IT personnel working the trenches in the fight against malicious emails know that financial transactions -- and the various documents that support and accompany those transactions -- provide malicious actors seemingly endless fodder for clever phishing attacks designed to separate legitimate organizations from their money and reputations, as well as their customers, clients, and partners.

Indeed, fake invoices, RFQs, POs, ACH documents, and remittance forms collectively constitute the "social engineering" backbone of innumerable phishing campaigns. And hapless employees keep falling for them, clicking through malicious links and opening malware-laden attachments -- often with nary a thought to the potential consequences -- bringing malicious actors and their sophisticated malware inside their employers' networks.
Over the past few months we have observed the increasing use of yet another type of transaction-based social engineering scheme designed to hook companies dependent on government contracts: the invitation to bid. In what follows, we'll take a look at a number of actual phishing emails reported to us by customers using the Phish Alert Button (PAB).
The Evolution of the Fake Bid Phish
Fake bid invitations have been around for a while, to be sure. In many respects, they are a natural variation of the fake RFQ, which leverages a targeted organization's search for new business to dupe its employees into opening the digital door to security breaches, costly down time, and financial mayhem.
Consider this confused, yet highly malicious phishing email, which can't seem to decide whether it's a fake PO or fake RFQ:
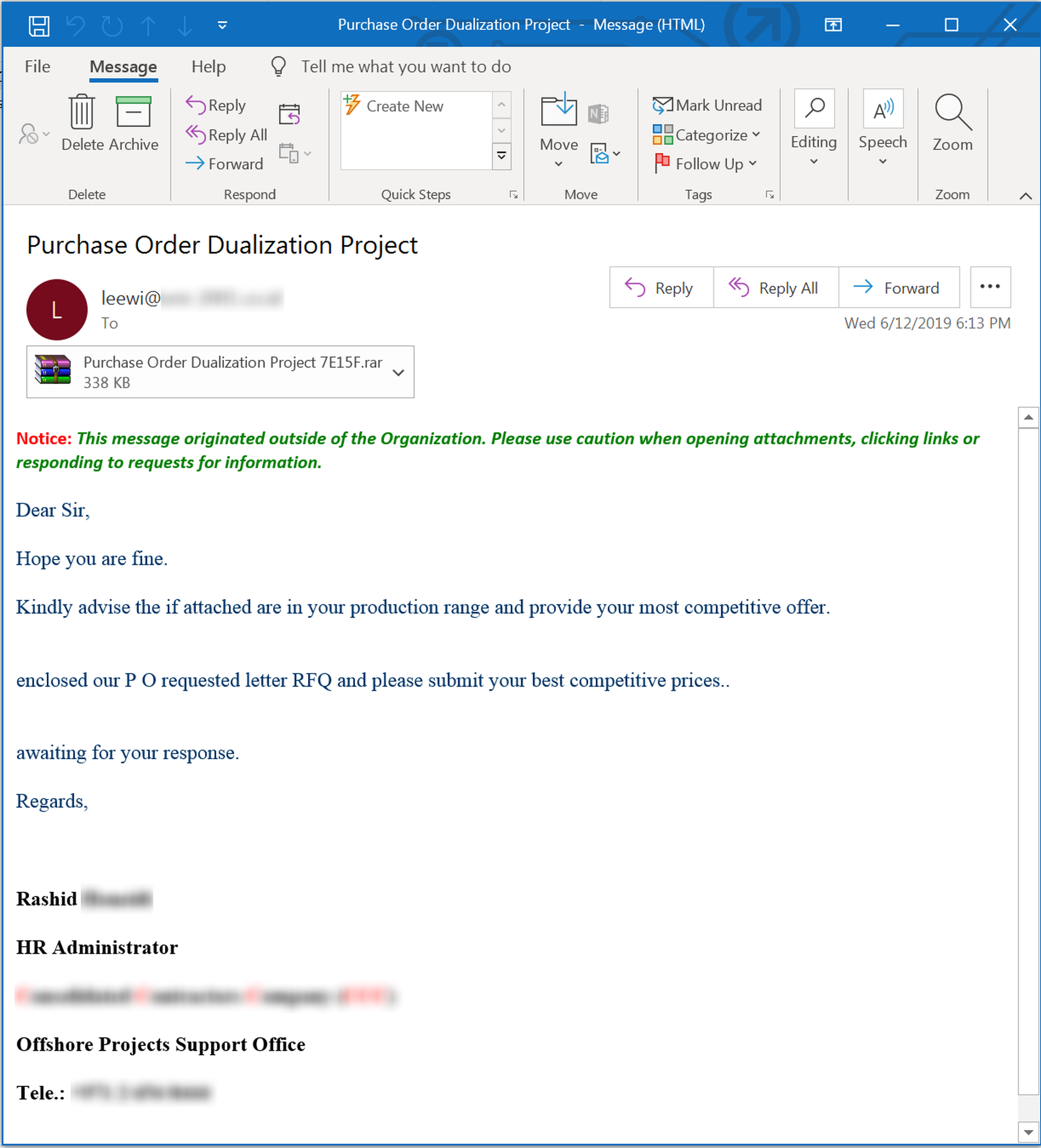
Despite the obvious mechanical stumbles in the email body, this phish fairly represents the blizzard of fake RFQ emails currently hitting users' inboxes. And it packs a mighty wallop in the attached .RAR file:
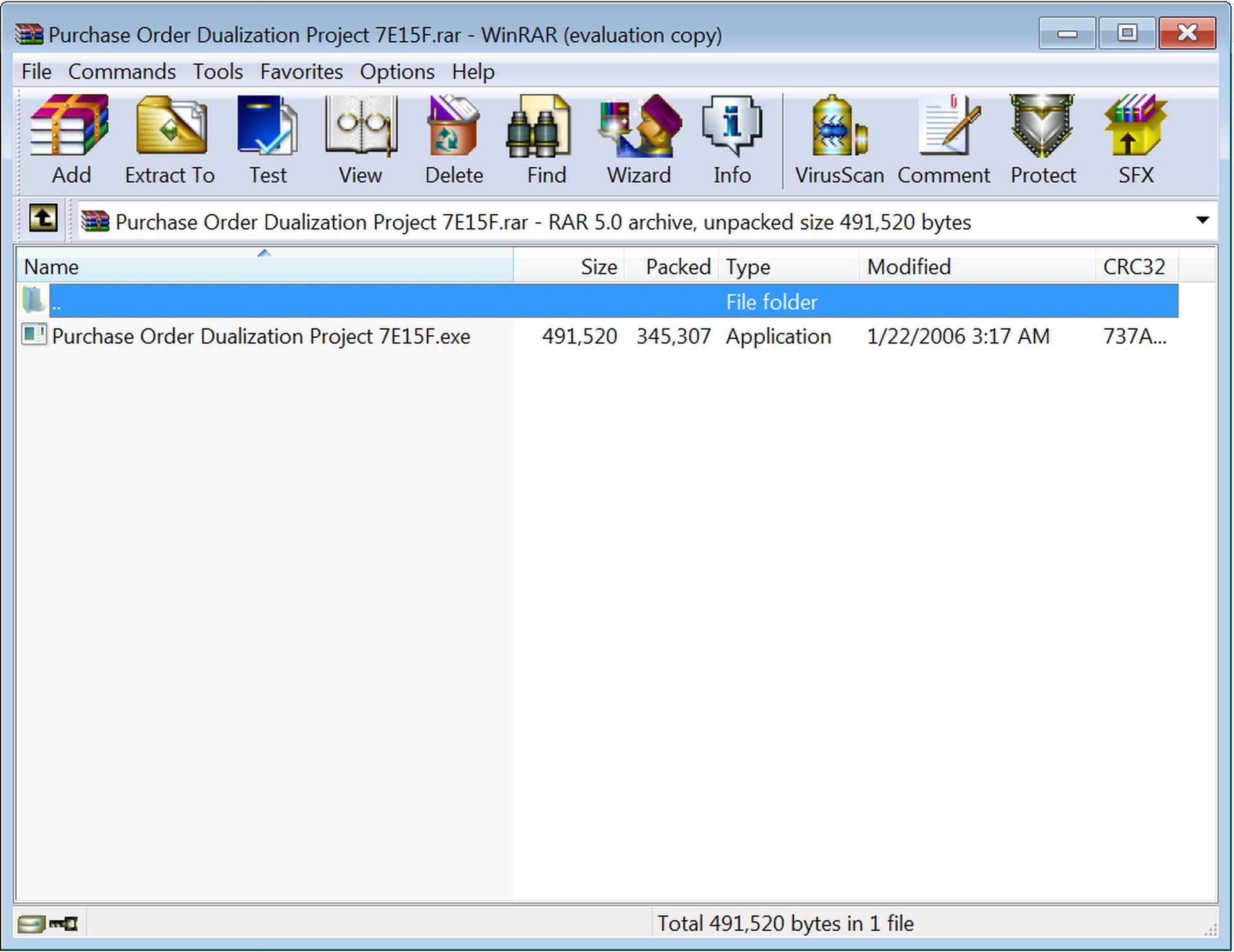
That's right: a good old-fashioned executable backdoor trojan. (And you thought those were going out of style!)
From that humble fake RFQ, though, it's just a hop, skip, and jump to this more polished fake "invitation to bid" on a potentially lucrative "airport project" allegedly being run by a well-known, upscale hotel chain.
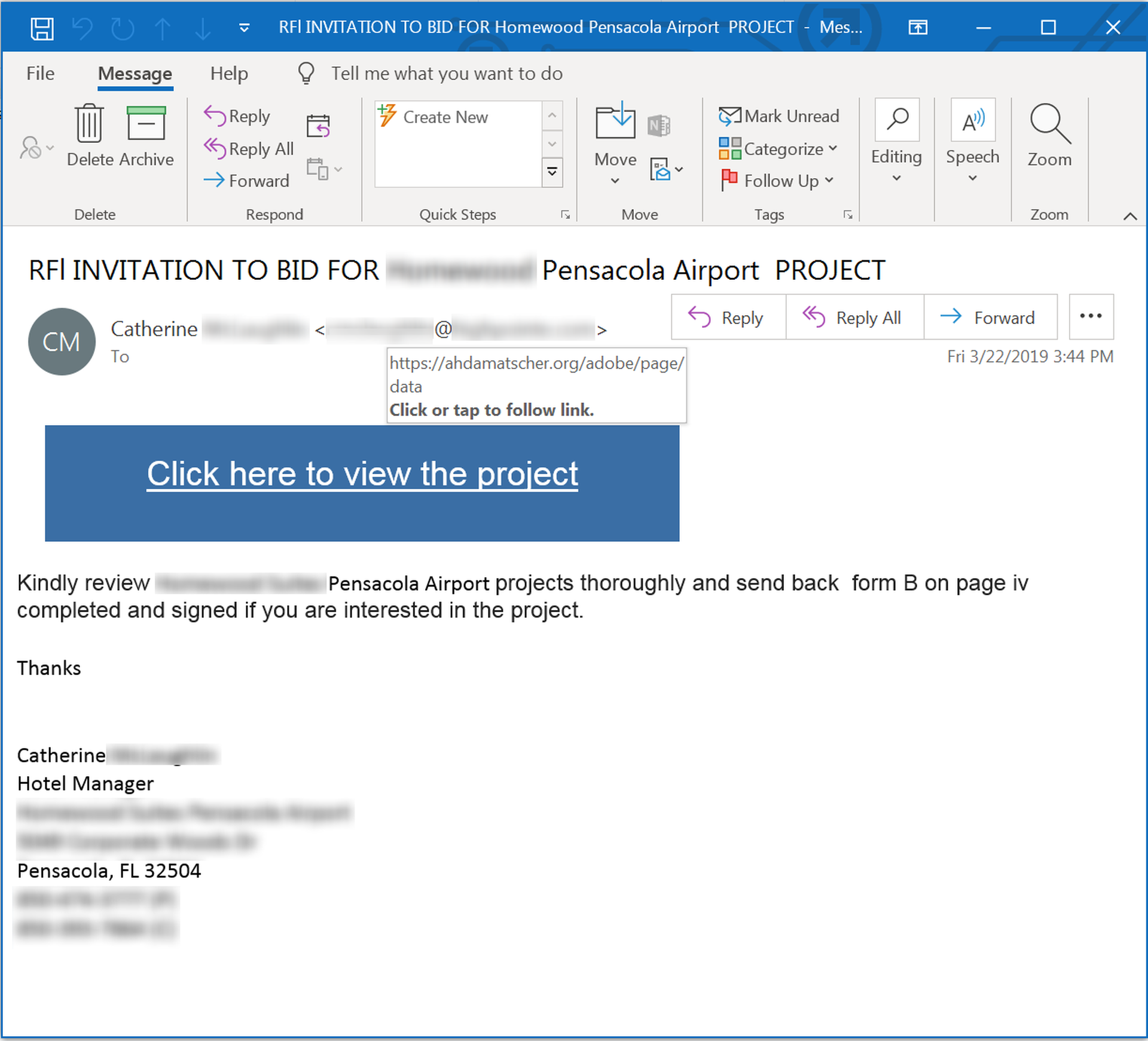
This phish is noticeably more polished than that fake RFQ, though it, too, has its problems.
More so than the phish we looked at earlier, however, this fake "invitation to bid" relies heavily on the enticing promise of more information lurking behind that malicious link -- even going so far as to provide specific directions for completing and submitting the bid form.
