As millions of people roll up their sleeves and receive their COVID-19 vaccines, company executives or HR departments will need to issue to employees communications related to inoculations and the prospects of returning to a physical office environment.
This is opening up a new angle for phishing scammers, who are sending emails that appear to be company-issued information referencing vaccines and COVID-19 directives. Indeed, in a Monday blog post, researchers at INKY warned that in late winter, a “wide swath” of its business clients received phishing emails featuring COVID-related lures and content inspired by some of the pandemic’s latest developments.
INKY told SC Media that employers and employees alike should stay wary, keeping an eye out for fake company instructions related to back-to-work policies as employees grow eager to receive their shots and possibly return to their old routines.
Furthermore, the scammers’ use of dynamic algorithms could make some of these social engineering schemes look like they are intended for the recipient, "extracting features (name, domain name) from a recipient's email address and using them to create personalized phishing emails,” said Bukar Alibe, data analyst with INKY, in an interview with SC Media. For example, an email sent to [email protected] could look like: "Hi Roger, Please review Example's new return-to-work guidance. Regards, Example HR Department."
In fact, a new phishing kit, LogoKit, “uses the same tactic to retrieve a company's logo from Google's favicon database to build personalized phishing sites in real time that adapt to each victim,” Alibe added.
One recently observed phishing sample that used this dynamic algorithm technique was an email containing what appeared to be a survey from the targeted business’s HR department, asking employees about their willingness to get one of the COVID-19 vaccines, so the company could arrange for employee inoculations at a nearby clinic.
“As we begin working with the Department of Health to obtain vaccination opportunities for staff, we are asking all employees to take a simple survey to let us know if you are interested in receiving a vaccine when it becomes available to us,” the phishing email read. The email also contained a link that at first glance seems to lead to a Survey Monkey URL, but actually was created to direct victims to a credential harvesting site on a hijacked domain.
Another phishing sample consisted of a fake message from a targeted company’s CEO asking employees to click on a link to an online document detailing the latest COVID-19 precautions, while a third warned employees that two of their colleagues contracted the coronavirus and instructed them to fill out a COVID-19 compliance form.
The fake CEO phish contained a link that leverages Google’s open redirect capabilities to send recipients to a malware injection site or credential harvesting site, the blog post explained. “Even if the recipient were to scrutinize the URL, all they'd see was a good-looking Google redirect,” the post said. Meanwhile, the compliance-themed phish embedded a legitimate link leading to a SharePoint site that was compromised and abused for credential harvesting.
Sherrod DeGrippo, senior director of threat research and detection at Proofpoint, said that while she hasn’t seen significant volumes of email threat activity using return-to-work themes just yet, “we have seen references to the vaccine in malicious social engineering, as well as the COVID-19 relief bill recently passed by the Biden administration. Vaccine and tax lures leveraging the IRS are very common right now, including some that are combined.”
As always, scammers will continue to leverage the latest headlines, crises and news trends to entice email recipients into opening attachments or clicking on malicious links. The international distribution of life-saving vaccines, and the promise of a more traditional work experience for some, certainly would qualify as exploitable themes.
Indeed, on this very day last year, the FBI’s Internet Crime Complaint Center issued a public service announcement warning citizens to watch out for phishing schemes related to coronavirus-related charitable contributions, financial relief, airline refunds, and fake vaccines, cures and testing kits. Of course, at the time no vaccine was available, so such lures weren’t nearly as believable. Now there are three vaccines in the U.S. alone, with a fourth likely on the way.
“We have seen this play out with lures on vaccine offers, stimulus checks, remote work protocols and a combination of many different themes,” said DeGrippo. “There is certainly a large segment of workers anxious to return to the office, and with news of certain businesses reopening, employees may have an expectation that they will see incoming email from their HR with further information. As they have in the past, threat actors have identified both a pertinent issue and a susceptible audience for an issue they can easily exploit through a well-crafted social-engineering email.”
