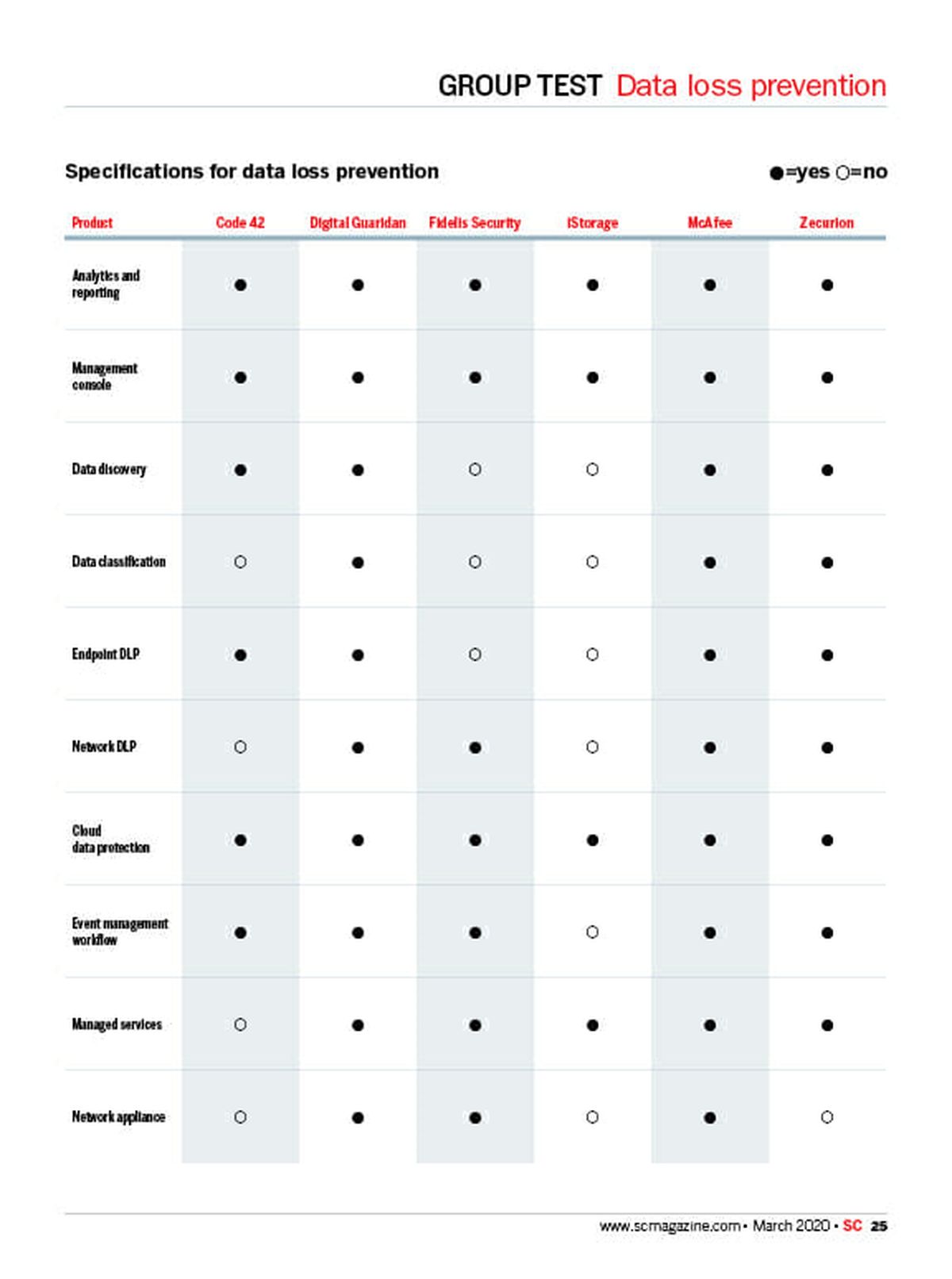
Securing data has become a labor-intensive task due to tremendous increases in volume and the far-reaching vectors it traverses. Only recently have compliance standards and frameworks cracked down on information security practices and most organizations still do not sufficiently monitor their data or control its accessibility. The aggressive changes in security protocols and tightened compliance standards affirm the importance of data loss prevention solutions, which control access and monitor behavior to prevent the improper handling or transfer of data.
