Threat researchers at HP Wolf Security have discovered a new social engineering trick disguised as an upgrade for Windows 11. When the user is tricked into downloading the fake installer, attackers move to distribute information-stealing malware known as RedLine Stealer. The threat is described in a recent blog post from HP malware analyst Patrick Schläpfer.
Schläpfer wrote about how attackers copied the design for Microsoft’s official Windows 11 website to provide an authentic appearance. The difference, however, is that when the download button is pressed, a suspicious zip archive called Windows11InstallationAssistant.zip is installed on the device:
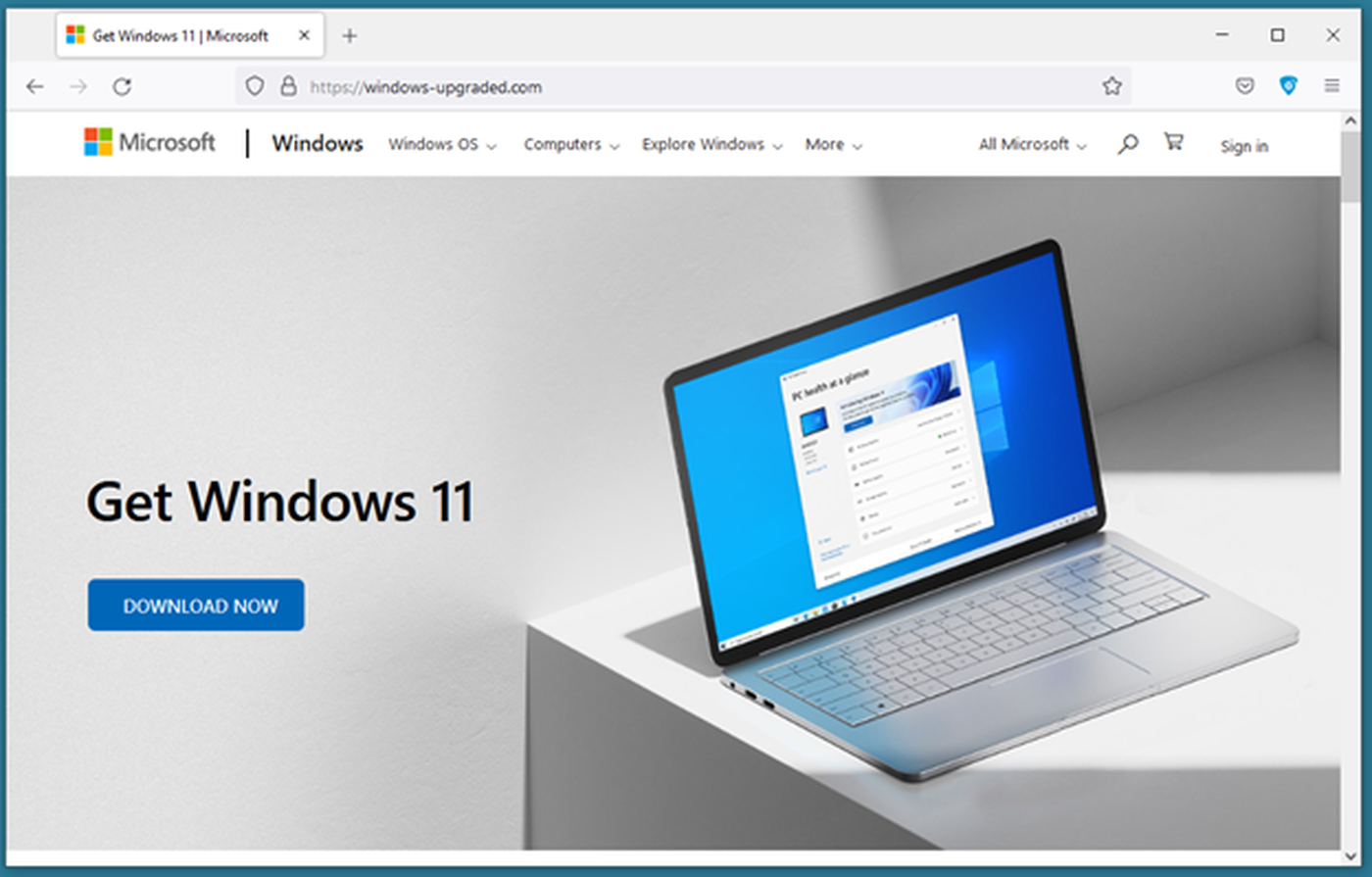
“After decompressing the archive, we get a folder with a total size of 753 MB. The executable Windows11InstallationAssistant.exe was the largest file at 751 MB,” Schläpfer wrote. “Since the compressed size of the zip file was only 1.5 MB, this means it has an impressive compression ratio of 99.8%. This is far larger than the average zip compression ratio for executables of 47%. To achieve such a high compression ratio, the executable likely contains padding that is extremely compressible.”
