Cyberthreats to infrastructure
Any cooperative effort that supports large-scale infrastructure protection must begin with an accurate perception of the real cyber risks that must be addressed. Experts understand that risk is measured by combining the probability of bad outcomes with the consequences of such outcomes. In the context of infrastructure protection, risks are driven by malicious threats and consequences of compromise to valued assets. To understand cyber risk, one must be able to effectively measure and evaluate these key components.

What are the cyberthreats to large-scale infrastructure?
The CIA model of confidentiality, integrity, and availability offers a well-known, textbook view of cyberthreats to large-scale infrastructures. As such, it can be used to create a hierarchical representation of threats to large-scale systems. These levels of the hierarchy can model general or domain-specific issues to highlight scenarios that target infrastructure assets. The depth and details of the hierarchy used should always be selected in a manner designed to help security engineers understand threats.
An example of a hierarchical breakdown of cyberthreats might be illustrated for a typical bank. The first level of decomposition might be defined for each business line of the bank. In this case, we can assume these to be personal banking, business banking, loans, and customer investments. The resulting hierarchical threat decomposition for the example bank, starting with CIA, and extending to the component businesses, is shown in the diagram in Figure 3 below:
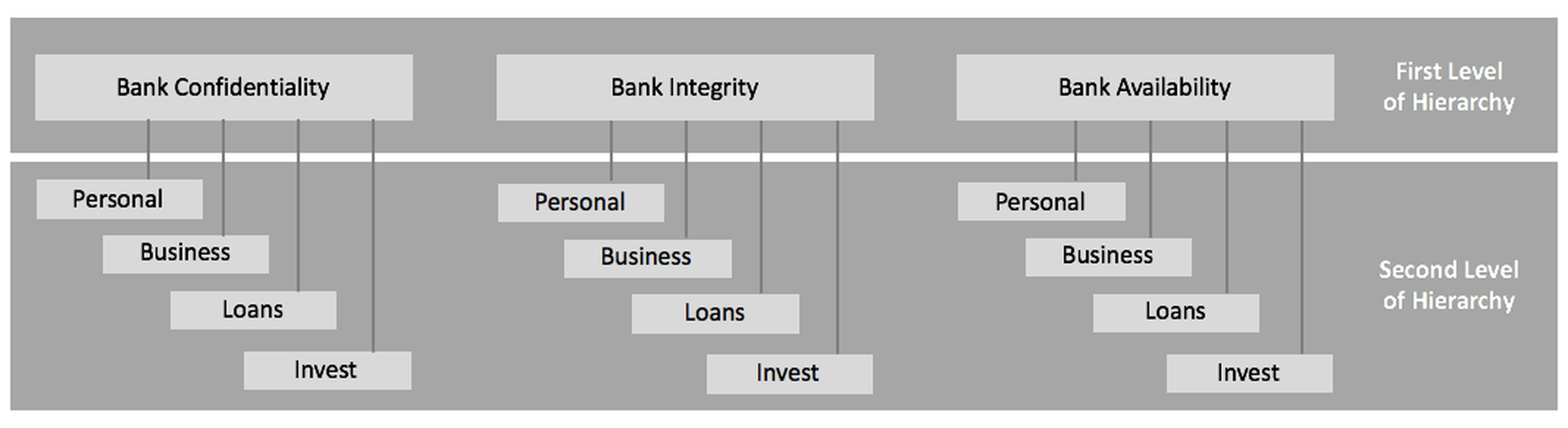
Figure 2-1. Two Levels of Hierarchical Threat Decomposition for a Typical Bank
The advantage of hierarchical threat decomposition for large-scale infrastructure is two-fold: First, the approach maintains completeness of the composite threat profile through each stepwise breakdown – so long as the decomposition is done properly. Second, the hierarchy offers the ability to provide detailed guidance on the specific threat scenarios that are applicable to the system of interest. Each scenario is developed by starting at the top level and working down to a leaf node.
