As with so many elements of cyber threats: Everything old is new again.
In this case, the QakBot malware that has been around for roughly 15 years, has reared its ugly head more aggressively in the past year, and IT security is meeting this with a firm and proactive response.
On Thursday, Trustwave SpiderLabs released a new article and decryption tool to aid financial services institutions (FSIs) in finding and rooting out the QakBot Trojan, which has become more pervasive in the past year, spread largely by phishing emails (as is often the case).
“It’s a general-purpose piece of malware, which has become more popular recently,” according to Karl Sigler, senior security research manager at Trustwave SpiderLabs, adding that bad actors have been able to use QakBot to transfer funds from legitimate customer accounts, steal information and even load ransomware in to the FSI’s systems.
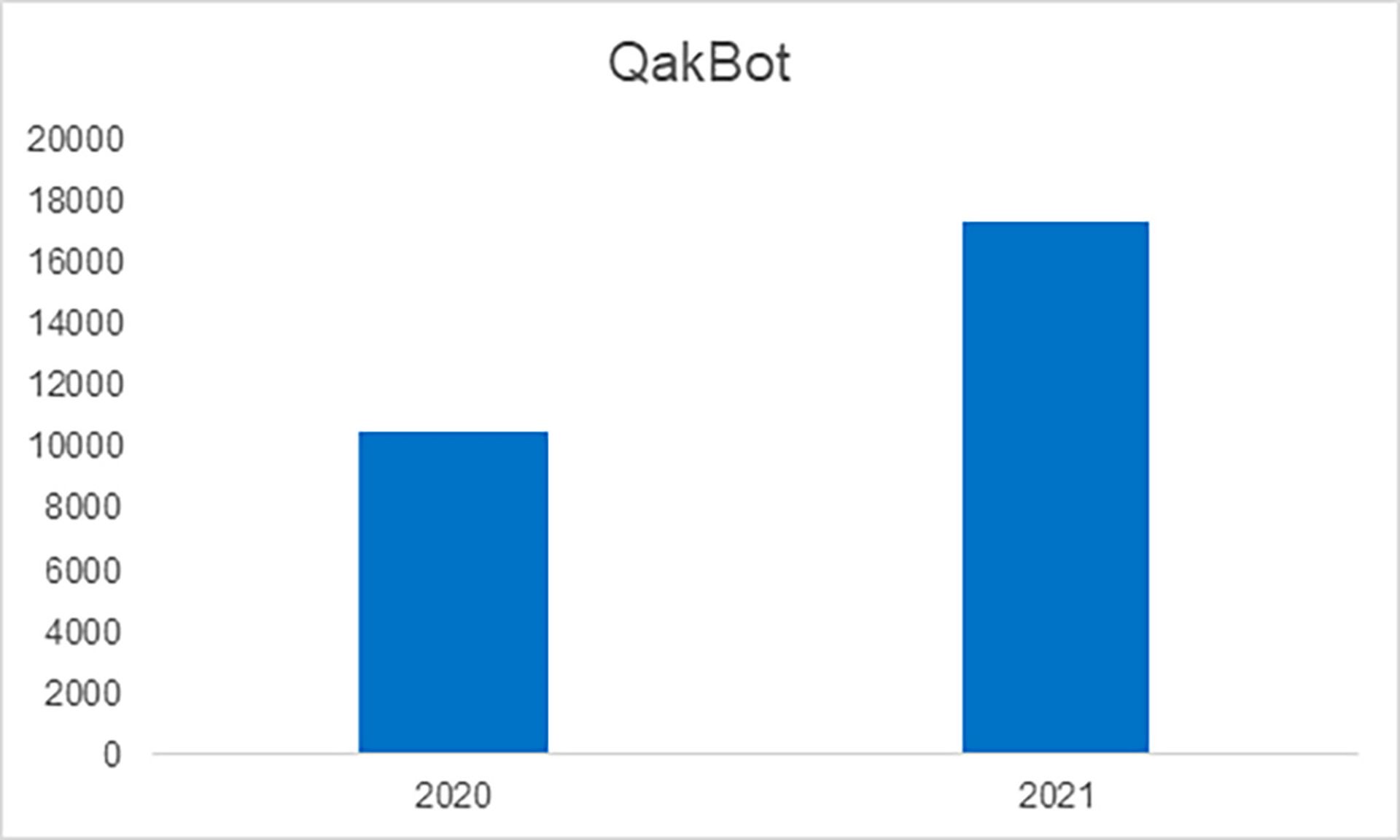
QakBot banking malware grew by roughly 65% in the first seven months of 2021, compared with the same period the previous year, according to Kaspersky. Indeed, QakBot has been on the scene since 2007. And, as is the case with many forms of malware, it has evolved as bad actors have become increasingly savvy and invested more in its development.
QakBot is, in fact, the “Swiss Army knife” of financial malware, according to Sigler, able to grab banking credentials, download ransomware, and exfiltrate business email with equal aplomb. Hence, being able to find and eliminate this persistent and impactful threat can be critical to U.S. FSIs.
“It has built a framework, rather than a ‘roll-your-own’ malware, which gives bad actors a strong foundation from which to build on,” Sigler said.
It is this “all-purpose” nature to QakBot that makes it so pernicious and so dangerous to FSIs and their customers.
Sigler’s team at Trustware did the research and the work to develop the decryption tool released Jan. 13 to help FSIs proactively seek out and nullify the QakBot malware, which typically seeks out bank credentials from the FSI site or the customer’s PC, and also monitors where financial customers go within a financial site and can inject its own code.
“We hope this gives the IT security professionals the ability to really look at QakBot information, which may be on any machine,” Sigler said. He pointed out that since the bulk of breaches and hidden malware may go unnoticed for upwards of six months, the cybersecurity tool may offer FSI IT security teams insight into finding and uprooting this malware.




