SE Labs tested VMware NSX Network Detection and Response against a range of advanced persistent threats designed to compromise systems and penetrate target networks in the same way as criminals and other attackers breach systems and networks.
Full chains of attack were used, meaning that testers behaved as real attackers, probing targets using a variety of tools, techniques, and vectors before attempting to gain lower-level and more powerful access. Finally, the testers/attackers attempted to complete their missions, which might include stealing information, damaging systems, and connecting to other systems on the network.
The following is the last of a three-part preview of SE Labs’ report on the exercise, which can be downloaded here.
In this installment, CyberRisk Alliance looks at what the testing revealed about typical attack stages.
Attackers start from a certain point and don’t stop until they have either achieved their goal or have reached the end of their resources (which could be a deadline or the limit of their abilities).
This means, in a test, the tester needs to begin the attack from a realistic first position, such as sending a phishing email or setting up an infected website and moving through many of the likely steps leading to stealing data or causing some other form of damage to the network.
If the test starts too far into the attack chain, such as executing malware on an endpoint, then many products will be denied opportunities to use the full extent of their protection and detection abilities.
If the test concludes before any useful’ damage or theft has been achieved, then similarly the product may be denied a chance to demonstrate its abilities in behavioral detection and so on.
Attack stages
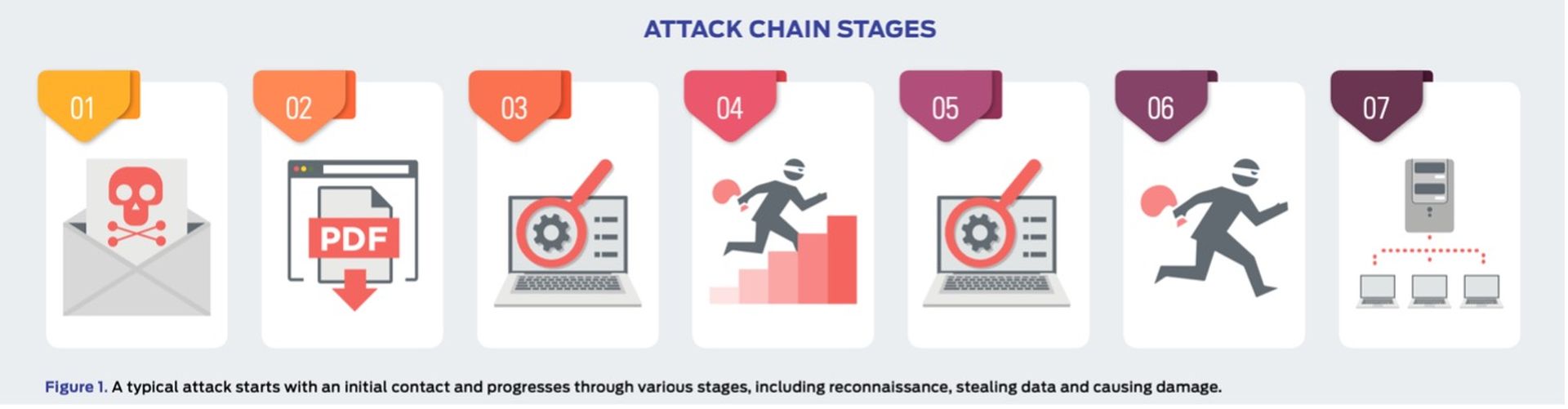
The illustration below (Figure 1) shows the stages of an attack. SE Labs measured how a product responds to the first stages of the attack with a detection and/ or protection rating. Sometimes, products allow threats to run but detect them. Other times they might allow the threat to run briefly before neutralizing it. Ideally, they detect and block the threat before it has a chance to run. Products may delete threats or automatically contains them in a ‘quarantine’ or other safe holding mechanism for later analysis.
When the initial attack phase succeeded, SE Labs then measured post-exploitation stages, which are represented by steps two through to seven below.
In figure 1. you can see a typical attack running from start to end, through various hacking activities. This can be classified as a fully successful breach.