The blog post includes a collection of screen grabs showing code analysis tracing the process by which the infection takes hold.
The tactics, techniques and procedures (TTPs) in this RedLine Stealer campaign are similar to one HP Wolf analyzed in December, when a malicious actor registered discrodappp[.]com and used it to deliver RedLine Stealer disguised as an installer for the popular Discord messaging app:
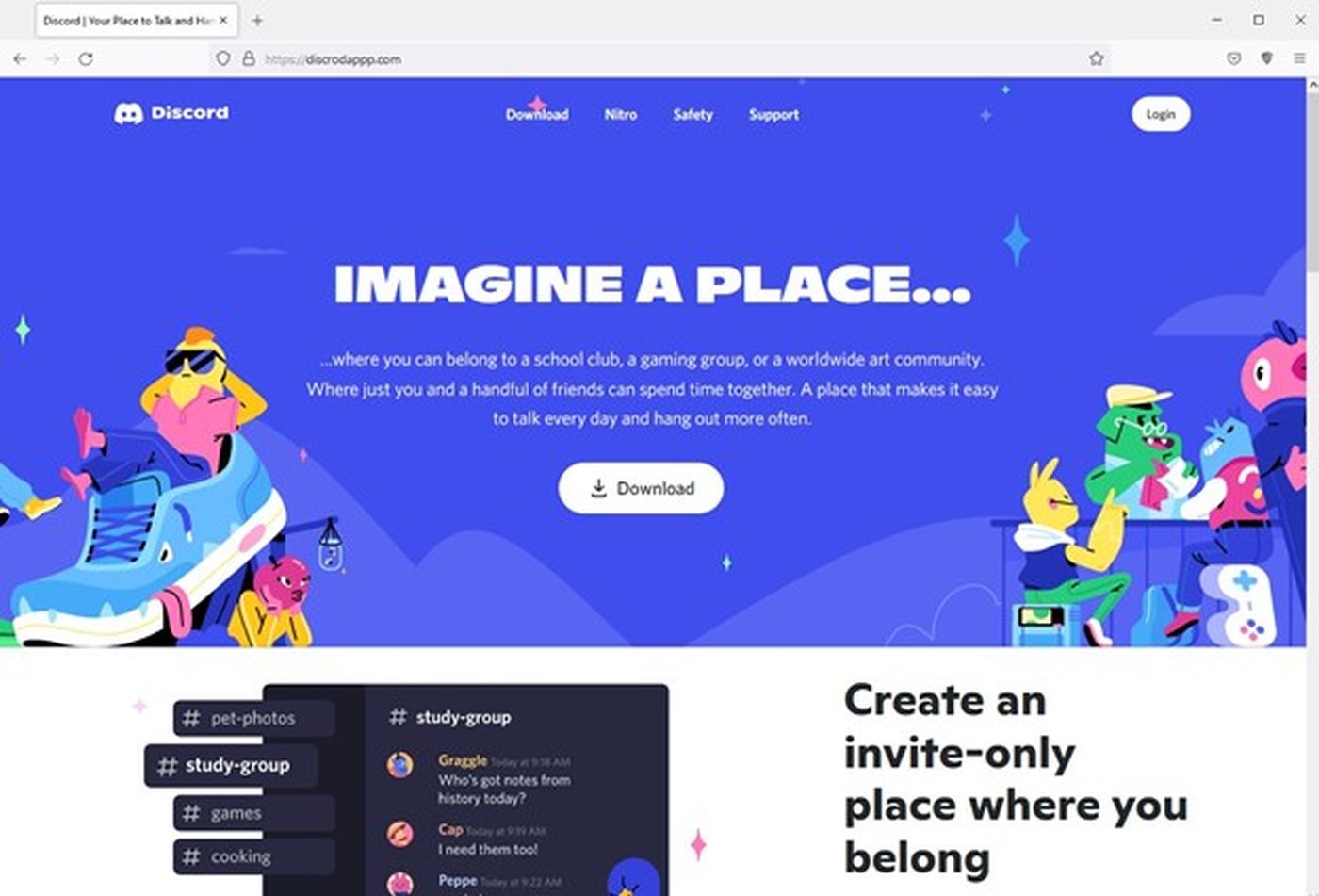
“In both campaigns, the threat actor used fake websites mimicking popular software to trick users into installing their malware, registered the domains using the same domain registrar, used the same DNS servers, and delivered the same family of malware,” Schläpfer wrote.
This latest campaign should serve as a warning about how attackers quickly exploit important events to create effective lures – in this case, the arrival of a Windows upgrade.
Since such campaigns often rely on users downloading software from the web as the initial attack vector, organizations must take care to educate employees and other users on the importance of only downloading software from trustworthy sources.