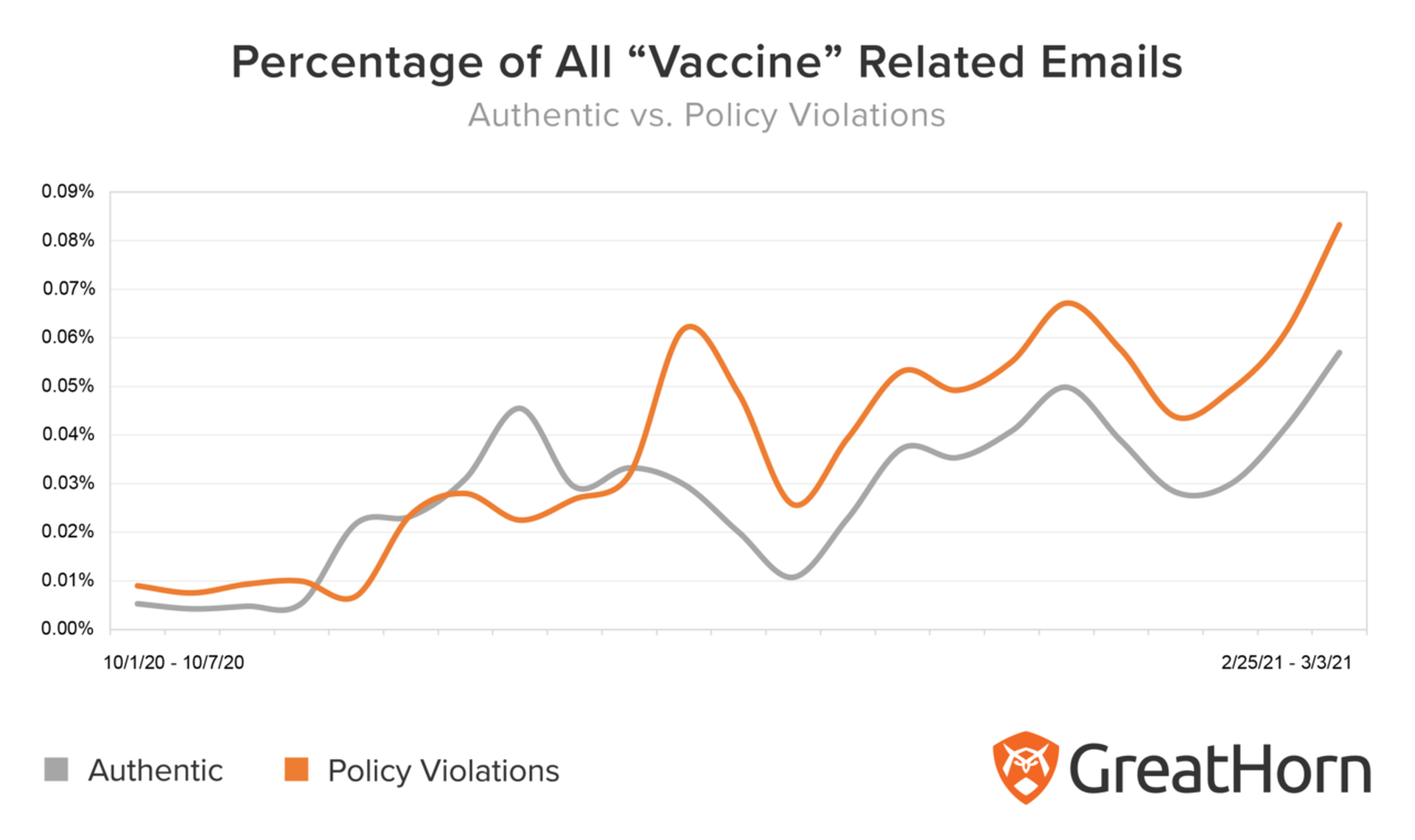
Other recent research reports have echoed INKY’s warnings. For instance, the GreatHorn Threat Intelligence Team last week reported a “significant increase in the use of the word ‘vaccine’ in phishing attacks, relative to the frequency with which the term is used in authentic emails.”
Meanwhile, Mimecast in its new The Year of Social Distancing global report, said it is almost certain that threat actors will continue to “exploit the unsettled work situation,” with a focus “both on remote workers and those returning to the office, which creates a whole new range of social engineering opportunities.”
“The return to the office is a key opportunity to interpose communications around erroneous new practices or procedures, seeking to take advantage of individual’s being unsure or confused about any new or emerging hygiene, COVID-focused safety measures, etc.,” said Carl Wearn, head of e-crime at Mimecast, in an interview with SC Media.
And on March 19, Vade Secure informed SC Media via email that it had detected roughly 1 million phishing emails related to the Moderna and Pfizer vaccines in just the previous three days.
To reduce the likelihood that employees falls for such ruses, DeGrippo recommended that companies “keep employees notified of malicious emails offering details on return-to-work policies, what they should expect in future legitimate communications, and how to verify messages. Instruct users to reach out to their IT security department to verify before clicking or opening a suspicious email. Even if your company has no return-to-work plan solidified yet, communicate that to your employees. Preempt any doubt or uncertainty that would get them to believe a malicious email.”
Additionally, “ensure any change to procedures or the implementation or use of new ones utilizes a trusted and established channel to communicate those changes,” suggested Wearn. “A direct contact known to the employee should also be contactable to verify any new processes or procedures as genuine, by personal contact preferably. Email alone should not be accepted as a trusted means of communication without other means of verification.”
“User awareness is a good first step,” agreed Alibe. “Employers should publicize their normal methods of communication and train employees to distrust any emails that deviate from established protocols.”




