Two years ago, the Cybersecurity and Infrastructure Security Agency sought to centralize bug reporting across the federal government, setting up a new vulnerability disclosure policy platform that would allow outside security researchers to safely and legally examine certain federal systems and websites and report them to the government.
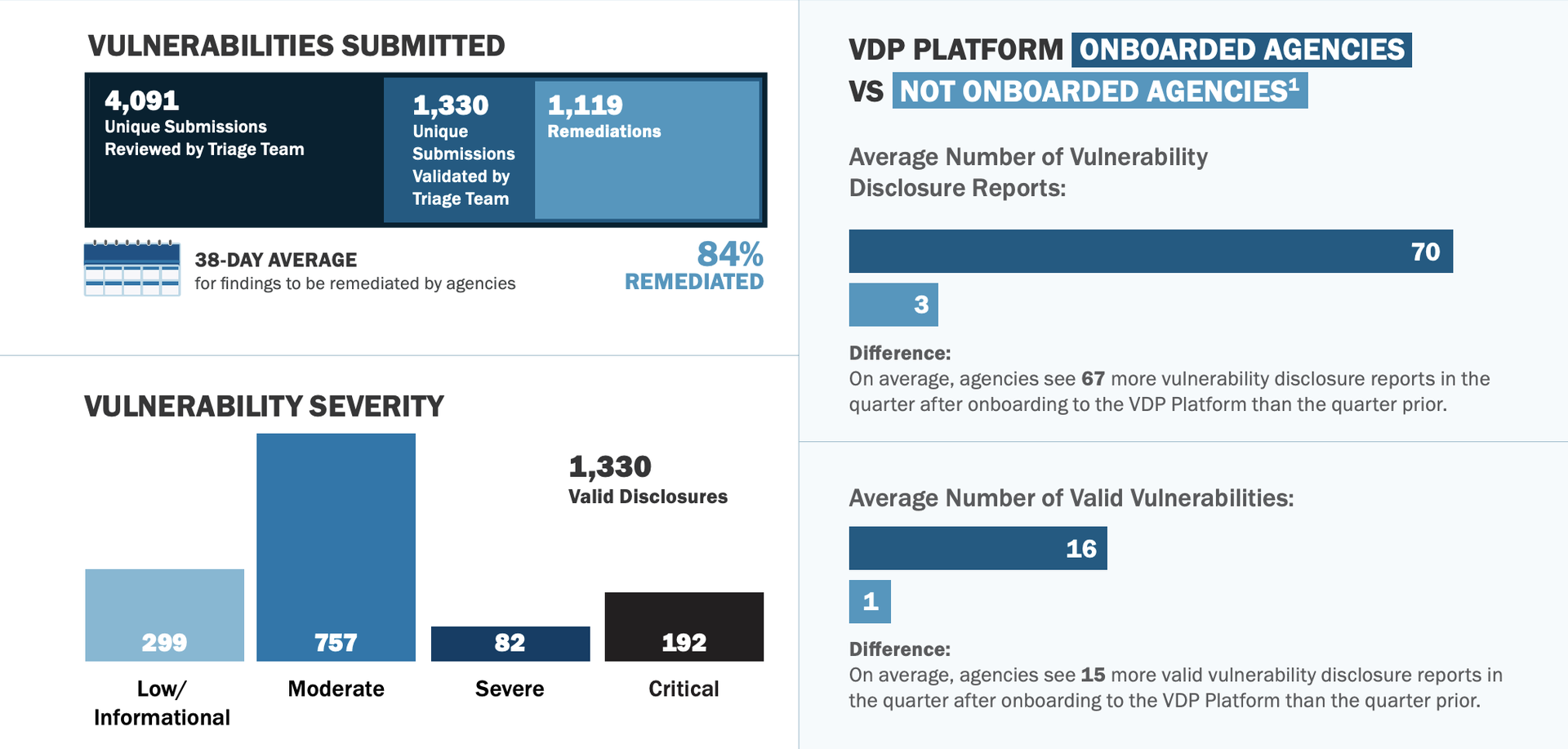
Now the cyber defense agency is advertising some of the fruits from that program, announcing in a new report Friday that the VDP program has onboarded 40 different agency programs and received over 4,091 unique submissions and 1,330 “valid” vulnerability reports from the public through the end of last year. Of those reported, 192 were classified as “critical,” 92 as “severe,” 757 as “moderate” and 299 as “low.”
