The threat group APT 29 has apparently returned to action with ESET uncovering three new malware families it is attributing to the cybergang.
Apt 29/The Dukes is best known as being the primary suspect behind the Democratic National Committee breach during the runup to the 2016 U.S. presidential election, but the group had remained quiet for the most part since that attack.
“This left us thinking that the group had stopped its activities,” ESET reported.
This changed recently when APT 29/The Dukes, aka Cozy Bear, were tied to the three new malware entities named, PolyglotDuke, RegDuke and FatDuke, that were used in campaigns with the last being noticed in June 2019. Collectively ESET named all The Dukes activities, both past and present, Operation Ghost. ESET believes Ghost has been functioning since 2013, but kept out of sight under the cybersecurity industries radar.
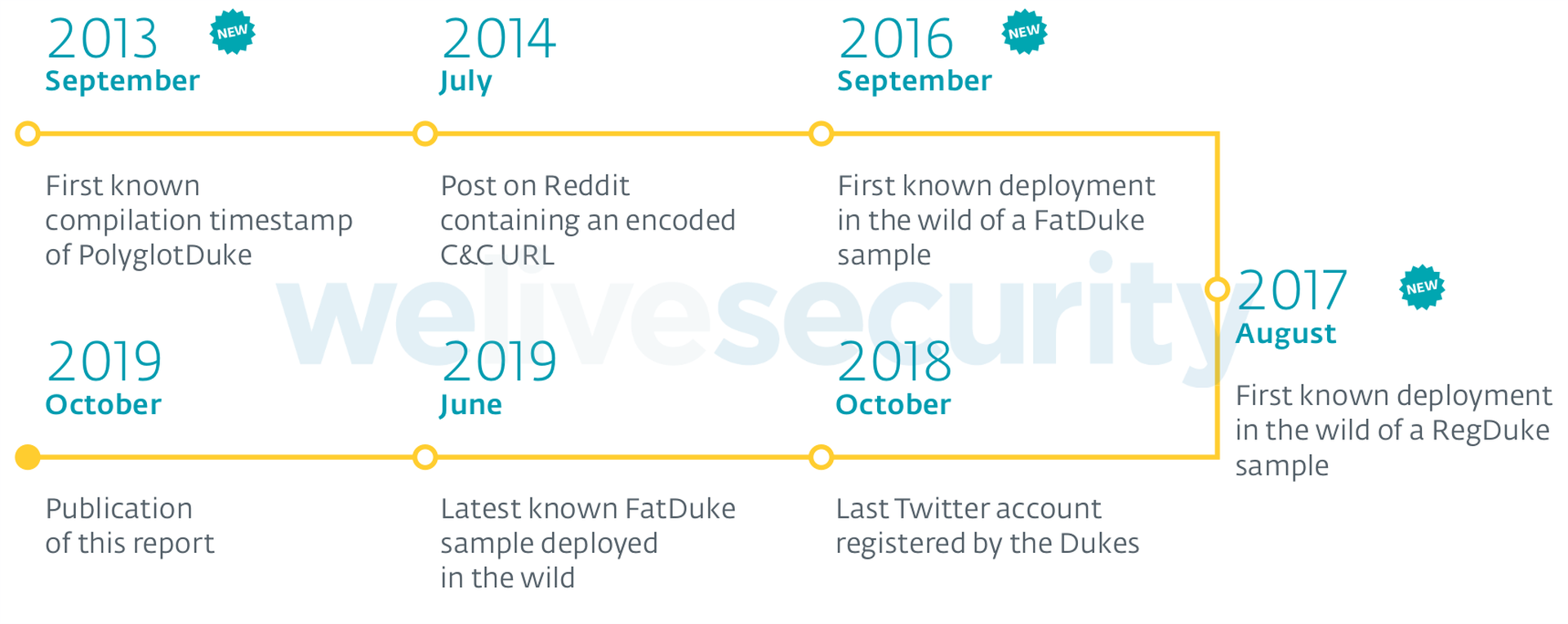
ESET accomplished its attribution primarily by comparing the techniques tactics and procedures (TTP) associated with the new attacks to older campaigns known to have been launched by the group.
These similarities include the use of social media sites to host the command and control servers, steganography in images to hide payloads or C&C communications and using Windows Management Instrumentation for persistence.
The targets hit during the most recent attacks also harken back to The Dukes earlier victims being ministries of foreign affairs that were previously struck by the group.
ESET did temper the faith it has in its attribution stating “that one based only on the presence of known Dukes tools on the same machines should be taken with a grain of salt. We also found two other APT threat actors – Turla and Sednit – on some of the same computers.”
In addition, the similarities found in the underlying code between current and past attacks do lend credence tying in APT 29/The Dukes, but ESET said it cannot discount the possibility that these are part of a false flag operation.



