In the wake of the Kaseya ransomware incident it was thought to have provided code for, the REvil ransomware gang went dormant, taking down infrastructure including their "Happy Blog" leak site. Now, the Happy Blog has returned.
The blog is hosting legacy leaked content from before the group first disappeared, multiple cybersecurity vendors have reported. Crowdstrike’s Adam Meyers reports that the firm has seen no instances in its incident investigations. Recorded Future’s Allan Liska found no new samples of REvil in Virus Total, a suspicious file aggregator used by malware researchers.
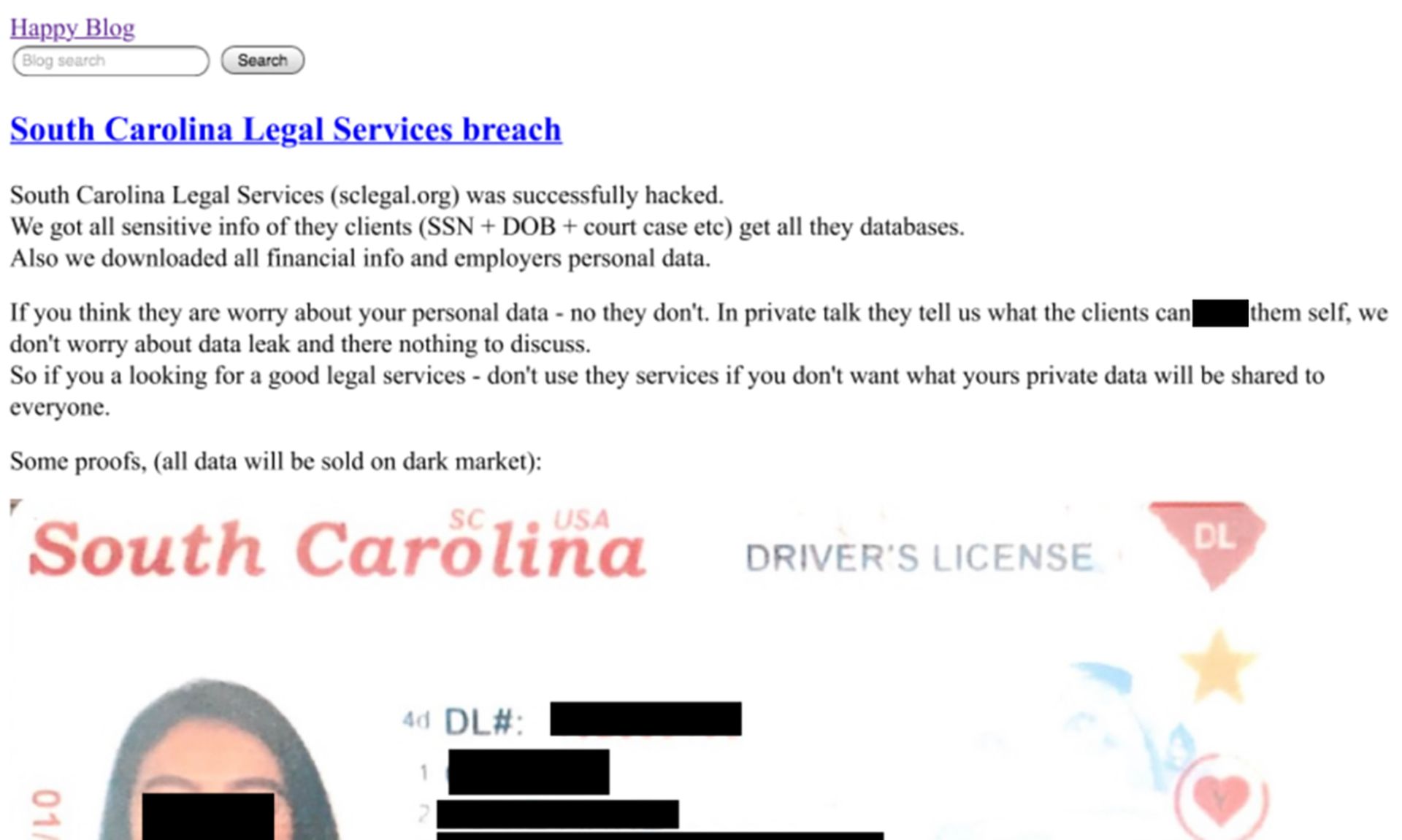
Happy Blog has traditionally been the second punch in a double extortion scheme. If victims decided to restore encrypted systems from back-ups, REvil would leak exfiltrated files on their leak site. The resurfaced site has no new content, however, and is populated with legacy posts from past breaches.
So, is REvil back?
“We have no reason to think that it's anybody else,” said Meyers, senior vice president for intelligence at Crowdstrike.
The new Happy Blog is on the same Tor URL as the old one, meaning the new site is being run by someone with access to the old infrastructure. It hosts the same leaked content, including personal information, which a law enforcement group may be hesitant to do if this was an elaborate sting operation.
Yet the return is still anomalous. Payment sites are partially restored but not accepting payments, said Liska, an intelligence analyst focused on ransomware with Recorded Future. And it’s unusual for a ransomware group that goes away to return under the same brand name, especially in an age with so much police and political attention on high profile actors.
“We expected REvil to reemerge; that, that was kind of a given. REvil members have that history of either being the leader or members Gand Crab [a defunct ransomware group]. What is unusual is just bringing back your own infrastructure, especially when so many law enforcement agencies have been hunting your exact infrastructure for so long,” said Liska.
Where did REvil go?
During its heyday, REvil ran the affiliate program used by extortionists that disrupted Kaseya and JBS. In mid-July, they abruptly vanished.
To many, the assumption was REvil was following the Dark Overlord ransomware group’s lead. Dark Overlord shut down weeks earlier amid the global fallout from Colonial Pipeline, creating the increased pressure for law enforcement to pursue ransomware groups. Throughout the summer, other ransomware groups closed shop, some producing decryption keys freeing existing victims
But the hasty disappearance would not have been REvil’s modus operandi. It wasn’t the first time the group had vanished into the ether. REvil is thought to have operated as Gand Crab until Gand Crab told its affiliates it was closing shop, giving affiliates a brief grace period to close down their operations. This time, they left without a word.
“There were all of these ridiculous rumors floating around on underground forums about how Unknown, the leader of the REvil group was, you know, in a jail somewhere in Siberia or had died of a drug overdose, or had been poisoned by the KGB,” said Liska
A more likely option, said Meyers, is that REvil saw the increasing amount of heat surrounding ransomware groups and paused operations to shore up internal security and let the temperature drop a bit.
“After all of the kerfuffle in the, in the springtime with Colonial and then JBS and Kasyea, I think they were taking time to make sure they weren't doing anything stupid, I think they wanted to recheck their infrastructure, recheck their operations, maybe vet some of their affiliates to make sure that they weren't law enforcement or informants or something like that, and then come back,” he said.
Indeed, Meyers noted that the payment sites and blog had been moved to new hosting, potentially a result of the groups internal audit.
What happens now?
“Ransom attacks,” said Meyers.
Meyers noted that the pace of attacks had not really let up, even without REvil in operation. In recent weeks Crowdstrike is still seeing 55 to 60 attacks a day, he said, with average ransoms over a million dollars.
“There were still plenty of ransomware actors out there — plenty of platforms to do ransom attacks with,” he said. “I think what we'll see is that their affiliates who may have also taken a break will come back and start to use the article platform again”
“I hope it’s one of those things where they come back only for law enforcement to take them down forever,” said Liska.