
Web-based applications provide speedy and convenient services to businesses and the general public. These applications can include online shopping platforms, email, banking, education, entertainment and social media. Undoubtedly, there are many popular apps — and all of them have the potential to be a threat actor’s next greatest exploit.
Like sharks drawn to blood in the water, cyber criminals see easy prey in the vast "hunting ground" of vulnerable web applications. Recent statistics paint a grim picture:
- In 2020, more than 37 million records were stolen, and web applications were at the center of 39% of breaches.
- In another study, 50% of all sites tested by NTT Application Security were discovered to have at least one serious exploitable vulnerability throughout 2021.
- And in Verizon’s 2022 Data Breach Investigations report (DBIR), over 60% of the 18,000 security incidents reported to the team were associated with hacks of basic web applications.
Each of these attacks involves exploiting vulnerabilities in an app’s code to gain access to databases containing sensitive data. Once they’re in, attackers can make off with the data and use it as ransom or resell it on the black market to higher bidders.
Web-based apps and attack surfaces
With the proliferation of app usage, the average organization’s attack surface has expanded considerably. The average large enterprise has 946 custom applications deployed, with another 193 in development.
Web-based apps are everywhere: They’re on personal and business devices, they are very frequently left open and running in the background — and security updates are not always performed regularly.
Many of these apps contain personally identifiable information of users, such as financial data, medical data, or other sensitive records that can be monetized for illicit gains. This means threat actors may gain access to an open, vulnerable attack surface that can provide them with valuable information.
Which industries have suffered the most?
No industry has been spared from web-based attacks, but a handful of these face significantly more pressure than others.
The 2022 Verizon DBIR listed finance, professional services, healthcare, and public administration as the top recipients of such attacks. Another study found that the professional, scientific, and technical services industry yielded the highest percentage of sites (65%) perpetually exposed to an attack, while the education industry reported the longest average span of time to fix critical vulnerabilities (523.5 days).
- Healthcare: Web-app attacks are on the rise in healthcare, with basic web-application attacks, miscellaneous errors and system intrusions behind 76% of healthcare data breaches in 2021. After years in which insiders outpaced external actors as the top threat to healthcare, in 2019 that trend reversed as app-based attacks carried external threats into the top seat.
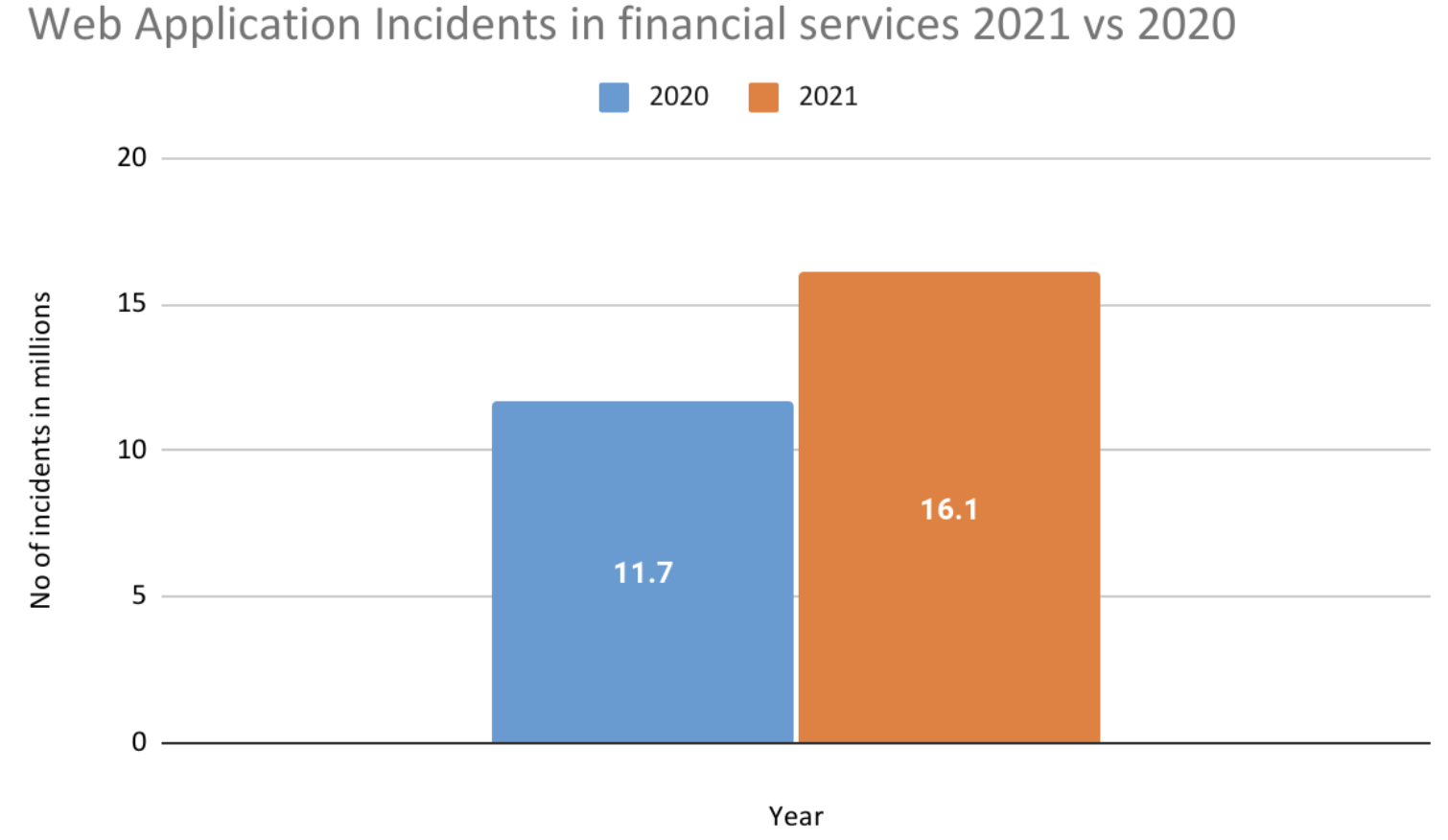
- Financial services: A popularity spike in online banking and mobile banking apps during the pandemic created greater demand for organizations to manage vast sums of data linked to personal finances. Attackers certainly saw new opportunities: Imperva Research Labs found that web-app attacks on the financial services sector increased 38% between January and May 2021.
