Today, identity projects are more critical than ever as digital channels continue to evolve and become the primary point of business and brand interactions. The entire user journey from ID proofing, compliance and fraud detection to authentication and authorization are all interconnected. This is pushing businesses to devote significant resources to the integration and orchestration of various solutions to ensure the user experience is seamless, personalized and secure.
User experience can mean the difference between won and lost revenue. It's the reason why companies like Google and Amazon don't have a help desk. These leaders have always found a way to manage identities while providing a simple and elegant digital experience. And, they do it by secure frictionless identity experiences.
However, identity is a complex undertaking that's not always easy to, well, orchestrate. Identity orchestration is gaining attention because it helps solve the common integration and workflow headaches that enterprises typically encounter with speed and agility. When orchestration is done right, organizations can provide the same level of user experiences as Google or Amazon — without requiring the same level of resources as those homegrown solutions.
The definition of identity orchestration
Identity orchestration is a flexible and adaptive integration framework that allows enterprises to easily design and maintain dynamic user journeys for identity and access management across the entire identity lifecycle. This means designing automated workflows for different identity use cases like fraud detection, identity proofing, authentication, authorization and more. Orchestration offers a faster and more agile approach of implementing change versus the traditional hard-coded solutions.
The value of orchestration is the coverage it provides for all your identity services, giving you the ability to visualize and map identity services across the user journey. Also, integrations don't require heavy development work and instead can be accomplished in no-code/low-code manner. By mapping multiple identity technologies together and making integrations easier and faster, orchestration enables organizations to look at the user journey holistically through the lens of a unified identity fabric.
"By 2023, 75% of organizations will be using a single vendor with strong identity orchestration capabilities and connections to many other third parties for identity proofing and affirmation, which is an increase from fewer than 15% today."
Gartner Market Guide for Identity Proofing and Affirmation
Why is identity orchestration important?
Identity is all about user experience and security, helping you determine whether you deliver personalized experiences to your users all while keeping their data secure. Typically, what's beneficial to your customers and employees is generally beneficial to your enterprise, too.
But, let's back up a bit.
What are some of the biggest market challenges that businesses face that would actually motivate an enterprise to invest in identity orchestration in the first place?
To start, securing digital identities is a greater challenge than ever before due to problems with legacy identity and authentication point solutions that were not designed for current use cases. Most current identity and authentication services are a complicated tangle of poorly integrated software and API services that impedes agility, costs a lot to operate and makes adaptive identity experiences an elusive goal. Why wouldn't companies want a way to make this easier?
Global Expansion: Companies with global reach face regional challenges when it comes to identity. A siloed approach is an expensive and complicated undertaking, that can lead to missed opportunities. Identity orchestration layer makes it easier to manage identities across the world and do tasks like A/B testing and optimize workflows across different geographies.
Regulatory Pressure: Every new year brings a new set of regulations, challenges and changes. This often requires changes to identity policies like fraud detection, ID proofing and authentication. Orchestration provides the agility to adapt to these regulations with speed and precision.
Data Normalization: Data often comes back in a variety of formats, with varied response times from vendors. Occasionally, the data returned may only provide partial understanding, which can lead to allowing a possible "reject" to become a "accept," causing a break in security. Orchestration enables organizations to create and enforce granular policies to account for these gaps.
Vendor Management: Managing and supporting multiple vendors is a challenge for companies and as new vendors come into the market, the work required to do things like research, connect, deploy and roll out new API integrations is time-consuming and expensive. Often, many companies face issues with vendor lock-in and challenges in switching to another vendor result in poor customer experience and increased churn rate.
Compliance & Fraud: Many organizations have to have strong controls around KYC/KYB, fraud and AML and stay up to date with regulations and compliance requirements. New data vendors are constantly emerging in the market and orchestration makes it easier to assess, engage, integrate and test new vendors.
Account Recovery: Cumbersome processes around account recovery, password resets, replacing trusted devices and managing multiple MFA methods can frustrate your users and cause lost revenue. Organizations need solutions that involve self-service, intelligence and automation. Orchestration enables you to easily embrace these initiatives and stay ahead of the curve.
What does an orchestration platform bring together?
So, how can organizations without immense resources embrace orchestration? How can they provide a seamless customer experience across all channels and touchpoints?
