Old-fashioned vulnerability management may no longer fit the bill. Here’s how continuous threat exposure management (CTEM) discovers, prioritizes, and validates potential risks and aligns remediation with business goals and compliance frameworks.
Continuous threat exposure management (CTEM) has emerged as a vital paradigm shift in cybersecurity strategy, addressing the inadequacies of traditional vulnerability management. In an era where data breaches and ransomware attacks persist despite substantial investments in cybersecurity, CTEM offers a proactive and holistic approach to identify, prioritize, and mitigate risks while aligning remediation efforts with business objectives and compliance frameworks.
What CTEM is
Gartner introduced CTEM in July 2022 as a comprehensive program that continuously evaluates the accessibility, exposure, and exploitability of an organization's digital and physical assets. Unlike reactive vulnerability management, which focuses on patching known vulnerabilities, CTEM anticipates and addresses potential threats before they manifest into significant security incidents. By integrating tools such as penetration testing as a service (PTaaS), attack surface management (ASM), automated pen-testing, and red-teaming, CTEM ensures a proactive defense posture.
How CTEM works
The essence of CTEM lies in its proactive nature, emphasizing integration, iterative solutions, and continuous improvement of security posture and cyber resilience. This approach fosters clear communication between security personnel and executives, aligning threat mitigation strategies with organizational goals. By making the role of Chief Information Security Officers (CISOs) more comprehensible to C-suite executives, CTEM enhances the effectiveness of security programs and promotes a culture of cybersecurity awareness throughout the organization.
CTEM operates on a cyclical process defined by Gartner, comprising scoping, discovery, prioritization, validation, and mobilization. Scoping involves defining the organization's total attack surface, encompassing internal and external vulnerabilities. Discovery utilizes ASM tools to identify potential threats and vulnerabilities, while prioritization triages risks based on their likelihood of exploitation and potential impact, aligned with business feasibility.
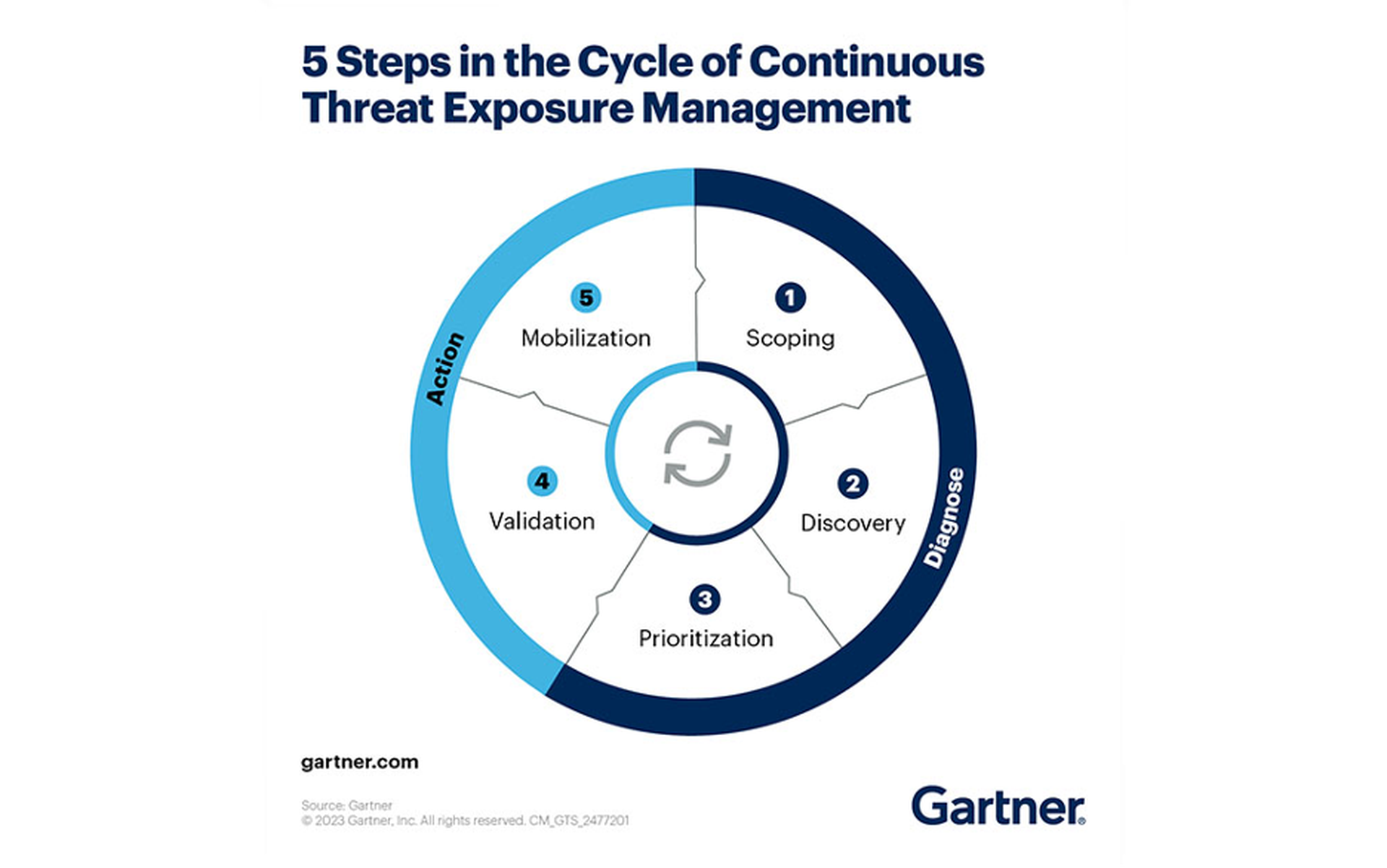
Validation is a critical step in confirming the existence and severity of identified threats, employing techniques like red-teaming and automated breach-and-attack simulation. Mobilization focuses on implementing remediation measures for validated high-priority threats, ensuring alignment with business objectives and effective communication across departments.
Exposure management, a key component of CTEM, assesses, prioritizes, and validates potential threats within a continuous cycle. It encompasses three crucial steps: determining the attack surface, assessing exploitability, and validating the threat's validity. By continuously reassessing an organization's security posture and risk exposure, CTEM minimizes vulnerabilities and enhances overall security resilience.
The necessity of CTEM and exposure management lies in their ability to foster a proactive security culture, efficiently addressing cybersecurity challenges before they escalate. By leveraging existing security tools and procedures, organizations can seamlessly integrate CTEM into their operations, optimizing resource usage and meeting compliance requirements.
Ultimately, CTEM represents a shift towards outcome-driven, business-tuned metrics that enable informed decision-making at the executive level. It acknowledges that while complete risk elimination may not be feasible, strategic risk reduction aligned with organizational goals is paramount. By prioritizing vulnerabilities and threats based on their impact and viability, CTEM empowers organizations to navigate the complex landscape of cybersecurity effectively.
Conclusion
CTEM embodies a common-sense approach to cybersecurity, offering a pragmatic and systematic framework to continuously refine priorities and mitigate threats. By embracing CTEM, organizations can proactively safeguard their assets, enhance resilience against evolving cyber threats, and ensure alignment between security initiatives and business imperatives.