Alas, it is all a mirage. Here are the same instructions -- this time for an "improvements project" being run by a health care organization:

Like the first phish, though, this bogus "invitation to bid" remains short and to the point. And that is the most obvious difference between these less ambitious "fake bid" phishes that we've seen now for several years and the newer "fake bids" targeted at government contractors.
Going Large
Governments tend to be large, sprawling organizations. Apparently, the phishing emails targeting private contractors who bid for government projects have to be just as big, just as byzantine, and just as bureaucratic. Or so it would seem from the steady stream of fake "invitation to bid" phishing emails we've been tracking over the past 4-6 months.
Let's take a look.
Here is the opening move in a routine phishing email purporting to hail from the Department of Transportation. (We've also seen similar emails spoofing the Department of Commerce.)
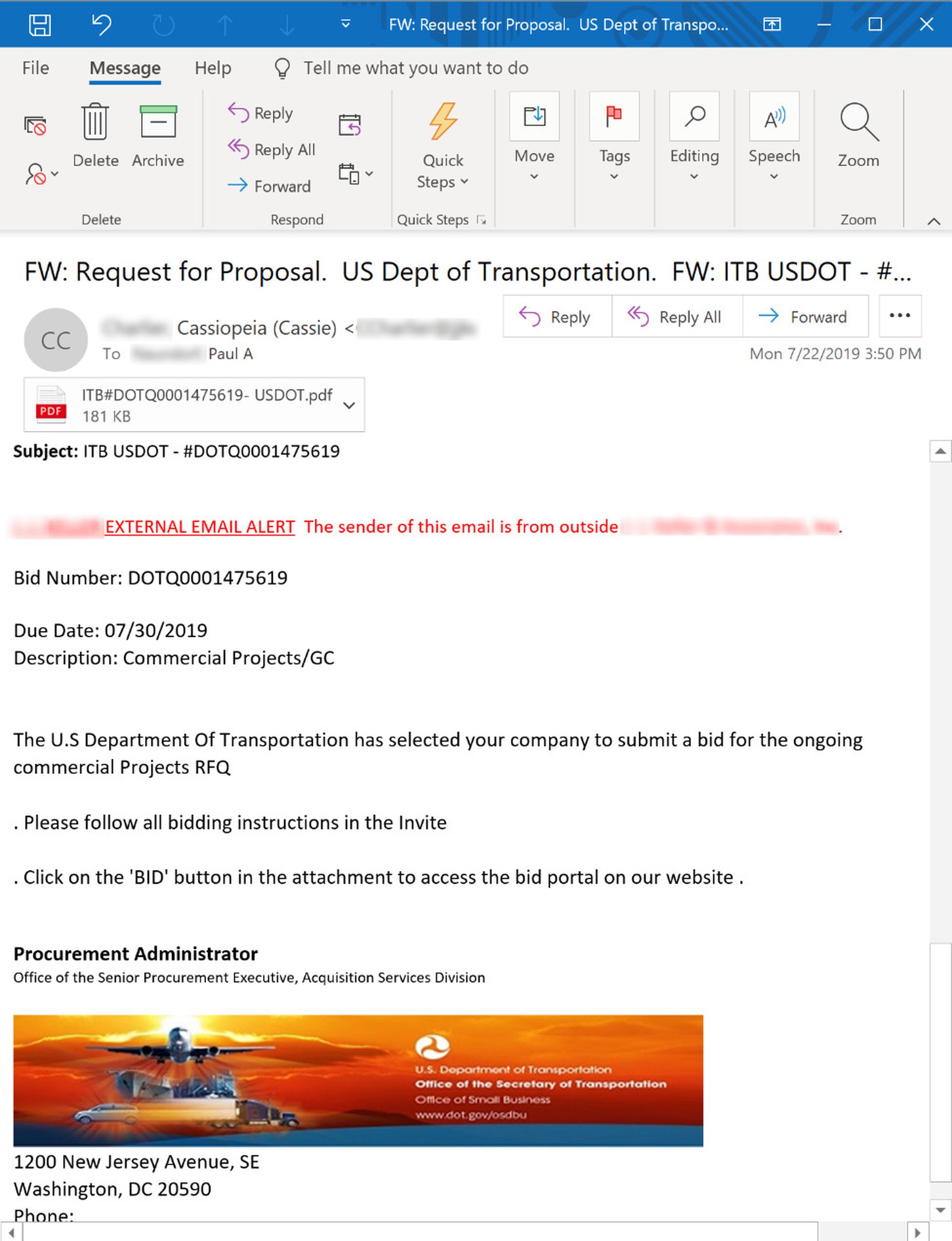
The level of detail and the disciplined construction of the email body is a noticeable improvement on the previous "fake bid" email we looked at just above. For all we know, this email might be based on an actual DOT email that the bad guys managed to get their hands on. Whatever the case, this well-built phishing email is only the first step in long slog to our final destination.