First and foremost, companies accept a unified approach to managing identities and authentication by breaking down existing silos. An orchestration platform brings together several aspects of the employee and customer journey in order to create a consistent and personalized experience. Breaking this down into a few different categories—registration & login, identity verification and intelligence — can help organizations get started.
Registration & Login
Identity orchestration helps companies find the best way to enable a frictionless registration and login experience for users while keeping security top of mind. Here's how embracing orchestration can help:
- Easily integrate identity proofing solutions, like providing proof of an actual document alongside a selfie.
- Utilize various options to verify users easily such as email, phone number, physical address without introducing friction.
- Automate IP address checks and flagging of other potentially fraudulent activity.
- Utilize auto-fill forms to make the registration process easier and secure by leveraging third-party identity providers like banks.
- Leverage Bring Your Own Identity (BYOI) methods like Apple and Google IDs who have already done most of the vetting ahead of time.
Identity Verification
There are many attributes that are analyzed from third-party sources and service providers to verify an identity. The level of a risk associated with the transaction or action must also be taken into account. In some cases, it is basic document-based identity verification, while in other cases, more due diligence is required.
Financial services, payments and other heavy regulated environments require robust solutions that can perform a variety of actions. Orchestration can help implement technologies that verify users based on credit checks, income verification, bank account information, social security and more.
On-Going Authentication
Data breaches and account takeovers (ATO) have become more prevalent, increasing the need for more robust account security. It's critical to ensure your accounts are secure and necessary to prevent fraudsters from creating new accounts resulting in cybercrime.
This can be done through:
- Biometric-based approaches to user authentication: This provides an extra layer of security for individuals who've already been onboarded, building on verification methods like identity proofing. For example, when a high-risk transaction is initiated (e.g., a wire transfer or a password reset), the user only needs to take a selfie/go through a live check.
- Behavior-based authentication: Organizations can flag potential unauthorized access or transactions by understanding user behavior around various factors. That can be logging in from an unknown location, making an unusually high purchase, or in an employee use case, even typing or moving your mouse differently than usual.
How does an identity orchestration platform work?
Identity orchestration approaches share the same end goal, but each organization has its own criteria and motivations. A common goal is speed and agility, making time to market and testing easier than ever before. Now that you know what some of the features are that are brought together in identity orchestration, how does the actual platform work?
- Integrations: An orchestration platform is only as strong as its ability to integrate all the required applications and data sources within an enterprise. That empowers the business to create the optimal user experience without any barriers.
- Flows: The next step is to set up the workflows across all the various integrated applications and data sources. There is often complex business logic associated between these workflows and the orchestration platform should give you a good bird's eye view of everything that is going on.
- Testing & Deploying: The main benefit of an orchestration platform is the ability to quickly run tests and push them live. This is due to the no-code/low-code manner in which these platforms are constructed which allow non-developers a seat at the table. An enterprise will know they have the right orchestration platform when their time to market is greatly reduced for a new app, feature, or change.
