You could say it’s the new cyber security motto: Don’t trust anyone — or anything — trying to access your network. This concept is at the heart of the zero trust security model, which is rapidly gaining momentum at many businesses and government agencies.
The concept continues to mean different things to different people, and as a result confusion persists among security leaders and teams as to how best to implement it. Indeed, a recent study from CRA Business Intelligence illustrated the challenge, with only 35% of the 300 security decision makers and influencers who participated in the study saying they are “very familiar” with zero trust concepts.
But when used properly, zero trust can spare incident response teams a lot of headaches when it comes time to investigate a potential compromise.
Click here for SC Media's eSummit "Implementing a Zero Trust Architecture."
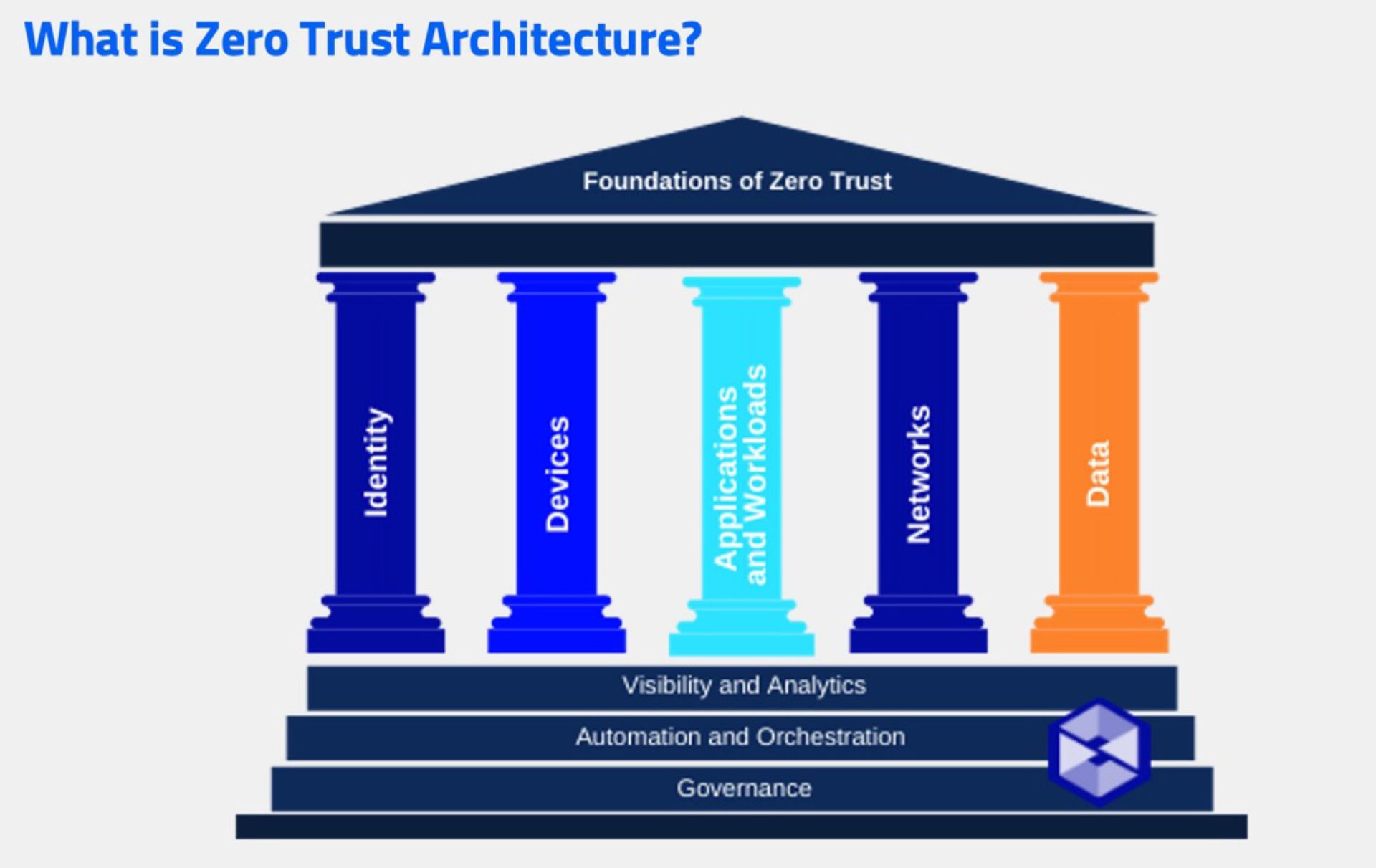
Pillars of zero trust
To better understand zero trust, think of it as a structure held up by five pillars, as this visual demonstrates:
One of the most widely used definitions comes from the National Institute of Standards and Technology (NIST):
“Zero trust is the term for an evolving set of cyber security paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources. Zero trust assumes there is no implicit trust granted to assets or user accounts based solely on their physical or network location.”
How it helps with incident response
One of the areas of cybersecurity where zero trust can play a key role is incident response (IR). A big part of the zero-trust framework is that you know all the devices that are in your network, and you are tracking them on a constant basis. You can respond to all those devices when something does not seem right.
Another aspect of the zero-trust framework related to IR is the establishment of a “base normal” — what your network looks like when there is no breach underway. This enables security teams to identify anomalies when they occur, whether they are coming from inside or outside the organization.
Zero Trust Network Access (ZTNA) solutions create logical access boundaries around applications, based on identities and context. With ZTNA, applications are hidden from discovery and access is restricted — via a trust broker — to a set of named entities, according to research firm Gartner.
Such a broker can verify the identity, context and policy adherence of particular users before granting access, and prohibits lateral movement elsewhere in the network. This significantly reduces the surface area for attack.
Challenges to watch for, tools that help
While ZTNA can help organizations increase control over their security infrastructures, it does create challenges to internal digital forensics and incident response (DFIR), such as the inability to collect data from remote endpoints when needed. Following incidents, security teams need to be able to collect the related data including what happened during the incident and immediately before it, to analyze the data so they can remediate the problem.
Organizations should consider deploying IR solutions that can collect data from any zero-trust platform, quickly identify and understand an activity that’s putting an organization at risk, and formulate a plan to stop the activity before it becomes an issue.
Such platforms also provide teams with the ability to preview and collect triaged and needed data from endpoints, using agents that run on the endpoints. This can save many hours in an investigation where timing is extremely important.
Conclusion
Zero trust security architecture will continue to gain momentum at many organizations, and with good reason. There are simply too many endpoints and too many risks for security leaders and teams to trust entities trying to gain access to networks.
Organizations must continue to gain a better understanding of how zero trust works and follow the NIST guidelines that have helped security teams to be successful.
Once that is done, zero trust will benefit IR programs. Solutions like those mentioned above will provide the automation necessary for effective e-discovery and IR response workflows via application programming interfaces (APIs) and provide organizations with the ability to quickly investigate and address incidents.
From there, organizations will be in a much better position to thwart attacks.




