Researchers have known for years that the COVID-19 pandemic served as an effective staging ground for phishing attacks and other social engineering lures. Now, new research released by Proofpoint sheds more light on just how much of a magnet it was, outperforming other major world events and attracting everyone from cybercriminal groups and fraudsters to nation-state hacking groups.
“The global relevance of the COVID-19 pandemic created an environment primed for exploitation like none witnessed in the age of the cybercriminal,” write authors Selena Larson and Daniel Blackford. “Proofpoint researchers had not observed the entire landscape pivot to using the same social engineering theme prior to COVID-19. Over 30 known threat actors and many more unattributed threat clusters tracked by researchers used COVID-19 themes in campaigns.”
Social engineering tactics have continued to evolve as the world enters the third year of the pandemic, highlighting the need for decision-makers to stay alert for various threat actors and address risks appropriately.
Despite the COVID-19 pandemic easing off this year, Proofpoint experts found that the total number of social engineering campaigns in the first quarter of 2022 remains equal to the average number of campaigns per quarter in 2021.
Content masquerading as business communications, including changes to company policy around travel, customer interactions, work from home arrangements, and potentially termination of employment, generated the most engagement with recipients, with the highest click rate based on available data. The category includes changes to company policy around travel, customer interactions, work from home, and potentially termination of employment.
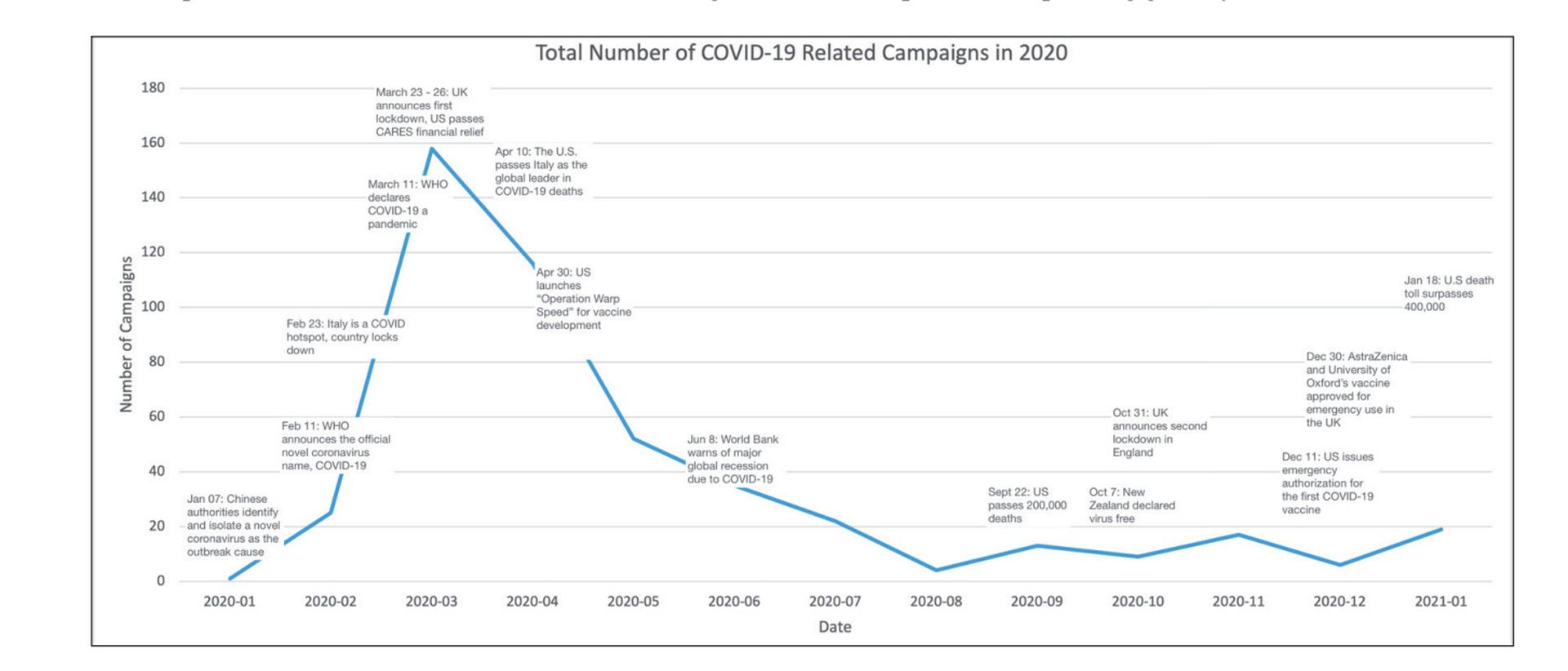
In an interview, Larson told SC Media that people interact with this type of content because they closely affect people’s livelihoods.
“Given that employment changed drastically during the pandemic that impacted people’s lives in a variety of ways, and legitimate communications about these topics were likely distributed via email, people were more likely to engage with such lures,” Larson explained in an email.
The research noted that generic themes were still frequently used lure during the first quarter this year, meaning the threat actor did not apply specific references to things - such as vaccines - but used the phrases ‘COVID-19’ or ‘coronavirus’ in the email followed by either blank email bodies or content irrelevant to the subject line.
For instance, Proofpoint researchers identified a credential phishing campaign with the email subject header "Early Covid22 Updated Request Processed on Tuesday, January 25, 2022."
The emails with COVID-themed lures had attachments that were intended to collect Adobe Cloud user information. Victims were directed to the John Hopkins Coronavirus resource center once the credentials were harvested.
The research also highlighted the return of TA542, Emotet, the most noteworthy actor leveraging COVID-19 themes so far this year. The first Emotet campaign was identified back in January 2020 using COVID-19 themes. It did not come back to the pandemic-related theme until February this year when researchers found it leveraging Excel attachments or password-protected zipped attachments, including Excel documents.
“Between January and April 2020, 13% of Emotet campaigns used COVID-19-themed lures,” the report read. “All these campaigns occurred between February and March 2022, making up nearly a quarter of all Emotet campaigns in this time.”
While there are a lower number of COVID-19 themed campaigns this year in comparison to 2020 when the pandemic just started, Larson noted that decision-makers should not drop their guard.
"Threat actors will continue attempting to capitalize on the topic as long as they stay socially relevant," Larson told SC Media.
As social engineering remains as the most critical component of cyberattacks originating via email, Larson pointed out that protecting email users and email vectors should be a top priority for organizations, particularly those heavily targeted industries with significant email traffic. This includes training individuals to identify malicious emails, using email security tools to block threats before they reach users' inboxes, and putting the right processes in place to ensure that threats can be mitigated immediately.




