The total number of organizations compromised by the MOVEit hack remains a mystery.
The Cl0p extortion group, which exploited at least one of the vulnerabilities in Progress Software’s popular file transfer service, has been publishing a steady drip of what it claims are newly identified victims daily. So far, there are no signs that the pace of reported incidents is slowing since the breach was disclosed in May.
Cl0p has posted the names of hundreds of companies, state and local governments, universities and other organizations on its dark web leak site. It's threats include leaking the data of any alleged victim if payment demands are not met. Meanwhile dozens of organizations have confirmed through media reports, public statements or regulatory disclosures that their data was indeed stolen.
That puts MOVEit in rarefied air as the most widespread file transfer hack recorded. But the daily stream of newly disclosed impacted companies has many security experts asking where the bottom is, and when Cl0p may finally exhaust its pool of companies to extort. Thus far, Cl0p is the only group that cybersecurity experts have seen exploiting one of the vulnerabilities, but Progress Software has announced a slew of similar SQL bugs in the past two months.
John Hammond, a senior security researcher at Huntress, quipped to SC Media that Cl0p "certainly knows how to drag out the news cycle."
"The MOVEit Transfer exploitation still seems to be an incident that never dies. Between the initial infection, the following vulnerabilities that we at Huntress discovered...and of course Cl0p’s continued leaking of company data, this has continued for over a month and a half now," Hammond told SC Media.
Nearly 370 organizations confirmed in MOVEit breach
Thus far, much of the public discussion around the impact of the hacks has focused on direct Progress Software’s customers, or entities that purchased or used its file transfer service. But cybersecurity experts who have sorted through the wreckage, as well as companies that specialize in scrutinizing software supply chain vulnerabilities, believe the universe of potential exposure could reach well beyond that group.
Brett Callow, a ransomware researcher at Emsisoft, has been tracking the ground-level impact of the hack, keeping tabs on every entity published on Cl0p’s site and other disclosures. Thus far, he has identified at least 369 organizations that have confirmed they were impacted by the breach or flagged as a victim by Cl0p.
He told SC Media that of those 369, at least 93 have been compromised through a third-, fourth-, or fifth-party supplier.
“The upstream/downstream is extremely complex and not all impacted [organizations] know they’ve been impacted,” Callow said in an email.
Many companies may not use MOVEit Transfer but — through what has become a normal business practice — may have sent their data to third-party providers who did. When those providers were exploited, they may have also exposed the information sent to them by other parties.
Hammond said it’s “easy to see” that multiple victims who did not use MOVEit Transfer themselves have been affected in the hack only because they relied on a provider who did.
“I’d agree this is a sort of a trickle-down effect, like a set of falling dominos…[that] can come from simply having data used in other locations, or software integrations or connected applications that bridge technologies,” he said. “Any technical way that organizations rely on one another could be used and abused by threat actors.”
Those are the kind of relationships that firms like Exiger, a supply chain risk management firm that caters to government agencies, banks and other entities, have been attempting to map out in the wake of the MOVEit vulnerability disclosures.
The company scrapes, collects and curates a variety of data points from the internet, capturing not just companies who have directly bought and used MOVEit, but also those who have contracts with third-party suppliers and providers that use the software, companies that purchased software bundles from sources like Carahsoft that are known to include MOVEit, and companies that post job descriptions that explicitly call for candidates who have experience with the file transfer service.
“We’re using multiple sources of data to get a picture of the installations [of MOVEit] and…different ways that we tie a company to a piece of software,” Munish Walther-Puri, vice president of cyber risk at Exiger, told SC Media.
According to data and figures shared with SC Media, there are at least 73,000 entities that Exiger is “moderately confident” have some type of meaningful relationship to MOVEit that could have exposed their data to theft in the hack.
If you take that a level further and begin examining the relationships between those firms and their software supply chain, the numbers rapidly balloon from there.

