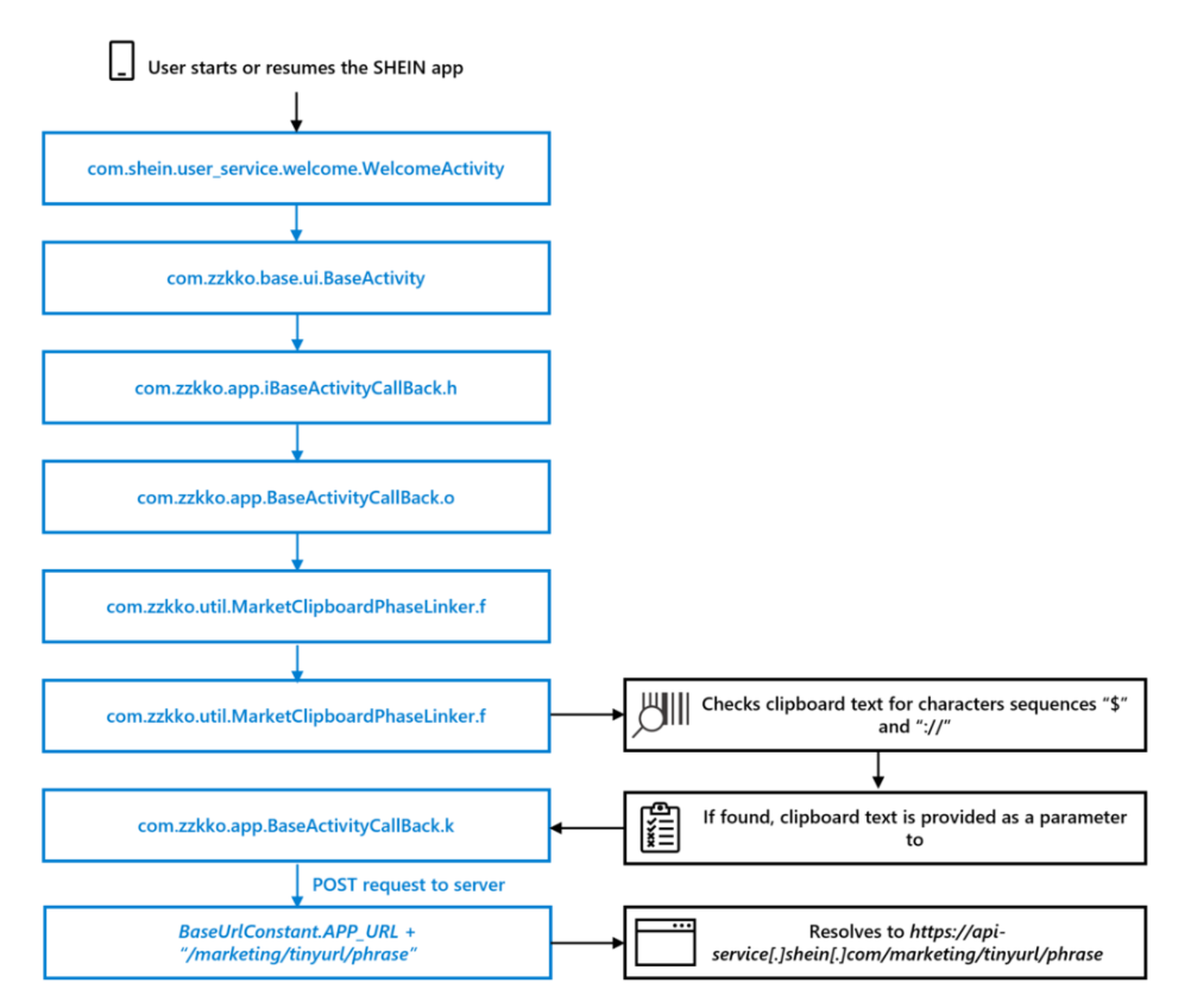
A version of the Shein shopping application, which has over 100 million downloads in Google Play, unnecessarily accessed the clipboard of Android devices and transmitted the contents to a remote server, posing security concerns.
In a March 6 blog post, Microsoft researchers said they discovered the issue in version 7.9.2 of the app released Dec. 16, 2021, and confirmed that Shein addressed it as of May 2022. Users need to keep the installed application updated to prevent potential malicious attacks.
Clipboards can be an attractive target for cyberattacks because mobile users often use them to copy and paste sensitive information, such as login credentials, financial data, and personal information. Threat actors can exfiltrate clipboard data to launch phishing attacks, steal passwords, or perform other fraudulent activities. There are even examples of attackers modifying clipboard contents for malicious activities, such as changing cryptocurrency wallet addresses before users paste them into a crypto wallet app.
Microsoft said they could not specify malicious intent regarding SHEIN's case but suggested that the feature of accessing clipboards was not necessary. SC Media has reached out to Shein for further information.
"Even if SHEIN's clipboard behavior involved no malicious intent, this example case highlights the risks that installed applications can pose, including those that are highly popular and obtained from the platform's official app store," Microsoft said.
The tech giant identified and verified Shein’s clipboard behavior by performing static analysis of the app to find "the relevant code responsible for the behavior" and then doing a dynamic analysis to run the app "in an instrumented environment to observe the code."
Following Microsoft's research findings, Google recognized the potential threats associated with clipboards and has made the following efforts to secure the Android platform.
- On Android 10 and above, apps cannot access clipboard data unless it is set at the default input method editor.
- On Android 12 and above, a toast message notifies the user of the clipboard access when an app calls to access clip data from a different app for the first time.
- On Android 13, the clipboard contents will be cleared after a certain period of time to enhance protection.