Ransomware attacks continue at a blistering pace as organizations remain vulnerable to the exploits bad actors use. Many victims are paying ransom, and despite efforts to bolster defenses, many continue to struggle at detection and response. Those are among the findings in a February 2022 survey report from CyberRisk Alliance Business Intelligence (CRA BI).
A new report from Sophos shows that the scourge is particularly brutal for organizations in the education sector.
CRA BI data
The data and insights in the CRA BI report are based on a survey conducted in January 2022 among 300 IT and cybersecurity decision-makers and influencers. Among the study's key findings:
• Forty-three percent (43%) of respondents suffered at least one ransomware attack during the past two years. Among them, 58% paid a ransom, 29% found their stolen data on the dark web, and 44% suffered financial losses.
• Thirty-seven percent (37%) said they lack an adequate security budget, while 32% believe they're powerless to prevent ransomware attacks because threat actors are too well-funded and sophisticated.
• Remote workers and cloud platforms/apps were the three most common attack vectors: o Remote worker endpoint (36%) o Cloud infrastructure/platform (35%) o Cloud app (SaaS) (32%) o Trusted third-party (25%) o DNS (25%) o Software supply chain provider/vendor (24%)
• Exploitable vulnerabilities accounted for the most common initial infection point (63%), followed by privilege escalation (33%), credential exfiltration (32%), and averse mapped shares (27%).
• Respondents are most concerned about losing access to their organization's sensitive data (70%); stolen data being sold on the dark web (58%); ransomware gangs gaining privileged access and/or controlling directory services (53%).
