This is part one in a five part series written by Dr. Edward Amoroso, of TAG Cyber and Gen. Keith Alexander, of IronNet Cybersecurity
Cybersecurity risk is now a mainstream consideration for any organization with valued assets. This is particularly true for any team with responsibility to provide essential services, including ones that might have safety or life-critical implications if not properly protected. Power companies, financial services firms, telecommunications companies, military organizations, and government agencies all come to mind as dealing with this type of growing risk – and all operate large-scale infrastructure.

What are the cybersecurity challenges of large versus small-scale infrastructure?
Early computer security methods in the 1980’s and 1990’s were designed to address small-scale risks to systems with modest size, scope, connectivity, and scale. Early Windows PCs, for example, were typically protected with anti-virus software, packet filtering rules, non-complex passwords, and basic malware scanners. While these methods might seem less impressive today, the threat was simpler in the early days, and most users felt reasonably safe.
As technology expanded, however, and large-scale infrastructure emerged that was dependent on computing for operation and control, the security risks grew accordingly. Unfortunately, many of the protections applied to large-scale cybersecurity were derived from early Windows PC security approaches. It is not uncommon today, for example, to find critical infrastructure security centered primarily on the use of the basic PC security capabilities mentioned above.
Familiar small-scale controls do, of course, play a role in protecting large-scale infrastructure. Passwords and firewalls, for example, are required to mitigate certain threats, regardless of the size of the assets being targeted. At the same time, however, the unique needs of large-scale systems demand security controls that match their broad characteristics. Any control that requires manual handling, for example, might be fine for a small system, but impossible to manage across a massively-scaled system.
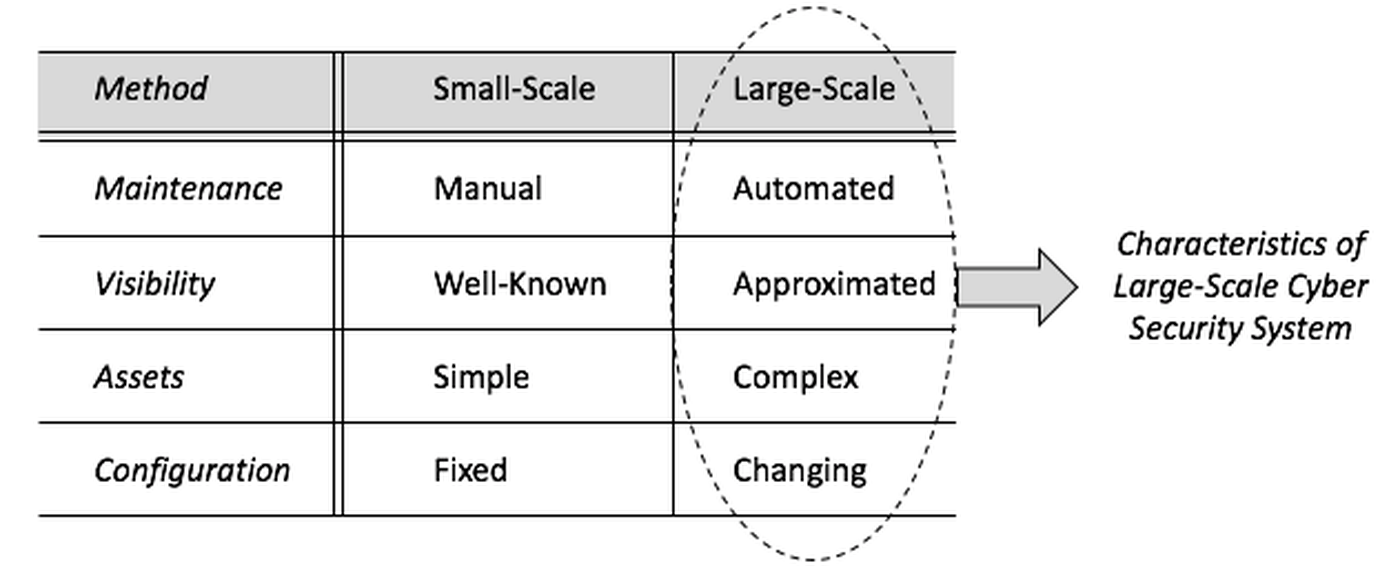
Differences between large- and small-scale security can be seen in common system management tasks. Maintenance, for instance, is manual for modest systems, but automated at scale. Gaining visibility in small-scale environments is simple, and assets are fairly well-known. Visibility is more complex for larger systems, and asset inventories are approximated at best. Finally, configuration tasks for small systems tend to be fixed, whereas larger environments must deal with ever-changing system attributes.
