In a newly published strategic analysis report, the CyberPeace Institute this week conveyed the exacting toll that cyberattacks are taking on the health care industry, especially the human impact on health care staffers, patients and society.
In response, the non-profit has offered a glimpse into its work-in-progress “Accountability Framework,” designed to help relevant health care stakeholders take responsibility for keeping cyberspace secure by enforcing behavioral norms and also by understanding and rooting out the underlying causes when attacks do happen.
“Too often, the lack of thorough investigation after major attacks leaves people desensitized, disillusioned and disempowered, consequently crippling their trust in institutions and governments,” the report states. “Not closing the accountability gap means widening the digital divide between those who have the capability to react to attacks, and those who do not. More importantly, not addressing and closing the accountability gap will exacerbate the void between victims, targets and threat actors.”
The ultimate goal of the framework is to achieve a state of “cyberpeace,” whereby human security, dignity and equity is ensured within the global digital ecosystem. But there will be challenges ahead if the methodology is to gain traction and become widely adopted, observers said. The framework will have to distinguish itself from similar efforts, C-level management will have to legitimately be incorporated into the accountability structure, and some official body or entity must step up to actually enforce accountability.

“It is clear that we need to have a better sense of where risk might lie,” said Marietje Schaake, president of the Cyber Peace Institute, in a virtual panel presentation marking the release of the new report. “And that chain of responsibility has to be clarified and optimized where there are still weak links that can be exploited. So I think there's a lot of work to do, and certainly closing the accountability gap has to help in attaching a price to these [cyber]crimes and to hopefully making them less lucrative, less attractive, and less favorable to the perpetrators.”
The Framework’s Structure
The Institute’s framework for mapping accountability is designed to help stakeholders – including senior management, IT professionals, medical staff, vendors and the government – commit and adhere to expectations of responsible cyber behavior, and then apply consequences when these norms are broken. The intention through this joint effort is to identify weaknesses in the cybersecurity chain that resulted in past attacks, identify role-based practical steps that each stakeholder group can take to stop future attacks, and facilitate better communication between stakeholders.
“The Institute believes that applying the accountability framework has the potential to deepen understanding of the current cybersecurity landscape in an innovative way, by shedding light on the weak spots in cybersecurity that have a direct impact on people as well as systems and infrastructure,” the report states. “Applying the framework as often as possible will allow for more effective filling of the gaps in cybersecurity, by revealing which of them have the most impact on the victims as people.”
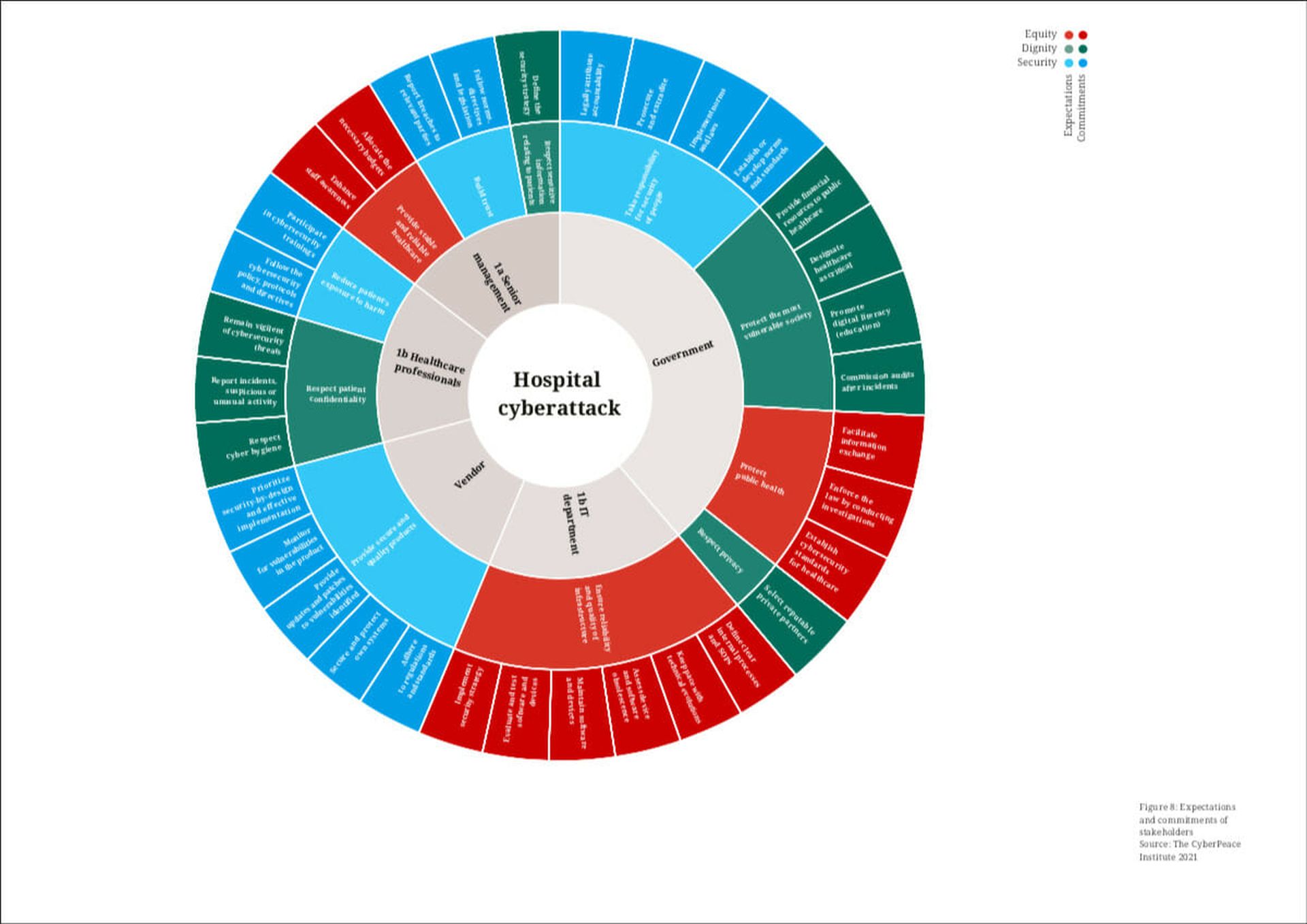
(CyberPeace Institute)
Moreover, applying the framework to past attacks could also potentially expose common issues like a lack of cyber investment and policies, insufficient education or insufficient legislation, the report continues.
