A hacking group linked to the Iranian government has been exploiting Log4j 2 vulnerabilities in SysAid, a set of popular IT support and management software applications, according to Microsoft.
The company’s threat intelligence center and other components asserted with “moderate confidence” this week that the group, which they call MERCURY (also known as MuddyWater), has been exploiting Log4j vulnerabilities in SysAid servers that are running the vulnerable code. Both Microsoft and the U.S. government have identified the group as affiliated with the Iranian Ministry of Intelligence, and the organizations targeted were all located in Israel, a top geopolitical foe of the Islamic Republic.
Microsoft, which receives telemetry from billions of endpoints and other assets across its vast customer base, observed the group breaking into SysAid applications on July 23 and 25 of this year. They believe the compromises were used to gain initial access to victim environments, but the company appears to be inferring from that data that the Apache vulnerabilities, which allows for remote code execution, were being leveraged.
“Based on observations from past campaigns and vulnerabilities found in target environments, Microsoft assess that the exploits used were most likely related to Log4j 2,” Microsoft wrote. “The threat actor leveraged Log4j 2 exploits against VMware applications earlier in 2022 and likely looked for similarly vulnerable internet-facing apps. SysAid, which provides IT management tools, might have presented as an attractive target for its presence in the targeted country.”
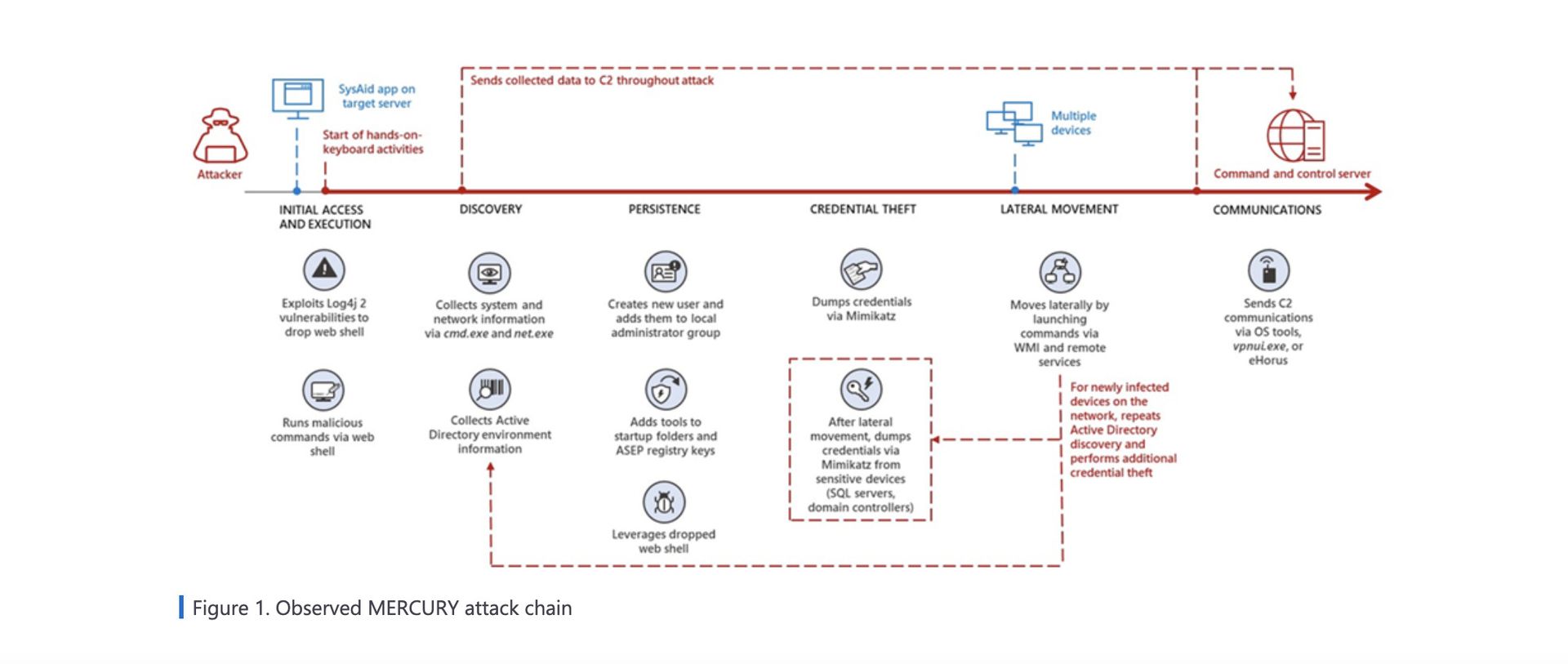
The actors used that access to drop webshells and conduct a number of reconnaissance based activities. In other cases, the access was used to download the group’s preferred tools to conduct lateral movement or establish a persistent presence within victim networks. That includes stealing user credentials, escalating to administrator privileges and adding malware to startup folders to ensure access even if the victim reboots.
