The Change Healthcare breach story has taken on a new twist, with emerging ransomware group RansomHub claiming Monday it has 4TB of data stolen from the healthcare tech company in February.
The Change Healthcare platform, which is owned by UnitedHealth Group subsidiary Optum, was breached by an affiliate of the ALPHV/BlackCat ransomware group in February, causing widespread operational outages and threatening the leak of sensitive patient and client data.
A $22 million ransom payment allegedly made by Optum, which is supported by blockchain transaction records associated with ALPHV/BlackCat, was apparently stolen by the ransomware-as-a-service (RaaS) in an exit scam.
The group reportedly published a fake law enforcement takedown notice on their leak site before disappearing with the full $22 million, leaving the affiliate who performed the breach, known as “notchy,” empty-handed.
Now, RansomHub, a new ransomware group that first began claiming victims on its site in February 2024 according to SOCRadar has stepped into the picture demanding payment and threatening to leak the stolen data.
“Change Healthcare and United Health you have one chance to protecting your clients data. The data has not been leaked anywhere and any decent threat intelligence would confirm that the data has not been shared nor posted,” the group wrote in a post on its website Monday, according to screenshots published by Dark Web Informer. “In the event you fail to reach a deal the data will be up for sale to the highest bidder here.”
Qualys Threat Research Unit Cyber Threat Director Ken Dunham told SC Media in an email that Change Healthcare’s situation demonstrates that ransomware payouts are “tricky business.”
“This can be explained through shifts in the criminal marketplace, lying by bad actors, multiple compromises, or other scenarios. It is not uncommon, as an incident responder, to discover not just one threat inside of a compromised environment, but two or more,” Dunham said. “It is also not uncommon for companies that give in to bad actors performing extortion, such as ransomware and DDoS payouts, to become ‘soft targets,’ quickly hit again with additional forms of extortion again and again.”
Malware resource-sharing group vx-underground subsequently posted a conversation one of its administrators had with a RansomHub admin, indicating that “many” former ALPHV/BlackCat affiliates had joined the group.
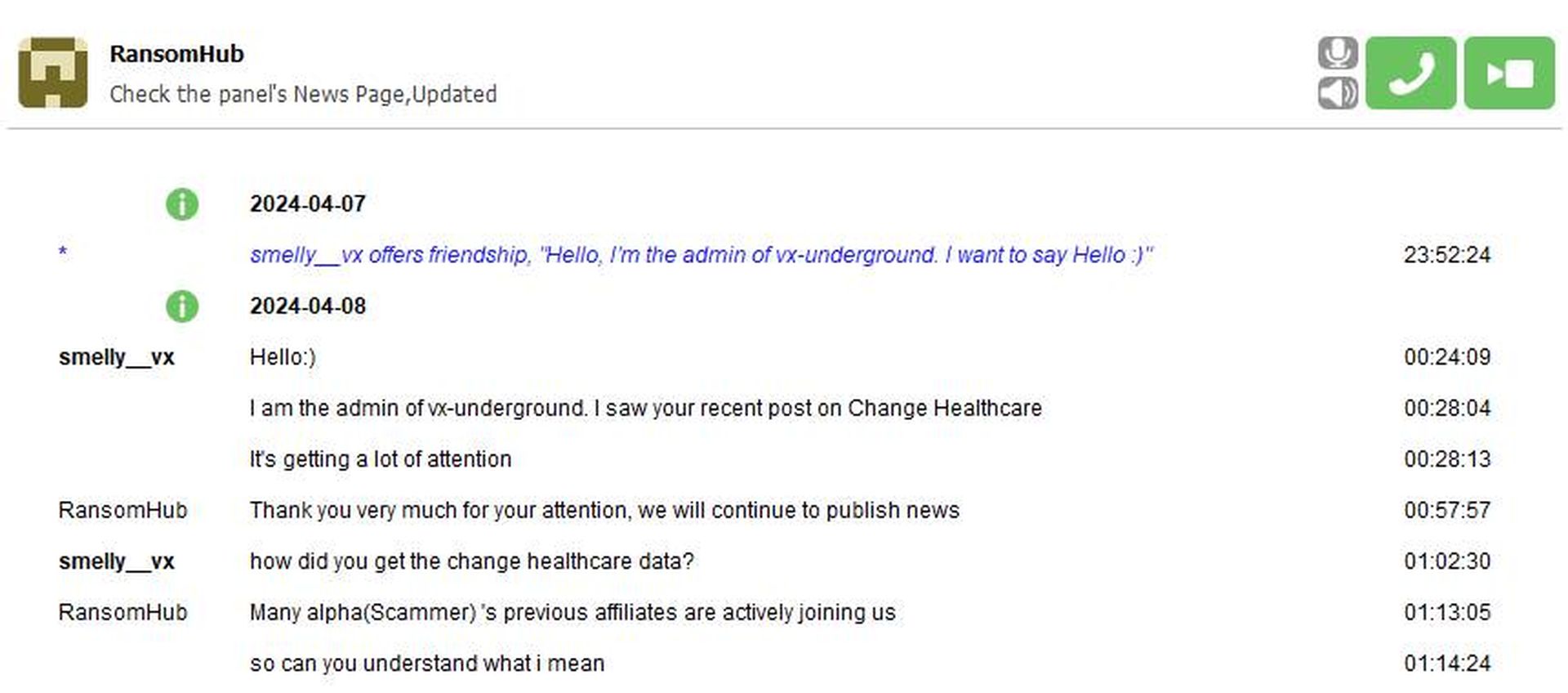
Vx-underground admin's conversation with RansomHub (Image courtesy of vx-underground)