The email urges recipients to click the "BID" button in the attached PDF to access the bid portal on the DOT's website. Here is the first page of what turns out to be an unusually long, four-page PDF:
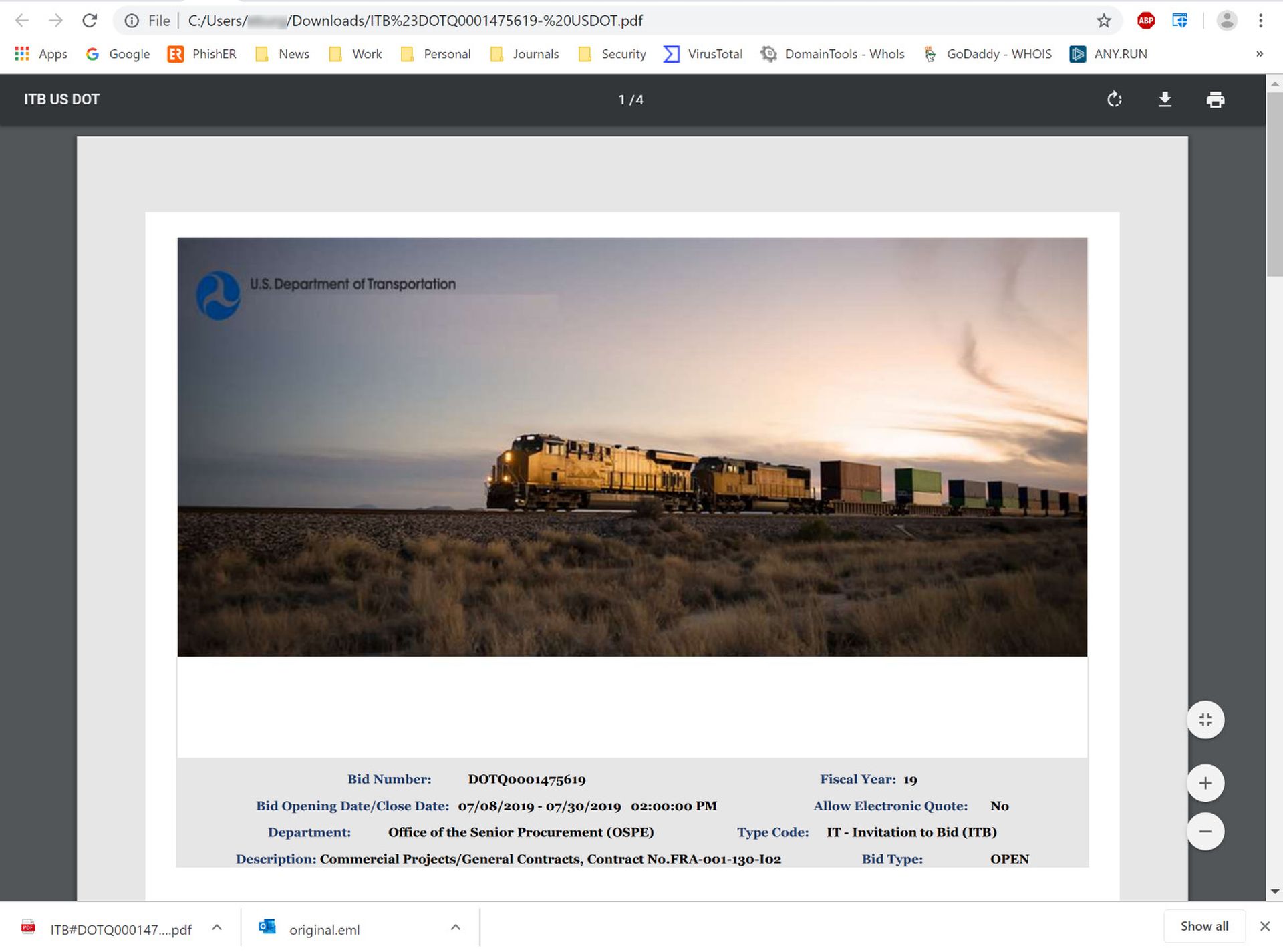
Notice that there is no BID button. This first page is devoted entirely to selling the ruse with still more carefully constructed, convincing detail. Users will actually have to scroll down to the second page to find the BID button amidst a host of other detail.
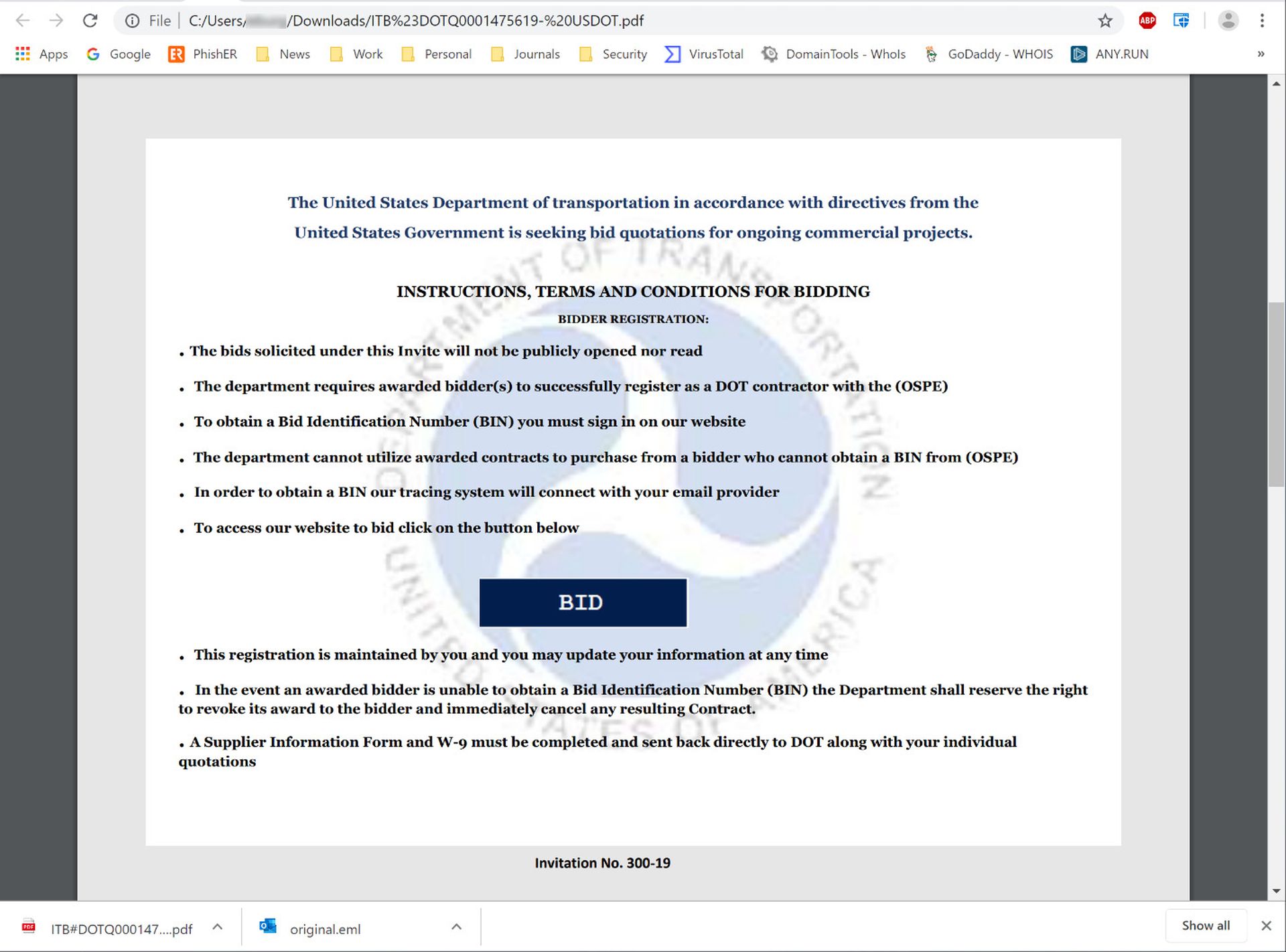
To say this kind of arrangement in a phishing email is unusual would be an understatement. In fact, it's almost unheard of. In 99.9% of other phishing emails we've encountered, the bad guys aim to get the money link in front of users as quickly as possible. Often that link is in the email body itself. When the bad guys do elect to relegate it to an attachment (typically to reduce the chances that it is flagged by scanners), that attachment is almost always a single page with the malicious link itself placed front and center before the victim. Even in the rare two-page malicious attachments that we occasionally encounter, the link is still on the first page.
