Ransomware is everywhere. It plagues businesses big and small, across the globe, even in the most hidden corners.
Still, over the past year, certain industries have been feeling the pain more than others. A Malwarebytes quarterly report released last August found that detections of ransomware among organizations rose 365 percent from Q2 2018 to Q2 2019, with a particularly high frequency of attacks against cities and municipalities, health care facilities and educational institutions.
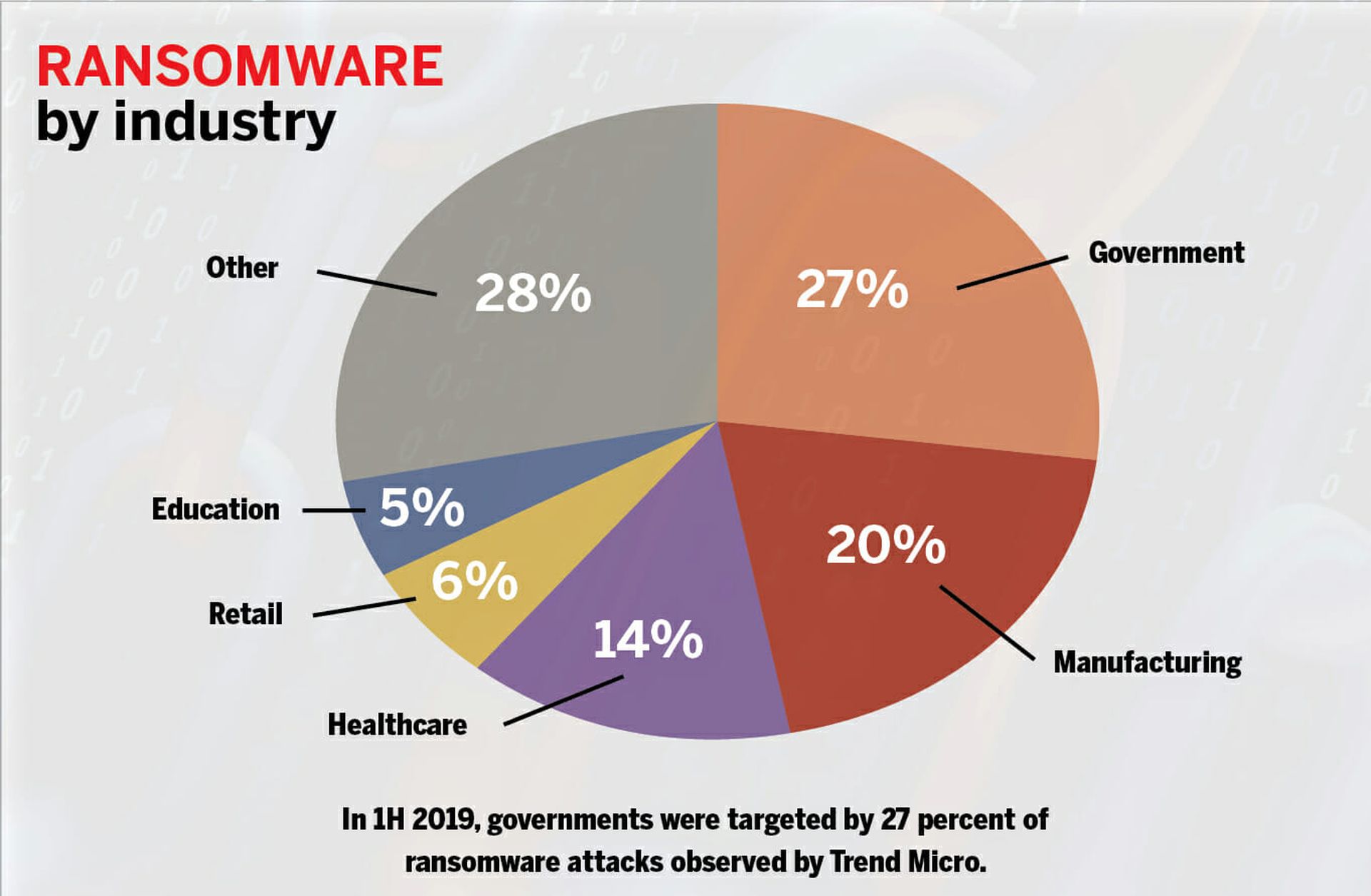
Telemetry from Trend Micro’s global threat intelligence network picked up on similar trends. In July, the cybersecurity firm reported that in the first half of 2019, governments were most often targeted by ransomware (27 percent of observed attacks), followed by manufacturing companies (20 percent) and health care organizations (14 percent). Retail and education were neck-in-neck after that.