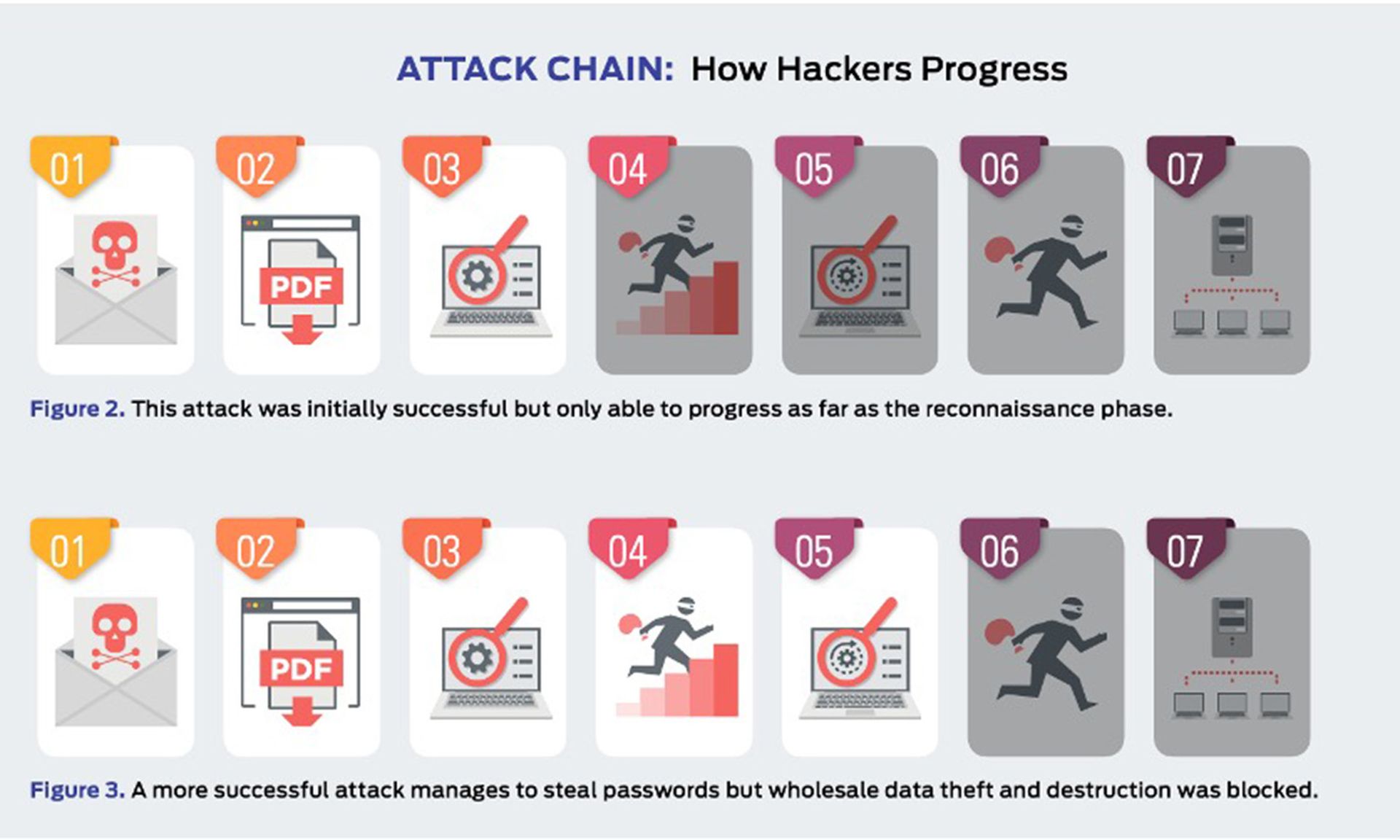
In figure 2. a product or service has interfered with the attack, allowing it to succeed only as far as stage 3, after which it was detected and neutralized. The attacker was unable to progress through stages 4 and onwards.
It is possible for an attack to run in a different order with, for example, the attacker attempting to connect to other systems without needing to escalate privileges. However, it is common for password theft (see step 5) to occur before using stolen credentials to move further through the network.
It is also possible that attackers will not cause noticeable damage during an attack. It may be that their goal is persistent presence on the systems to monitor for activities, slowly steal information and other more subtle missions.
In figure 3. the attacker has managed to progress as far as stage five. This means that the system has been seriously compromised. The attacker has a high level of access and has stolen passwords.
However, attempts to exfiltrate data from the target were blocked, as were attempts to damage the system.
NSX NDR performance
The test exposed VMware NSX Network Detection and Response to a diverse set of exploits, file-less and malware attacks and reconnaissance ‘discovery’ techniques.
"The testers behaved as attackers, pivoting between systems (and generating lateral movement traffic), attempting to use credentials, exfiltrating data and creating command and control data flows,” the report authors wrote.
VMware NSX Network Detection and Response detected all the threats during testing.
Also from the report’s conclusion:
“An attack is made up of multiple stages and we record when a product detects malicious activity, including the initial ‘delivery’ stage of an attack, when a connection is first made and malicious code is sent to the target. We also watch out for code execution; behavior by the attacker after their attempts to gain lower-level access (privilege escalation); and their movement across the network after the first stages of the attack (lateral movement).
“The results are strong and not one attack stage went undetected. Sometimes products are overly aggressive and detect everything, including threats and legitimate objects. In this test VMware NSX Network Detection and Response generated no such false positive results, which is as hoped.”
The final verdict: VMware NSX Network Detection and Response wins a AAA award for its excellent performance.
To learn more about the testing, check out this VMware blog post.




