
A new variation of spyware that targets Android devices has been observed by researchers since October specifically targeting banking applications and impersonating applications from several large reputable financial institutions.
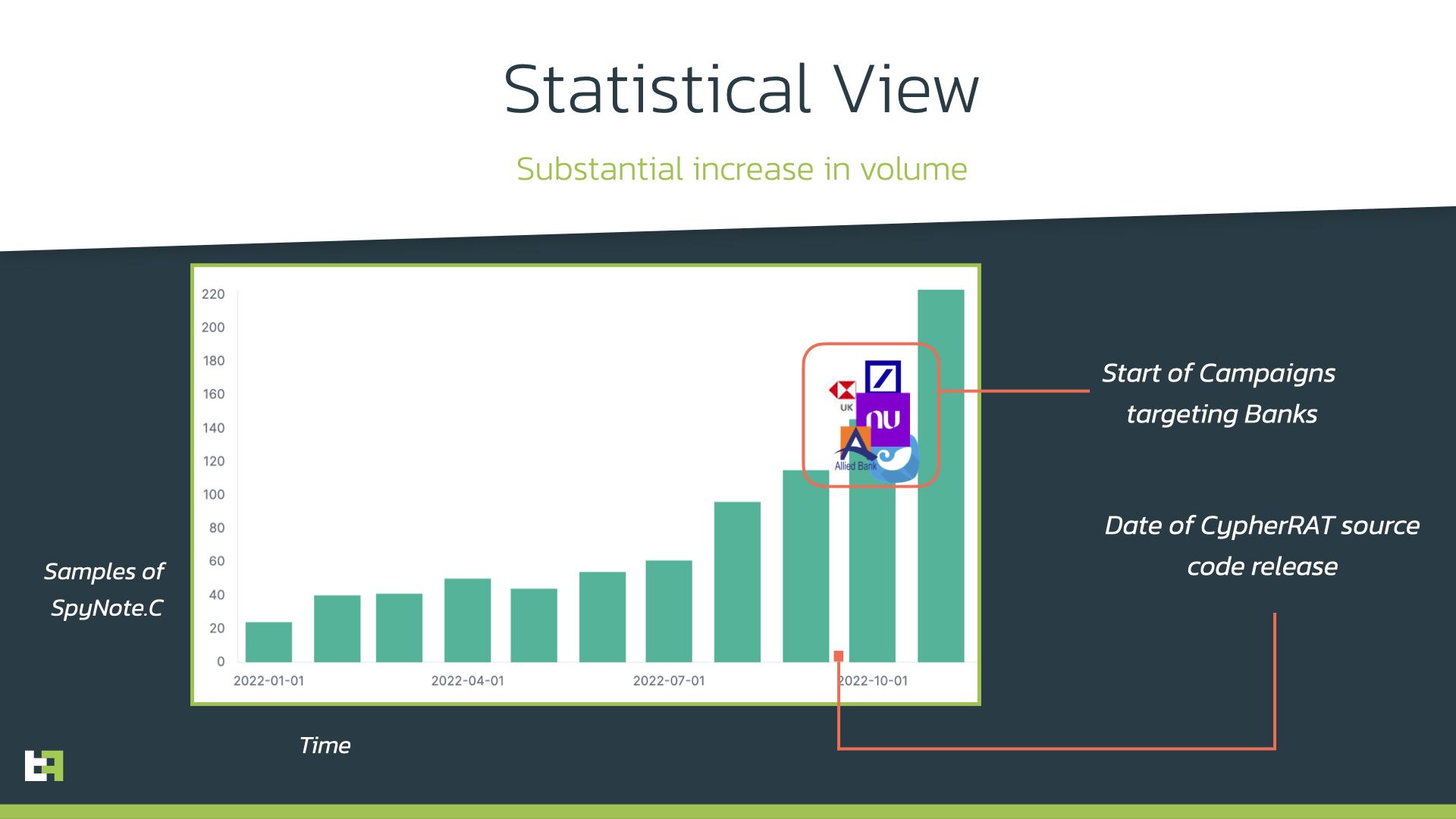
In a Jan. 5 posting, ThreatFabric researchers said they saw in October a large increase in samples from the SpyNote malware family. They note that the malware, aka SpyMax, can monitor, manage and modify device resources and features along with remote access capabilities.
Besides impersonating generic apps like gaming and productivity app, the SpyNote.C variant has also been impersonating financial institutions such as HSBC, Deutsche Bank, Kotak Bank, BurlaNubank, as well as other well-known apps like WhatsApp, Facebook and Google Play.
ThreatFabric researchers said the SpyNote.C variant was sold under the name “CypherRat” from August 2021 to October 2022, when the source code was made available via GitHub and they began seeing its use increase significantly.
SpyNote.C can exfiltrate and use personally identifiable information from online banking customers, as well as track SMS messages, calls, videos and audio recordings. It can extract two-factor authentication codes and record keystrokes, as well as lift passwords from social media apps like Facebook and Gmail.
By using Android’s Accessibility Services, the researchers say SpyNote.C makes it difficult to uninstall, and allows the malware to install new versions of itself, as well as other apps without any user input.
ThreatFabric researchers said in their conclusion that they see “the potential start of a new trend, which will see a gradual disappearance of the distinction between spyware and Banking malware, due to the power that the abuse of Accessibility services gives to criminals.”