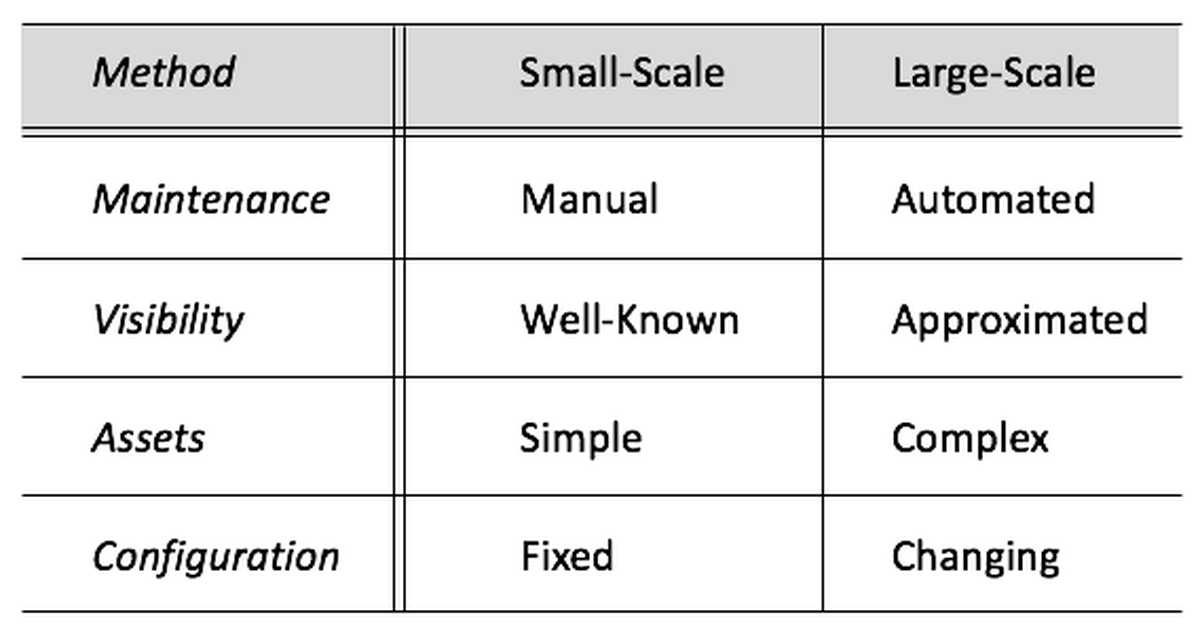
Figure 1-1. Managing Small-Scale Versus Large-Scale Systems
With these differences in mind, the owners of modern infrastructure must accept that new methods of cybersecurity protection are required. Furthermore, everyone knows that the simple hacker threat to early PCs has been replaced by threats from determined, capable adversaries, funded and backed by criminal groups or nation-states. To address this growing risk, consideration must be given to the protections necessary to defend against cyberthreats from highly-capable, well-resourced malicious actors.
What type of protections are required for large-scale infrastructure?
To protect large-scale systems, engineers need controls that are consistent with the management considerations one finds in complex infrastructure. This implies that security controls for maintenance must: (1) be fully automated; (2) address the challenges of developing visibility over complicated networks; (3) be designed to protect high-value assets with serious consequence if breached; and (4) deal with the constantly changing configuration of large-scale systems.
Careful planning must therefore go into the design of cybersecurity protection architectures for any large-scale infrastructure. Most modern Chief Information Security Officers (CISOs) in business and government recognize this challenge and allocate considerable time and effort to designing and implementing a good security architecture. With the rising cyberthreat from highly capable adversaries, however, individual CISO-led teams – even if they focus their efforts – will not be able to go it alone. They will often need external assistance.
Careful planning must therefore go into the design of cybersecurity protection architectures for any large-scale infrastructure.
Some of this external assistance has always been obvious: Businesses do not develop their own security tools, but rather buy from vendors. This is true in government, as well. Similarly, information sharing groups has long offered means for cooperative discussions between experts from different sectors, both public and private (the FS-ISAC, for instance, is an example). So, it is reasonable to suggest that government and industry must work together to address cyberthreats. The big question is how this objective can be best achieved.
Can different organizations agree to cooperate on cybersecurity objectives?
Businesses and agencies will only cooperate on joint cybersecurity initiatives if they see significant benefits for themselves, with minimal associated operational, financial, or cyber risk. Admittedly, this is how almost all business decisions are made, but large-scale cybersecurity might be slightly different, because the benefits could be less local, and more holistic. For instance, security controls for DNS are not managed by any individual organization, but are rather maintained collectively.