There is a reason the bad guys are eager to get their money links before users as quickly as possible. The more clicks you put between users and their final destination -- whether it be an adware installation laden with EULAs, privacy policies, disclaimers and optional crapware installs or a malicious phishing email such as we have here -- the fewer the number of users who will actually make it through to the end. Simply put, superfluous clicks bleed impatient users.
If nothing else, the execution of this phish speaks not only to discipline of the malicious actors running the campaign, but to their own confidence that they have understood their "audience" (for lack of a better term) well enough to take this kind of risk. After all, what's a few extra clicks when a big government contract is in the offering?
But wait! We're not even close to being finished here. That BID button in the attached PDF takes users to a professionally designed spoof of the DOT's own website, which greets them with still another set of instructions that must be closed to continue.

Once that instructions box is closed, the magical BID button finally comes into view.
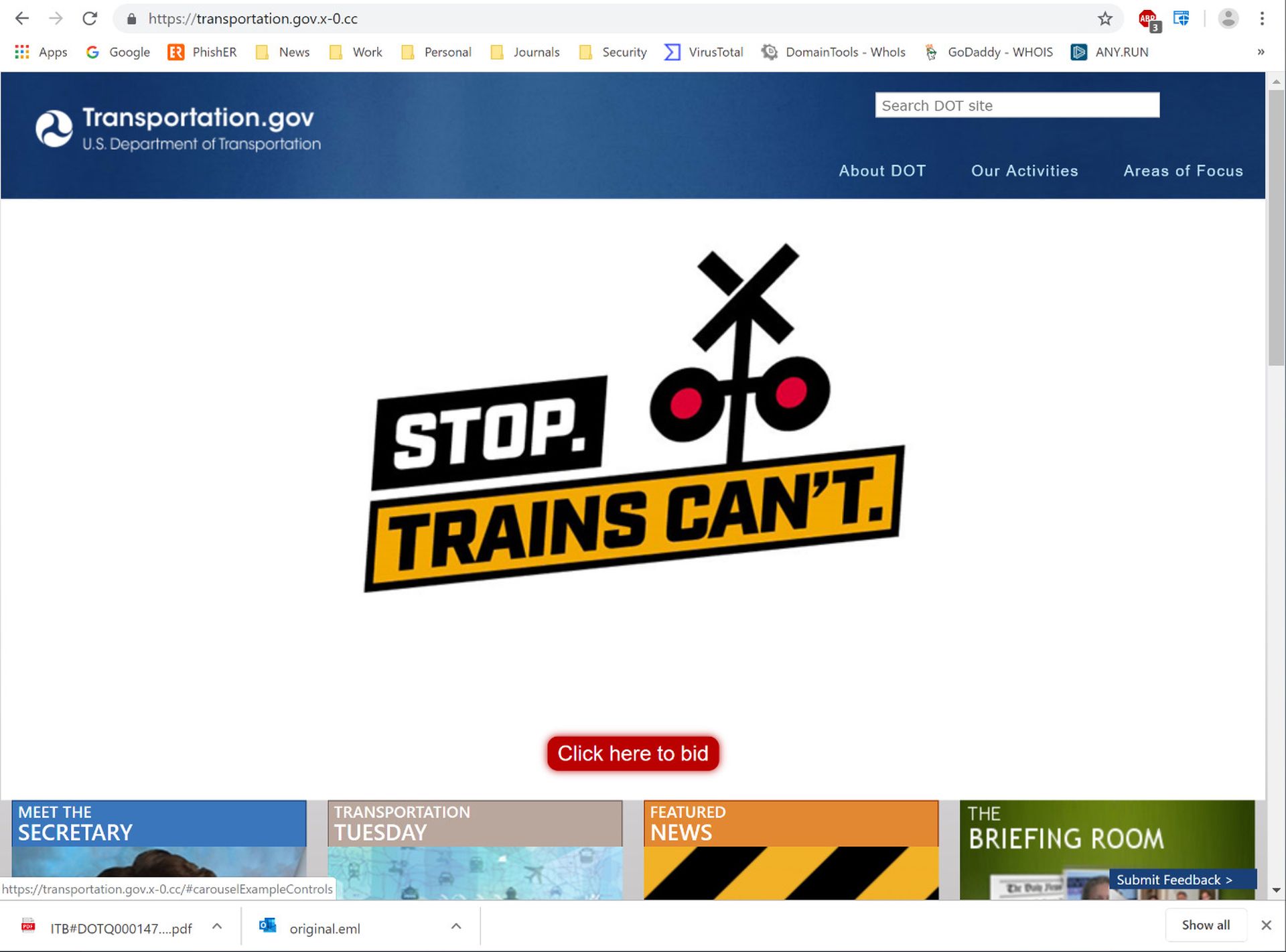
The BID button itself ends up opening a login box that -- at least for anyone with a functioning brain -- ought to be a red flag.