- Public utilities and admin: Roughly two-thirds of the apps used by the utility sector and public administration organizations have a serious vulnerability that goes untreated for more than 280 days. These attacks are particularly damaging, as they allow attackers to sever the delivery of essential services — such as water, electricity, gas and telecommunications — from local communities.
Most common app-based attacks
Unfortunately, attackers have a plethora of techniques they can use to launch app-based attacks. But thanks to comprehensive attack records, it’s possible to identify some of the most common vectors.
- Cross-site scripting (or XSS): The attacker injects malicious code into a trusted website by sending the code to an unsuspecting user. Assuming the sender’s code is trustworthy, the recipient’s browser executes the code without validating it, thus giving the sender access to any records stored by the browser.
- SQL injection: This attack exploits the fact that applications must query their content database to fulfill a user’s request. However, instead of satisfying a normal content query, the attacker inserts their own SQL query on a web page, effectively replacing a benign input query with a malicious one. Successful attacks can permit attackers to spoof identity, change data, destroy data or make it entirely unavailable.
- Credential stuffing: One of the most common techniques to take over user accounts, this attack involves brute force automated injection of leaked passwords and usernames into hundreds of different sites. The attack exploits the human tendency to re-use the same password across multiple accounts and apps.
- DDoS: Distributed denial of service attacks work by pummeling an organization’s server with more requests than it can field. By overloading the server, the attack can shutter web page loading times and bring down entire websites altogether. The intent is to sever communication lines and render the app’s services unavailable. Attackers might perpetrate a DoS attack by encoding a loop counter function or specific object allocation that inputs an extremely high volume of requests.
Best practices to improve web-app security
Adversaries may have a range of attack techniques to choose from, but organizations also have a buffet of tools available to use in their defense.
- Expand visibility of the attack surface: Organizations can increase their awareness of threats by employing automated security tools that can identify and remediate vulnerabilities early in the software development lifecycle. Dynamic application security testers and interactive application security testers, such as those provided by Invicti, can work together to scan a website’s entire infrastructure of assets — revealing high-risk vulnerabilities, as well as hidden files and server misconfigurations.
- Sanitize and validate user input: A high number of app-based attacks involve exploiting weaknesses in user inputs. Organizations can significantly reduce the risk of breaches by sanitizing their data input, which can be done through eliminating unwanted characters from input, and validating to ensure that inputs conform to established alphanumeric security requirements.
- Employ white hat professionals: Organizations are highly encouraged to employ white hat professionals. These experts get inside the mind of an attacker, subjecting web-based apps to the full arsenal of possible intrusion methods, to identify lingering vulnerabilities.



