The Fast Identity Online (FIDO) Alliance has a single purpose — to move the digital world beyond reliance on passwords. Ten years after its 2012 founding, the alliance has partly succeeded, although its next steps may require a radical change in the way we authenticate ourselves online.
Here's what the FIDO Alliance has done so far, and where it's taking us next:
The origins of FIDO, and what it's accomplished
The FIDO Alliance began in mid-2012 as an effort by PayPal, Lenovo, Validity Sensors and other companies to develop open-source protocols, using biometrics and public-key cryptography, that could replace passwords. Even today, the alliance's motto is "solving the world's password problem."
"Current password authentication is weak due to reuse, malware and phishing, and leaves enterprises and end-users vulnerable to financial and identity theft," stated the alliance's launch announcement in February 2013. "FIDO-compliant smartphones, tablets, PCs and laptops can replace password dependency and exposure of sensitive user information by automatically and transparently providing user credentials when they're required."
Since then, more than 200 companies have joined the alliance, including Amazon, Apple, Google, Intel and Microsoft.
As the alliance explained in a recent white paper, there are three levels of authentication security as defined by the U.S. National Institute of Standards and Technology (NIST).
NIST refers to each as an "authenticator assurance level (AAL)":
— AAL1: A "memorized secret," such as passwords or long-term-use PINs
— AAL2: Multi-factor authentication (MFA) without phishing resistance (e.g. authenticator apps and tokens, SMS texts, and smartphone push notifications)
— AAL3: Hardware-based phishing-resistant authentication mechanisms (such as security keys)
The alliance aims to move most internet users from AAL1 to AAL3, from easily stolen passwords to theft-resistant cryptographic methods of authentication.
