Everyone wants to receive a free $50 Best Buy gift card and USB drive in the mail, but as the saying goes, nothing is ever truly free.
A cybercriminal gang has put together a unique attack profile based on this human frailty, but one that has been on the scene since the early days of cybercrime. The attack begins with an actual paper letter mailed through the U.S. Postal Service to a specific target that contains a socially engineered message designed to entice recipients to place the USB drive in their computer, according to Trustwave's Spider Lab.
The note says the gift card is thanks for being a great Best Buy customer and that the USB drive contains a list of products that can be purchased with the card. Not surprisingly, there is nothing on the gift card, but the USB does come with a surprise: malware.
Researchers found the USB drive’s Arduino microcontroller was programmed to emulate a USB keyboard. This is an obfuscation method, as most security software by default allows a USB keyboard to connect. Once the drive is inserted, a payload is injected and additional code is downloaded.
“These types of USB devices are widely known and used by security professionals. The fact that they are also cheap and readily available to anyone meant that it was just a matter of time to see this technique used by criminals ‘in the wild.’”
The fact that USB drives are an everyday item makes them appear less threatening to the average person, unaware that they can be used for malicious purposes, Trustwave noted.
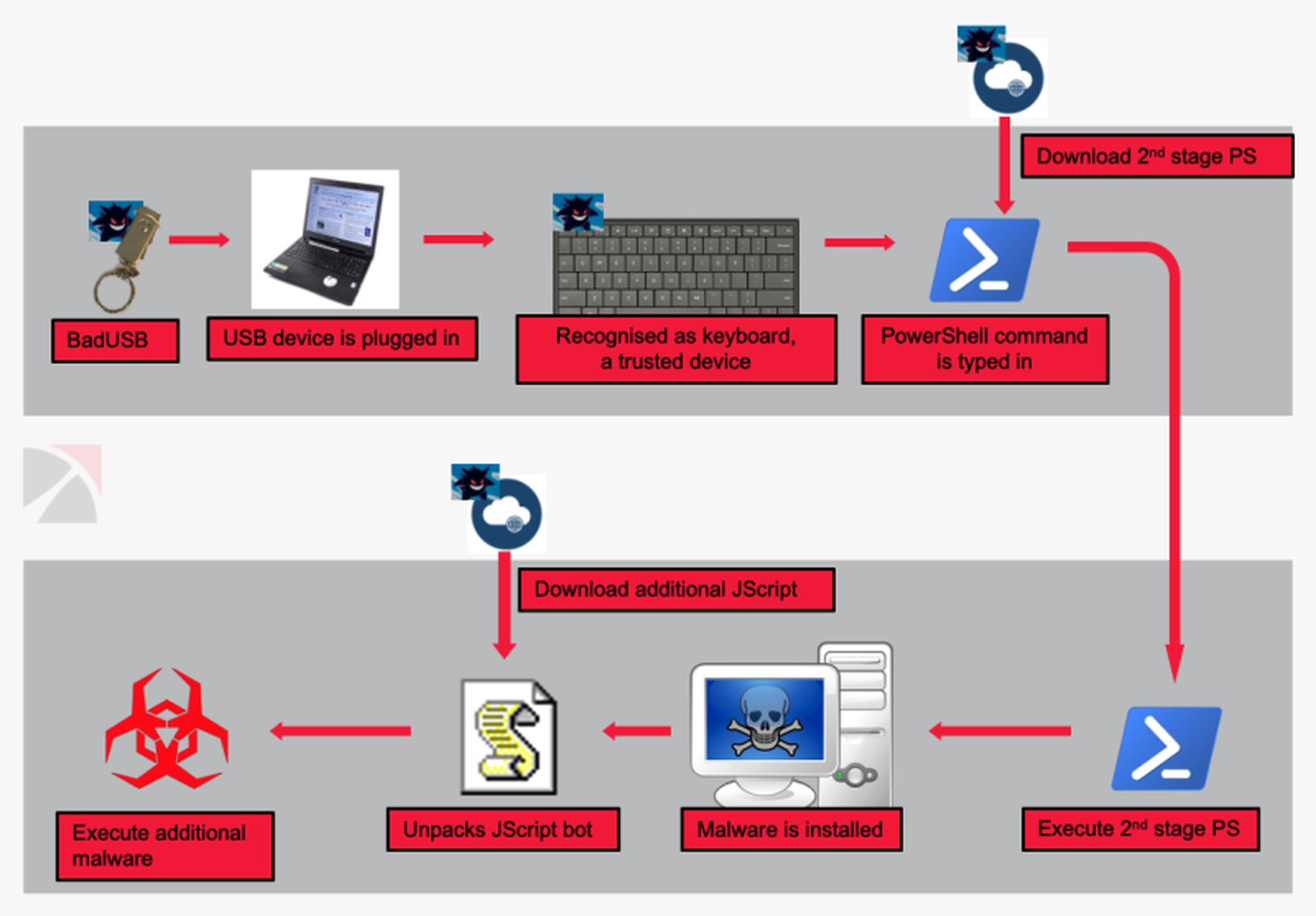
A fake message then pops up on the screen saying the USB device is not recognized, possibly to confuse the victim as to what is taking place. At this stage additional JavaScript is downloaded in order to register the now infected device with the command-and-control server. The C2 server then sends some encoded data containing the info-stealing software.
At this point a great deal of information is taken from the device:
- Username
- Hostname
- User’s System Privilege
- Uses WMI query to get the:
- Process owner
- Domain name
- Computer model
- Operating system information
- Office and Adobe acrobat installation
- List of running Processes (including PID)
- Whether the infected host is running in a virtualized environment
The malware then enters a loop and reactivates every two minutes when it can receive additional commands from the C2 server.
“This is reminiscent of how phishing and some of the first ransomware attacks began -- with physical mail. People would receive CD-ROMs or floppy disks in the mail claiming to have some valuable information or program on them. As soon as they insert it into their computer, the malware that was actually on the disk would execute, just as with this USB,” said Marc Gaffan, CEO of Hysolate, adding this is a perfect example of how creating a zero-trust environment can be key to protecting your data.


