| Product: RiskIQ PassiveTotal | Category: Attack Surface Management |
| Company: RiskIQ | Review date: April 2021 |

This review is part of the April 2021 assessment of the Attack Surface Management (ASM) product category. If you haven’t read the category overview, you might want to check it out – it explains the category’s basics, use cases, and the general value proposition. Our testing methodology explains both how we interact with vendors and how we tested these products. In short, ASM products aim to discover and manage an organization’s external digital assets. This approach extends far beyond assets with an IP address, however, including everything from certificates to S3 buckets to DNS misconfigurations.
Company background
RiskIQ was founded in 2009 by Lou Manousos, Chris Kiernan and David Pon, all three of whom continue to lead over 200 RiskIQ employees today, with Manousos at the helm as CEO. The company has raised $83m in funding to date with the most recent Series D raised in June 2020. RiskIQ initially focused on digital risk protection (DRPS), looking for malicious use of a company’s brand, or indicators that the infrastructure for an attack campaign is being built.
RiskIQ acquired PassiveTotal in 2015, expanding its use cases into threat research. More recently, with the introduction of Illuminate, RiskIQ also leans more formally into the ASM space, but also builds on PassiveTotal’s focus on threat research. By providing both adversarial threat intelligence, attack surface monitoring and third party risk intelligence, RiskIQ now occupies a unique spread across multiple interrelated customer needs.
Product summary
RiskIQ is well known for its threat intelligence capabilities and massive database of Internet-related artifacts. Notably, RiskIQ has been around longer than most others in the ASM space and has historical data going back over a decade.
RiskIQ is well positioned to step into this market – really, all they needed was to build more ASM-focused front-end tool on top of all the data they already have and it appears that’s exactly what they’ve done with Illuminate. Unfortunately, we didn’t have time to test Illuminate in time for this group test, so this review will focus on PassiveTotal, which has a lot of the building blocks that enable Illuminate’s ASM features.
PassiveTotal is a more than competent attack surface monitoring tool (see the ASM overview for an explanation on the difference between monitoring and management when it comes to ASM). Note that we will specifically be reviewing PassiveTotal from an attack surface perspective – just one of many use cases the tool supports. There are features and functionality that will be beyond the scope of this review to delve into.
However, query results and notifications are comprehensive: it’s a lot of unfiltered, unprioritized data. An analyst might skim results from time to time or do point checks, but it’s inadvisable to try to review every single artifact associated with your organization. Even small orgs can generate tens of thousands of artifacts – especially media and marketing-heavy organizations. If you’re looking for a tool that does the work of floating the most risky assets to the top of a list, RiskIQ’s Illuminate product is designed to meet that need.
RiskIQ is a great example of where the freemium model works best. They’ve built an essential research tool, so even if someone wasn’t interested in their digital risk protection product, when a new offering like Illuminate comes along, RiskIQ has another opportunity to inform and upsell freemium users on new products.
Target market: As a freemium tool, PassiveTotal is used by independent researchers all the way up to security practitioners working for the world’s largest enterprises. The full-featured research tool is within reach of anyone that needs questions answered about digital assets exposed to the public Internet.
Time-to-value: PassiveTotal queries an existing database of Internet artifacts – it’s possible to enter queries and start analyzing results within seconds of logging in. When using it as a monitoring tool, it might take 20-30 minutes to build out a list of public assets to monitor.
Maintaining value: A few hours each week to review new assets as notification emails are received. Consider monthly reviews of monitored assets and update as necessary.
Strengths: Massive data repository with historical records going back over a decade. No restrictions on querying RiskIQ’s data, which opens up third party analysis use cases. PassiveTotal includes the ability to share projects which fosters a valuable intelligence sharing community that PassiveTotal users have access to.
Weaknesses: Artifacts are often too spread out across multiple tabs and views to get the “big picture”. Reputation scoring logic is… questionable.
Conclusion: Even if you’ve already settled on a different product for your attack surface management/monitoring needs, PassiveTotal is an essential research tool that few others can match or compete with, at least, starting at a price of $0.
Deployment and configuration
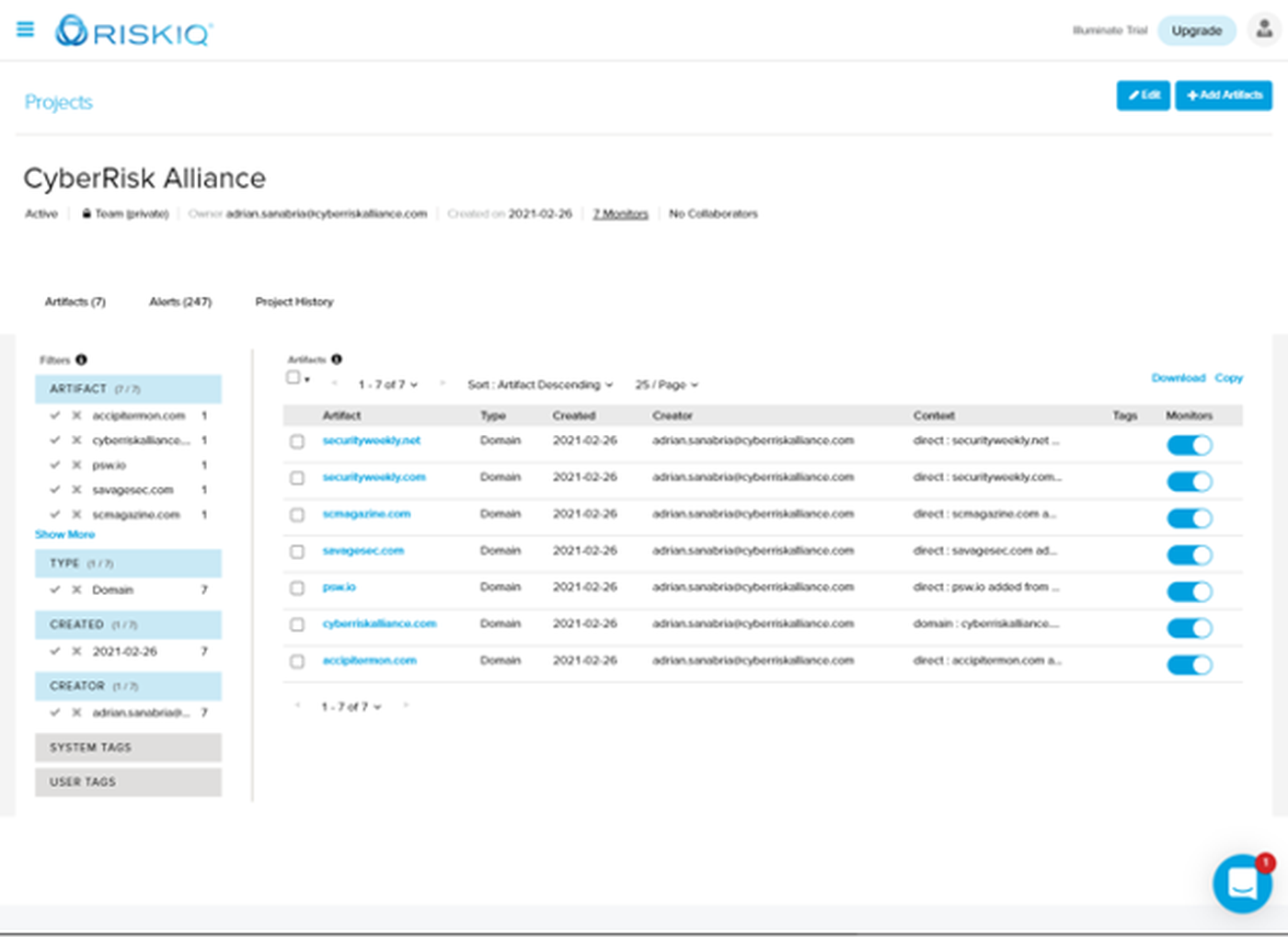
After creating an account (which anyone can do, PassiveTotal is a freemium product), monitoring assets is as simple as performing a search on a domain and adding it to a project. Note that what we typically call “assets”, PassiveTotal refers to as artifacts.
A list of monitored artifacts is easy to build and manage.
Usage
Using PassiveTotal as a monitoring tool is a three-part act. Perform an initial search on a domain or asset to view the relatively new overview summary. This includes some of the more interesting artifacts and a reputation score.
We’re not terribly impressed with the logic that goes into building the reputation score, however. Buy your domain names at NameCheap or Gandi? You’re “more likely to be malicious”. After testing a few dozen domains, the reputation score appears to be entirely based on where you shop for domain names. We all have friends that shop at Walmart, but does that mean we should reconsider hanging out with them?
We promise we’re not taking this personally (our product testers personally use both NameCheap and Gandi), but feel like a reputation score should be based on a bit more than choice of registrar, name server and email provider.
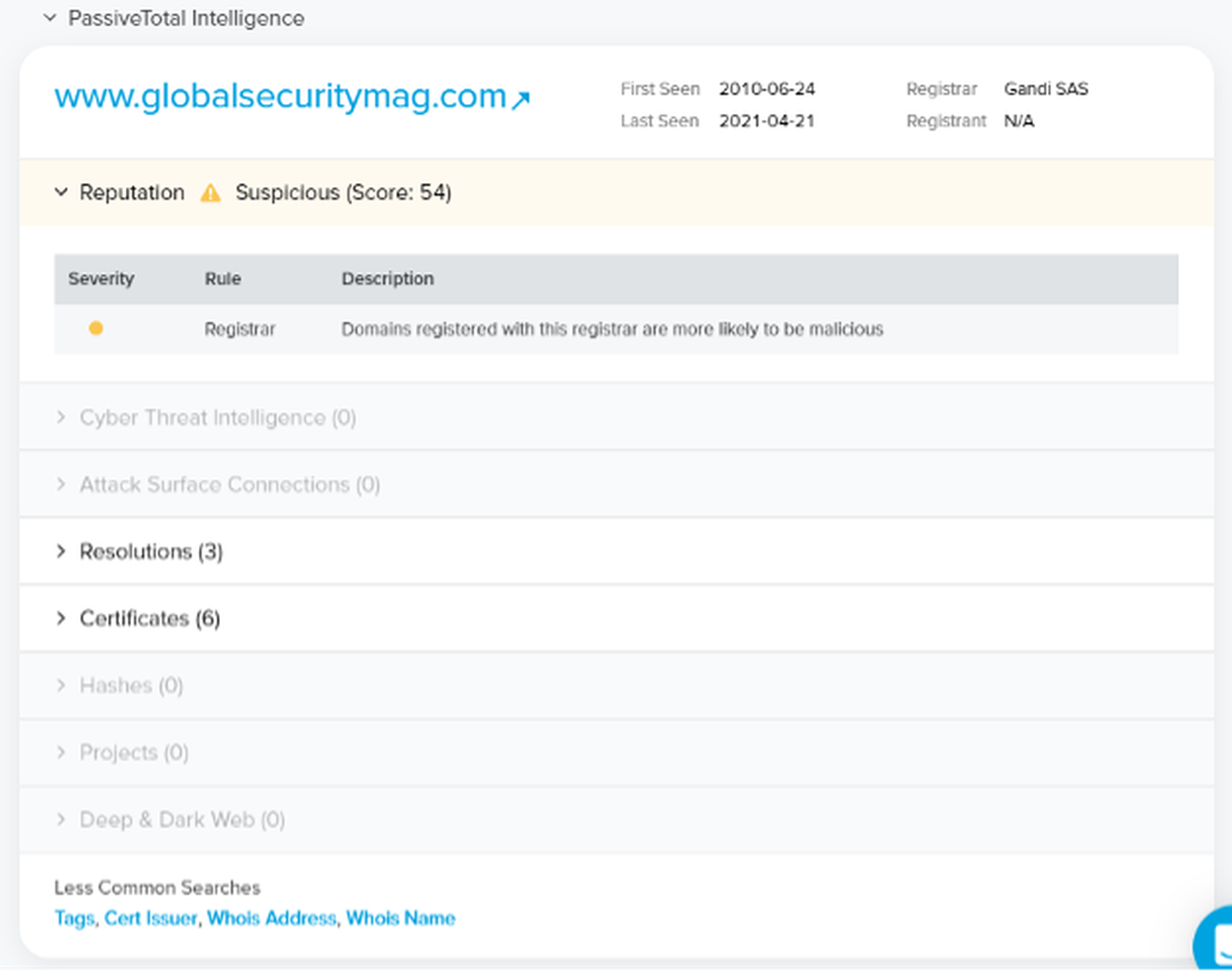
Clicking on the domain name (with the arrow), takes us to a screen very familiar to anyone that has used PassiveTotal. A lot of information is packed into this one window and it’s where the bulk of research and analysis is done. The data here can be filtered by tags, asset attributes and timeframes. RiskIQ automatically adds ‘analyst insights’ and insightful tags that indicate where the associated IP addresses are hosted, among other things.
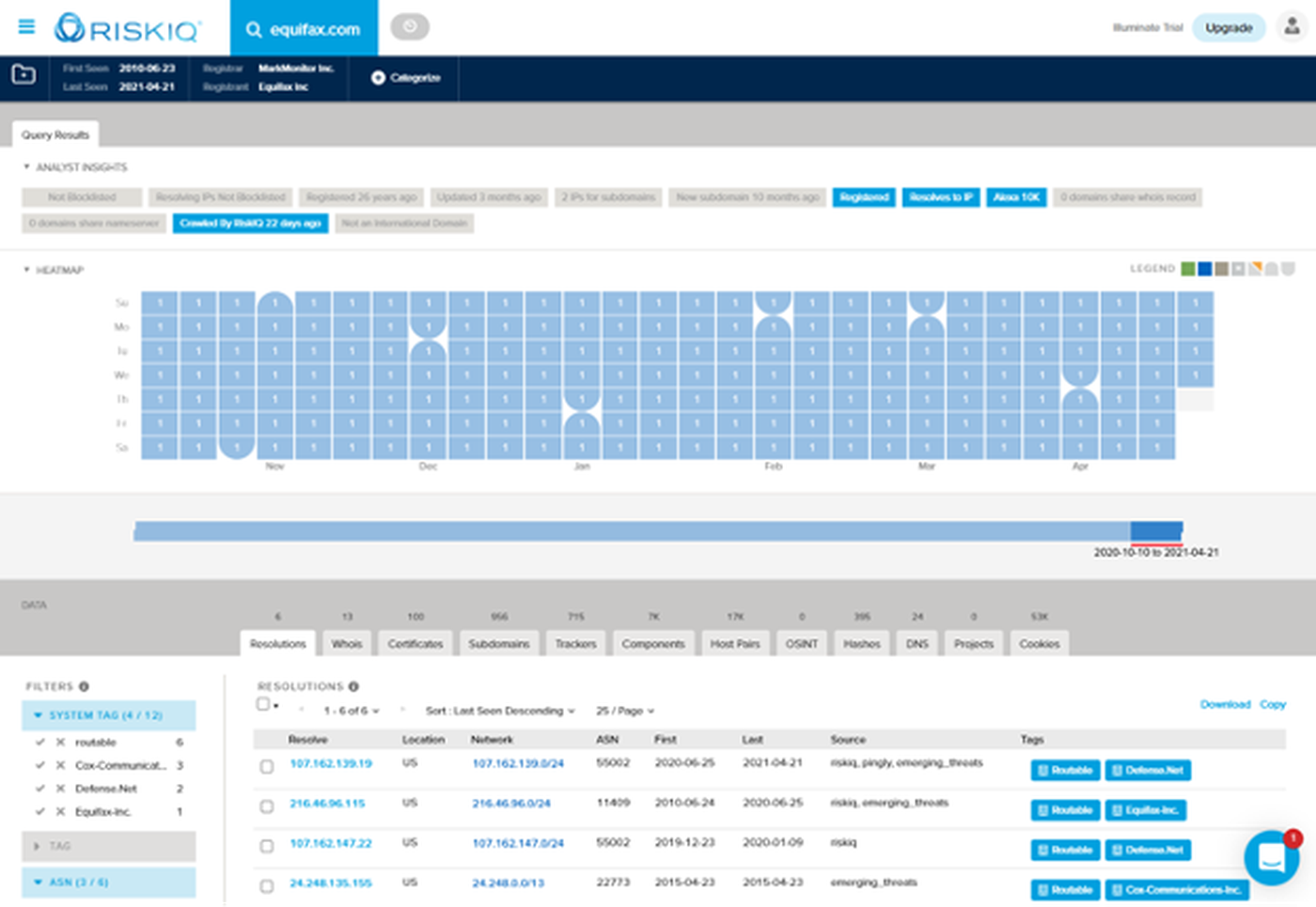
It’s worth digging into some of the data types available here. DNS records, WHOIS records and certificates, when paired with historical context can be instrumental in an investigation, when simply trying to understand when a change took place or can alert analysts to new assets coming into use. Subdomains are always a great place to find old and abandoned projects that should have been decommissioned years ago. “Host pairs” can draw attention to third party relationships, partners or integrations.
Stepping up into the application layer, Trackers uncover relationships between social media accounts and marketing tools. Components expose the specific hosting, cloud and software technologies in use on assets. RiskIQ even catalogues Cookies, which lays claim to its own tab on the analysis page.
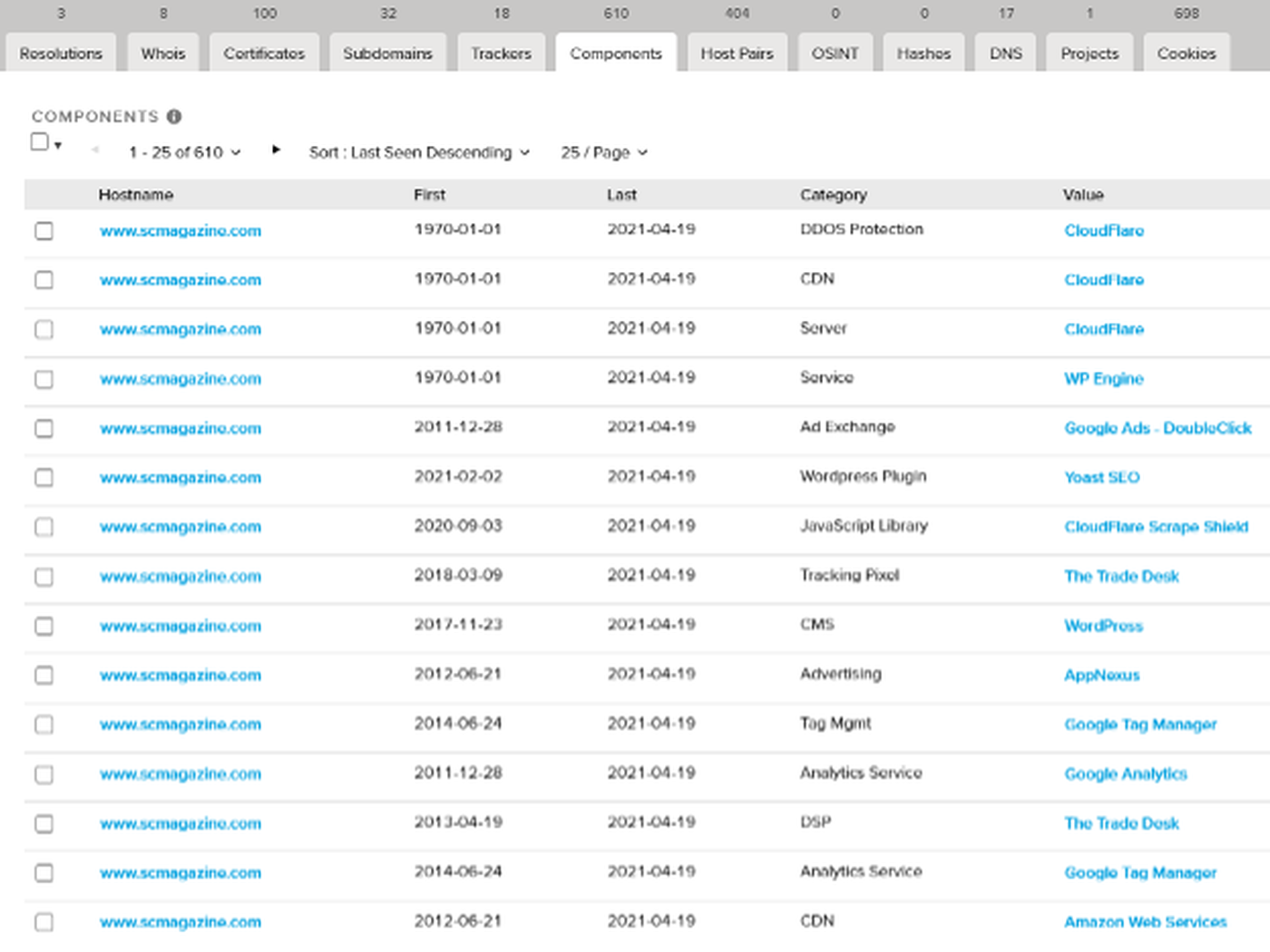
Data from any of these views can be downloaded for offline analysis, or importing into another tool or application.
In addition to analysis, it is possible to report domains as malicious from this view. This is also where we can add this artifact to one of our projects, by clicking the folder in the upper left corner.
Once added to a project, PassiveTotal will send regular email digests with a summary of new artifacts discovered.
Notable Integrations
- Splunk (SIEM/SOAR)
- CRITs (Threat Intelligence)
- MISP (Threat Intelligence)
- Maltego (OSINT Gathering)
- CrowdStrike (EDR, Threat Intelligence)
- Microsoft Azure Sentinel (SIEM/SOAR)
- Palo Alto XSOAR (SOAR)
- SpiderFoot (OSINT Gathering)
- ThreatQuotient (Threat Intelligence)
- ThreatConnect (Threat Intelligence)
- EclecticIQ (Threat Intelligence)
- Anomali (Threat Intelligence)
- TruStar (Threat Intelligence)
Claims
“PassiveTotal simplifies the event investigation process.”
“Security intelligence that scales security operations and response.”
“Attackers have nowhere to hide.”
After the first two claims, we were worried we’d have nothing to fuss about! Both are fairly conservative claims and the tool easily meets the expectations they set. As for leaving attackers nowhere to hide, that might be stretching things a bit. RiskIQ’s dataset is admittedly vast, but somehow, attackers still manage to evade us from time to time.
Roadmap
RiskIQ recently added Illuminate, which we will review when we next revisit the ASM market for a group test.
