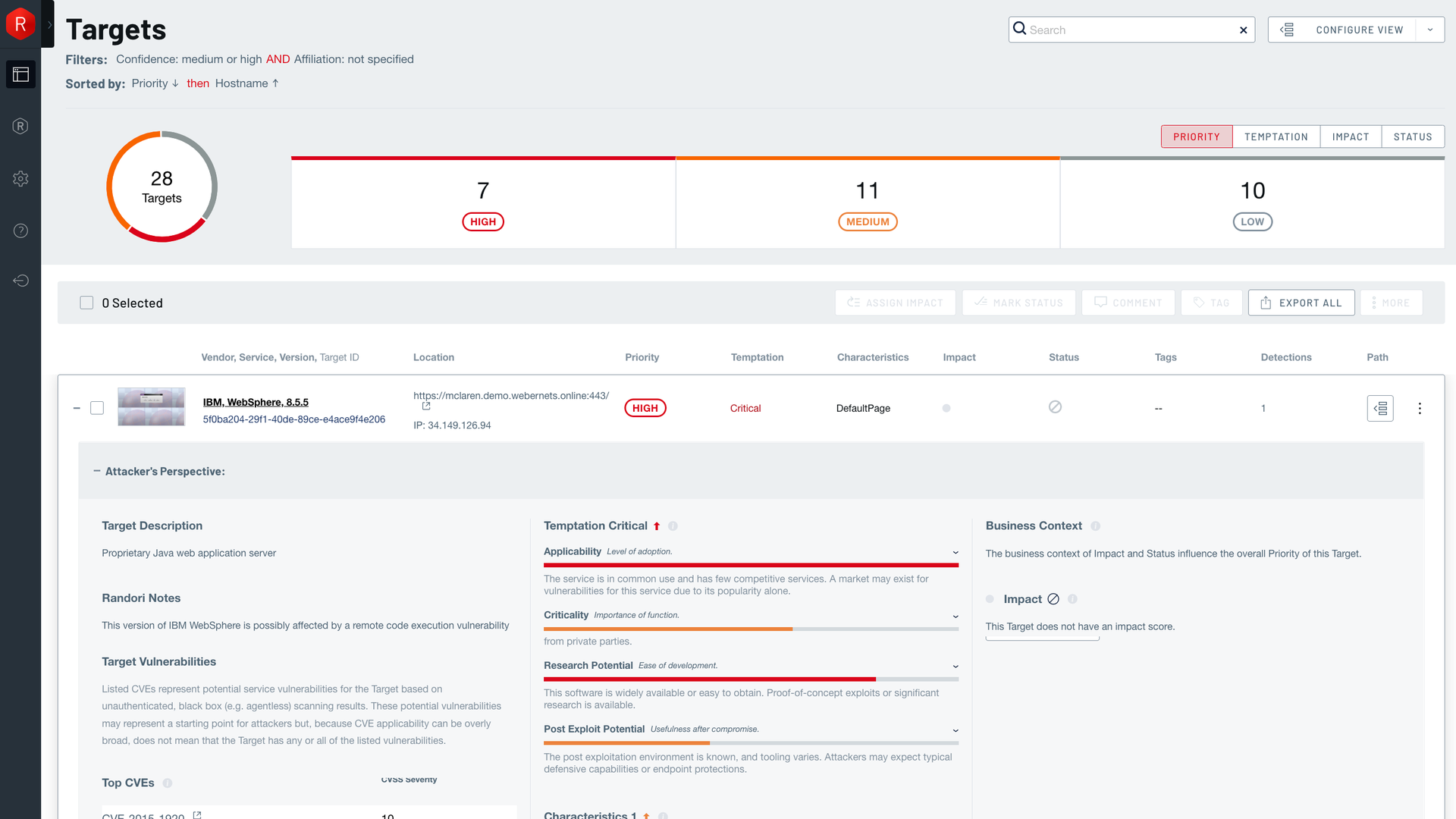
An increasingly sophisticated threat landscape requires ongoing efforts to track potential security gaps within networks and systems.
With that in mind, solutions recognized in this category monitor systems to identify issues before adversaries do by performing network or device vulnerability assessment. They may use active or passive testing and are either hardware-or-software based solutions that report vulnerabilities using some standard format/reference. The result? Better response to security issues that could leave companies exposed.