At InfoSec World 2020 on Monday, Rex Sarabia, security awareness program manager at Lululemon, led the session “Building an Enterprise Security Awareness Program from the Ground Up.”
SC Media interviewed Sarabia about his presentation to learn more about Sarabia’s biggest challenges, his tips for security professionals starting up their own programs, and how he “gamifies” training for employees and executives.
Thanks for joining us, Rex. Your InfoSec World session explains how you built a security awareness program from the ground up at Lululemon, an apparel retailer for “sweaty pursuits,” as you describe it.
Sure. So I should clarify by explaining that even though there was no formalized role before me, there was always somebody or a group of people that held the same responsibilities – I didn’t start from a completely blank slate. The challenge then was that [my predecessors’] responsibility for security awareness was more… ‘side of the desk’ in its accountability in relation to their more primary, core responsibilities of their role. Which I think a lot of people would agree that raising security awareness is already a challenge to pull off effectively because of the inherent challenges to raising awareness for any cause. This level of difficulty only multiplies in any large, complex organization.
Fortunately, priorities shifted where it was decided that a dedicated, 'single throat to choke' position was needed. Which was great! For management to reach that turning point and obviously for me being in the right place at the right time, I can’t complain there! I’d like for us to get to a point where if an incident occurs, a question that gets raised as part of the post-mortem is: “What kind of training/education did this person get? Is there a correlation between their behavior that caused the incident and their risk profile? Is there a gap here that security awareness can address?”
What has been the most challenging aspect of filling a role that never before existed at the company and constructing such a program from scratch? Or to put it in Lululemon terms, what aspect of the job so far has been your sweatiest pursuit?
Funnily enough, before filling this role, if you had asked me the same question then, intuitively I would’ve reasoned that “getting things moving” or “getting it off the ground” would be the natural response. It’s physics, right? It takes more effort to get something moving from a resting state than it does to maintain that momentum. But, surprisingly enough, this wasn’t my experience… We went from not having a global, scalable way to deliver training that is also auditable, to launching web-based training to over a hundred employees to meet PCI compliance requirements in less than three months. Realistically, it was less than two months if you subtract the time “my wife went on a holiday” and “the days I spent onboarding for new hire orientation.” That velocity of change may be an inherent as part of our corporate identity – I think I’m still too new to say that definitively, but one can always speculate...
So, long story long, I think that so far on this journey, my sweatiest pursuit has actually been the efforts to sustain. Say if, in the rush to take off, to get going, maybe you didn’t bring all the things you wish you had. Now that you’re fully away, you’re in flight, you forgot something important, but not immediately needed, like your parachute. Well, that’s okay. Because now your focus is to just fly the plane. Just stay in the air until you know what to do next. If you can stay flying long enough, you can learn how to land, and by then you’ve also already figured out how to navigate so you can fly yourself to some place where you can land to get that parachute and whatever else you need, but didn’t have when you initially took off. I’m not a pilot but “build a plane in midair” is a common corporate metaphor, right? The first twelve months was a lot of work, but it was also a lot of firsts too – some for me and some for the org and some for the both of us. So that initial hustle perpetuates itself, feeding off its own momentum, its own energy. It’s okay going full bore at 100 mph because it’s exciting.
So that was the first year. Now we’re nearly halfway through the second year – and what an eventful year it has been so far, eh? Those things that were fun and exciting last year, that everybody loved and want you to do again this year – well, it’s definitely a lot easier the second time around, but there’s still a lot of work that needs to go into at least maintaining, meeting the same expectations as last year. Not to mention, not everything went perfectly well either, superstar (I’m referring to myself here). There’s still plenty of “opportunities for improvement” that demand just as much, if not more, of your time and attention as well. Oh yeah, and by the way, since human behavior is also fluid and technology is also always changing, those bad actors out there are also always adapting and finding new ways in so your existing training, content and approach, while relevant and well-suited last year may also need to be updated. A journey of a thousand miles begins with one step, but after that first step there’s still a hell of a lot of steps to take after that.
Is there a certain freedom building such a program from the ground up as opposed to tweaking or rebuilding an already existing one?
There is definitely a freedom in starting fresh over tweaking an existing program. But constraints and limitations can be enabling too. Analysis paralysis is a very real concern. So, admittedly, my answer is a “no-answer” answer. Everybody’s situation falls somewhere on that spectrum between starting fresh and transforming/improving an existing program. Security awareness is just as important in one scenario as it is in the other. Our value-add as security evangelists is in our ability to or learn how to adapt to the situation we find ourselves in, figuring out what works for our people, so that the message of good security practices still gets through and is put into practice by our audience.
For organizations attempting the same feat, what would you recommend they prioritize first as they lay out an execution plan?