MuddyWater is viewed by many threat intelligence organizations and U.S. government agencies like Cyber Command as Iran’s top cyberespionage group, with a heavy presence in Middle Eastern countries as well as Europe and North America. Earlier this year, CyberCom began publishing some of the group’s open source tools on VirusTotal in an effort to raise detection rates, a list they have updated as recently this past month.
According to a joint alert put out by the U.S. and UK governments in February, the hacking group is “known to exploit publicly reported vulnerabilities” like Log4j and has also targeted public sector organizations and critical infrastructure across the globe, including the telecommunications, defense, and oil and gas sectors as well as local governments.
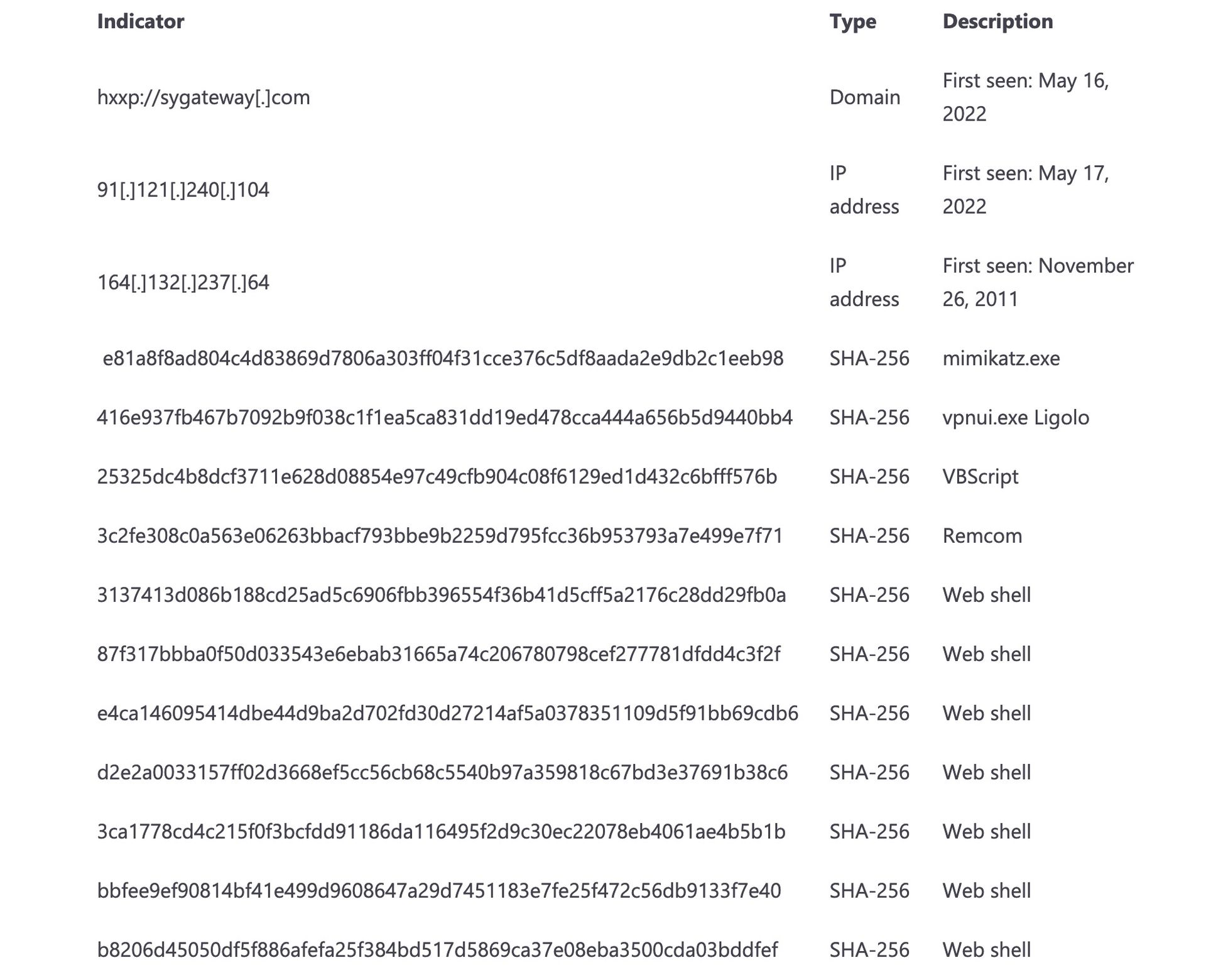
SysAid rolled out patches for the vulnerability in their cloud and on-premise products in January. Microsoft is advising organizations that use SysAid to ensure they have the most up to date versions of the software, review authentication logs for remote access infrastructure and upgrade to multifactor authentication where possible. The blog also includes 14 separate indicators of compromise for organizations to leverage for detection.