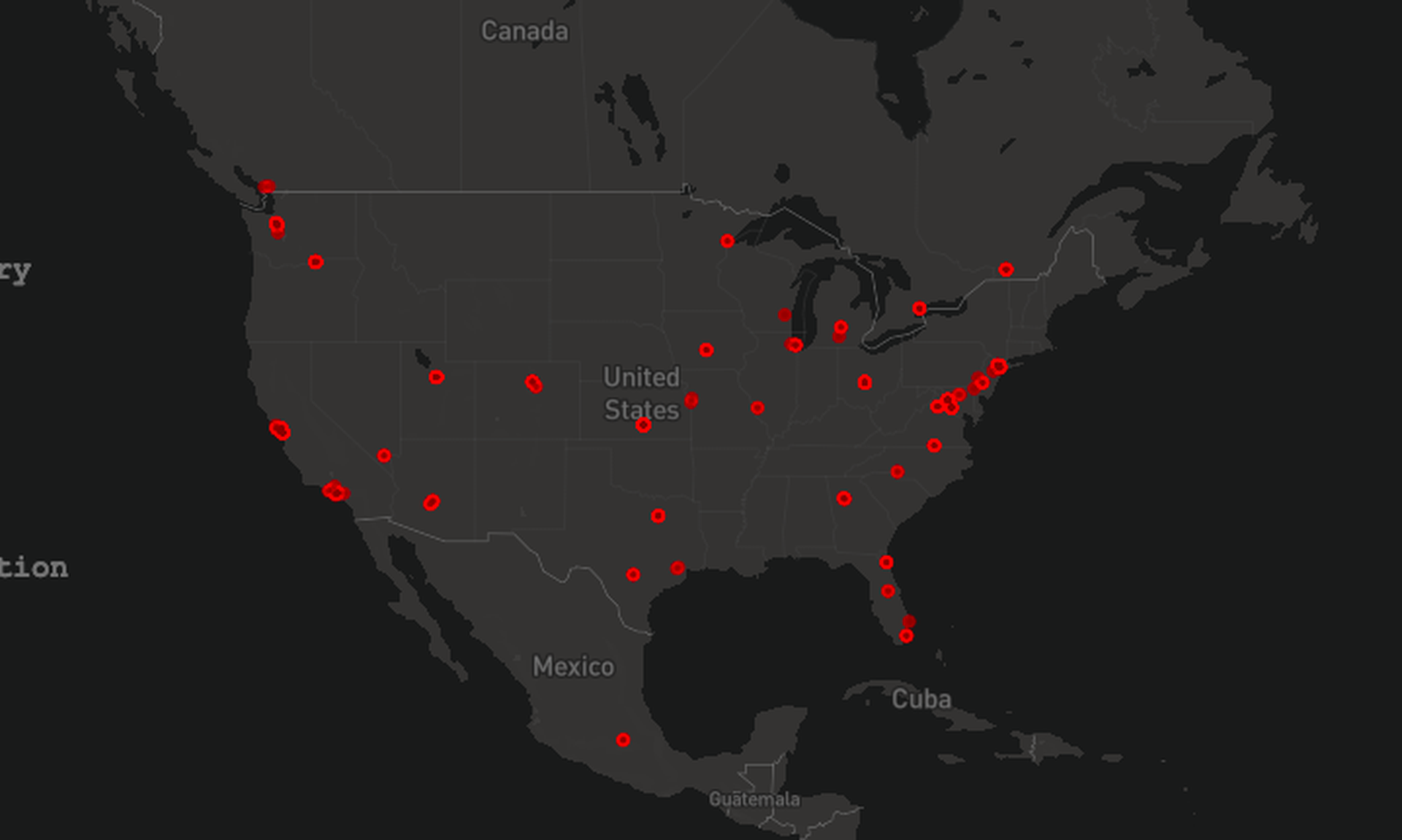
Human-powered gangs remain the most dangerous and insidious threat on the ransomware front, but a newly introduced map feature serves as a reminder that there is still a wide array of automated campaigns designed to serve up ransomware as well.
Updated on a daily basis, the map, from Comparitech, visualizes attempted ransomware attacks around the world over the past three weeks, showing the geolocations of publicly accessible, compromised IPs running databases that have been served a ransomware file. The data isn’t particularly actionable, but it does send a strong message about the global scope of the ransomware problem and certain overall trends.
For instance, over four months of aggregated data, the average bitcoin demanded from these automated attacks was 0.02, or $8,025.18 at the rate of exchange as of June 14, and the average deadline was 48 hours.
“The data is sourced through random port scanning and automated investigation of open ports using API-streamed data coming from search engines such as Shodan, BinaryEdge, Censys and Zoomeye,” said head of Comparitech’s cybersecurity research team Bob Diachenko. “We look at the database banners that contain the data we aggregate: IP, geographic location, type of database and port. When we see an index or collection named ‘Readme’ and its permutations, we process its content to extract the average BTC demanded and the most frequently used email and wallet address.”
For example, Comparitech found one Read_me note in an infected Elasticsearch cluster that warned the recipient to pay 0.0175 bitcoins within 48 hours to recover encrypted data. “After 48 hours expiration we will leaked and exposed [sic] all your data,” the note stated. “In case of refusal to pay, we will contact the General Data Protection Regulation, GDPR and notify them that you store user data in an open [forum] and is no[t] safe.”
It is not clear what percentage of the total automated ransomware attacks around the world is represented by this map – nor is it specified if any of the openly accessible databases were intentionally left open as a honeypot.
“Keeping in mind that this scan only covers unprotected databases connected to the public internet as the attack vector, it is a useful visualization,” said Dirk Schrader, global vice president, security research at New Net Technologies. “Displaying the spread over the globe [and] the number of daily attacks makes it an impressive map for the uninformed and helps to raise awareness.”
Still, “information security professionals know that there are more attack vectors for ransomware to have an eye on,” Schrader continued. “A well-prepared organization will use available sources like Shodan or Censys, plus [their] own scanning capabilities and device hardening and change control [practices] to reduce its attack surface.”
Other commentators, including Joseph Carson, chief security scientist and advisory CISO at ThycoticCentrify, didn’t see much practical use for the map, however.
“I did not find it very… actionable, which is what I really would like to see; however it was interesting to see where the victims of ransomware attacks are located,” said Carson. “While it is a great visualization, it [does] not help convince organizations executives to invest in security to prevent them from becoming the next victim.”
Nevertheless, Diachenko said Comparitech is offering the tool because “we wanted to highlight the importance of following the basic cyber hygiene rules and provide an even clearer picture of ransomware incidents across the globe. In most cases companies ignore them and think that ransomware gangs operate mostly as state-level actors and target big and critical infrastructure objects. The reality is that there is a huge variety of ransomware actors that simply scan and hit the exposed databases with a ransom note hoping to get something.”
“There is no immediate action that can be taken after looking at the map," he continued. "However, its main purpose is to trigger the intention to check if your company's security perimeter is safe now and do that ASAP."