• Companies are not taking the threat lying down: 62% will increase ransomware protection spending.
A closer look at education
Sophos commissioned research agency Vanson Bourne to conduct an independent, vendor-agnostic survey of 5,600 IT professionals from mid-sized organizations (100- 5,000 employees) across 31 countries. 320 respondents were from lower education i.e. organizations that cater to students below 18 years, including primary, secondary, elementary, high school, and K-12 institutions. 410 respondents were from the higher education sector, encompassing organizations catering to students above 18 years such as colleges and universities.
Given the many differences between a small school and a larger university, separating education in this way enables us to gain greater insights into the challenges and experiences faced by different types of education organizations. The survey was conducted during January and February 2022, and respondents were asked to respond based on their experiences over the previous year.
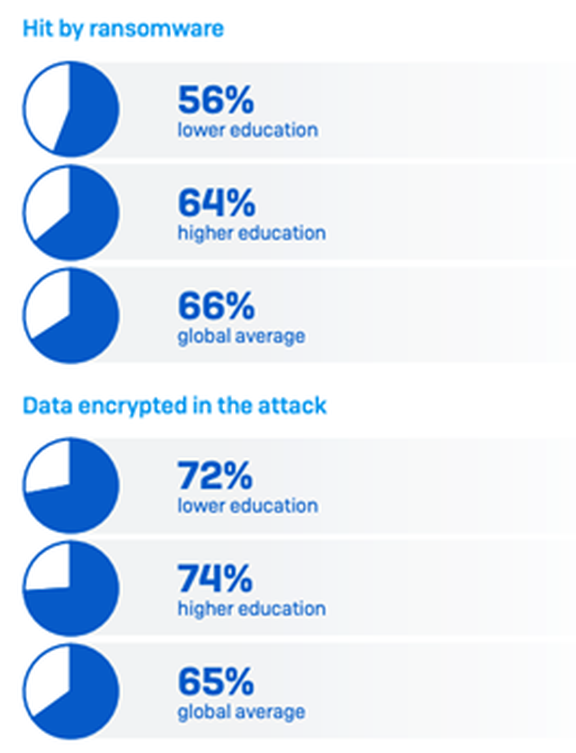
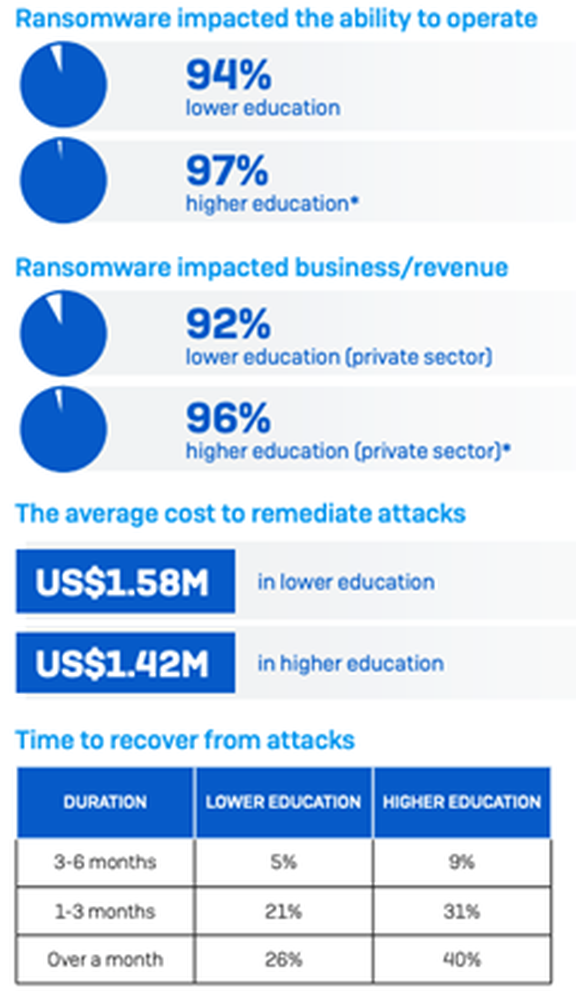
Whether affected organizations are focused on lower or higher education, attack rates are high:
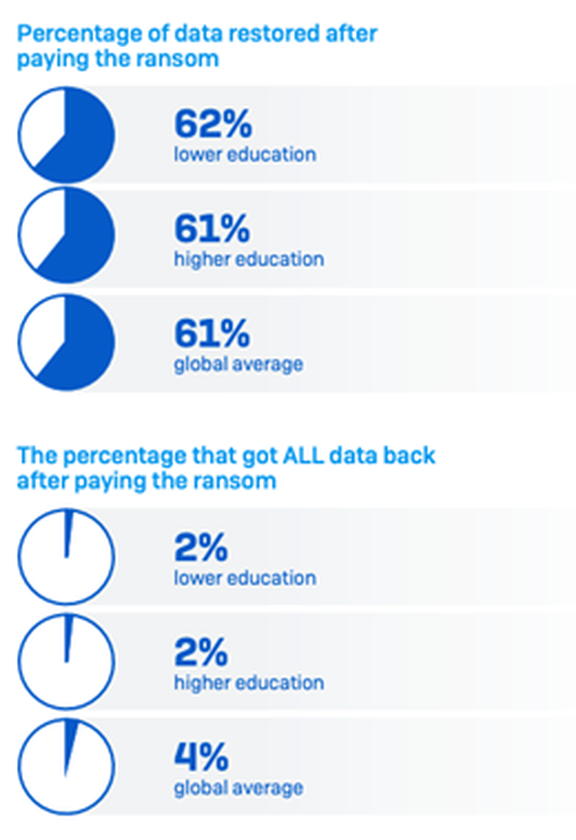
The findings show that a majority of respondents had to pay a ransom to get their data back:
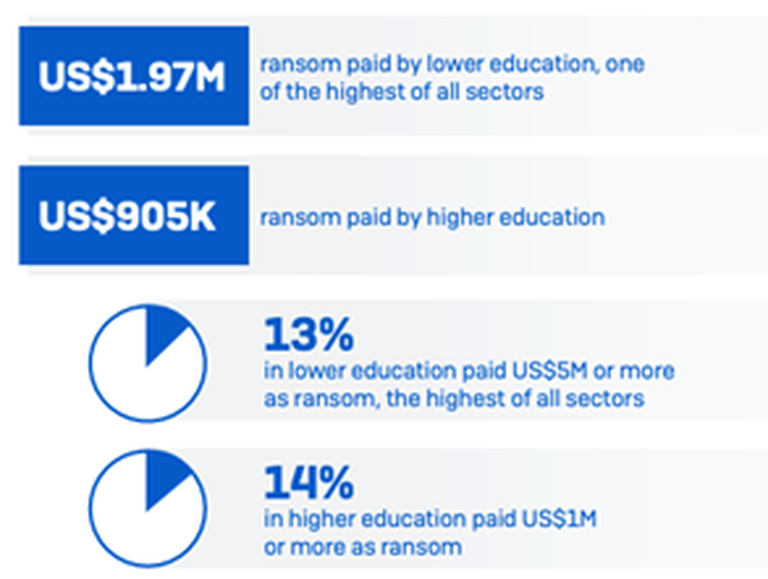
Unsurprisingly, the financial cost was high:
Attacks proved costly beyond what organizations paid in ransom:
Lower cyber insurance coverage
Meanwhile, across all sectors, on average 83% of organizations had secured cyber insurance against ransomware. In comparison, only 78% of lower education and higher education organizations have coverage.
