Mandiant and Google’s Threat Analysis Group this week issued separate blog posts on North Korea’s cyber capabilities in support of its political, financial and national security goals.
In a Thursday post, the Google TAG team reported discovering state-backed attackers exploiting a remote code execution vulnerability in Chrome, CVE-2022-0609. The campaigns, dubbed Operation Dream Job and Operation AppleJues, targeted U.S.-based organizations in the news media, information technology, cryptocurrency and financial tech industries.
The earliest evidence of the exploit was Jan. 4 and a patch was issued Feb. 14. The TAG team said it suspected the groups worked for the same entity with a shared supply chain, but had different mission sets and techniques. The infrastructure of one of the campaigns overlapped with another campaign from last year that targeted security researchers. Google contacted all of the targets notifying them of the activity.
Operation Dream Job targeted over 250 individuals with emails claiming to come from recruiters for Disney, Google and Oracle. The emails spoofed links to job-hunting sites like Indeed and ZipRecruiter. The targets worked for 10 different news media, domain registrars, web hosting providers and software vendors.
Over 85 users in the cryptocurrency and fintech industries were the targets of Operation AppleJues, using at least two compromised fintech sites that hosted hidden iframes to deliver exploit kits. In other cases, trojanized cryptocurrency applications were distributed via iframes in fake websites.
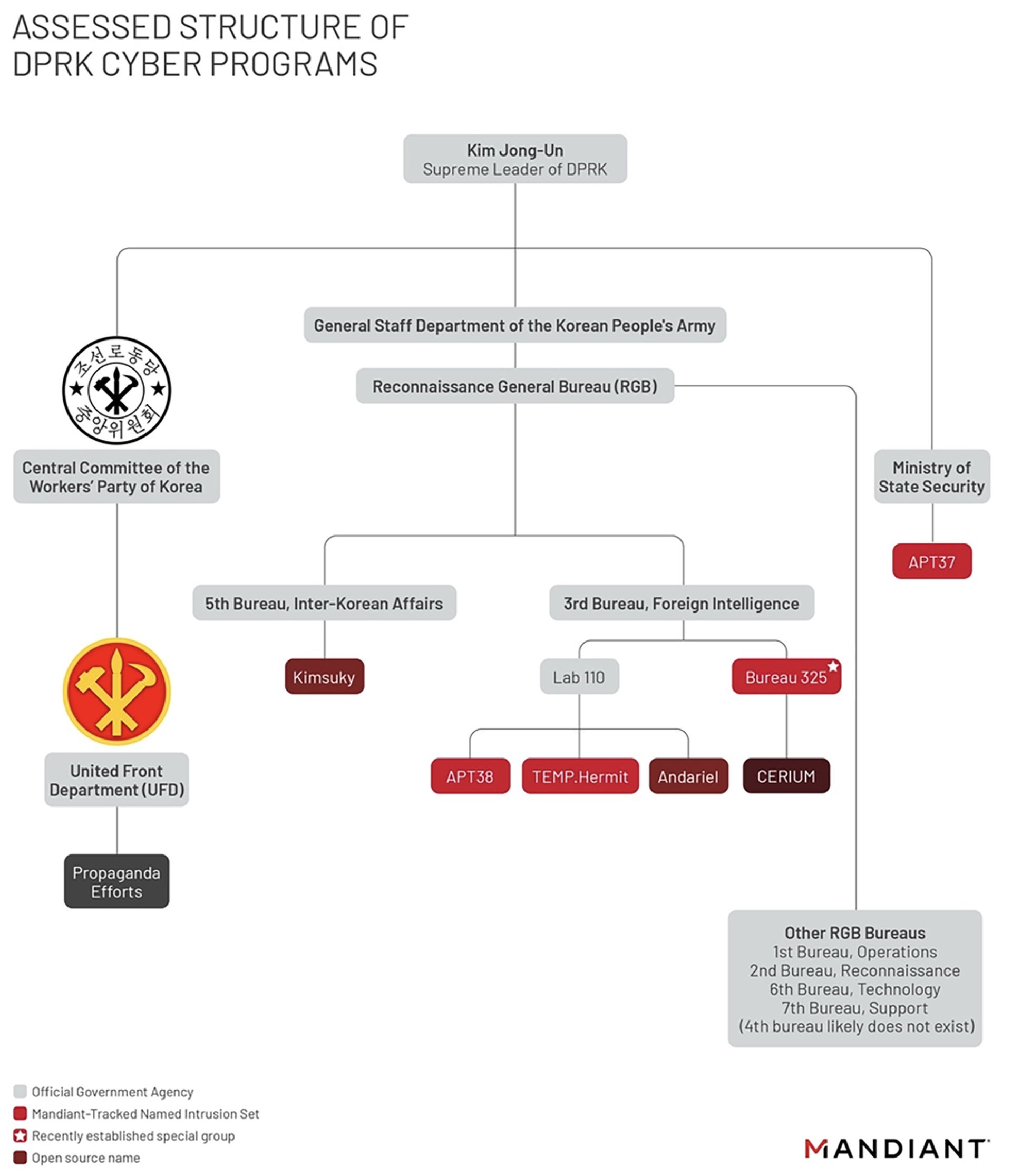
On March 23, Mandiant posted “Not So Lazarus: Mapping DPRK Cyber Threat Groups to Government Organizations,” an organizational chart of North Korea’s threat groups. Numerous North Korea cyber operators are often referred to as the “Lazarus Group” as an umbrella term in open-source reporting, the Mandiant researchers wrote. The cybersecurity firm, however, judges the Hermit Kingdom’s intelligence apparatus to have the flexibility and resilience to create cyber units based on North Korea’s needs.
Mandiant broke down the groups into three organizations that are composed of smaller units with specific missions: the United Front Department (propaganda targeting South Korea), the Ministry of State Security (counterintelligence), and Reconnaissance General Bureau (foreign intelligence). See the chart below: