Cloud technology and cloud security are not inherently synonymous. There are many ways in which cloud service implementation can go awry. In case you missed it, learn more about the challenges facing public cloud security with the first installment of our three-part series on the ins and outs of public cloudsec.
Remediating vulnerabilities and rectifying areas of weakness in an organization's cloud network is a top priority for cybersecurity. In this second installment, we’ll focus on 5 ways that organizations can address the challenges of the public cloud and improve their overall cloud security posture.
5 steps to securing public cloud
While these steps aren’t intended to be an exhaustive summary, they should provide solid footing for organizations to better understand their environment, mitigate risk where possible, and identify a plan for continuous improvement.
#1: Cover your bases with cloud risk management
You could make the case that risk management is the first and most critical step to getting public cloud security right. If this one fails, the whole operation is doomed. Organizations must understand how their risk profile changes when they move to the public cloud, and then set appropriate controls and responsibilities to account for such risk. A strong risk management policy should be able to address various items such as:
- Accountability: Define roles and responsibilities of key cloud stakeholders (e.g. cloud security architect, cloud developers, IT operations, security)
- Definitions: Map out risk scenarios and determine criteria for prioritizing multiple types of risk
- Procedures: Understand the steps involved in discovery, reporting, remediation, and resolution
- Controls: Clarify default organizational policies as well as any rules exceptions
- Communication: Clarify team structures and opportunities for cross-team coordination and feedback loops
There’s a wealth of resources organizations can draw on to craft risk management policies that address their cloud security needs. Some of these include:
#2: Establish continuous visibility of cloud assets
Organizations need visibility over the entire cloud inventory. Otherwise, they run the risk of fielding misconfigurations and unpatched vulnerabilities in the wild.
The cloud’s dynamic, decentralized and distributed model allows for thousands of instances and accounts to run at the same time, substantially expanding the attack surface and multiplying blind spots that conventional network monitoring tools can’t reach.
To address the visibility gap, organizations should strongly consider capabilities that enable continuous inventory discovery and asset management. These provide several benefits — continuous monitoring and discovery of cloud assets entering the environment, a unified dashboard where multiple teams can make decisions based on shared intelligence, and the ability to aggregate analytic data on assets that span multiple cloud environments. This helps teams better identify misconfigurations, allocate resources more efficiently, track changes in cloud assets over time and respond cohesively as a single unit.
#3: Train developers to recognize and eliminate cloud security risks
There’s been a lot of talk about infrastructure-as-code, which effectively means provisioning cloud infrastructure as code so that teams can automate config and controls at scale rather than individually and manually. It’s an outstanding feature, but it only works if developers are given the tools to proactively ‘own’ and test code before it goes to production. Aside from offering instruction in cloud security fundamentals, it’s highly recommended that organizations adopt DevSecOps practices and eliminate the mindset that security is the sole responsibility of any one team.
Due to the rapid speed that cloud-native components can deliver (via Kubernetes, serverless functions, APIs), organizations don’t have the luxury to bolt on security after runtime, especially considering the recent acceleration in zero-day exploits. A cloud security posture management tool, or CSPM, is good at detecting misconfigurations, but generally only much later in the SDLC. By shifting security responsibility of IaC templates into developers’ hands and automating security assessments, organizations can significantly reduce the risk of misconfigured code altogether.
#4: Enforce multifactor authentication as part of a zero trust policy
The public cloud has put a spotlight on how critical it is to get identity and access right. Across the industry, the number of identities that organizations must manage have significantly increased as a result of cloud adoption. In the last year alone, 84% of security professionals claim to have weathered identity-related attacks on their organization, according to the Identity Defined Security Alliance (IDSA).
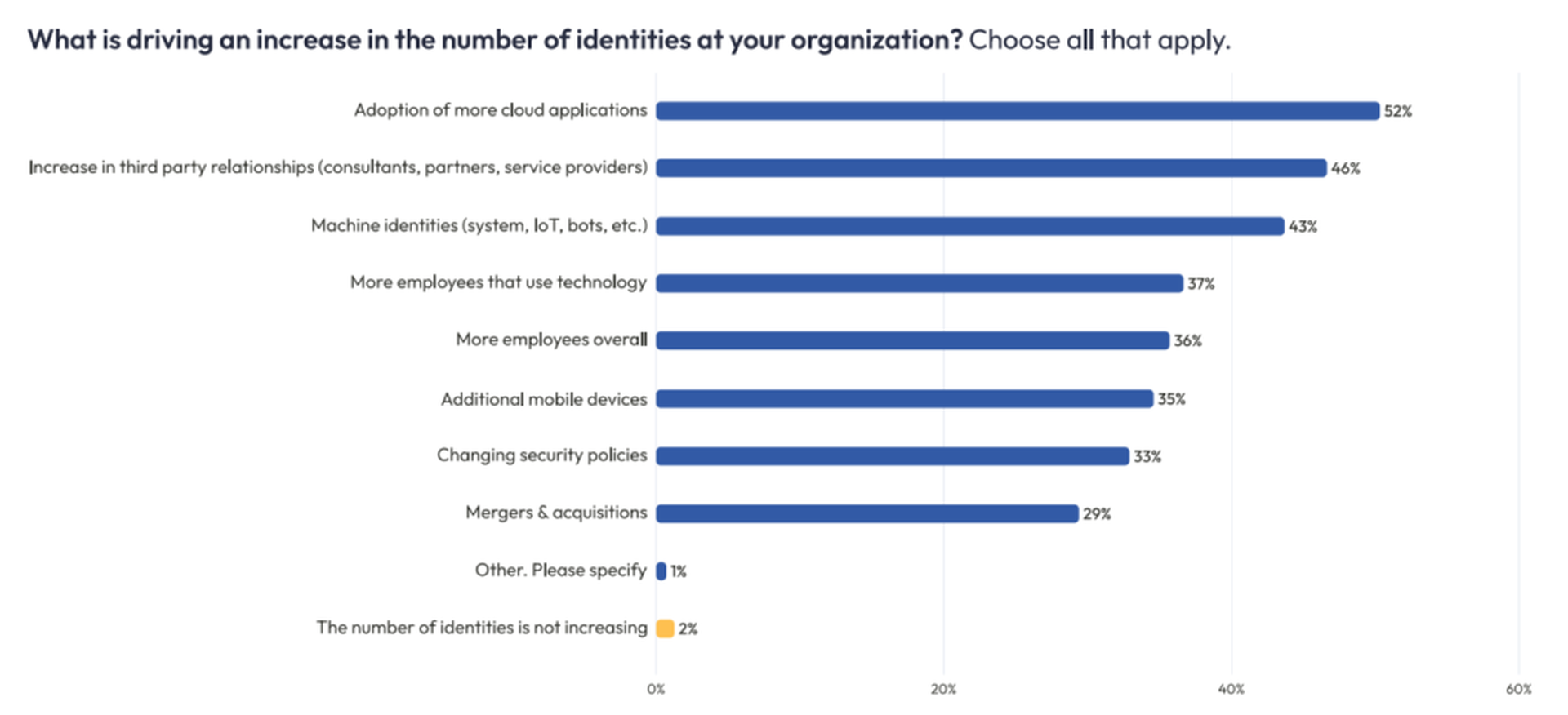
There are different ways an organization can secure identities in the cloud. Multifactor authentication should be a no-brainer: By insisting that users verify their identity through two or more forms of authentication, organizations can drastically reduce fraudulent sign-ins and credential-based attacks. Alongside MFA and least privilege access, zero trust policies can help organizations specify granular access controls that are better suited for the dynamic, distributed properties of cloud-native applications. ZTA technologies also offer a combination of encryption, network segmentation, endpoint protection and authentication functions that are indispensable for the public cloud.
#5: Simplify cloud security governance with a CNAPP
Public cloud security is an all-hands-on-deck matter, demanding collaboration and open lines of communication between teams that have historically operated separately. For example, developers need to understand secure code design to prevent misconfigurations. Security needs to get on the same page as developers when it comes to risk assessment and remediation priorities. And non-IT business units are responsible for following cyber hygiene in moving workloads to the cloud.
It’s very easy for public cloud security to suffer from the ‘too many cooks in the kitchen’ dilemma, as multiple teams interact with multiple tools across multiple cloud environments from multiple locations.
To dramatically simplify cloud security oversight and operations, organizations should consider using a cloud-native app protection platform, or CNAPP. The concept of a CNAPP, originally conceived by Gartner, describes a unified platform that combines the capabilities of several existing cloud security categories, mainly “shift left” artifact scanning, cloud security posture management (CSPM), Kubernetes security posture management (KSPM), IaC scanning, cloud infrastructure entitlements management (CIEM), as well as runtime cloud workload protection platform (CWPP). Essentially, it’s like a Swiss army knife for the cloud, unifying all your disparate cloud security functions and needs in one place.
While the idea of a CNAPP is relatively recent, more cloud security vendors are beginning to offer a platform suite of tools that provide all the associated features and benefits of a CNAPP.
Straight from the experts
For more tips on how to secure the public cloud, check out our upcoming third installment where you can catch recommendations and insights from the cloud security experts SC Magazine spoke to.




