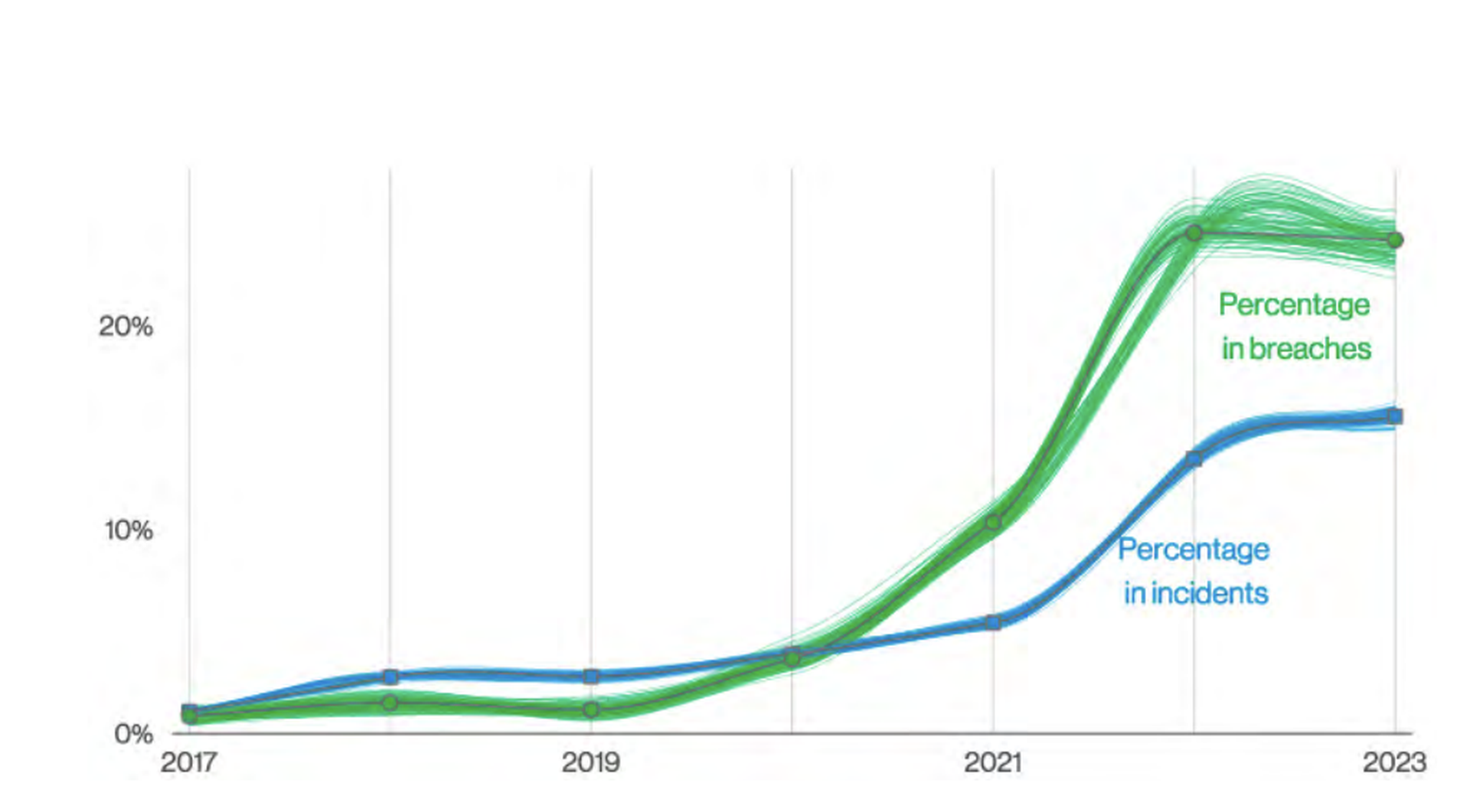
However, if someone does break into your system, the most likely cause will be ransomware. Encryption and extortion overall have risen to 15.5% of all reported cybersecurity incidents, the second most frequently reported action after DDoS. It’s also the No. 1 most-frequent action taken by hackers during system intrusion incidents.
These results are “staggering,” and Verizon’s report suggests we have yet to see rock bottom.
“[W]e had been anticipating that Ransomware would soon be hitting its theoretical ceiling, by which we mean that all the incidents that could have Ransomware, would have,” the authors wrote. “Ransomware is present today in more than 62% of all incidents committed by Organized crime actors and in 59% of all incidents with a Financial motivation, so sadly there is still some room for growth.”
The most common entry points into a victim system for ransomware attackers were through email, desktop applications and web applications.
Only a fraction (5%) of the breaches captured in the DBIR report involved exploiting security vulnerabilities in systems or devices.
Log4j: not as bad as feared, still impactful
When Log4j was first disclosed, federal agencies and threat intelligence companies sounded the alarm, not just because the bug was embedded in untold numbers of commercial systems and software, but also because they had observed early signs that cybercriminal groups and nation-states were racing to find vulnerable instances and exploit them before industry could identify and patch them.
That led to one of the largest coordination efforts ever done between government and the private sector around a vulnerability, and Verizon’s data validates some of those concerns.
