A search engine optimization (SEO) water hole technique called Gootloader has been observed targeting legal-related search terms and has been identified as a threat to law firms and people doing searches for legal information online.
In a blog post Aug. 10, Trustwave’s SpiderLabs said the Gootloader malware has gained notoriety because of its exploitation of compromised WordPress sites for malware distribution and its use of SEO poisoning techniques to achieve high rankings in web search results. By manipulating search engine results and luring unsuspecting users to compromised websites, the researchers said Gootloader takes advantage of a user’s trust in search results to deliver malicious payloads.
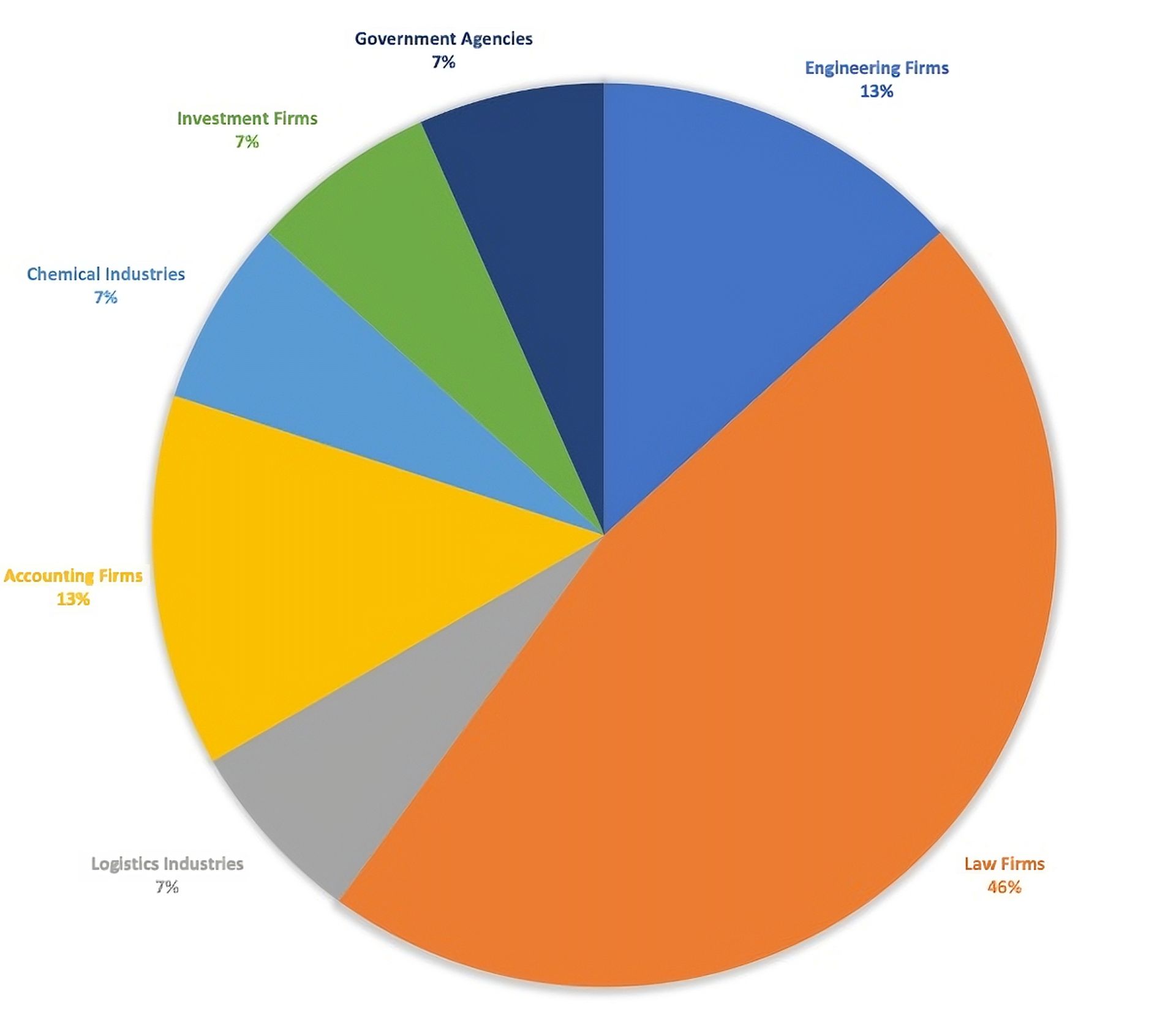
The SpiderLabs researchers reported that close to 50% of these cases target law firms (see chart below). And while the majority of the keywords are in English, the Gootloader campaign also targets the French, Spanish, Portuguese, German, and South Korean languages.
“Trustwave SpiderLabs has been tracking Gootloader for quite some time and has seen a variety of campaigns utilizing the first-stage loader malware,” said Karl Sigler, senior security research manager for Trustwave Spider Labs.
Sigler said the malware is somewhat unique since it combines SEO promotion of malicious websites offering industry-specific assets, such as contract templates, to lure victims instead of the more common phishing techniques.
“This technique balances the significant return of miscellaneous and random data from opportunistic attacks and the specific, but low-quantity data from targeted attacks," he continued. "Targeting a specific industry like the legal industry with this type of attack will likely result in a high volume of a specific data set.”
According to SpiderLabs, the attack typically starts with a seemingly harmless search for supply agreement documents that lead to the compromised WordPress webpages controlled by Gootloader actors. SpiderLabs collected several search queries that lead to the compromised websites and identified the keywords used by this malware group, revealing a predominant SEO keyword focus on legal documents, such as “agreements,” “contracts,” and “forms.”
When visiting a poisoned link from the search engine result, the researchers said the user would get directed to a page that mimics a forum. This fake forum page employs social engineering tactics to entice the user to click on a direct download link for the desired document file. When the user clicks on the download link within the fake forum, they are redirected to another WordPress webpage, typically identified by the PHP path "download.php," which is also controlled by the attacker. The visitor’s information is similarly checked, and when the conditions are satisfied, a ZIP file gets provided for download. The filename of the ZIP file is derived from the user’s search keyword.
Here's the catch: The ZIP file does not contain the intended file that the user was expecting. Instead, it conceals a malicious .JS file, cleverly hidden within a legitimate JavaScript library, explain the SpiderLabs researchers.
Law firms store highly sensitive information that spans mergers and acquisitions, intellectual property, medical records, trust and estates, tax data, and a range of legal filings, making them a prime target of threat actors, said John A. Smith chief executive officer at Conversant. Smith said the Gootloader malware gets targeted specifically at law firms likely because of the attractiveness of their data assets.
“It has been used since late 2020 to deploy ransomware, as well as infostealers and remote access tools,” said Smith. “Ransomware is always a top threat for law firms, because firms cannot afford to lose their data or see it published — they rely on both client trust and their reputations for continued business, so paying the ransom is often the best or only path to resolution.
Smith said because this attack relies on end users downloading a malicious file, it may seem that training the end user is the best course to avoid these incidents.
"However, end-user training is one part of a layered defense strategy, and if IT had employed the proper controls that blocked users from being able to download such files, and the proper file inspections had been activated at the controls level, the file would not have been downloaded regardless of the actions of the user," Smith added.