For those with cyber insurance, the process for securing coverage has changed over the last year for over 90% of respondents:
- 39% in lower education and 44% in higher education say fewer providers are offering cyber insurance.
- 50% in lower education and 49% in higher education say the level of cybersecurity they need to qualify for cyber insurance is now higher.
- 46% in lower education and 40% in higher education say policies are now more complex.
- 35% in lower education and 41% in higher education say the process takes longer.
- 34% in lower education and 31% in higher education say it is more expensive.
Improving defenses
While there's no easy way to defend against ransomware, there are measures institutions of education can take to protect their systems and data better. CRA BI’s ransomware report gave the following examples:
Security awareness training: While not perfect, and users will likely continue to click on links they shouldn't, the first line of defense is teaching users to be aware of the risk of malicious links and attachments. The fewer malicious links staff click upon, the fewer attacks the security team will have to respond to. With phishing being a common initial attack vector, ensure email anti-spam and anti-malware defenses are as robust as possible.
Asset management: The security team can't protect systems they don't know exist, so gaining an accurate listing of systems, cloud services, endpoints, and more in the network will help teams understand what systems need protecting and keeping up to date. Pay special attention to how credentials and access are managed, system configurations, network shares, and all software is kept up to date.
Keep systems up to date and safely configured: Be sure to implement an effective vulnerability and configuration management program. Have systems scanned for outdated software, misconfigurations, excess access rights, and more. And when these things are identified, be sure to remediate the situation quickly.
Data management: Knowing where critical data resides is the first step to protecting it from being encrypted by criminals. Not only can data be better protected, but it can also be securely backed up in case of a ransomware attack and then readily restored.
Multifactor authentication: Ransomware attacks typically involve stolen login credentials, either for the initial compromise, moving laterally within the organization, or perhaps both. Two-factor authentication can go a long way to cutting these attacks short.
Trust no one: Zero trust is all the scuttlebutt in cybersecurity today. Still, it's just a term that should mean nothing attempting to gain access to a system or network (whether human or machine) should be trusted by default until they've proven themselves trustable. Because attackers use stolen credentials to gain access to systems within an organization, zero trust should mean monitoring for more attributes in which trust can be built: is the user accessing this system from a trusted or known network? Are they acting and using data in a typical way? What about the endpoint they are using? If there's anything suspicious, it would be a good idea to limit that account's access until they can prove they're who they claim to be.
Begin segmenting your networks: Network segmentation is another strategy that helps to reduce risk. Once an attacker is on the network, they move to other systems. If the network is wide open and can access any system from the point they gained entry, an enterprise could be in trouble. Segmenting networks makes it much more challenging to wander from system to system throughout the organization at will.
Incident response: If there's been a breach, and it's a safe bet that every organization will be breached, the organization needs to be able to identify that it's been breached and have a plan in place to mitigate the damage as much as possible. This means having a team in place. They develop playbooks for different attacks and situations and practice their response.