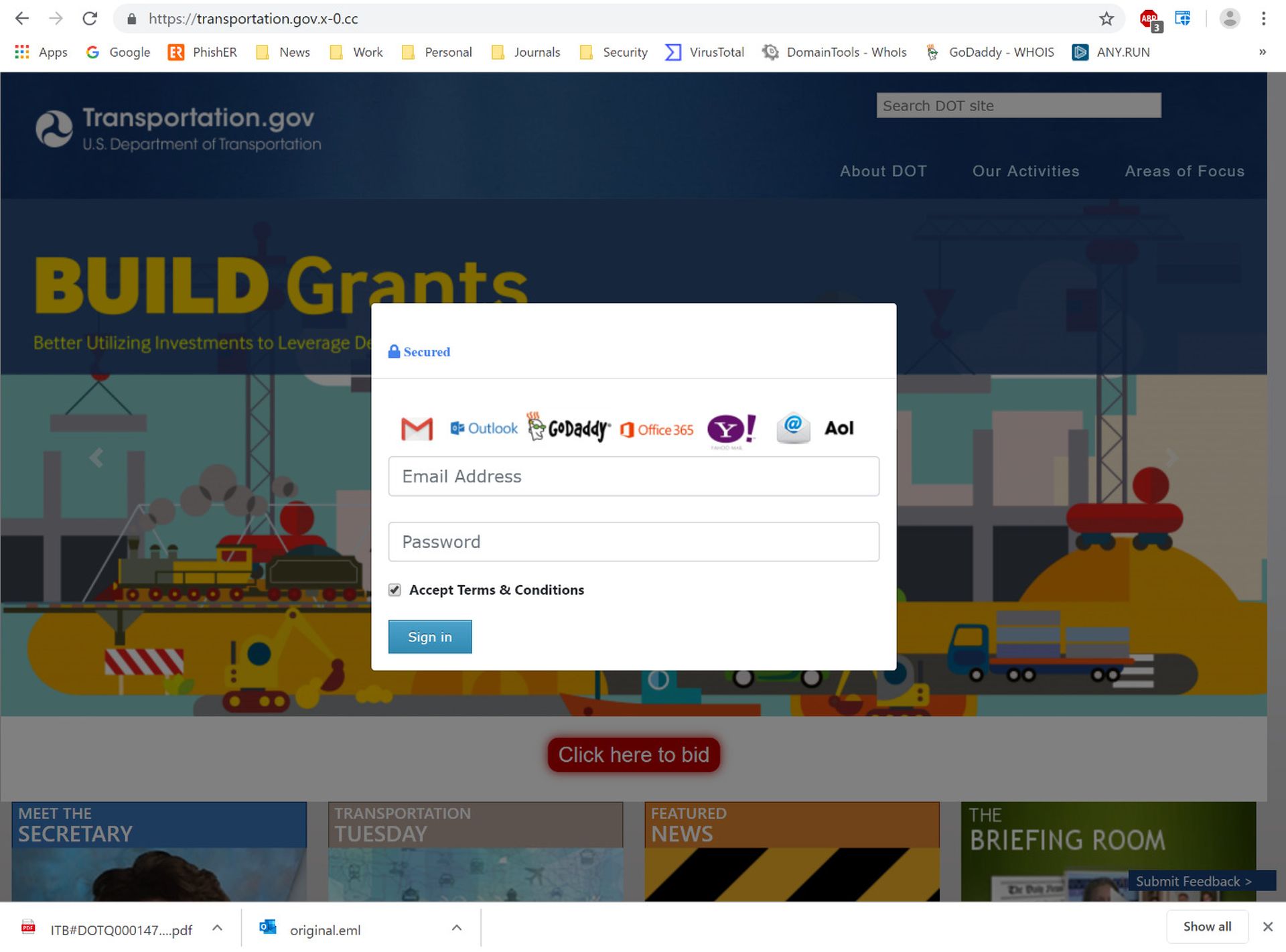
No, the DOT is likely not accepting AOL logins. And they would be utter fools to accept punters from Yahoo!.
Whatever else can be said of this phish, it must win some kind of award for "most elaborate credentials phish" -- like, ever. (We certainly haven't seen anything that comes close.)
Variations on Variations
Over the course of the past few months, we have seen several variations on this phish. For example, this fake "invitation to bid"...
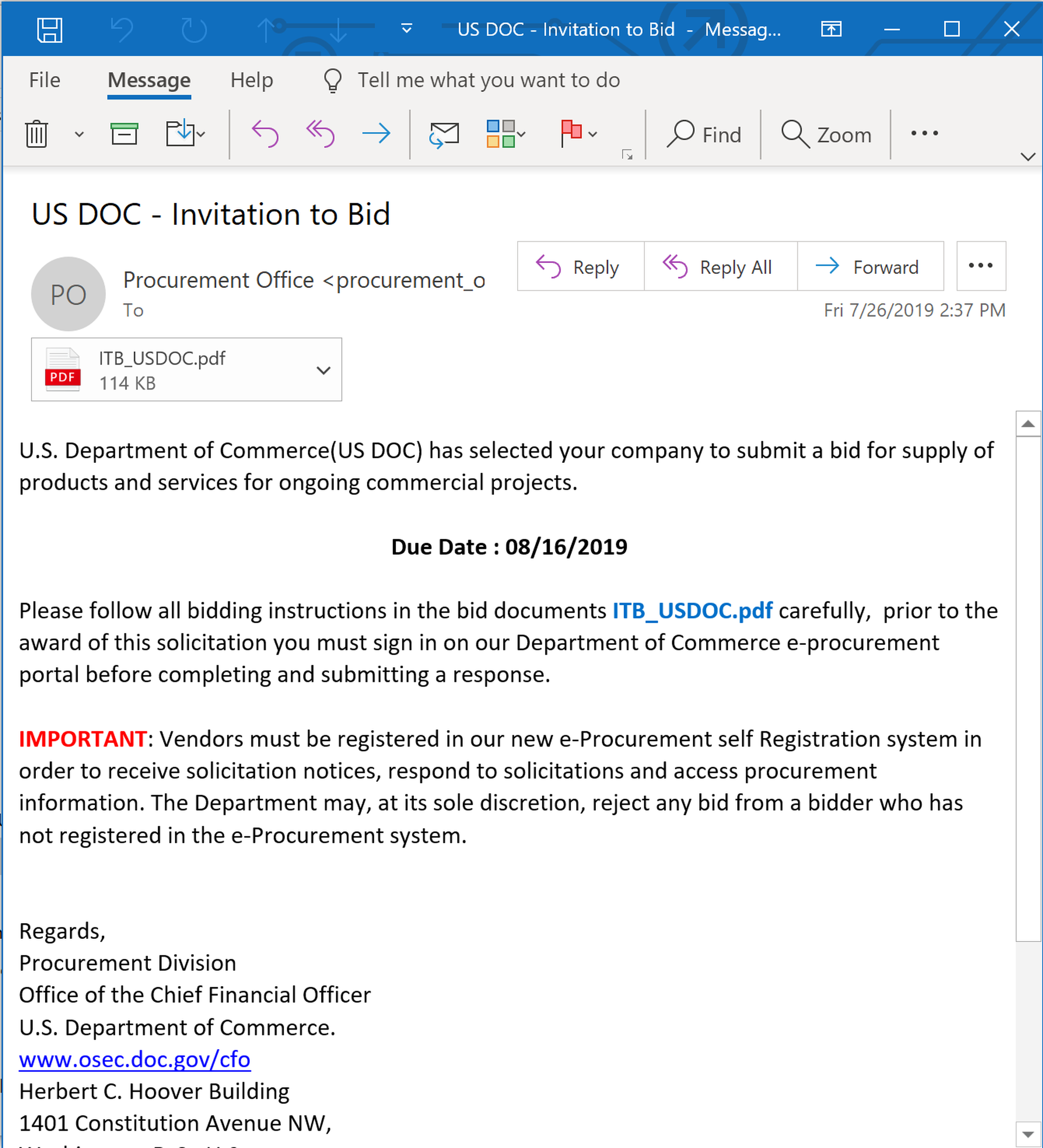
...takes users through a PDF (with the BID link on the first page)...