Security analysts can use threat hierarchies to examine what-if scenarios to investigate the effectiveness of controls. This supports a structured analysis of security issues, which can result in improved identification of proper mitigation strategies – including, of course, involvement in a sharing collective. Sample two-level threat scenarios that can be hierarchically decomposed as part of our bank example include the following:
- Confidentiality – Loans: This scenario might involve loan-related information being disclosed to an unauthorized individual. Such a disclosure could have serious implications for personal privacy and may result in economic harm or public consequences in a variety of circumstances.
- Integrity – Business Banking: This scenario could involve business information being modified by an unauthorized entity. Such action not only undermines customer confidence in the business, but could also degrade the community’s confidence in the bank as well.
- Confidentiality – Customer Investments: This scenario could involve unauthorized disclosures of the details of particular investments, perhaps in a high net-worth wealth management unit. Such a disclosure could introduce significant litigation risk if material harm is done to the client, and could be damaging for the bank’s reputation, particularly if the relevant client is a prominent individual or institution.
- Availability – Personal Banking: This scenario could involves the malicious blocking of individual access to their accounts. While the immediate impact of such an activity might seem fairly minor, such unavailability could cause significant concern – and even panic – particularly if the outage is extended and widespread.
Every large-scale entity involved in the provision of essential critical services or assets must engage in a detailed threat breakdown along the lines of the example shown above – albeit with significantly more detailed levels of decomposition. In some cases, the resulting threat hierarchy might include many thousands of leaf nodes, each corresponding to a path in the tree, and each representing one specific threat scenario that must be addressed by the overall security scheme.
In some cases, it will be trivial to map scenarios from the threat tree for one organization to that of another. For example, a distributed denial of service (DDOS) attack involving on a botnet of compromised virtual servers is obviously a common risk for many different organizations. Banks, government agencies, and even military departments regularly experience DDOS attacks and can therefore easily coordinate on an integrated response using naming, routing, and other shared infrastructures to identify and limit the scope of such potential attacks.
In other cases, however, the mapping of scenarios across different organizations or sectors may be more difficult. For example, some sectors may be more reliant on particular types of industrial control systems (ICS) or supervisory control and data acquisition (SCADA) systems than others. In those cases, coordination within a given sector or grouping of companies may be easier to effectuate versus broad-scale cross-sector sharing.
Even in such a scenario, however, there are benefits of broader sharing of such threat behaviors, because even where different asset classes or systems are targeted, there can be useful learning to be gleaned about attacker behavior than can be applied outside the particular context of a given attack. So, even though such mapping may be more difficult and the benefits less clear at the outset, there are still good reasons to share such information broadly at scale in real-time.
What are the consequences of cyberattacks on large-scale infrastructure?
The consequences of any attack on infrastructure will vary based on the circumstances of the affected set of systems and the particular sector being targeted. Customers of telecommunications providers, for example, may experience severe consequences from even temporary service outages. Consumers of other producers, such as consumer apparel or particular luxury goods, might not view temporary unavailability of access to such goods as being as serious. Of course, it is worth noting that viewed from a business perspective, while the relative importance to the consumer may be lower, the impact on a business (and the relative impact on the economy) can still be significant, particularly where such an attack has an immediate impact on a particularly time-sensitive business function.
Other factors such as the timing of a particular incident can also influence the relative consequences of an attack. For example, a retail organization might view denial of service threats just before the holiday season as having significant implications. In contrast, the same retailer might be less concerned with the consequences of a similar attack at a different time, where the impact on same-store sales might be less critical. This difference in timing matters when protecting particular types of corporate infrastructure, because it influences the measurement of risk.
The various factors for evaluating risk can be further broken down into so-called “hard” consequences, which can include damage to financial, business, and other tangible assets and “soft” consequences, which can include potential damage to reputation and image. Regardless of the nature of the consequence, however, all organizations will have some sort of hierarchical view of their top risks, and many will be driven primarily by a combination of the nature and scale of the potential consequences and the likelihood of an attack resulting in such consequences.
Take, for example, a pharmaceutical company that develops drugs based on years of expensive research. Theft of their medical intellectual property is often considered the top cyber risk for the company, and it is driven primarily by the nature of the consequences of such theft. That is, it might be just as likely that email or calendar information for employees might be hacked. But the consequences of such IP theft is so great that it drives that particular risk to the top of the list.