For this feature, SC Media asked top cyber experts to look at four key business categories – manufacturing/industrial, health care, government/cities and school districts – and provide perspective on why they have become such viable targets.
Manufacturing & heavy industry
In March 2019, Norwegian aluminum producer Norsk Hydro was hit with a crippling cyberattack that, according to early estimates, caused over $40 million in damages due in large part to lost margins and volumes.
The culprit: LockerGoga ransomware, which soon after played a hand in attacks against additional manufacturing and chemical companies including Columbus, Ohio-based Hexion, and Waterford, New York-based MPM Holdings Inc. (aka Momentive). It may also be what sidelined Swiss heavy equipment company Aebi Schmidt.
Phil Neray, VP of industrial cybersecurity at CyberX, says manufacturing companies are an obvious and viable target for ransomware campaigns because “downtime is measured in millions of dollars per day – so CEOs are typically eager to pay up.”
But the potential for damage transcends finances – a ransomware-caused shutdown can also have life-threatening consequences. “If you start shutting down something in a manufacturing facility and it’s not properly augmented or secured, you could possibly release chemicals into the environment and affect the workers on site,” says Tim Bandos, VP of cybersecurity at Digital Guardian. Making matters worse, manufacturing companies often have “archaic security controls in place” that are not easily scalable to adequately protect their large-scale operations, he continues.
From 2011-2015, Bandos served as cybersecurity director, incident response and threat intelligence, at a leading chemical manufacturing company. (He asked SC Media not to reveal its name.) Bandos himself bore witness to ransomware attacks at his former company, although nothing on the scale of Norsk Hydro.
One such attack exploited a hole in a firewall placed between the company’s primary networks and the process control network that runs its operational technology. This allowed the ransomware to sneak right through to PCN-related networks. “That’s when the kinetic effects start happening. Valves start turning, things start opening up that maybe shouldn’t be,” says Bandos. (Fortunately, the company had safeguards in place to prevent a major event leading to injury.)
The LockerGoga ransomware that has wreaked havoc on manufacturers has repeatedly evolved, in some versions acting more like a destructive wiper, threatening to not only encrypt data, but also overwrite disk drives, if victims don’t pay up. Other malware strains exhibiting these dual functionalities include MegaCortex and GermanWiper. This only raises the stakes further.
“Now you have to not only recover the data that you lost, but you have to recover the entire operating system along with that, and that’s a larger effort for a company to work with,” says Christopher Scott, global remediation lead at IBM Security’s X-Force Incident Response and Intelligence Services (IRIS) team.
IRIS has reported a 200 percent increase in destructive malware incidents over the first half of 2019, compared to the second half of 2018. Many involved ransomware attacks perpetrated against chemical and manufacturing companies. To prevent future attacks, Scott recommends that manufacturers adopt multifactor authentication, execute a defense-in-depth strategy, and practice segmentation of key systems.
“Everyone needs to learn from this… to be more proactive ahead of time, because having to spend the money up front after an attack like this can be much more devastating than deploying a security software that might cost you a half a million dollars or a million bucks to cover your entire enterprise,” says Bandos.
Health care
The landmark February 2016 Locky ransomware attack on Hollywood Presbyterian Medical Center wasn’t the first such incident against a medical facility, but it arguably represents a watershed moment for cyber professionals working for health care organizations (HCOs). The reported $3.6 million ransom demand demonstrated that attackers were beginning to recognize the immense wealth they could quickly accumulate by targeting vulnerable organizations dealing in highly sensitive and life-saving data. Since then, major ransomware campaigns against HCOs have continued relatively unabated.