The agency says 1,119, or approximately 85%, of those bugs have been remediated thus far, and it took agencies, on average, 38 days to fix or address flaws reported through the program. That’s roughly in line with the timeframe given in a previous CISA order for agencies to address “critical” vulnerabilities within 30 calendar days of reporting.
“Since launch, the VDP Platform has seen tremendous growth in the number of participating agencies and vulnerabilities disclosed,” the report stated. “As more agencies participate on the VDP Platform, CISA’s insight into vulnerabilities across the FCEB becomes more comprehensive, leading to more-effective network protection and prioritization of remediation and resources."
The most frequent types of flaws found through the program were for cross-site scripting, server misconfigurations, data exposure caused by weak encryption or unsecured web applications and server-side injections.
When announcing the program in 2021, CISA Executive Assistant Director Eric Goldstein estimated that the effort could save the government more than $10 million. The report does not provide any metrics, but claims the VDP offers agencies “significant time and cost savings” around vulnerability mitigation.
In response to questions from SC Media, CISA sent a statement from Jim Sheire, its chief of cybersecurity shared services, that did not provide specific or updated figures around cost savings, only saying that CISA's verification and triaging service saves "significant agency time and resources" and prevents the need for individual agencies to set up their own vulnerability disclosure program "which could easily cost each agency hundreds of thousands of dollars per year to separately design, procure, deploy, and maintain themselves.”
Sheire also said that the remaining 15% of vulnerabilities not listed as remediated were "addressed by compensating controls while remediation proceeds."
The VDP also has the ability to spin off unique bug bounty programs — events that bring in security researchers to hack systems for monetary rewards — for specific agencies and incidents. Two such examples provided in the report were “Hack DHS,” a three-part bug bounty event focused on the Department of Homeland Security that took place in 2022, and a specific bug bounty event focused on discovering vulnerable instances of the Log4J vulnerability that was spun out within 36 hours of the vulnerability’s disclosure.
While CISA doesn’t provide specific figures for the Log4J event, it says that Hack DHS invited a total of 726 outside security researchers, found 235 vulnerabilities (including 40 deemed critical) across 13 different DHS systems and awarded $329,900 in awards.
CISA is keen to show off the benefits of using the program, saying each new submission gives them greater awareness of security shortfalls within federal civilian executive branch agencies and has led to the detection of known exploited vulnerabilities “on federal systems that were not identified by existing scanning tools.”
They’re also eager to demonstrate that the government now welcomes outside security researchers poking around in (some) federal systems. That sentiment is part of a years-long evolution from the Department of Justice and other government bodies who once viewed such outside research as unwelcome (and possibly illegal) but now sees the private sector as a critical partner in the fight against digital hackers and foreign governments looking to exploit holes in federal cybersecurity.
“These vulnerabilities exist on [federal] systems regardless of whether they are discovered, and the more vulnerabilities disclosed through the VDP Platform and remediated by agencies is a net positive,” CISA’s report notes.
Casey Ellis, founder and chief technology officer at BugCrowd, which partnered with CISA on the VDP and helped contribute to language in CISA's binding operational directive on vulnerability disclosure policies, told SC Media said one of the biggest impacts from the program was preparing federal agencies on how to ingest vulnerability reporting from the public, as well as creating a valuable feedback loop between government and security researchers.
"It is important to remember that the majority of [civilian federal] agencies differ greatly from cloud-native technology companies that find remediation straightforward," Ellis said. "Legacy technology is frequently involved, and 'vulnerability management and remediation' muscle groups must be developed. This response time and response rate indicates to me that the program proprietors are actively working to not only listen to the Internet's Immune System, but also improve their ability to act on its advice."
Last year, DoJ said it would no longer pursue prosecutions for “good faith” security research under the Computer Fraud and Abuse Act. At the RSA Conference in June of that same year, Leonard Bailey, head of DoJ’s cybersecurity unit and special counsel for national security in the Computer Crime and Intellectual Property Section, said the department has learned that “cybersecurity is complicated enough to not take certain players off the playing field when they’re helping.”
He also told SC Media that the department welcomed discussion with the cybersecurity community about the best way to define “good faith” security research.
“There have been concerns about how we actually will apply this sort of policy, and one of the things that we’ve been saying to the community is: why don’t you help us help you?” said Bailey. “That is to say, to the extent that there is an effort to kind of figure out what good security research is, you’re in a better position to define the norms and practices and the behaviors that should constitute that.”



