Threat hunting has become a critical exercise in the fight for stronger security. But as the threat landscape continues to change, hunting techniques must also adapt. In a recent report, Sophos looks at the changing landscape and offers guidance to help organizations get started with threat hunting. This includes a summary of the tools and frameworks security teams are leveraging and five steps IT professionals should follow to prepare for successful threat hunting.
The report includes the following takeaways on the current threat landscape:
Attacks have increased in volume, complexity, and impact
Over the last year, 57% of organizations experienced an increase in the volume of cyberattacks, 59% saw an increase in the complexity of attacks, and 53% said the attacks had a greater impact. Almost three out of four organizations (72%) saw an increase in at least one of these areas. A growing trend is the increase in supply chain attacks, such as the SolarWinds incident revealed in March 2021. Attackers had inserted modified instructions into the source code of their Orion solution that is used to manage complex networks remotely. This backdoor enabled the adversaries to access the networks of SolarWinds’ customers, including several government agencies.
Ransomware is a real threat to all organizations
66% of organizations were hit by ransomware in the last year, up from 37% in 2020. This is a 78% increase over the course of a year, demonstrating that adversaries have become considerably more capable of executing attacks at scale.
The growing use of legitimate tools in attacks
Adversaries increasingly exploit bootlegged or pirated copies of legitimate, off-the-shelf software and free, open-source tools. Typically, these tools are designed to simulate cyberattacks to improve security but can be exploited by criminals to do the opposite. Tools like Mimikatz (used by penetration testers and malware authors alike), while not strictly commercial offerings, were used widely - appearing in nearly every hands-on-keyboard incident Sophos investigated over the past year.
Also, notably dominant (thanks to its source code being leaked in 2020) were pirated copies of Cobalt Strike (an adversary simulation software), which were not only used in ransomware attacks but also dropped as an initial payload of other malware.
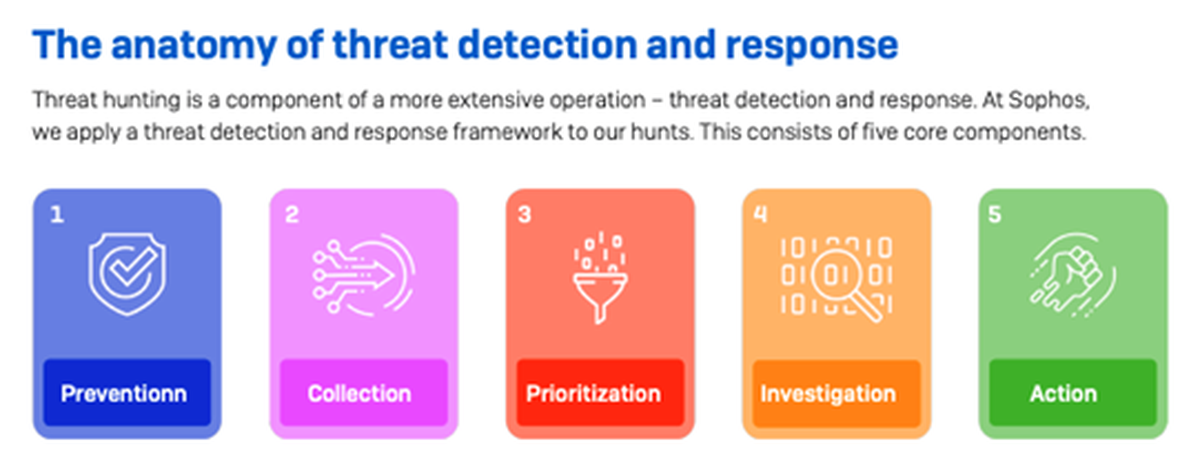
Five key steps
To prepare for and engage in threat hunting, Sophos recommends five steps to ensure success:
- Understand the maturity of your current cybersecurity operations
- Decide how you want to go about threat hunting
- Identify technology gaps
- Identify skills gaps
- Develop and implement an incident response plan
For more detail on these steps and to better understand the challenges and solutions, download the full report