Including tools like machine-learning-based behavior analysis and relationship graphs to advanced monitoring techniques, these products narrow the gap between actual and adequate data security practices. Unlike other product groups, the data loss prevention group does not necessarily appeal to a specific industry or organization. All organizations, regardless of size, need to incorporate data loss prevention into their security posture, and we are confident that at least one of these tools will suit most business needs.
Some organizations may even choose to deploy more than one option for bolstered data security. For security professionals that value their data (that should be all of you), we strongly endorse these products and recommend integrating them into your environments. All organizations should now consider data loss prevention tools to be security staples since their importance will only increase in the foreseeable future.
Data loss prevention products also come with automation capabilities that minimize the laborious nature of data security, increase response time and reduce human error.
This month, the SC Labs team looked at the data loss prevention space, where products control access and monitor behavior to ensure that end-users do not improperly transfer company information or files. The value of sensitive data has recently encouraged organizations to invest more resources in data loss prevention and these investments have, in turn, directly reduced organizational risk and compromise events.
At this point, most organizations operate predominately – even exclusively – with electronic data. Companies either duplicate their paper files electronically or convert them to electronic format and then archive them. Therefore, the amount of data security teams and administrators must protect and the vectors they must secure has grown exponentially in businesses great and small, and organizations have often not done nearly enough on the security front to adjust to this increase.
The discrepancy between adequate data security and actual data security has spawned information security compromises, some of which resulted in unmitigated technological disasters and public relations nightmares. Some of those organizations have suffered severe financial consequences and the loss of customer trust, necessitating a change in information security practices as well as new and tightened compliance standards.
The sheer number of data points makes tracking and monitoring files and corporate content extremely difficult, further complicating the practice of data loss prevention. Trying to adequately configure data protection while not hindering productivity can be a challenging task to navigate. From a security standpoint, there is an inherent drive to make a security posture as airtight and impenetrable as possible. However, doing so interferes with streamlined processes and may even inhibit employee efficiency when it comes to task completion.
This interference arises because of the stringent policies and settings that airtight security mandates. Employees may be unable to access certain files or applications without requesting access to them first.
This additional step dramatically increases the overall time required to complete tasks, which, in turn, reduces production. We saw many impressive features in this space geared toward airtight access control, anomalous behavior detection and information monitoring.
As in other areas of cybersecurity, data loss prevention products also come with automation capabilities that minimize the laborious nature of data security, increase response time and reduce human error.
From standard security features to more advanced monitoring techniques like keystroke capture and end-user behavioral analysis, these six products impressed us with their innovative developments.
Data loss prevention solutions, such as the ones featured here, are vital in the fight to protect valuable data and limit data vulnerabilities. In some cases, organizations may prefer to deploy more than one of these data loss prevention products to reach an optimal security posture.
The vendors have not customized these products for any specific industry or type of organization. Everyone needs to incorporate data loss prevention into their security practices and should consider these products a staple in any security toolset.
PICK OF THE LITTER
Digital Guardian Data Protection Platform focuses on content, context and user-based classifications to appropriately tag and fingerprint sensitive data without adding more false positive results. This highly content- and context-aware solution provides substantial visibility, control, protection and compliance support in a single package. This solution is both comprehensive and competitively priced, making it an SC Labs Best Buy.
Zecurion DLP covers our list of features and tops it off with more than ten different content detection technologies, giving it extensive monitoring capabilities. Its robustness combined with its unparalleled monitoring and access control make Zecurion our SC Labs Recommended product for this month’s round of reviews.