Recent CyberRisk Alliance Business Intelligence (CRA BI) studies on everything from ransomware to third-party risks and cloud security challenges show many common problems for security decision makers and their teams.
For example: 300 IT cybersecurity decision-makers and influencers responding to a January 2022 CRA BI survey said ransomware gangs were exploiting security holes around remote workers and cloud platforms/apps to do serious damage. They specifically cited remote worker endpoints (36%), cloud infrastructure/platforms (35%), cloud apps (32%), trusted third parties (25%), DNS (25%), software supply chain providers (24%) and more.
When it comes to the most common infection points, they cited exploitable vulnerabilities (63%), privilege escalation (33%), credential exfiltration (32%) and averse mapped shares (27%).
As seen on front lines of incident response
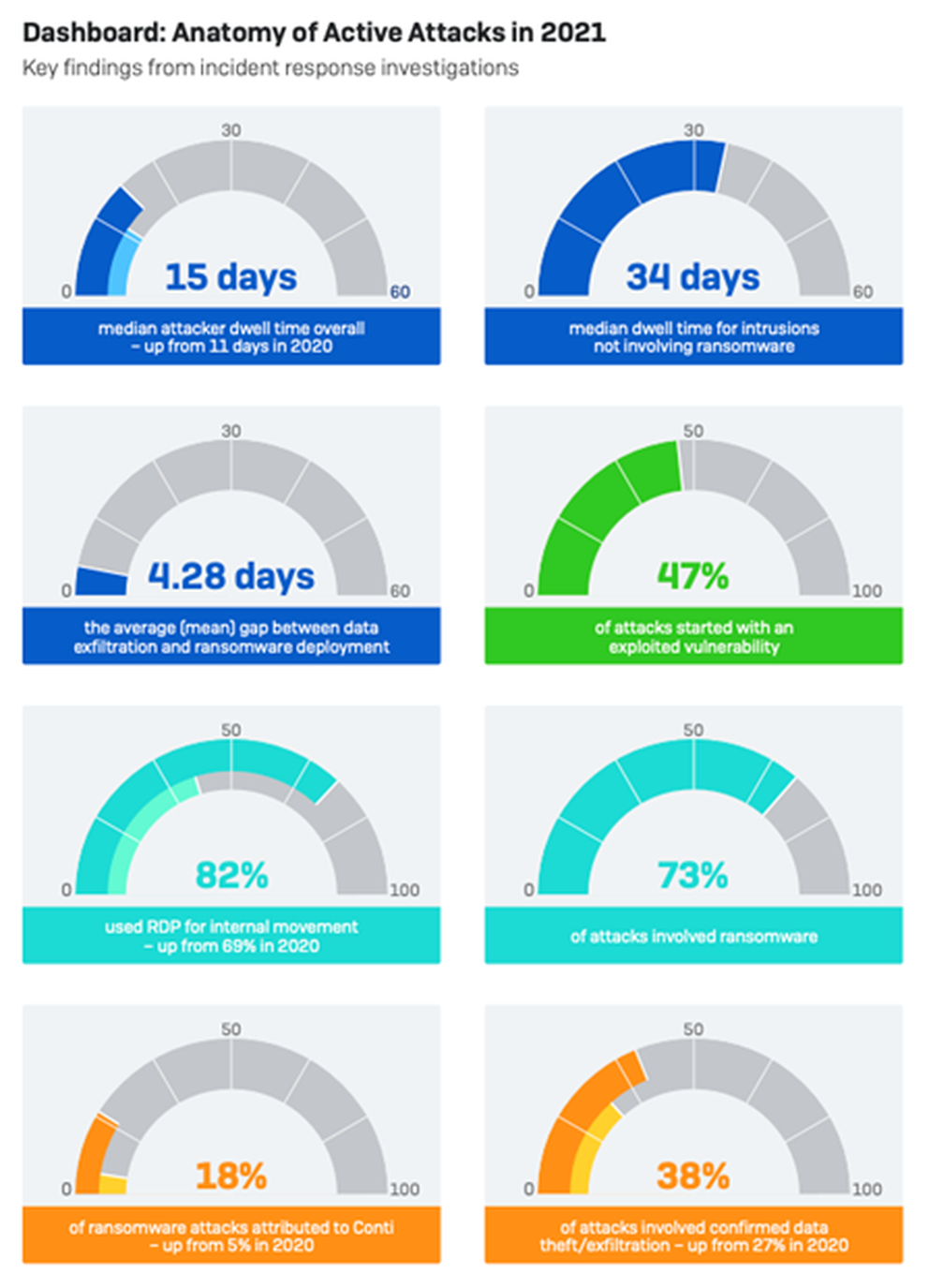
The results share similarities with recent research from Sophos. The company recently released a report based on 144 incidents targeting organizations of all sizes in 2021 in a wide range of industries, which found, among other things, that ransomware gangs who successfully infiltrate company systems dwell for 34 days before launching their attack. Nearly half of these attacks (47%) were traced to exploitable vulnerabilities.