Ransomfeed also noted that it cross-referenced all 28 victims RansomHub has posted on its site with ALPHV/BlackCat victims and found only two overlaps, including Change Healthcare. This further supports the hypothesis that RansomHub is not a rebranded version of ALPHV/BlackCat, but a new group recruiting past affiliates.
“This comes as no surprise. We had previously outlined this scenario in our blog post, foreseeing the potential for such alliances in the cybercriminal ecosystem,” Ngoc Bui, a cybersecurity expert at Menlo Security, told SC Media in an email. “The involvement of a middleman, typical in ransomware-as-a-service (RaaS) attacks, adds another level of complexity and risk. It complicates the direct line of negotiation and payment to the threat actors with the data that was stolen.”
RansomHub began a countdown of just over 12 days for UnitedHealth to make a ransom payment before the dataset is sold.
The group claims that the 4TB they obtained includes medical and dental records, payment and claims information, patient personal identifiable information (PII) – including social security numbers – and PII of active U.S. military personnel. The group also claims to have more than 3,000 source code files for Change Healthcare’s software solutions.
“Healthcare providers stand to experience some of the worst consequences of cyberattacks and data breaches, as they manage immense amounts of sensitive personal and health information about staff, members and patients,” Darren Guccione, CEO and co-founder of Keeper Security, told SC Media in an email. “Government officials and industry leaders have long advised against paying ransoms, because while doing so may seem like the simplest solution to a ransomware attack, this only fuels the explosive growth of this criminal activity.”
SC Media reached out to Optum to ask whether it would update clients, patients and law enforcement about the development, whether it has had any contact with RansomHub and whether it could confirm or deny any prior ransom payment and did not receive a response. The last update to UnitedHealth Group’s information page on its Change Healthcare cyber response as of this writing was on March 27.
Dunham offered this additional advice for victims of ransomware: “Disaster Preparedness (DR) planning must carefully consider all the implications of payout or not, when it comes to extortion and ransomware, to avoid the pitfalls of becoming a soft target or introducing additional risks unwittingly without considering the TTPs of bad actors, insurance coverages, regulatory and other requirements.
“Of course, breaches are best prevented in the first place, if possible, with strong cyber security hygiene and layered SecOps,” Dunham concluded.




