
Ransomware attacks rose 41% last month as threat actor groups shifted top spots, according to new research from NCC Group.
November’s sharp increase in reported incidents is backed by uncommon contributions. According to the research, threat groups Royal and Cuba claimed first and second place as most active and accounted for 16% and 15% of all attacks, knocking LockBit from the top spot for the first time since September 2021.
“Although LockBit appears to have sloped off this month in terms of total organizations compromised, it is possible that the newcomers to the top three threat actors are amassing as many victims as they can before the holidays, in preparation for 2023,” NCC Group warned in the report.
Royal ransomware — a strain that emerged in January — works without affiliates and is therefore different from the traditional ransomware-as-a-service model. The group uses partial encryption and multi-threaded ransomware to accelerate encryption process and evade detection.
And when it comes to distribution, Royal has a more human touch than traditional ransomware attackers like LockBit, said Matthew Fulmer, manager of cyber intelligence engineering at Deep Instinct. “They use social engineering as their delivery mechanism, and they will reach out under the guise of callback phishing attacks.”
Indeed, threat actors delivering Royal ransomware have been observed to use innovative methods to distribute and obfuscate the payload. In November, Microsoft reported that a threat actor tracked as DEV-0569 embedded phishing links in contact forms on target companies’ websites. According to Microsoft, the group also hosts fake installer files on legitimate-looking software download sites to make malicious downloads look authentic while using Google Ads to expand their malvertising technique further.
Microsoft also recognized DEV-0569 as access brokers for ransomware operations — this, alongside concerns that additional ransomware groups are also using Royal strain, may explain the recent increase in Royal ransomware, NCC Group said.
Besides the insurgence of the new group, the report highlighted that the relatively old Cuba ransomware group has made an “alarming” and “uncharacteristic” contribution with its largest number of attacks recorded by the NCC Group in nearly two years.
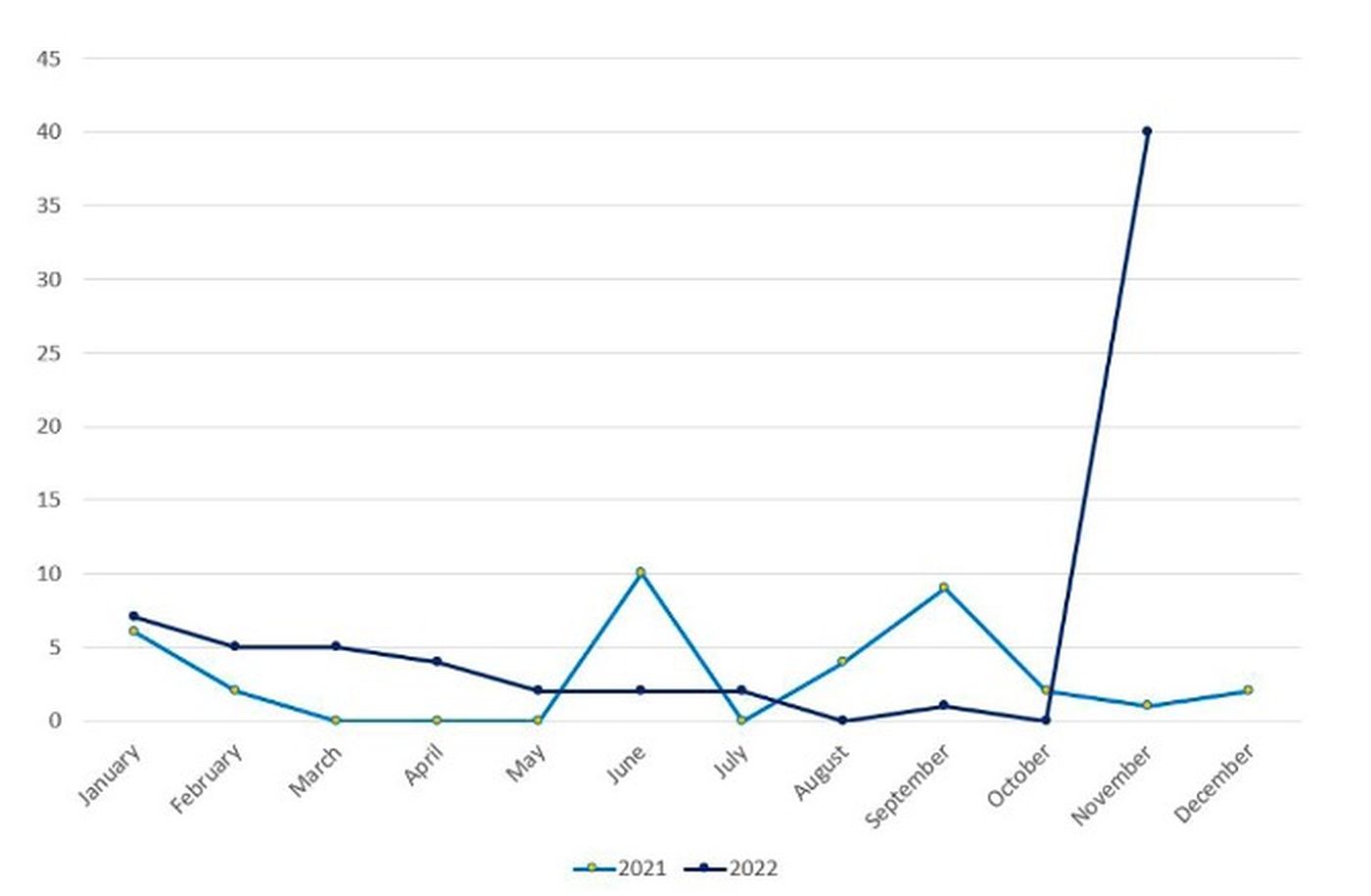
“Looking back over the last two years, the number of Cuba ransomware attacks had been noticeably quiet,” the report read. “As such, a record number of 40 attacks in November is highly unexpected from the Cuba operation. Whether this is the start of a more active Cuba operation and one which moves the variant to the top three ranking on a more permanent basis will remain to be seen.”
“We certainly anticipate spikes and fluctuations in threat actor behaviors, however, the significant jump observed here may signal a more frequent, higher level of targeting,” NCC Group added.
Though LockBit 3.0 remained active, taking third place, and making up 12% of attacks last month, NCC Group said its attacks were “substantially less” than expected.
Matt Hull, global head of threat intelligence at NCC Group, said in a statement that the reduced operation in LockBit 3.0 may suggest the group could be disbanding. Fulmer, however, warned that organizations should not drop their guards.
“LockBit lost a bit due to their builder being leaked [in September this year] and some of the internal information about their encryptor becoming public. This just means they will regroup and rebuild to come back stronger with more resilience and tighter internal protections,” Fulmer said.
“[LockBit] will likely continue to be one of the most prolific ransomware strains observed in 2023,” Brad Crompton, intelligence director at Intel 471, added.



