Threat researchers at HP Wolf Security have noticed a rise in malware campaigns that use tainted Microsoft Excel add-in (XLL) files to infect systems. HP malware analyst Patrick Schläpfer wrote up the findings in a recent blog post.
In these campaigns, emails with malicious XLL attachments or links are sent to users. If they double-click the attachment, Microsoft Excel opens and the user is prompted to install and activate the add-on:
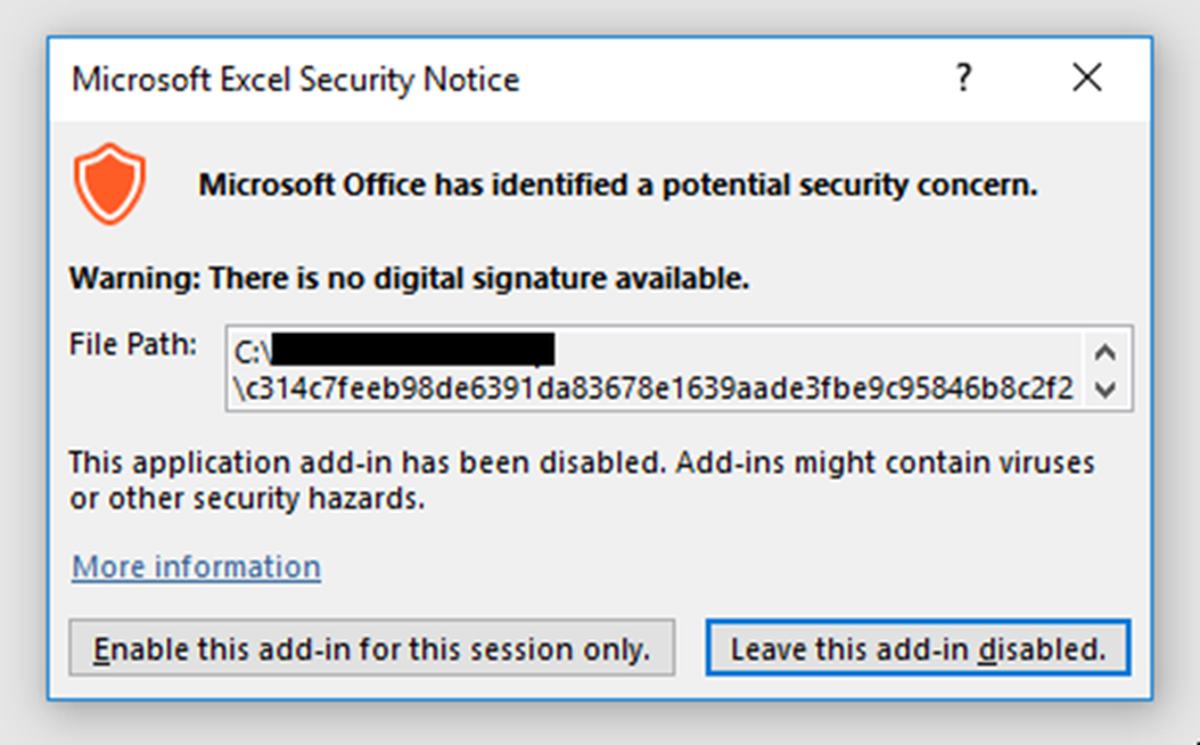
“Attackers usually place their code in the xlAutoOpen function, which is executed immediately when the add-in is activated,” Schläpfer wrote. “What makes this technique dangerous is that only one click is required to run the malware, unlike VBA macros which require the user to disable Microsoft Office’s Protected View and enable macro content. However, XLL files are portable executables that follow the format of dynamic link libraries (DLLs) which many email gateways already block.”
The technique is tracked in MITRE ATT&CK as T1137.006. The idea behind it is that they contain high-performance functions and can be called from an Excel worksheet via an application programming interface (API). This feature enables users to extend the functionality of Excel more powerfully compared to other scripting interfaces like Visual Basic for Applications (VBA) because it supports more capabilities, such as multi-threading. However, attackers can also make use of these capabilities to achieve malicious objectives.
The rise in XLL attacks led HP Wolf researchers to peer into underground forums to gauge the popularity of tooling and services using this file format. They encountered adverts from one threat actor repeatedly, who claimed to be selling a builder that creates XLL droppers.
The blog post includes a collection of screen grabs showing code analysis tracing the process by which such an infection takes hold.
Schläpfer noted that Microsoft Excel does offer many legitimate ways to execute code, such as Excel4 macros, Dynamic Data Exchange (DDE) and VBA, which are widely abused by attackers. Over the last few months, HP Wolf has seen malware families such as Dridex, Agent Tesla, Raccoon Stealer and Formbook delivered using XLL files during the initial infection of systems.
The increasing volume of XLL attacks in the last few months indicates that attackers are interested in exploring this technique further, and that more attackers favoring XLL over other execution methods should be anticipated in the coming months.
HP Wolf recommended organizations consider the following mitigation measures:
- Configure your email gateway to block inbound emails containing XLL attachments.
- Configure Microsoft Excel to only permit add-ins signed by trusted publishers.
- Configure Microsoft Excel to disable proprietary add-ins entirely.