The Institute is actively looking to collaborate with health care institutions that have been victims of a cyberattack to test run the methodology against their incidents. A more in-depth look at the framework is available in the report, titled: “Playing with Lives: Cyberattacks on Healthcare are Attacks on People.”
Experts suggested the framework is well-intentioned and holds promise, but it may still need to further differentiate itself from similar efforts, and overcome key challenges that lie ahead.
“An accountability framework has potential, but there are areas that need to be thoroughly considered, such as: What happens when there isn’t someone available – like a government agency, regulator or appropriate coordinating body – to hold a stakeholder accountable?” said Dr. Bryan Cline, chief research officer at HITRUST, the Health Information Trust Alliance. “In its current state, its simply too early to tell if the framework is on the right track in terms of its methodology.”
Cline noted that The Institute's creation borrows elements from other existing frameworks that may not quite be “as expansive in scope, or as lofty,” but do already help grant health care institutions safe harbor, protecting them from fines and penalties in the event of a cyber incident.
While this new framework “could help identify and fill in any gaps, and also act as a bridge for similar efforts internationally,” Cline said it also obliges health care professionals to adopt yet another framework, “when many of the elements exist elsewhere and existing frameworks can more easily be enhanced and expanded to provide additional capabilities.”
For instance, Cline noted that the NIST Cybersecurity Framework already “provides a common language and approach for the implementation of comprehensive cybersecurity programs across all industry sectors to achieve specific cybersecurity outcomes, and a U.S. government-led public-private partnership has produced specific guidance to the health care industry on how to implement the NIST Cybersecurity Framework (NIT CSF), leveraging controls, framework-based risk analysis and existing informative resources such as NIST SP 800-53, ISO/IEC 27001 and the HITRUST CSF.”
“HITRUST also provides the most widely used cybersecurity assessment and assurance programs in the health care industry that actively promotes cybersecurity awareness and encourages strong cybersecurity programs,” Cline continued. “It is unclear what will distinguish the CyberPeace framework. The initiative could potentially tie all these and other related activities in the U.S. together, but there is already work in this area."
David Finn, executive vice president of strategic innovation at CynergisTek, similarly noted that the framework “is on the right track, but not shockingly new.” For instance, he said, the NIST CSF and the Health Care Industry Cybersecurity Task Force to Congress have already “call[ed] for most of these actions” that the CyberPeace Institute is advocating.
However, “the fact that it is health care-specific and global does differentiate it to a great degree,” especially because risks do vary from industry to industry, he acknowledged.
Finn said that if the framework is to work, then senior management accountability can’t stop at the CISO level. Rather, senior management must include the entire C-Suite, particularly those who write the checks.
“If the CIO and CISO can’t get funding or staffing, how can you hold them accountable?” asked Finn. Cyber risks, “while they manifest in IT and security, are enterprise risks that impact clinical operations and care delivery, patient care and revenue… There must be a way to hold those executives accountable – if not directly, then through… governance. Make the CEO and CFO sign off on decisions around risk acceptance and mitigation, both for the good and bad. That’s how the banking industry fixed their problem.”
Ultimately, Finn said, the accountability framework will likely resonate with those health care institutions that are attuned to the critical nature of information security, while those entities that live in the past may struggle with the concept.
“The organizations and people who understand that security is a strategic function of health care delivery and operations are well down the road,” said Finn. “However, the ones who are still operating in the old healthcare paradigm… will likely not figure it out. That train was already building up a head of steam, but COVID-19 sent it out of the station and there is no going back. Health care is going to be consumer-driven and consumers want security and privacy.”
In a related story, Tony Cook, head of threat intelligence on GuidePoint Security’s consulting team, recently spoke with SC Media about how an increasing number of health care institutions, in the wake of major attacks, are embarking on threat-hunting missions to seek and destroy exploitable vulnerabilities across third-party applications.