The following chart captures dwell time and the ransomware activity that takes place:
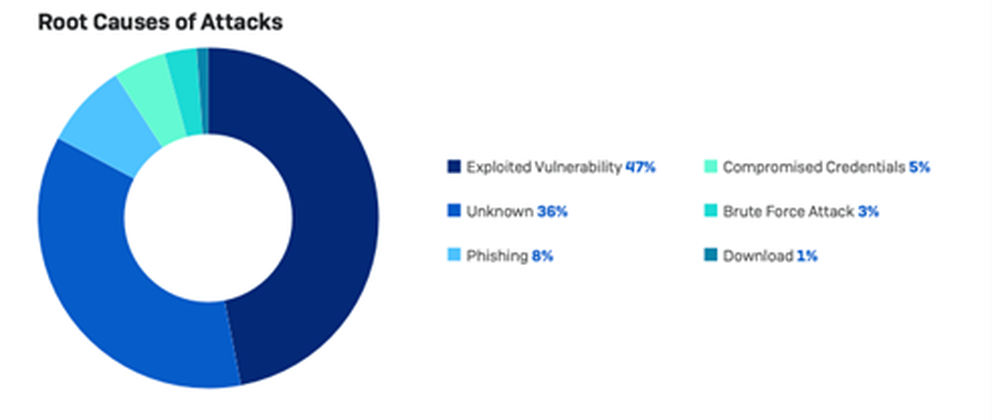
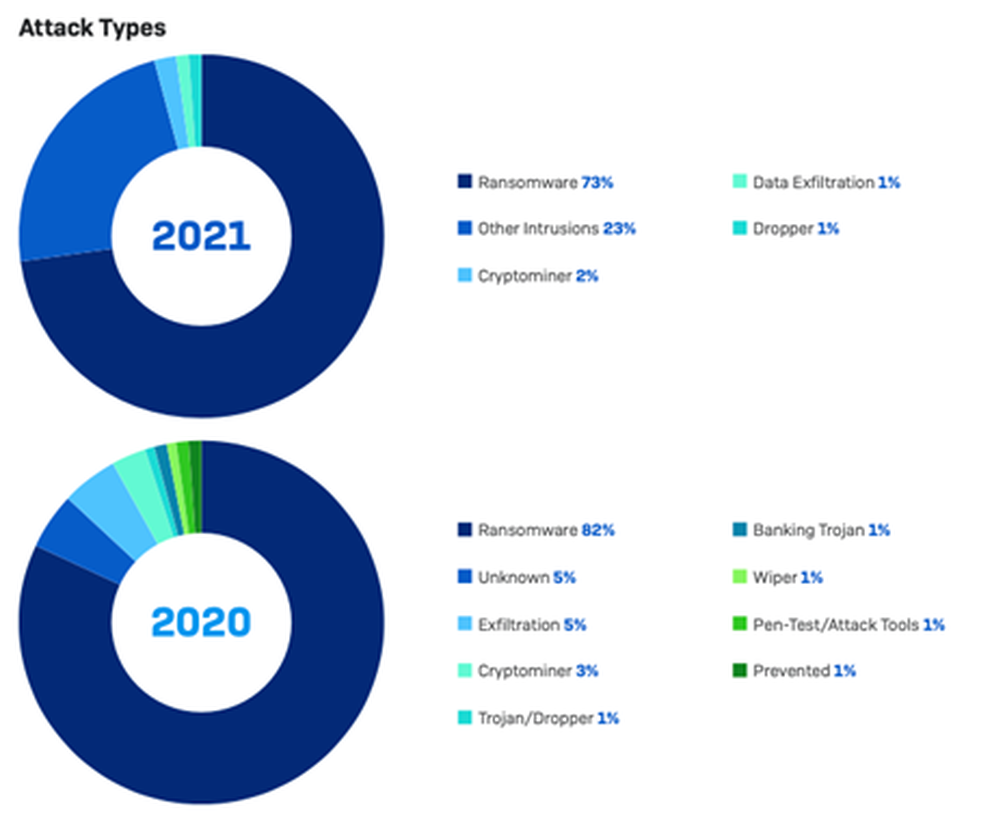
This collection of charts, meanwhile, show the root causes of compromise and the specific types of attacks:
Defensive measures
As Sophos’ 2022 Active Adversary Playbook report notes, every organization is a target for an adversary somewhere, and increasingly, for more than one. If there’s a vulnerable entry point into a network, attackers are looking for it and will eventually find and exploit it. Until the exposed entry point is closed and everything that the attackers have done to establish and retain access is completely eradicated, just about anyone can walk in after them -- and probably will.
Security teams can defend their organization by monitoring and investigating suspicious activity. The difference between benign and malicious is not always easy to spot, however.
Technology in any environment, whether cyber or physical, can do a great deal but it is not enough by itself. Human experience and skill and the ability to respond are a vital part of any security solution.
Detecting, investigating and responding to the red flags of known adversary toolsets and techniques are more critical than ever.
Improving defenses
While there's no easy way to defend against ransomware, there are things enterprises can do to protect their systems and data better. CRA BI’s ransomware report gave the following examples:
Security awareness training: While not perfect, and users will likely continue to click on links they shouldn't, the first line of defense is teaching users to be aware of the risk of malicious links and attachments. The fewer malicious links staff click upon, the fewer attacks the security team will have to respond to. With phishing being a common initial attack vector, ensure email anti-spam and anti-malware defenses are as robust as possible.
Asset management: The security team can't protect systems they don't know exist, so gaining an accurate listing of systems, cloud services, endpoints, and more in the network will help teams understand what systems need protecting and keeping up to date. Pay special attention to how credentials and access are managed, system configurations, network shares, and all software is kept up to date.
