Vendor: CounterCraft
Price: $50,000
Contact: http://www.countercraft.eu
Quick Read
What it does: CounterCraft Cyber Deception Platform minimizes the impact of attacks using buffer zones and focuses on threat intelligence and achieves high adversarial interaction by leveraging real decoy servers, not emulations.
What we liked: The look, feel, and response of the decoy systems are identical to those in the production environment. We thought new Rule Interface was extremely intuitive and lets security teams make changes with simple, drag-and-drop functionality.
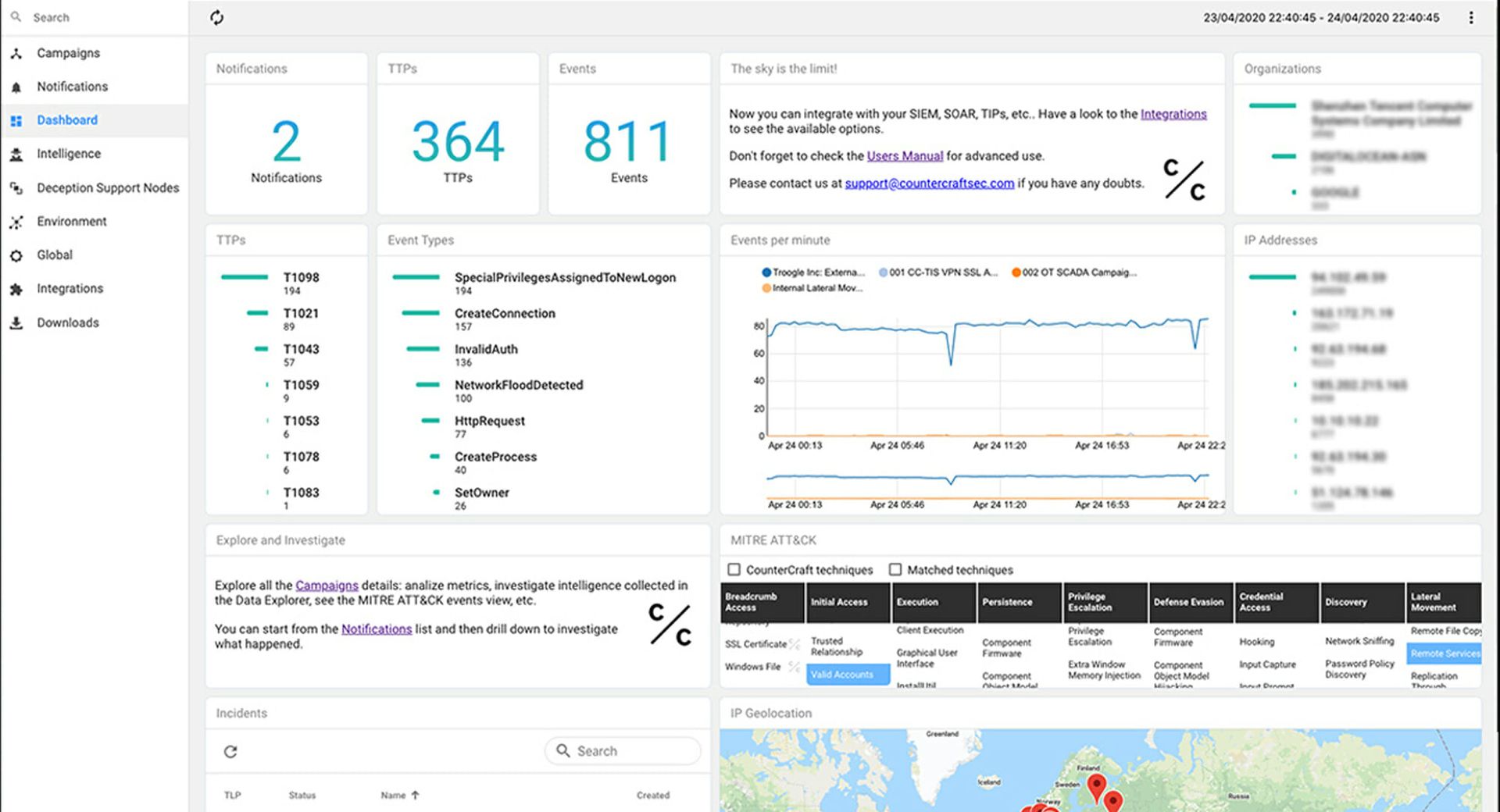
Security pros will find CounterCraft Cyber Deception Platform a full-spectrum deception product that minimizes the impact of attacks using buffer zones. In these buffer zones, assets assume the role of threat hunters and offer real-time attack detection with targeted and actionable threat intelligence.
The platform itself covers three primary use cases: detection, TTP collection, and adversary management. It builds and deploys synthetic environments with high-interaction assets and design campaigns to make them as realistic and attractive to adversaries as possible. The look, feel, and response of the decoy systems are identical to those in the production environment. Deception breadcrumbs lead adversaries deeper into deception environments where they will likely interact with full-blown deception operating systems, prolonging the interaction. Security teams may extract the telemetry information gathered from these adversary-deception interactions to gain insight into current environmental activities without making adversaries suspicious.
CounterCraft Cyber Deception Platform deploys asset campaigns as well as assets. The operation tools let security teams configure the deception environment with customizable, out-of-the-box options based on specific campaign types, such as external or spear phishing campaigns. The Campaign Builder houses a catalog of templates that automatically creates a skeleton campaign. Analysts may then take this skeleton campaign, fill in any missing information, and activate it in on their environment. Once built, the campaigns have cards that indicate which deception hosts and services are running, simplifying otherwise complex deception management. Analysts may also build reusable, custom breadcrumbs. These are managed directly from the console using an intuitive registry that shows the location of every breadcrumb within an environment.
We thought the Rule Interface was one of the most significant and valuable improvements to the platform. Rules serve as triggers for automated responses. Previously, organizations found the limited automation and complex rules difficult to negotiate. However, configuring rules feels much more intuitive with the new interface which lets security teams make changes with simple, drag-and-drop functionality. Security teams will also appreciate the breadth of known attacker behavior patterns that develop from the event correlation that the platform conducts automatically. Platform response capabilities complement existing security investments with prioritized decisions and actionable suggestions. The platform even includes a built-in breach and attack simulation tool that uses real-world attacks, demonstrating the value of having a deception product deployed within an environment.
CounterCraft Cyber Deception delivers simplicity by offering easy intelligence collection, analysis, and deployment. We think it’s a solid deception product that focuses on threat intelligence and achieves high adversarial interaction by leveraging real decoy servers, not emulations. These deceptions do not just act as mere tripwires. They can actually operate outside traditional network environments and offer automated adversary management and function. The massive API comes fully documented and easily integrates with several third-party tools. Those interested in extracting with TTPs, IoCs, threat intelligence incorporation, and MITRE ATT&CK mapping will likely find this solution a particularly wise investment.
The product costs $50,000 and includes a global partner network for local support and deception consultation. Professional services are available for custom deception assets and campaign design.



