In 2022, security practitioners struggled to address the growing attack surface created by their rapid push to remote work and cloud-based operations during the previous two years. Cyber criminals exploited new vulnerabilities – including those introduced by the growing use of third-party software – to launch ransomware and other attacks.
But with tools like zero trust, XDR and more automated threat intelligence tech to bolster vulnerability management, cloud, email and endpoint security, organizations fought back – and established plans to invest more to secure networks and data in the next two years.
Click here to download the full 2022 Cybersecurity Year in Review Report from SC Media.
The following is the first of a seven-part series about where security practitioners struggled and, in many cases, made headway throughout 2022. Here, we focus on their zero trust challenges.
Zero trust gridlock
Massive security vendor hype surrounded zero trust in recent years, with many claiming to have the solutions to enable zero trust out of the box. Given the market saturation — and a mandate from the Biden administration for federal agencies to implement zero trust — one could reasonably expect most organizations to be well on their way.
But in 2022, organizations instead found themselves caught in stiff headwinds.
This was especially true for federal agencies. In June, for example, the Center for Strategic and International Studies released a report that took a hard look at the implementation challenges surrounding zero trust efforts, which included things like encryption, multi-factor authentication and improved logging that should have been done years ago.
Similarly, a September 2022 survey of 216 security practitioners conducted by CyberRisk Alliance (CRA) Business Intelligence found those difficulties affecting organizations across multiple industries. Respondents described a host of challenges slowing their integration of existing systems into an overall zero-trust framework, including the shift from a legacy “all access” identity and access model to one that is limited to just what is needed.
During the study, only one out of four respondents reported their organization had implemented zero trust.
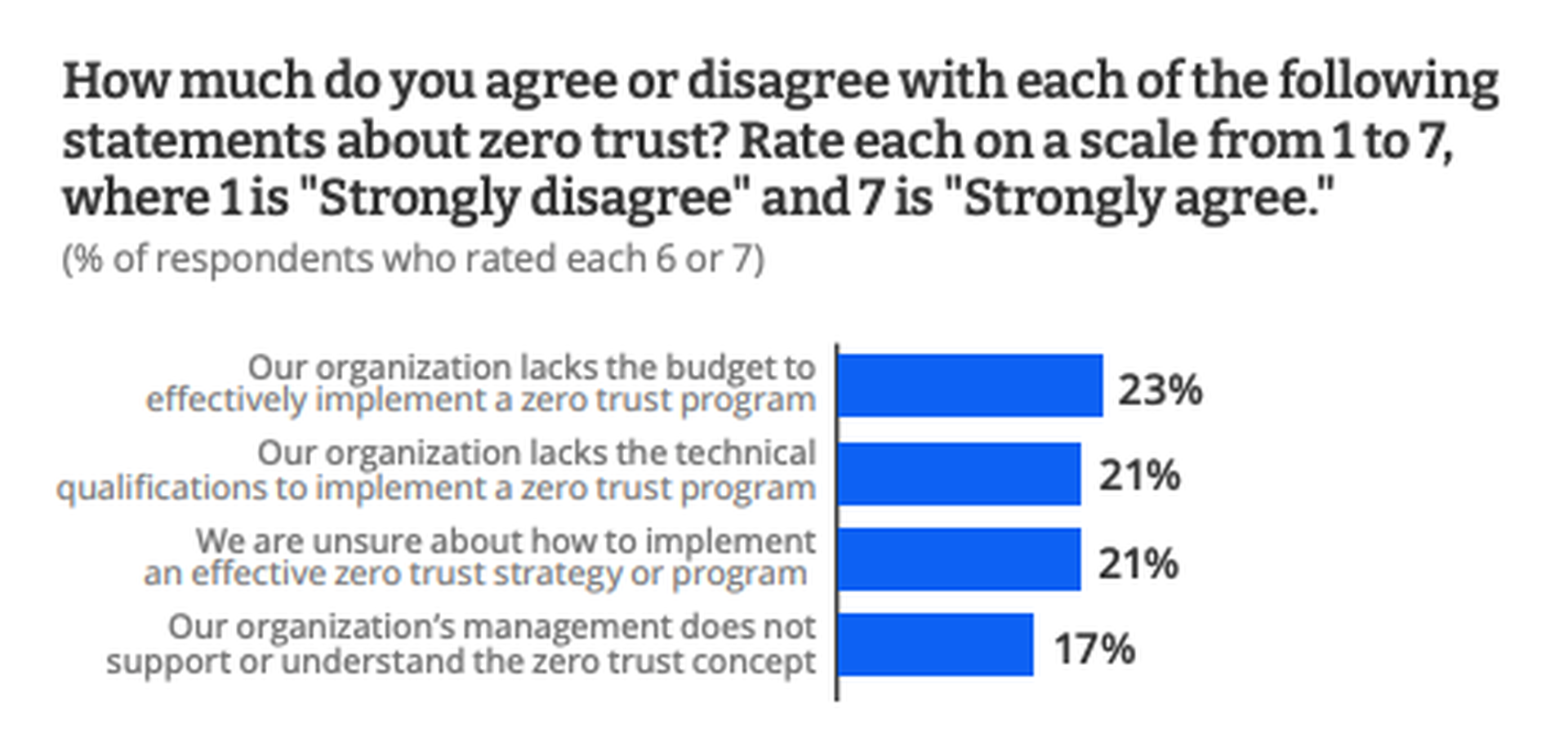
Those who hadn’t made the leap to zero trust in 2022 said the transition was just too difficult and wouldn’t be effective at their organization. Others said budget limitations and inadequate staff to provide oversight or support for a zero-trust model kept them from adopting it. The most prevalent obstacles in adopting zero trust, however, were the lack of knowledge about the framework and lack of buy-in from senior management.