Every organization managing critical infrastructure must identify their top risks. This is typically done by first listing and estimating the magnitude and probability of the top attack scenarios based on existing vulnerabilities. The next step is to list and estimate the magnitude and probability of the most undesirable consequences the organization might experience as a result of an attack. Risk ranking is then done by creating a cross-product of the two lists and then turning that output into something meaningful.
An example might be a pharmaceutical company that first identifies its top three vulnerabilities from plant operations, drug research, product management, and other business units. It then creates a list of the top-three most undesirable consequences. Finally, it takes the cross product of the two lists, turning the final output into an estimate of top risk scenarios based on the company’s particular mission. Here is what such an exercise might look like for a typical pharmaceutical company.
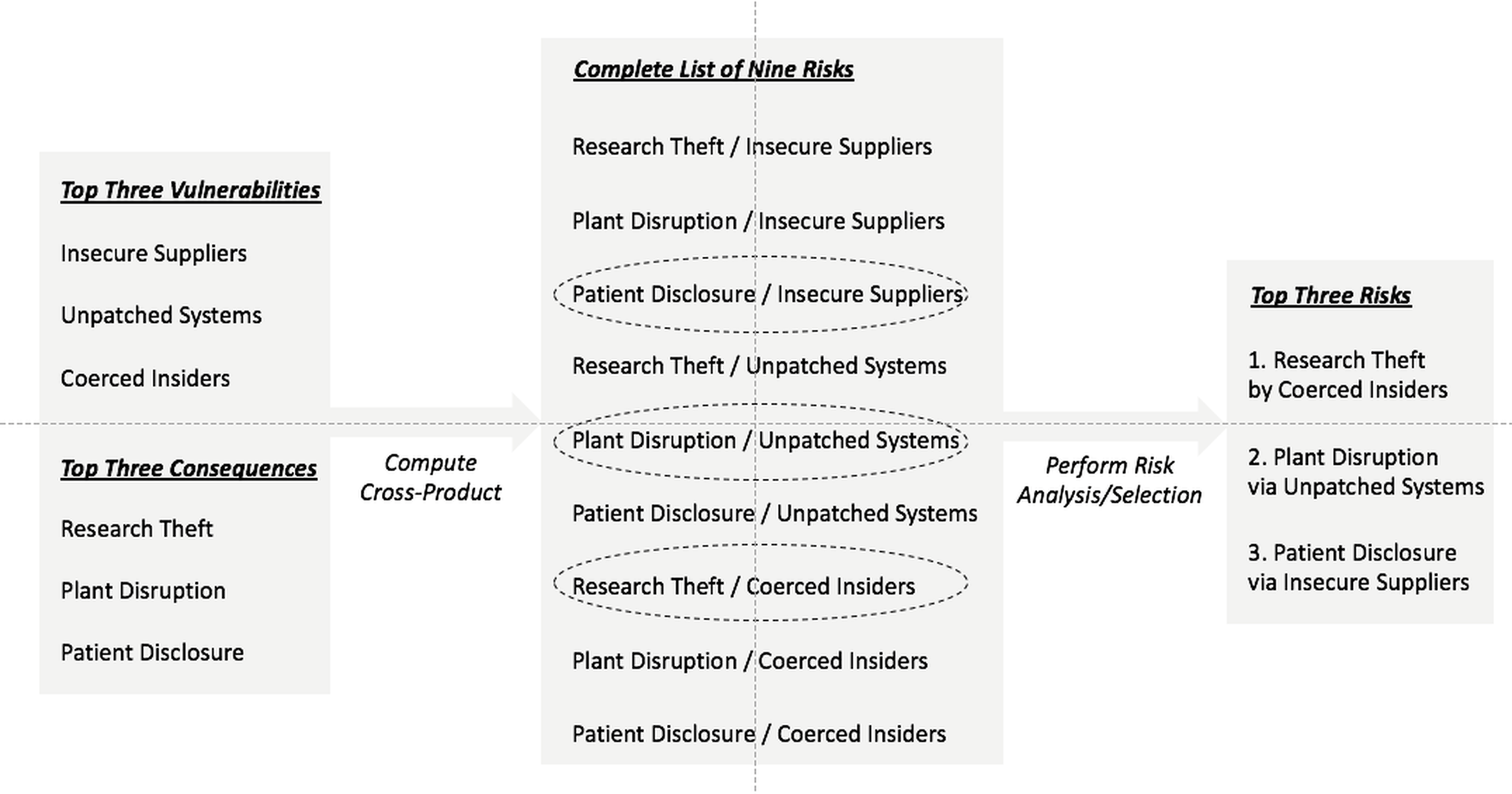
Figure 2-2. Sample Risk Analysis from Vulnerability and Consequence Information
A similar evaluation for an infrastructure provider might involve a significantly larger, more complex list. Regardless of the complexity, however, this task be completed to guide internal allocation of security resources, and to help evaluate risk in the context of a collective security arrangement. That is, even beyond assisting with internal security, having an understanding of local risk is essential to optimizing the assistance being sought from peers in a cooperative security ecosystem.