Keep systems up to date and safely configured: Be sure to implement an effective vulnerability and configuration management program. Have systems scanned for outdated software, misconfigurations, excess access rights, and more. And when these things are identified, be sure to remediate the situation quickly.
Data management: Knowing where critical data resides is the first step to protecting it from being encrypted by criminals. Not only can data be better protected, but it can also be securely backed up in case of a ransomware attack and then readily restored.
Multifactor authentication: Ransomware attacks typically involve stolen login credentials, either for the initial compromise, moving laterally within the organization, or perhaps both. Two-factor authentication can go a long way to cutting these attacks short.
Trust no one: Zero trust is all the scuttlebutt in cybersecurity today. Still, it's just a term that should mean nothing attempting to gain access to a system or network (whether human or machine) should be trusted by default until they've proven themselves trustable. Because attackers use stolen credentials to gain access to systems within an organization, zero trust should mean monitoring for more attributes in which trust can be built: is the user accessing this system from a trusted or known network? Are they acting and using data in a typical way? What about the endpoint they are using? If there's anything suspicious, it would be a good idea to limit that account's access until they can prove they're who they claim to be.
Begin segmenting your networks: Network segmentation is another strategy that helps to reduce risk. Once an attacker is on the network, they move to other systems. If the network is wide open and can access any system from the point they gained entry, an enterprise could be in trouble. Segmenting networks makes it much more challenging to wander from system to system throughout the organization at will.
Incident response: If there's been a breach, and it's a safe bet that every organization will be breached, the organization needs to be able to identify that it's been breached and have a plan in place to mitigate the damage as much as possible. This means having a team in place. They develop playbooks for different attacks and situations and practice their response.