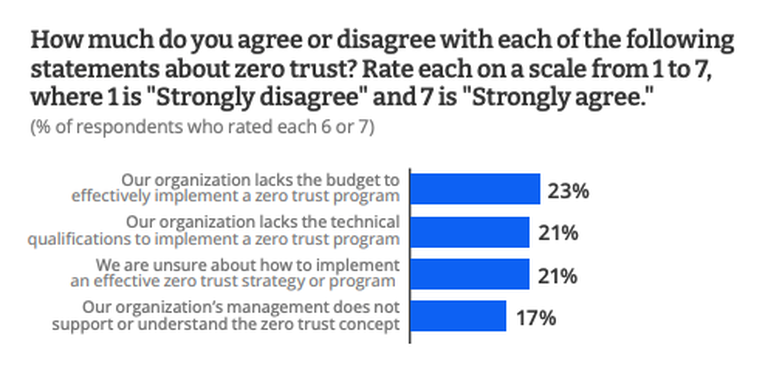
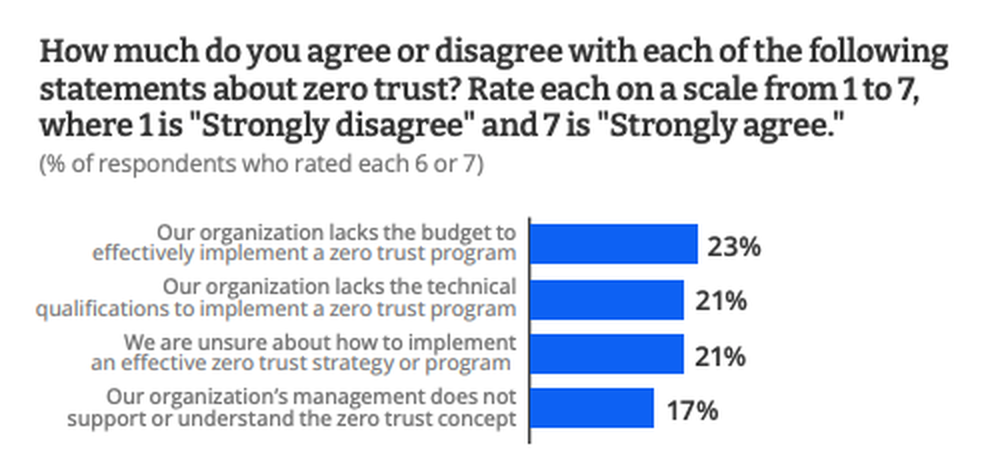
As one respondent put it, “Technical execution seems to be the most challenging part. Making sure we’re able to gracefully convert from a trusted environment to zero trust is what’s taking the most time.”
An SC Media article about zero trust efforts among federal agencies noted that initiatives were clashing with longstanding cultural and budgetary problems plaguing federal IT teams, a problem shared by the CRA survey respondents from other industries.
Said Suzanne Spaulding, former head of CISA’s predecessor agency the National Programs and Protection Directorate: “We have a tension here, because part of what we also need to do is make sure Congress really gets it that this is a multi-year effort and that they can’t be demanding [at the end of this year] ’Why haven’t you migrated completely to a zero-trust architecture yet?’”
Zero trust successes
Despite the headwinds, the news about zero trust in 2022 wasn’t all bad. Leading the way in implementation were organizations CyberRisk Alliance Business Intelligence called “zero trust champions.”
In September, slightly more than half of respondents fit the champion mold based on their status for implementing zero trust and their overall perception of its importance in their zero-trust strategy.
Meanwhile, even among those who face zero-trust headwinds, plans were afoot to ramp up spending on zero trust expertise and technology. The challenges are many, but most organizations expressed a determination to ultimately adopt zero trust in 2023 and beyond.
In October 2022, Gartner cited ramped up zero-trust implementation as one of the reasons spending on information security and risk management products and services would grow 11.3% in 2023, reaching more than $188.3 billion. The research and consulting firm identified three factors influencing growth in security spending: the increase in remote and hybrid work, the transition from VPNs to zero-trust network access, and the shift to cloud-based delivery models.
“The modern CISO needs to focus on an expanding attack surface created by digital transformation initiatives such as cloud adoption, IT/OT-IoT convergence, remote work, and third-party infrastructure integration,” said Ruggero Contu, senior director analyst at Gartner. “Demand for technologies and services such as cloud security, application security, zero-trust network access, and threat intelligence has been rising to tackle new vulnerabilities and risks arising from this exposure.”
CRA respondents agreed, with one saying of the zero-trust component: “There has been a slight learning curve and hurdles to implementing zero trust, but the benefits are worth it.”