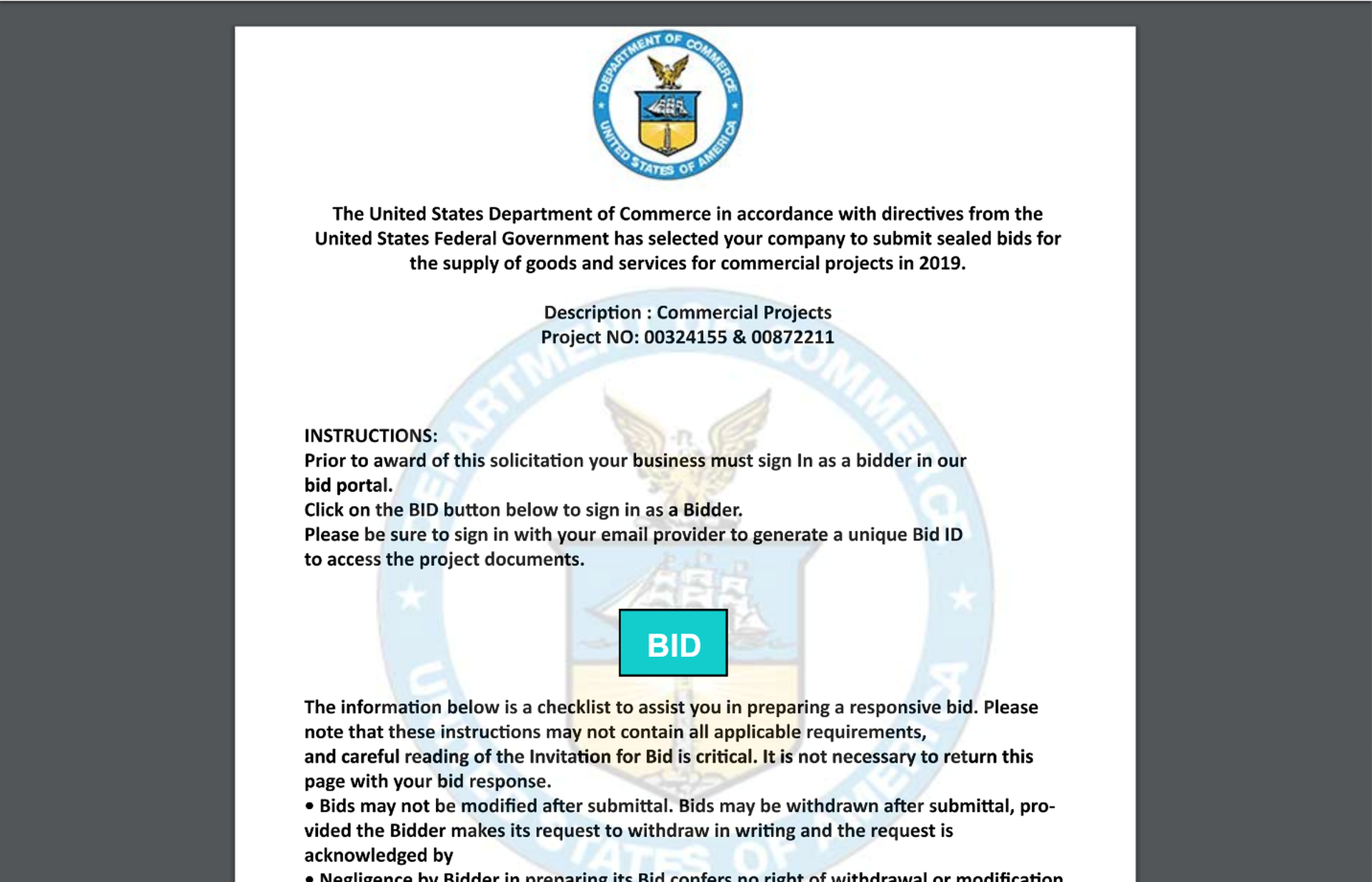
...and on to an equally well-designed spoof of the website for the Department of Commerce:
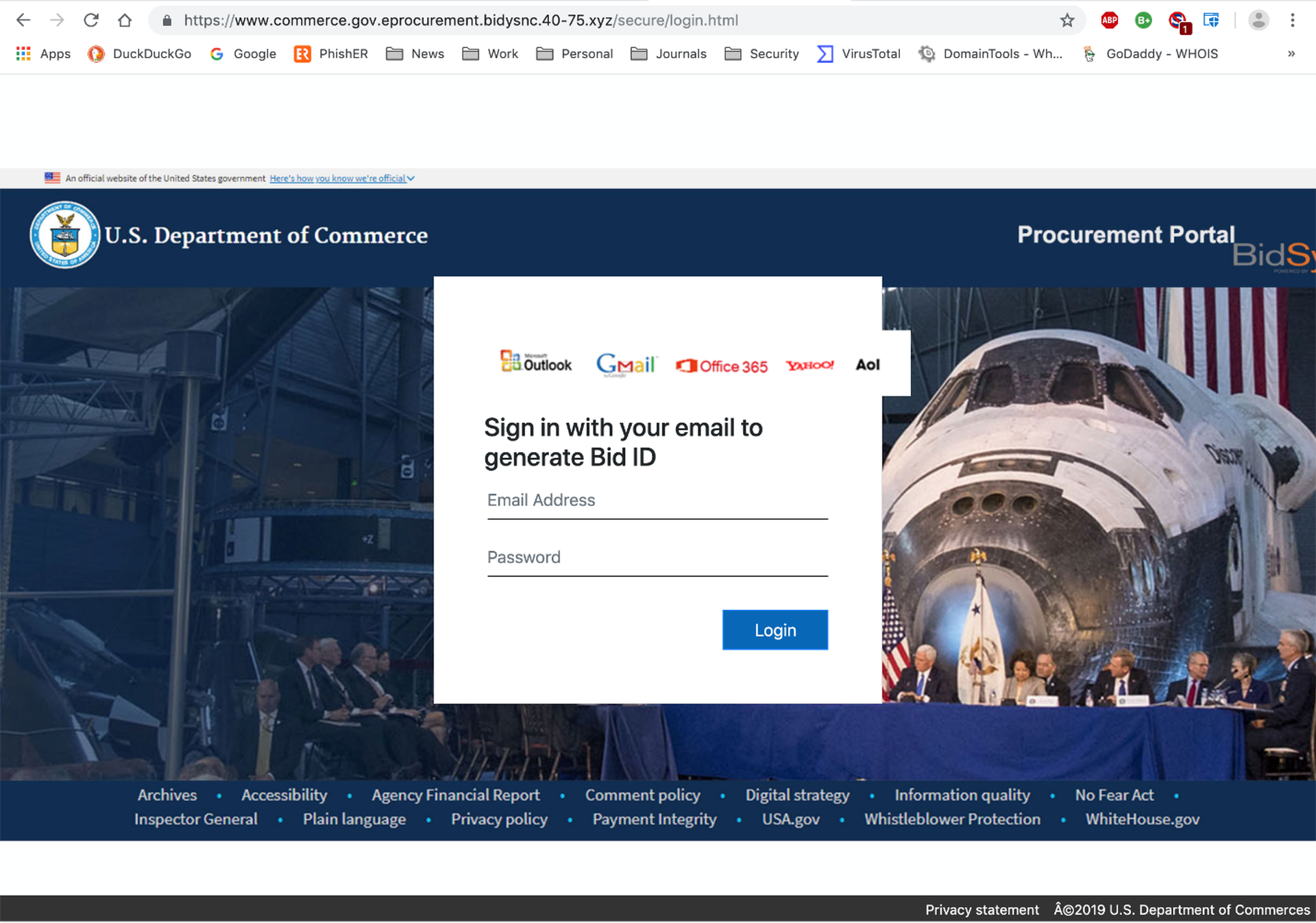
Apparently, the bad guys thought better of continuing to accept GoDaddy logins for some reason. (AOL and Yahoo! users are still good to go, though.)