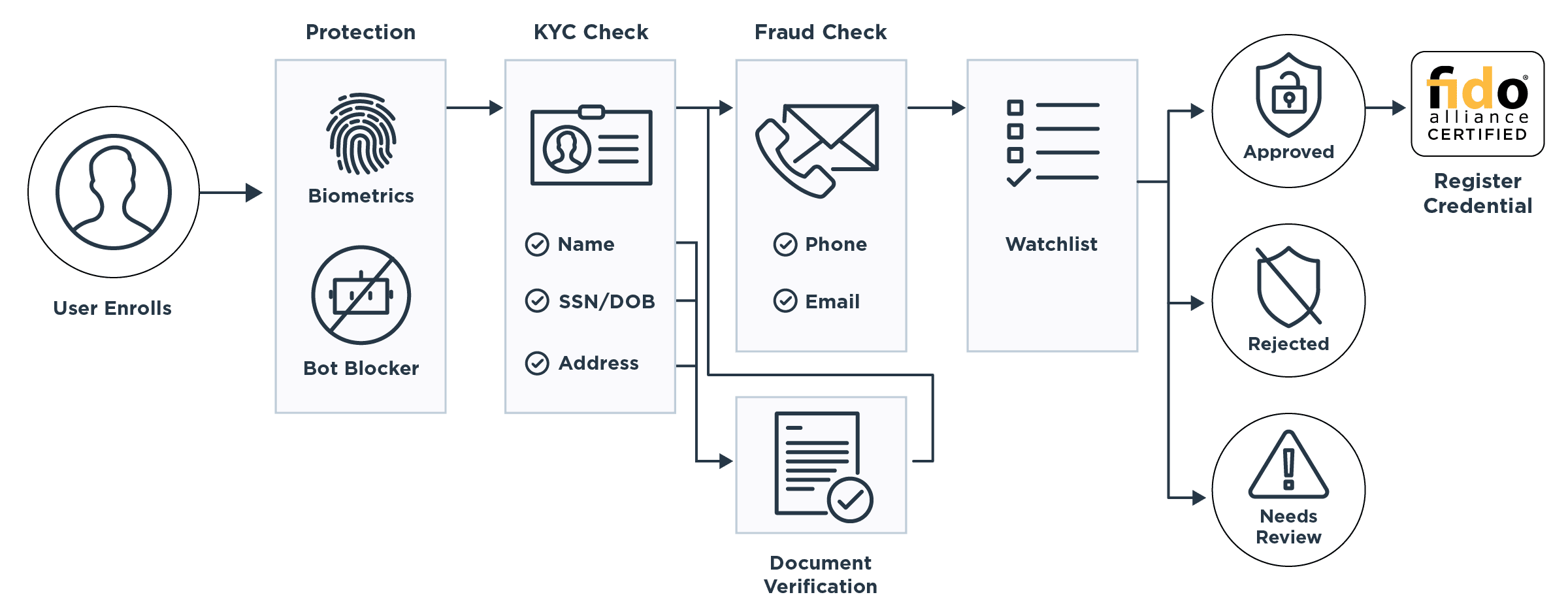
Here's an example of an orchestrated workflow that a user might experience:
What to consider with identity orchestration
Identity orchestration will change how your company manages identities, for the better. But, let’s be honest — it’s not so easy to make it happen.
Challenges with Implementing Identity Orchestration
Some of the problems with implementing identity orchestration include:
- Hidden Costs / Delayed Implementation: The market for identity orchestration is still young. Early adopters have seen issues with coverage for their existing apps, data and user bases. And for orchestration to really work, it does need to provide full coverage
- Siloed Use Cases: Some orchestration platforms are built only for the customer or employee use case. Most organizations need a single orchestration platform to cover employees, customers and other identities such as other human identities (such as partners, contracts), machine identities, APIs and more.
- Coding Required: A main selling point of orchestration is speed and agility. Low-code or better yet, no-code, makes it easy for the business to be a part of the identity conversation. This eliminates the need for constant back and forth with IT and the ensuing delays from development and coding.
The First-Generation of Identity Orchestration
To date, only a few large digital businesses and banks view identity as a strategic core to their business. And, they have invested millions of dollars in building their own in-house orchestration tools, leveraging many point vendors' limited workflow and hub capabilities. This approach worked well as it solved the problem (maybe temporarily). However, it slows down time-to-market and quickly leverages more modern identity proofing, authentication and fraud detections capabilities.
Building an orchestration platform in-house often requires alignment between product, IAM, risk/security and development team. This then needs to be manually integrated to third party providers and continuously maintain them, which often results in forced vendor lock-ins. This developer-centric approach is not only unsustainable, but it also limits the agility to innovate, improve ID proofing coverage and respond to evolving fraud techniques.
This is why you need an identity and access management expert to help. As businesses expand globally and become digital, investing in a future-proof identity strategy is critical. This will help get customer identity management to drive top-line growth and reduce operating, fraud and licensing costs.
Don't wait to orchestrate
Today's consumers have to navigate a dizzying array of identity touchpoints throughout their day. Often out of frustration they abandon carts, don't register for new services and/or choose a competitor with better user experience. Make no mistake about it, your digital experience is often how they perceive your brand quality and reputation.
User experience is paramount but security goes hand in hand with it. Cyberattacks and fraud are on the rise and organizations need the ability to provide advanced authentication and authorization controls or risk losing their trust and reputation. Identity orchestration enables quick time to market for new technologies such as fraud detection, ID proofing and passwordless authentication that not only keep users secure but provide frictionless experiences as well.
While different companies may have different reasons for considering identity orchestration, in the end, identity orchestration will help you to not only address these challenges, but continuously optimize cost, performance and experience — all while reducing your security risk and making user experiences more seamless.
Want to learn more about Identity Orchestration and Ping's no-code platform? Please visit our orchestration page.