Planning is good exercise as long as it doesn’t delay the actual execution. Doing something good today is better than doing something perfect tomorrow – it’s not always an easy balance to maintain – there will always be compromises so I hope you’re adept at making them. And since no plan survives first contact with the enemy, I think it’s most important to design a plan with the mindset of knowing that it’s highly likely that it’ll need to change anyway. At least that way, any plan you come up with will have resiliency baked into it.
If your company isn’t explicitly required to perform security awareness training, then find something your company doesneed to comply with and see if you can leverage off that; it may at least point you in the right direction. In all likelihood your company has some kind of PII, so partner with your Privacy-Legal colleagues (these folks are your closet allies outside of your security colleagues) since privacy and security are really two sides of the same coin.
There are plenty of ways to understand risks wherever you are. It just takes a little empathy and imagination to see what could go wrong and then do your best at applying the likelihood of those events occurring and then finally multiply that by the magnitude of its impact. Piece of cake. My background is Big Four [accounting], so my natural, knee-jerk reaction to a question about “priorities” is to take a risk-based approach. There are a lot of risk frameworks out there and plenty of companies that will provide you with their best approach to them for you. Obvious, right?
Okay. So, something that can be operationalized tomorrow? Get tuned in to all of your internal communications channels. Not just the official methods, but the informal ones as well – the most mass-applicable and clever example that I also mention in the [InfoSec World] presentation – is to add a note in your email signature. That space can be used to market events or mention a brief IT security “best practice of the day.” You know, it’s okay to be corny because we’ve got good intentions. Messages can carry different objectives and meanings for different segments of your audience. The more natural you are at effectively working within those channels in getting the message out is never going to put you at a disadvantage. The best security advice in the world doesn’t do anybody any good if it’s being yelled into the void. Teaching is fundamentally a higher form of communicating, so it stands to reason that your abilities at being a teacher are going to be limited by your ability to communicate. Also, too obvious.
Start training. Training can manifest very differently based on your context. It may be as simple as holding lunch-and-learns throughout the year on various security topics or maybe you need the scale and accountability that only an enterprise LMS, training platform can offer. Doing all that already? That’s great! Publish or update your internal knowledge base about good security practices, keep the material fresh and relevant with regular updates and current to recent events. When COVID really started to gain traction in the US, it was early March. There were a lot of early reports about scams going on. So I wrote an internal blog article about misinformation, scams, etc. that our employees could immediately benefit from beyond their work lives. A lot of it was simple and common sense, but there’s a lot of noise out there so providing a signal through trusted, internal comms provided our folks a shortcut to actionable intelligence. Start doing something.
Lastly, for those that are past the basics, I want to give an example of a “next step.” Assemble a team of advisors and evangelists. This past year we started our “Security Champions” working group. This group is a cross-functional representation of our enterprise. We’re starting off small at first, but eventually the goal is to have a group in each of our major markets. It’s absolutely critical for this to include representatives from outside of IT, like accounting, to enhance the diversity in perspectives. We meet monthly to discuss training needs and feedback on past initiatives, to announce upcoming security initiatives, or to serve as focus groups for vendor demos. Having a pool of opinions you trust, readily available, is indispensable to boosting your security awareness program to the next level since nobody has a monopoly on good ideas and security doesn’t exist solely in a vacuum.
Your presentation includes a timeline that runs from your first day on the job in March 2019 through May 2020. Pick a highlight from along this timeline that you consider to be a key milestone/achievement and explain why.