“Hospitals may find themselves without the use of key systems. Without an EHR [electronic health record], patient care will certainly be affected. Some services can continue manually, albeit with delay, but in other situations care may not be possible at all,” says Jason Taule, CISO and VP of standards at HITRUST, the Health Information Trust Alliance. “A physician, for example, can still write a manual prescription, presuming he/she has enough knowledge of possible drug interactions, but radiology units are almost exclusively online and digital now, which means patients would have to be diverted elsewhere for care.”
Such setbacks can be devastating, says Clyde Hewitt, VP of security strategy at CynergisTek. However, “What is less publicized is… the adverse financial impacts to cash flow.”
Hewitt recalls one particular hospital that, despite recovering its network in just two weeks, was forced to manually input massive volumes of downtime forms into the EHR system so that claims could be generated and sent to the insurance companies. “Co-payments also could not be collected until the claims were processed. This resulted in a 60-day gap in receiving payments and put the organization into a $60 million deficit before they started to recover,” says Hewitt.
There’s also the potential of facing major penalties for violating HIPAA regulations, or even investigations by the FBI or the Joint Commission, which accredits more than 21,000 U.S. health care organizations. “But even if loss of accreditation is not a significant concern, HCOs should still be concerned about the higher cost of cyber liability insurance coverage following an incident,” says Taule.
And yet, “health care leadership has historically been slow to recognize the threat and therefore provide adequate resources to address the threat,” adds Hewitt.
The problem is, where to start? Hospitals make for great victims because they have “one the largest attack surfaces of any industry,” due to “all the interfaces needed to provide care,” Hewitt notes. EHR systems aside, there are also connected medical devices, patient wearables, physical environmental controls and more. “Many of these devices operate through the cloud and many are years or even decades old. This makes it very challenging to implement robust defenses,” Hewitt adds.
Furthermore, the health care landscape itself is composed of a diverse array of organizations, with varying levels of commitment to cybersecurity. It’s not just hospitals who are at risk – it’s small doctors’ offices, clinical labs, research facilities and others. Incidents like the May 2017 WannaCry offensive that cost the UK’s massive National Health System £92 million get worldwide attention, but for every NHS, there are many smaller HCOs getting hit, like Bridgewater, Massachusetts-based medical billing company Doctors’ Management Services (DMS) or the Dental Center of Northwest Ohio.
“The mission, regulations, geography, technical environment, management team, information involved, financial resources, culture and personnel vary substantially across each type of organization,” says Taule. “For all the progress HCOs have made in recent years, many still find themselves without a full-time, well-trained, experienced, executive-level person in charge of security” who must lobby management for cyber investments.
Attacker tactics are also constantly changing, and HCOs are generally not nimble enough to keep up. Hewitt says attackers are getting better at targeting specific organizations with spear phishing emails, while Taule says attacks are becoming easier to execute due to the advent of ransomware-as-a-service offerings like GandCrab.
Adversaries are also showing more willingness to exploit vulnerabilities in medical IoT devices, leveraging them to gain a foothold into organizations and later commit a damaging attack. “The next step in this evolution could be ransomware on IoT devices, particularly in health care IoT: pacemakers, insulin pumps, etc.,” said Bogdan Botezatu, director of threat research and reporting at Bitdefender.
Consequently, Taule recommends that HCOs incorporate firmware into their control frameworks and their vulnerability scanning and patching efforts.
Government & municipalities
Last July, more than 225 U.S. mayors stood their ground against ransomware attacks, signing a resolution stating they would reject any extortion demand. The gesture came two months after a Robbinhood ransomware attack shut down the city of Baltimore’s servers, resulting in estimated response and recovery costs of $18 million – well above the original $80,000 ransom demand.
According to the United States Conference of Mayors’ resolution, “at least 170 county, city or state government systems have experienced a ransomware attack since 2013.” Victims have been as large as the city of Atlanta and the Port of San Diego, both struck by SamSam ransomware in 2018. But smaller, provincial targets have been an even more frequent target, including La Porte County, Indiana and the Salisbury, Maryland Police Department just this past year.