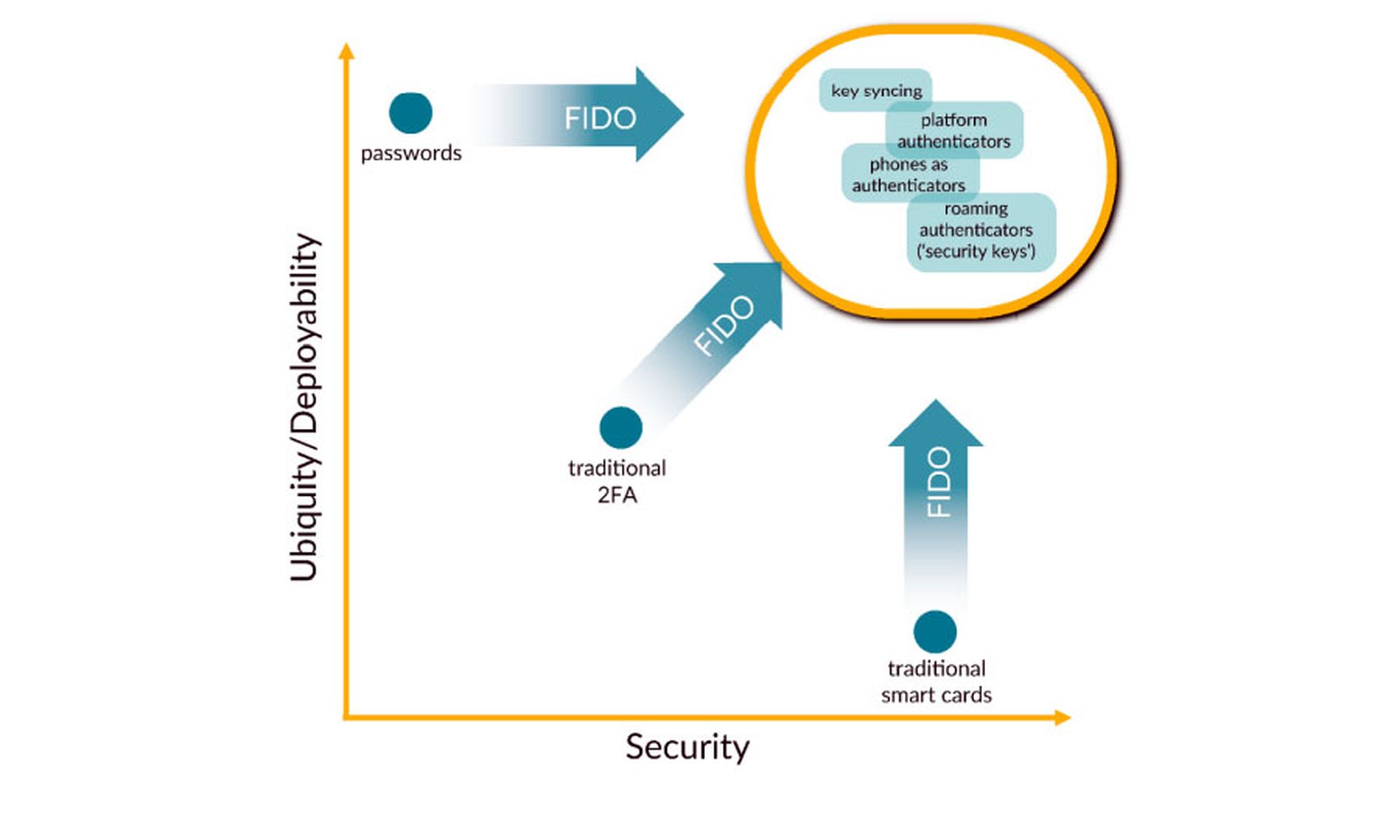
Yet most consumers today, the FIDO Alliance points out, are still stuck using passwords or PINs for almost all purposes, although "users will sometimes be asked to engage in AAL2 (e.g., for online banking)."
AAL3 devices, once "relegated to niche use cases in high-security government and enterprise settings," have become more commonplace in business environments, but most consumers will never have used one. FIDO's real achievement has been the gradual awareness of MFA as an option. Even if it usually meets only the AAL2 level of security, it’s still a lot safer than just raw passwords or PINS.
Up next — phones as authenticators
The problem is that consumers still use passwords far too often, don’t use MFA or other AAL2 solutions often enough, and barely use security keys and other AAL3 solutions at all.
FIDO's solution is to upgrade consumer smartphones and laptops to AAL3 authentication devices, as hardware security keys are now, as explained by the alliance, Apple, Google and Microsoft in May 2022.
"When you sign into a website or app on your phone, you will simply unlock your phone," said Google's Sampath Srinivas in a Google blog post. "Your account won't need a password anymore."
"To sign into a website on your computer, you'll just need your phone nearby and you'll simply be prompted to unlock it for access," Srinivas added.
If you need a second factor, a Bluetooth connection between the phone and the computer should demonstrate that you are in possession of both devices in the same place.
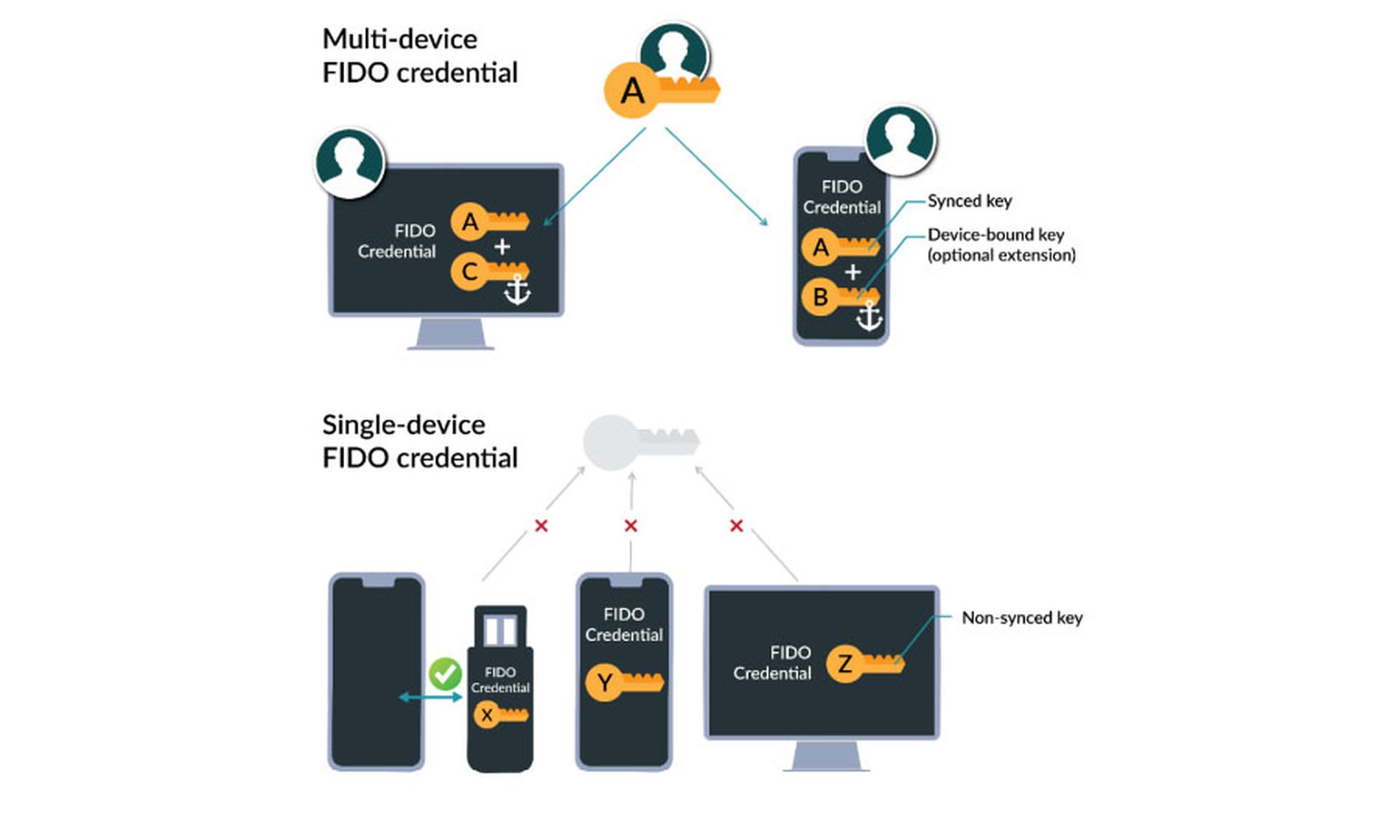
Furthermore, devices should be able to store FIDO cryptographic "passkeys" (a term that the FIDO Alliance itself doesn't use), which will be backed up to the cloud as part of normal device-platform behavior. When you get a new iPhone, Mac, Android phone or Windows laptop, your backed-up FIDO passkeys will be synced to your new device as soon as you log into your Apple, Google or Microsoft account.