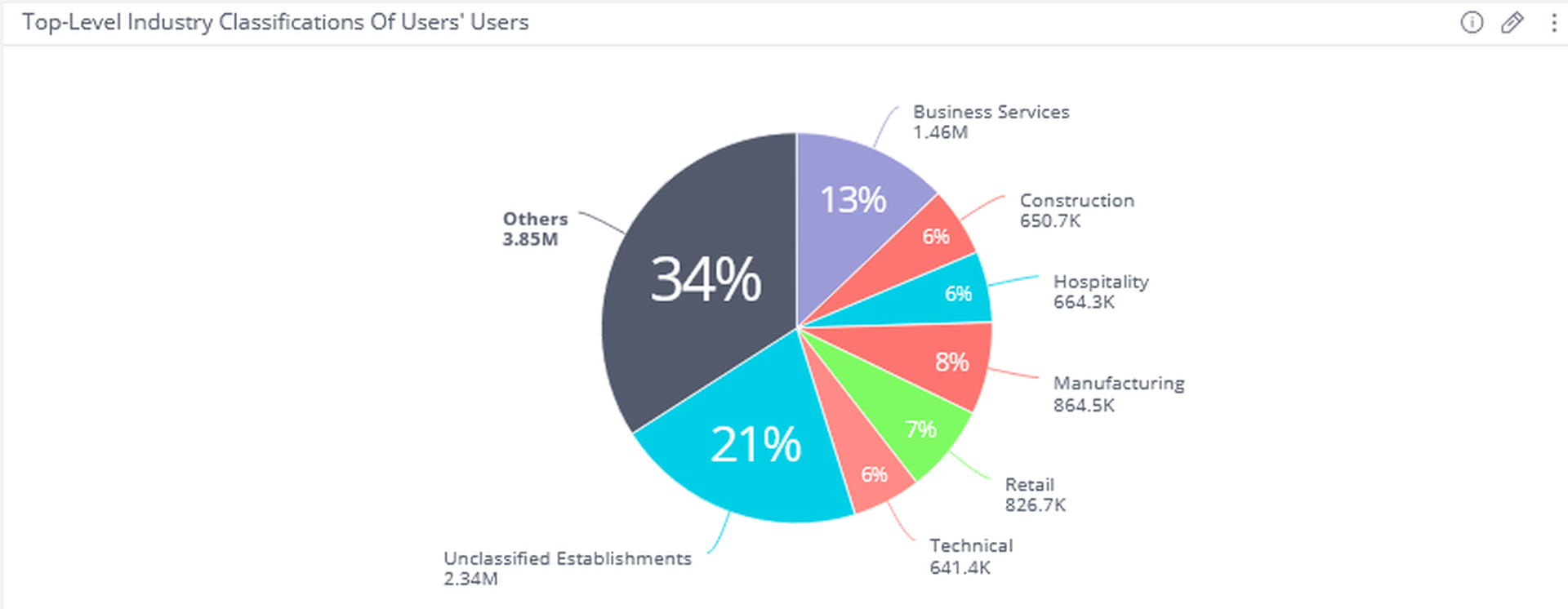
Walther-Puri noted that when looking at the data, there were no obvious signs that the impact was overly concentrated in any particular business sector, another sign of the potentially widespread nature of the hack.
To be clear, Exiger is not claiming that all — or even most — of these entities were exposed or had data compromised. Rather, the statistics are meant to illustrate the broad universe of entities who have some type of meaningful risk or dependency associated with MOVEit, either directly or through their software supply chain.
The danger is more than hypothetical. For instance, at least 52 of the entities on the list of firms impacted by the MOVEit bug are known or believed to be customers of Zellis, a UK-based payroll provider. In June, a number of customers, including the BBC, Boots, British Airways and Aer Lingus, confirmed that their data was stolen in the MOVEit hack via Zellis. Last month, the company said at least eight of their customers have been compromised in this manner.
Another organization known to be affected, the National Student Clearinghouse, partners with more than 3,500 schools across the country. At least 65 schools have been confirmed or claimed as victims in MOVEit thus far, and Callow believes the compromise of the NCS could auger many more disclosures in the public education space in the coming weeks and months.
However, Hammond also that after a month and a half of widespread publicity around the vulnerabilities, intense patching cycles and round after round of disclosures, he "believes/hopes" that such trickle-down impacts are not “anywhere near as prominent” today as they were at the outset.
A complex web of dependencies leave organizations exposed
While awareness of software supply chain entanglement has risen among businesses and policymakers in recent years, security experts say hacks like MOVEit provide a stark reminder of how frequently organizations rely on and share data with third-party providers. That complex web of dependencies can result in organizations being exposed to a hack without even knowing it.
“Connections between systems have eased the ability to move data between organizations, but have certainly added complexity when it comes to application security and the consequences of a successful attack vector,” Kristen Bell, an application security expert at GuidePoint Security, told SC Media.
Bell notes that our information is now stored by banks, hospitals, doctors offices, local, state and federal agencies, among other sources. Being able to easily share data from master records has given us the ability to leverage master or single source data rather than having to duplicate it in multiple places. The flip side of that coin is that data is much harder to protect in transit than it is to protect at rest.
“In short, these types of issues are likely to continue to emerge. There is no silver bullet in terms of prevention because it's hard to be proactive about the unknown when it comes to third-party supply chain issues,” she said.