Businesses might thus be asked to recognize the larger benefits of keeping other organizations, perhaps even competitors in the same industry or cyber ecosystem, safe from cyberthreats. This might be achieved through the sharing of attack indicators, observed adversary tactics, discovered weaknesses in vendor solutions, and on and on. Presumably, the mutual security benefits of working with a competitor would prompt agreements to share openly.
To that end, cooperation between businesses, agencies, and other groups must address two ends of the spectrum: upside benefits and downside risks. In both instances, the case can be made that for large-scale infrastructure, both the benefits and the risks can cascade, and perhaps accelerate, as lateral traversal of an attack occurs. That is, threats to someone else’s system, however remote, might find their way to you. It is therefore worth cooperating to prevent such cascading threats, as well as to take advantage of shared situational awareness and collective defense.
The primary upside protection benefits of mutual coordination and cooperation across business and government entities for large-scale cyberdefenseinclude the following:
- Early Warning – An organization can develop a more effective early warning capability if other organizations and external groups share threat behaviors and indicators in real-time. Not engaging in such sharing could limit the ability of an enterprise to sense that an attack might be cascading toward them.
- Broader Visibility – By working together with other organizations and external groups, the local security team benefits from broader visibility, including an improved understanding of how local enterprise changes might cascade to other portions of the Internet.
- Strength in Numbers – The simple fact that cooperation introduces more eyes on a given cyberthreat means that organizations that cooperate with other organization and external groups with similar capabilities can leverage strength-in-numbers and thereby better achieve local security goals.
- Collective Defense – Cooperating to share threats at scale means that each entity in the system is better defended from threats, even as they continue to spread and morph. The overall system is thus significantly more resilient to cyberattacks.
The corresponding downside risks that must be managed in the development of any large-scale cooperative arrangement for cybersecurity include the following:
- Privacy of Shared Data – Sharing information with members of a broad cooperative might result in leaked data, and could expose a business to regulatory risk (although this is mitigated, in part, by provisions of the Cybersecurity Information Security Act of 2014 (CISA)). Data must therefore be properly anonymized and must ensure that participants are not exposed to sharing risks.
- Attribution of Incidents – Similarly, the potential for any sort of public attribution of an embarrassing or problematic security incident to a specific entity may reduce, or even remove, the willingness of that organization to share further information.
- Competitive Relationship – The normal hesitation for one company to directly assist a competitor cannot be ignored. CISA has addressed the legal barriers in this arena, and the hope and expectation is therefore that broader groups of organizations—particularly in the critical infrastructure and core economic sectors—will adopt mutual focus on safety to assist other sector participants notwithstanding potential competitive pressures.
The benefits and risks of a cooperative to secure large-scale systems across business and government organizations must therefore be assessed to determine the best approach. Too often, cooperative security organizations leave participants wondering whether the relevant risks and benefits have been fully considered. It is a central thesis of this report that cooperative security arrangements will fail in the absence of suitable attention, up front, to these sensible pro-and-con management concerns.
How can government coordinate with industry for improved cybersecurity?
The optimal role of government in large-scale protection is often unclear. First, most large businesses are multi-national. So, while national allegiance is easily identified (e.g., Verizon is an American company, and Huawei is a Chinese company), such allegiance will rarely supersede the interests of shareholders. This emphasis is often misunderstood by government agencies focused on national interests. The intensity of this issue will vary across different countries.
Government also complicate their relationships with industry through regulation, and the associated penalties for businesses not meeting security obligations. If, for example, incident reporting is mandated by governments, this can limit voluntary information sharing about incidents that might be marginally reportable. There is a reasonable argument that if governments wish to incentivize voluntary sharing, they might consider prohibiting regulatory action based on shared information.
A third challenge for governments in large-scale cybersecurity is that most critical infrastructure, especially the United States, is owned by the private sector. This implies that most threat telemetry, behaviors, indicators, and early warning information will not originate with government. This fact is often not fully understood by citizens and politicians who demand that government step in and fix large-scale cybersecurity threats. Government rarely has the information, authority, or resources to do so.
In the end, a partnership is required between government and industry for large-scale cybersecurity. Governments must share information they control, such as classified data that can be downgraded or shared securely to defend critical infrastructure. Similarly, businesses must recognize that their obligations to society often extend beyond just the shareholder, and that it is in their interests to cooperate freely and openly on large-scale cybersecurity issues both within their nation as well as potentially across international borders with key allied nations and industry partners.
Part 2 will appear on July 31