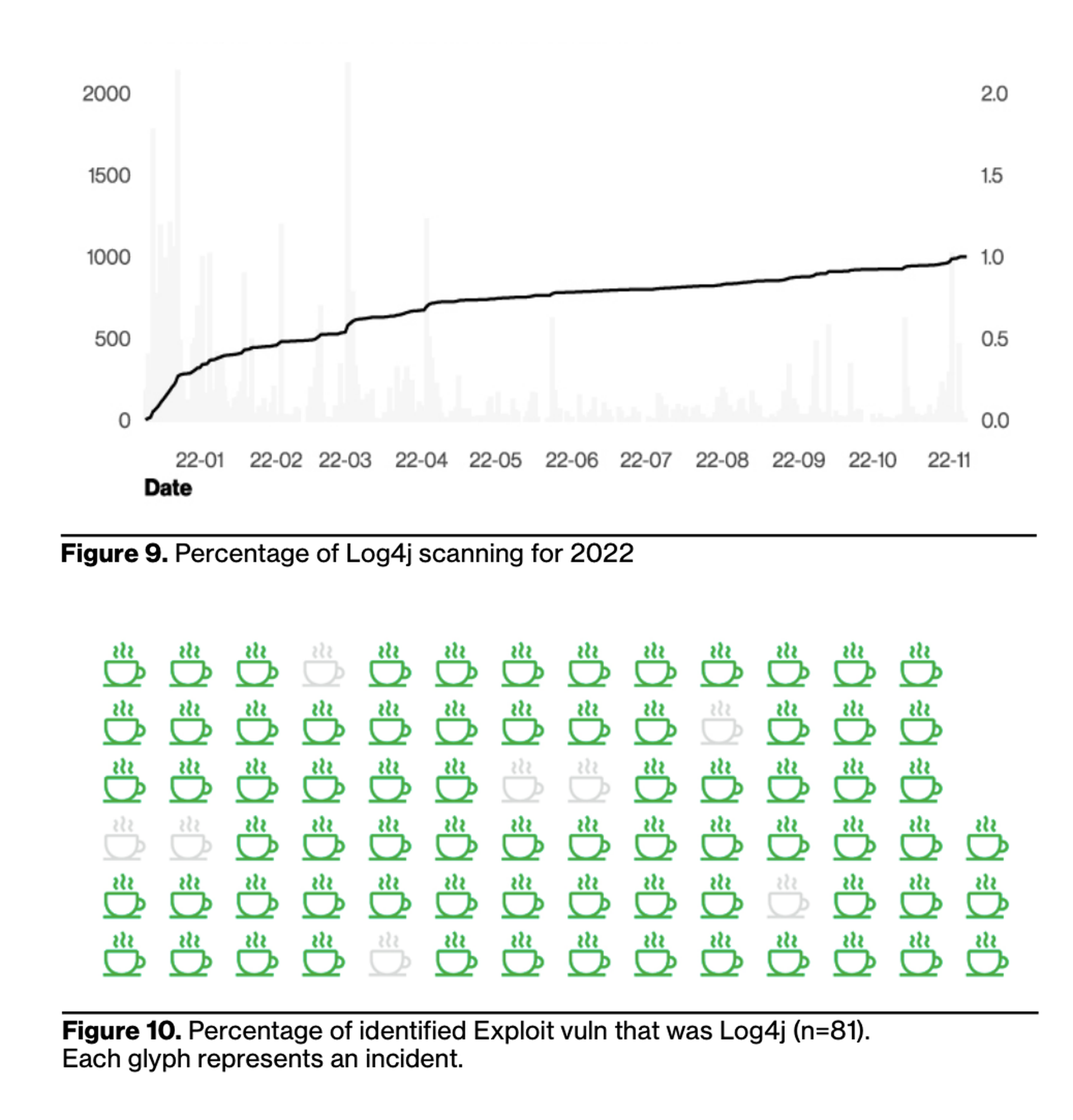
While the flaw was widely publicized in November 2021, fully one-third (32%) of vulnerability scanning around Log4j since took place in the 30 days following disclosure. However, those numbers likely include both bad actors as well as defenders looking to scan their own networks.
Verizon thinks the collective effort to identify and patch dramatically reduced the number of exploitable systems, but that doesn't mean the hype was fake. They also found that 73% of cases involving digital espionage and 26% involving organized crime included use of the bug in some way.
Worry about your disgruntled contractor, not China
While espionage and other nation-state-directed hacks can be extremely impactful and tend to dominate news headlines, Verizon’s data underscores just how much of the malicious activity we see in cyberspace is for profit. Nearly 95% of all breaches were financially motivated (to be fair: some nations, like North Korea, are known to hack for profit as well.)
Only a small fraction (5%) of the breaches captured in the DBIR report involved exploiting security vulnerabilities in systems or devices.
Approximately 1 in 5 breaches Verizon tracked last year had some form on insider participation, whether malicious and intentional or through errors. Despite larger business trends toward digitization and automation, the vast majority of breaches still include some type of human element, whether error, misuse, being victim to a social engineering attack or stolen credentials.
Still, the average organization is far more likely to suffer a breach due to an end user — an employee, contractor, intern or other insider — as they are from a state-backed hacking group or politically motivated hacktivists.
“This is relevant because we were expecting some increased activity in State-sponsored attacks, be it Espionage-related or not, due to the ongoing conflict in Ukraine,” the authors wrote. “Even with anecdotal evidence of increased ideology or hacktivism-related attacks stemming from the geopolitical discussion, it really isn’t making a dent in larger statistical terms.”