Security program fit
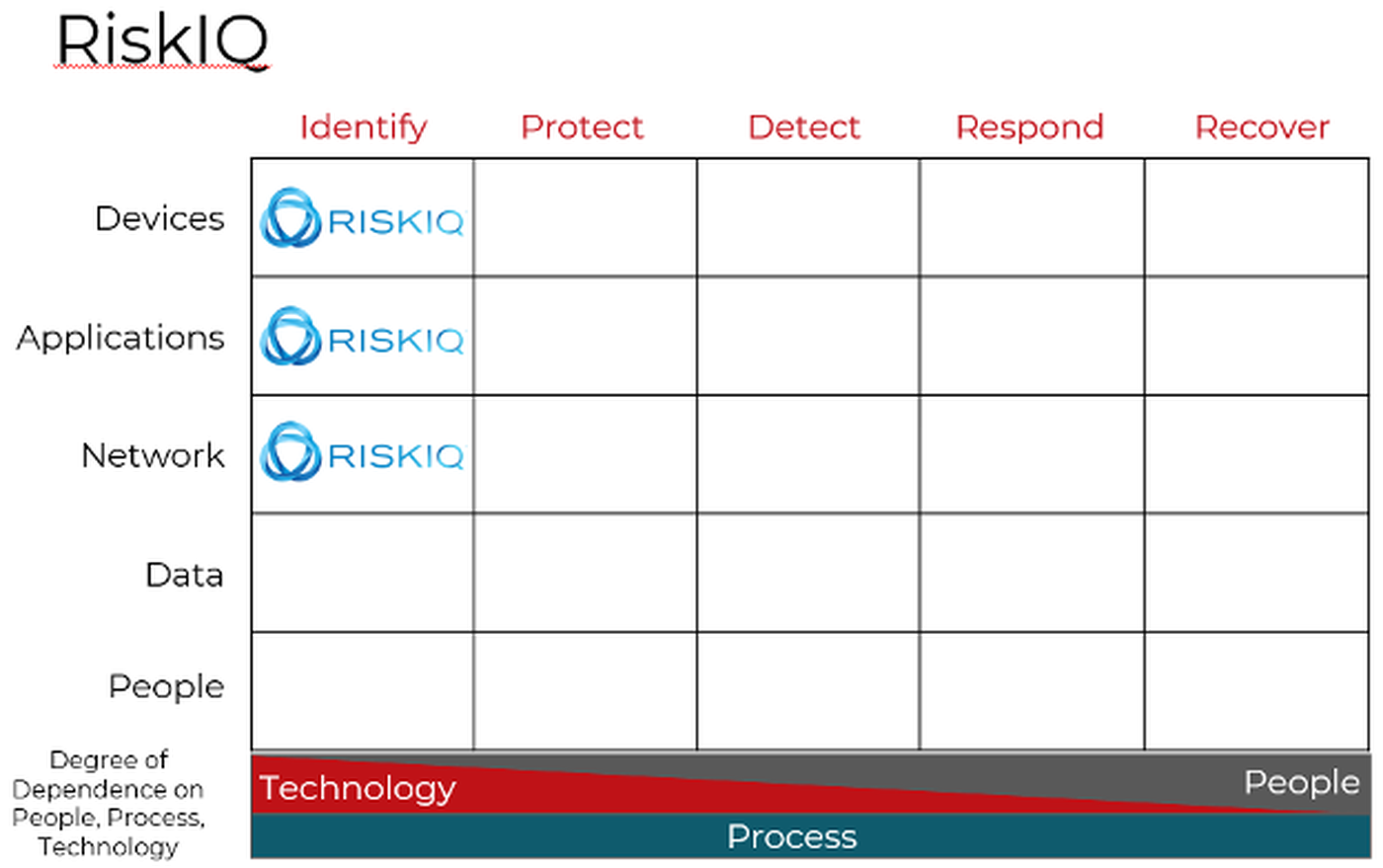
RiskIQ, like other products focused on discovering vulnerabilities and misconfigurations, fits solidly within the Identify column of the Cyber Defense Matrix.
Conclusion
RiskIQ’s PassiveTotal is an amazing tool for nearly any research task involving infrastructure connected to the Internet, either now or in the past. It is less useful for monitoring an internal inventory, as it is optimized for research workflows and not inventory management. This isn’t a knock against the product, it is excellent at what it was designed for. The company has released a new product that may fill this gap. We’ve had a peek at RiskIQ’s Illuminate product, however and look forward to checking out some of the new attack surface monitoring functionality in the future.