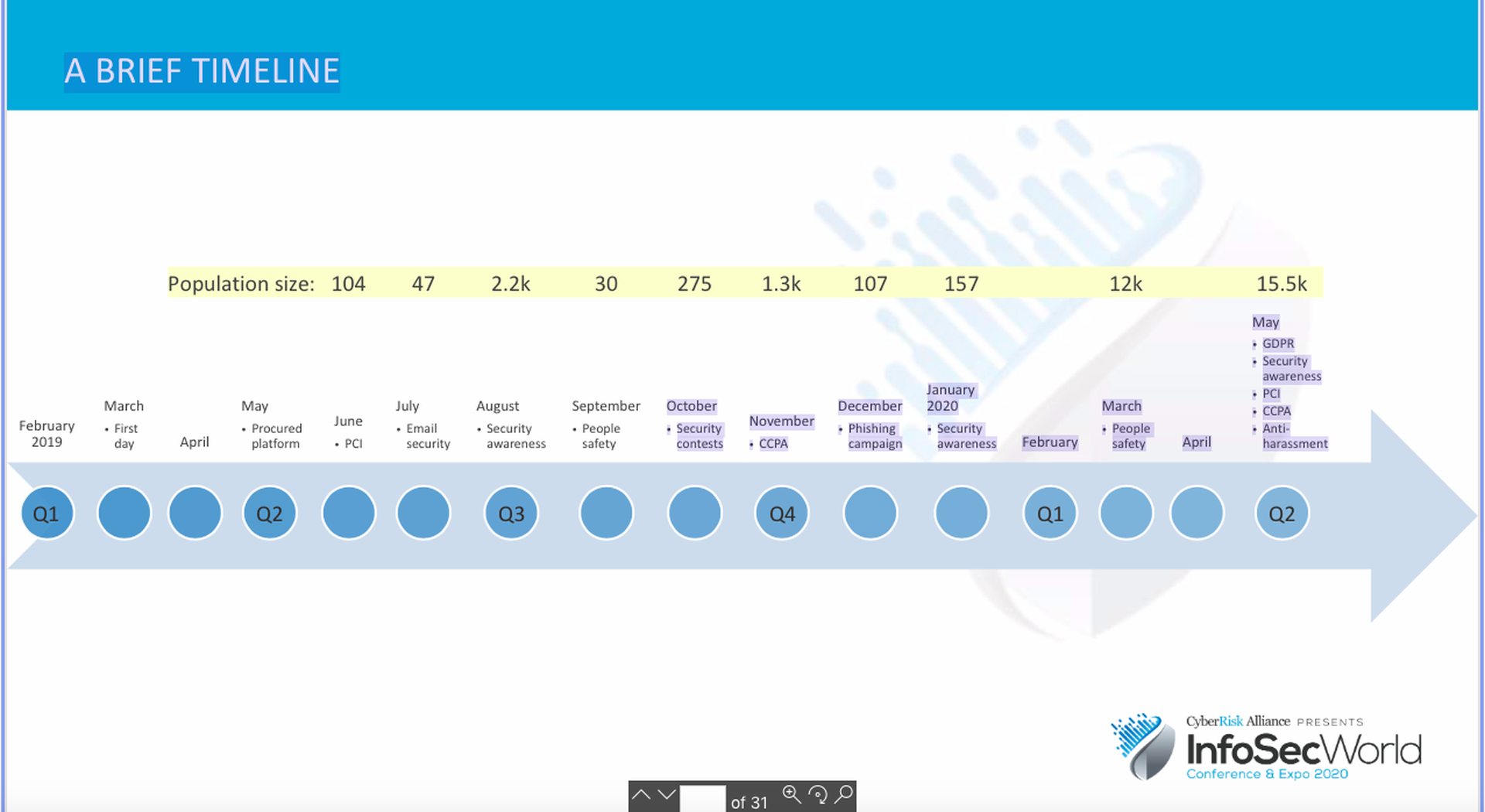
There are two moments over the past year that stand out. Firstly, and probably less interestingly, was the first really big (to me at least, at the time) training campaign that went out to all of our largest, corporate, employee population that’s based across North America. That was when I came to that “Oh, I’m really doing this now/I’m that guy” kind of realization.
The more fun one that I talk about briefly in the presentation is our annual Leadership Summit. That was pretty intense for me. We had only decided to attend and [participate] both maybe a month or two before. Other teams that were a recurring presence at this conference probably has closer to twice the amount of time to plan. And with everything else that was going on at the time, everything really had to come together within the last two, three weeks before the event in order to come off mildly successful. So it was stressful, but it was also really fun and personally rewarding for me. My fondest part of that memory was the amount and variety of people that had to do their individual parts for any of it to really come off. It was one of my all-time-best examples of teamwork and collaboration. We’ve already started planning on the next one and how we can do it better.
Being there at the event itself was really fun. I think we, even for the briefest moments in our interactions during the conference, got a lot of people interested in security where they would not otherwise have been... Our short eight-foot table had three demos. They were all hands-on, and all specifically designed to be relevant to the attendees’ daily work and personal lives. I think that was one of the real turning points for me in appreciating the value of the learning process, for people to be physically involved in the lesson that's being taught. We had demo PIN pads that we borrowed from out IT lab to show what card skimmer overlays actually actually look like on our own hardware and how to detect them! I feel like that learning experience was impossible to replicate on a computer screen as it did in real life. The whole week was a real whirlwind and, if left to my own, could ramble on about.
A key takeaway from your presentation appears to be that the user experience matters because "fun = effective." Does that mean you’re a fan of gamification when it comes to security awareness programs?
Yes, definitely. It’s obvious to me – I’m a gamer. Uh, I’m not a very good one – started too late in life for that – but still. You don’t have to be good at something to still enjoy it, right? So gamification has been my default approach to making training fun. It’s not always possible or necessarily appropriate, but if you find yourself in a position that allows you to get away with gamifying security, then why not? I don’t think it’s necessarily unique to our organization, but generally I think it’s safe to say we enjoy a little friendly competition with one another from time to time. In my mind, gamification is synonymous with competition. So, it’s easy for me to say “Yes, it’s obvious,” especially when I see executives banter with one other about who’s completed their security awareness training first.
How do you make learning fun at Lululemon?
Making security fun is not easy, but it’s a goal worth pursuing.
Fun, by itself, can be tough, so making security fun has to be a really intentional effort since it doesn’t just happen on its own. Last year was a lot of figuring stuff out and seeing what sticks. Everybody enjoys different things and good game design is a discipline all on its own, so I don’t think I’ve found a way to “hit a home run” across the board for everybody yet. But one of the more fun initiatives we did last year was for National Cybersecurity Awareness Month, when we held weekly contests, challenges. These challenges may have been a mini-game or answering a short quiz. If you completed the weekly challenge, then you were entered into a raffle for a prize. The idea was to get them interested and then limit their attention to 10-15 minutes max, like taking a coffee break to learn about security.
It’s a recurring topic, at this point, but at the Leadership Summit, we also had a raffle for the participants there. The raffle required participants to “study” a workstation bristling with security no-nos and then submit their findings into a fishbowl. Before the end of the summit, we randomly drew winners, spot checked their work, and then let them choose from our raffle prize pool. We only printed enough empty lines on one side of the “entry” slip, but some people continued writing additional red flag items even to go so far as to write on the back of the paper slip.
I’d like to move the needle forward and expand from “reward the individual” to “reward the group” because nothing reinforces learning and motivates behaviors better than hearing it from your peers.
This year, strengthening our Secure SDLC [Systems/Software Development Life Cycle] processes is one of top our priorities, specifically at the development/engineering group, our coders. We are taking the initiative for security to “shift left” – which is a tangible place to start ,but the goal is to make security embedded, to exist continuously throughout the SDLC process.
There are still a lot of details that need to be fleshed out about the overall program, but the general idea is that training throughout the year culminates into a year-end practical exercise where our devs can act as “black hat” hackers for a day and score points by identifying and exploiting common vulnerabilities, like OSWAP Top 10, in a controlled, sandboxed environment. If anybody has run an exercise like this before, ping me! Of all the vendors I’ve spoken with, describing it, I get the impression that the concept for a comprehensive program like this program is not as common as I would have thought.
One of your last slides offers a preview of the future of your program. You talk about creating more specialized or focused learning paths/programs for higher-risk employees and executives. What kind of training will that entail and to what extent will you use data/analytics to assess the risk levels of each employee to determine if they need this higher level of training?
There’s a lot to unpack in that question. Anybody who’s already made it reading this far should be commended. I say that meaningfully because, as I may have inferred, an effective security awareness program is always going to be a multi-pronged effort. Because our business is people. And people are different. So it stands to reason, that our approach to how we educate our people should be different as well. Everybody learns at their best differently. Everybody has different constraints that may [relegate] security to the backs of their mind. It’s a natural human behavior to underestimate risks. That’s why we’re here – to make what seems daunting and complex easy and consumable by everyone.
…Start with metrics that other teams are already producing. For SDLC, this could be from your application security team’s bug bounty program or vulnerabilities from code scanning or the amount of time or story points spent by your dev team remediating security bugs or issues.
One of the additional benefits of gamification is that there’s always going to be stats and metrics that come out of it. I’d like to get to a point where I can reward % of reported simulated phish emails across a team, department, office, etc. into a gamified, friendly-spirited competition. So far, we’re on target in improving upon our simulated phishing campaigns from last year by automating the ‘phishing-catching-training’ cycle mentioned on slide 20.
Admittedly, I haven’t deep-dived into the data as much as I want. If the capability maturity model can be compared to Maslow’s hierarchy of needs, then conceptually, I place data/analytics higher up, somewhere near the vicinity of self-actualization. The most basic technology platforms out there will generate a lot of data about your training methods – at least for your online campaigns – so if you’ve got that then you’ll have a wealth of metrics to start with. In all likelihood it’ll be a combination of the individual’s authority and privileges, their likelihood of future and history of preventable incidents (e.g. losing a phone, clicking a link, downloading an attachment, etc.), and what degree of training they’ve received.
…The real question for a security awareness program is to what scale and at what level can you can deliver specialized training to all demographics of your audience. There will always be a need for basic (mass consumption) security concepts like phishing or tailgating. Hopefully in time, these lessons can be relegated to friendly reminders.
Specialized training should be whatever is the most relevant, most specific to the individual. And the more relevant a training becomes, the more likely it’ll stick with the learner. If I could simplify my mental model of CMM for security awareness, it’s three simple levels. Level 1, they know it. Level 2, they do it. And level 3, they tell other people to do it. Getting everybody to Level 3, regardless of where they are in the org, is the mission.