“Municipalities make excellent targets for several reasons,” says Sherrod DeGrippo, senior director of threat research and detection at Proofpoint. “They typically have underfunded information security protections, despite running what some would consider critical infrastructure.”
“Due to small IT footprints, they often lack robust security controls and disaster recovery solutions that would allow them to prevent these types of attacks and/or to recover quickly,” DeGrippo continues. “Many municipalities also manage a huge number of interconnections into their network. These interconnections add complexity to the security and management of their networks, allowing simple misconfigurations to be exploited by threat actors.”
Compounding these challenges are a proliferation of third-party vendors, contractors and suppliers that work with government agencies – each with their own set of vulnerabilities. “Threat actors can potentially use them as a backdoor to reach the systems of a local city or state agency,” DeGrippo remarks. For that reason, “We recommend a thorough vetting of the security and access controls of all vendors before connecting them to a network.”
When ransomware successfully infects a government entity, it essentially disrupts day-to-day business operations that allow society to function normally and cities to stay funded. For example, the Baltimore attack reportedly waylaid the collection of water bills, property taxes and parking tickets, along with the distribution of city permits.
This is troublesome enough. However, there is an even greater concern that a future ransomware attack could impact critical infrastructure or emergency services. “If the communication systems utilized by first responders were taken offline, it could cripple their ability to respond to emergency situations – especially considering many are migrating toward Voice over Internet Protocol phone networks, which are more susceptible to a ransomware attack,” warns Michael F.D. Anaya, head of global cyber investigations and government relations at DEVCON, and a former supervisory special agent for the FBI in Atlanta.
One might wonder if the advent of smart cities will only further increase the threat surface. “IoT devices have typically been built for very specific functions without a significant focus on built-in security features. As such, they tend to be vulnerable to attack, provide easy targets for lateral movement within environments, and are sufficiently numerous and distributed to be difficult to secure through means traditionally applied to laptops and other devices,” says DeGrippo.
On the plus side, however, “A key advantage is that any city looking to implement smart technologies will have to undergo a digital transformation that will retire vulnerable, antiqued systems. These new systems will be a fresh start, offering up-to-date security measures that will make them harder to compromise.”
To counter the threat, DeGrippo recommends that municipalities “develop threat profiles that highlight areas of risk, and implement a proactive, people-centric security approach” that includes security awareness training, which even cash-strapped localities should be able to afford.
Schools
Another realm of the public sector that’s also under attack is local educational districts – so much so that in July 2019 New Orleans Governor John Bel Edwards declared a state of emergency, which made his jurisdiction’s local districts eligible for government funding to better protect themselves.
“I applaud the Governor of Louisiana for taking decisive action to help school districts respond to the cybersecurity threats they are facing,” says Douglas Levin, president of EdTech Strategies, LLC, which operates the K-12 Cybersecurity Resource Center. “Most districts have not devoted the necessary resources to managing the cybersecurity risks they are facing today, much less tomorrow. Outside assistance and resources are critical to helping them to respond and recover.”
With that said, however, “the state’s response is akin to giving an aspirin to someone who just broke their arm,” Levin continues. “There are more fundamental issues facing the state of school cybersecurity – in Louisiana and beyond – and it will require a comprehensive and sustained response over time. It will include the passage of education sector-specific cybersecurity compliance policies, more resources for school districts to deploy and monitor cybersecurity controls, and more transparency and information sharing.”
Examples this year of ransomware attacks on school districts include prominent incidents involving school districts in Syracuse, N.Y.; Bridgeport, Connecticut; and likely Houston County Schools in Alabama (the district did not officially confirm ransomware in the last case).
Levin says districts often fall victim to ransomware attacks because academic environments “tend to have large numbers of unsophisticated users, be more trusting of technology, and [be] more open to deploying relatively immature online services and applications. Yet, school district IT infrastructure tends to be quite varied, older and less well-supported than in other sectors.”
And although many school districts are on tight budgets, they have been known on occasion to pay up. “I have heard anecdotally that more recent ransomware payments have been made by school districts at a much higher cost, reaching seven figures,” Levin continues. Clearly, school districts must continue to get educated fast on the ABCs of ransomware. As must government bodies, HCOs and manufacturers.



