A new online POS skimmer used by one of the Magecart groups has been spotted injecting an iframe into retailer websites that asks for payment card information.
Malwarebytes came across the new technique being used on a Magento powered e-commerce platform. Unlike other skimming methods, which search for the active payment form on the page and replace it with one prepped for skimming, the new version simply inserts an iframe onto a shopping cart check out page that asks for the visitor’s name, credit card number, CVV and expiration date, said Malwarebytes Head of Threat Intelligence Jerome Segura.
The malware is injected into all the PHP pages on the targeted site, but the ifram is only activated when the shopper visits the shopping cart check out page.
“If the right conditions are met, an external piece of JavaScript is loaded from thatispersonal[.]com, a domain registered with REGISTRAR OF DOMAIN NAMES REG.RU LLC and hosted in Russia,” Segura said.
The dead giveaway that something is amiss is the shopper is being asked for this info, and then told they will be shifted to a third-party site where the transaction will be completed.
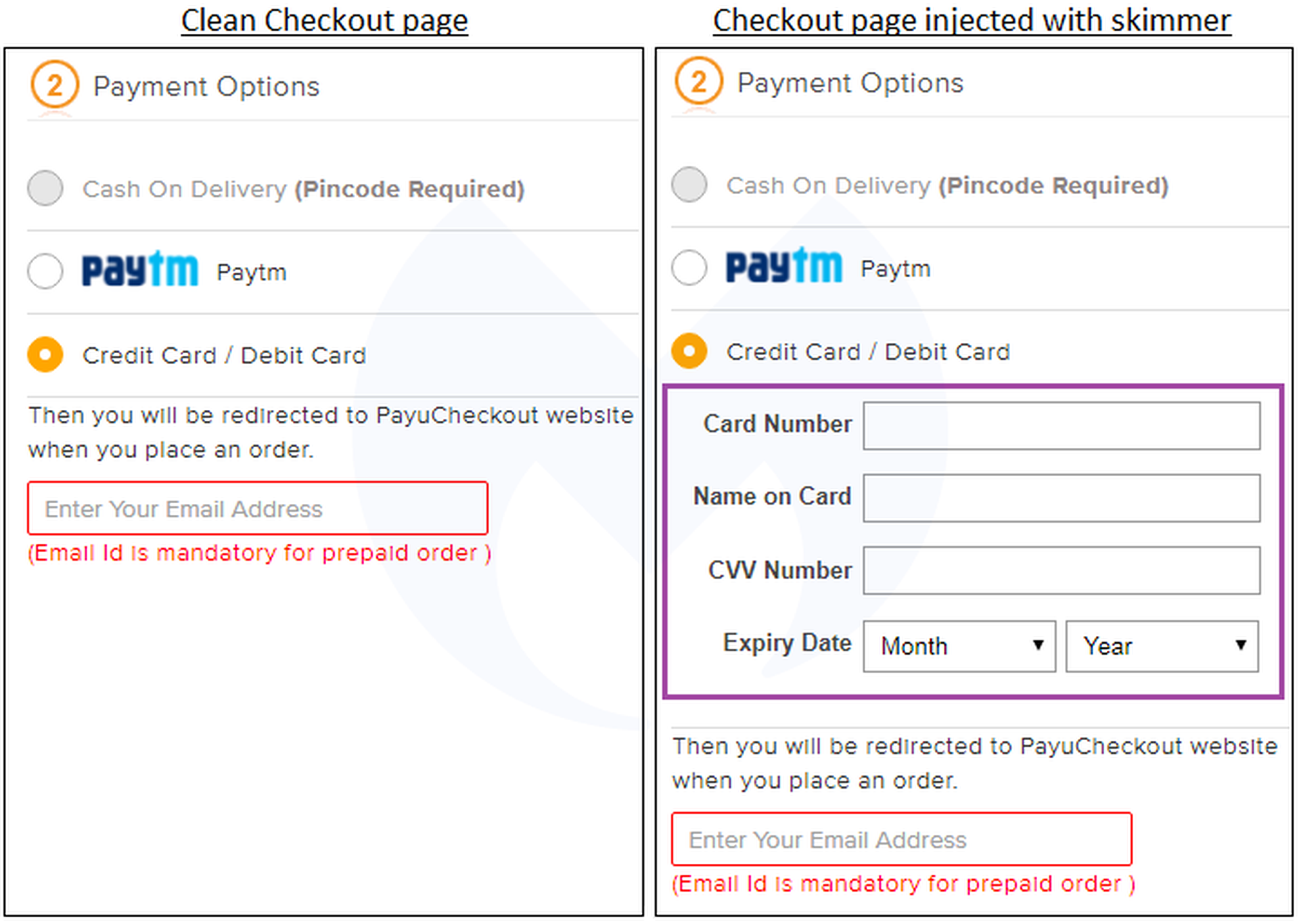
“By itself, this may not be out of the ordinary since online merchants do use such forms (including iframes) as part of their checkout pages,” Segura said, adding, “Why would a merchant want to get their customers to type in their credit card again and hurt their conversion rate?”
The malware does validate the credit card data before it is exfiltrated and then the customer is actually taken to the legitimate payment page after their information is stolen.