This second function should solve the problem of losing access when losing or replacing authenticating devices, as explained in the March 2022 FIDO Alliance white paper entitled "Everybody Is Invited: How FIDO Addresses a Full Range of Use Cases."
"We expect that FIDO authenticator vendors … will adapt their authenticator implementations such that a FIDO credential can survive device loss," says the white paper. "This means that users don’t need passwords anymore: As they move from device to device, their FIDO credentials are already there."
The real end of passwords?
The FIDO white paper is not subtle: "FIDO-based secure authentication technology will for the first time be able to replace passwords as the dominant form of authentication on the internet," it asserts.
If the Apple, Google or Microsoft security and backup mechanisms aren’t secure enough for some vendors, the FIDO Alliance says, it will provide an optional extension using "device-bound cryptographic keys" to supply even greater security.
The catch is that the FIDO Alliance isn't saying exactly how or when these new technologies are going to be implemented. Its white paper is short on technical details and sets no deadlines. The joint Apple-FIDO-Google-Microsoft announcement that came two months later said that "these new capabilities are expected to become available … over the course of the coming year," but did not get more specific.
It's a bit hard to know how eagerly to expect these innovations. The FIDO Alliance may indeed have new specifications in beta testing that will make this brand new passwordless world a reality by 2024. Or this all could be aspirational for the moment, a map to a place where the roads haven't yet been laid out.