Interestingly, some of the latest variants of this phish have ditched the PDF attachment altogether -- combining elements of the old email body and PDF into a single, jumbo-sized email that puts the BID button before potential marks much more quickly.

As we have stressed in earlier blog posts, the bad guys are always learning and adapting. The fact that this campaign is still going after six months, though, tells us that the malicious actors behind it must be enjoying some level of success with it. And we've certainly seen evidence that the bad guys were right to think they could get traction with this kind of elaborately designed credentials phish.
The DOT phish we laid out above, for example, generated considerable interest -- even excitement -- amongst employees at the targeted organization. The initial recipient in that organization wasted no time in pursuing it...
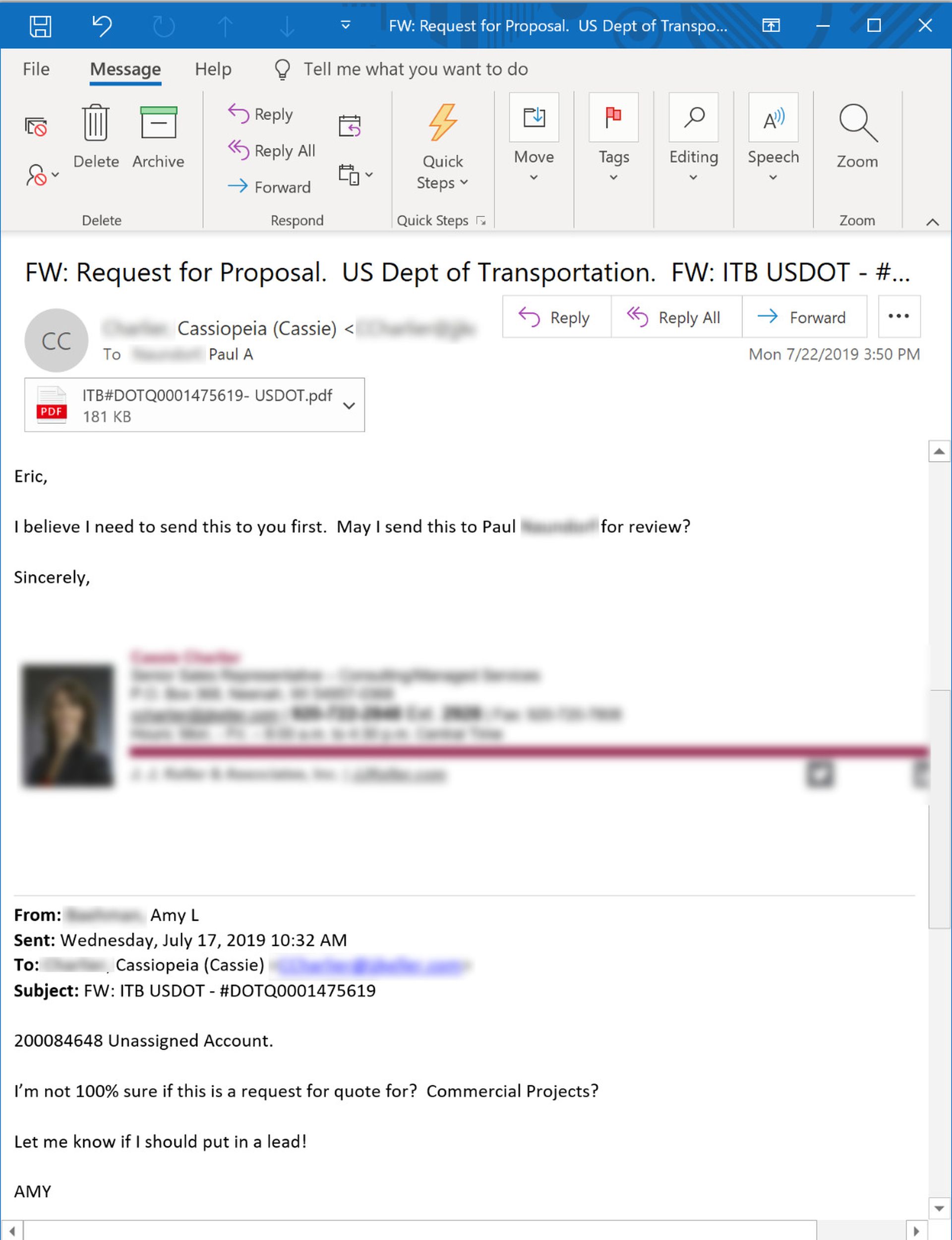
...and, in so doing, spreading that malicious email to others in the organization:

Malicious actors certainly don't lack for incentives to pursue this kind of phishing campaign, as government contractors could very well be sitting on plenty of attractive data, ranging from extensive contacts with well-heeled clients and customers to logins and other special access to government agencies. And then, of course, there is the money. For, in the end, it's always about the money.
Put simply, a well-executed credentials phish against a government contractor could yield a bonanza for malicious actors working this kind of campaign. And the elaborate detail and disciplined construction of the campaign certainly reflects that.
Conclusion
Even if you're not in the government contracting business, this kind of phishing campaign ought to make you sit up in your chair. If nothing else, it clearly demonstrates the lengths to which malicious actors will go to wangle something as simple -- and potentially destructive -- as a set of login credentials from your users and employees. The bad guys are just that determined, just that disciplined.
It should also serve as a warning that the days of counseling users to spot phishing emails by looking for grammar, spelling, and syntax errors are long gone. Your users won't help you keep the bad guys out by becoming grammar nazis. And that training session you did last year in the break room with a box of doughnuts and a PowerPoint deck will forever be a distant, foggy memory.
What your employees need is New-school Security Awareness Training, which teaches them what to look for and regularly tests their mettle against simulated phishing emails based on the latest phishing campaigns actually out there "in the wild." And the "wild" we speak of is not something scary "out there," lurking just beyond the tall trees of your firewall. It's in your users' inboxes right now, today, and each and every day.