What type of bad actors must infrastructure owners focus on stopping?
Many generic taxonomies exist regarding the specific types of bad actors that an organization must contend with. Such textbook descriptions of malicious entities, and their respective motivations for their actions, usually include at least the following five groupings, which are not intended to be an exhaustive catalog:
- Hackers and Vandals – This is the least malicious group to contend with, generally because their motivation is often driven either by technical curiosity or by concern for their reputational standing within a social group. Hackers and vandals rarely (if ever) try to damage society or physically harm other people, so they tend to be more easily reasoned with when caught.
- Purpose-Driven Groups – This is a more intense offensive group than hackers, because their motivation is generally driven by philosophical, political, or religious beliefs. Such beliefs tend to result in more determined campaigns than one finds with individual hackers. The famous group Anonymous, for example, falls into this category of purpose-driven malicious actors.
- Business Competitors – Although one would like to think that competitors will play fair, the reality is that in many sectors, competing organizations will aggressively seek to gain a business advantage. At times, this may result in seeking to obtain competition-sensitive information, from intellectual property data to pricing and corporate transactional information.
- Criminal Organizations – This group is can also be particularly intense, and is almost always driven by financial motivations. Computer fraud has become a popular means for stealing money, often involving social engineering front-ends with robust workflow processes to execute credit card, identity, medical, insurance, and other common forms of cyber theft.
- Nation-State Military – As one might expect, nation-state sponsored campaigns are the most difficult to defend against, and may represent an intractable problem for business. If a nation-state such as China or Russia targets a business via cyber means, then that business is almost certain to fall victim to some extent, given the access of nation-states to relatively unlimited financial and human capital. That being said, companies still have an inherent duty to mitigate the risks that serious nation-state threat actors pose to them and their customers.
In applying this textbook categorization of threat actors, organizations must use their own risk analysis to determine the key actors of interest and the particular nature and scale of the threat to their organization and industry. For example, a company that manages sports talent may be unlikely to be targeted by a nation-state; however, that agency would be wise to consider the potential for attacks from competitors as well as from a broader base of threat actors—such as illicit news organizations focused on their clients’ reputation—that might not pose as significant a threat to other sectors.
What specific techniques are required to mitigate security risk in real-time?
The mitigation of cyber risk is a two-fold process. First, it requires proper attention to all the protection and compliance basics found in any textbook or introductory course on cybersecurity. Listing this well-known litany of security policies, procedures, and functions is not necessary here. Anyone reading this report is likely to be familiar with controls required in frameworks such as the CIS Top 20 Critical Security Controls Solutions, NIST SP 800-53, rev 4, or the General Data Protection Regulation (GDPR) from the European Union.
The extension from familiar security and compliance baselines to more advanced security solutions is the focus of the remainder of this report. Specifically, we explain how an effective defense of large-scale infrastructure requires use of methods that take advantage of analytics, data science, and network engineering methods to provide situational awareness aimed at fostering the optimal types of prevention, detection, and response to cyberthreats.
Part 3 to be posted on July 31.



