Anyone duped by a clever phishing campaign is in for a world of hurt. Researchers are sounding a "critical severity" alarm over a malicious Microsoft Word document that packs malware strains RedLine Clipper, Agent Tesla and OriginBotnet.
At risk, according FortiGuard Labs, are "any organization," according to a technical breakdown of an August phishing campaign spotted by researchers, who posted a technical breakdown of the maldoc on Monday.
According to the writeup, by Senior Virus Analyst Cara Lin, the Word document contains a malicious URL what will drop malware onto the victims system. Malware includes OriginBotnet (for keylogging and password recovery), RedLine Clipper (for cryptocurrency theft via clipboard data) and Agent Tesla (for credential harvesting).
Targeted data associated with applications include popular cryptocurrency wallets, leading browsers, Outlook and other e-mail clients and a host of VPN services.
"[Attacks begin] with a malicious Word document distributed via phishing emails, leading victims to download a loader that executed a series of malware payloads," Lin wrote. "The attack demonstrated sophisticated techniques to evade detection and maintain persistence on compromised systems."
The "complex chain of events"
Lin said cyberattacks associated with this campaign involve "a complex chain of events."
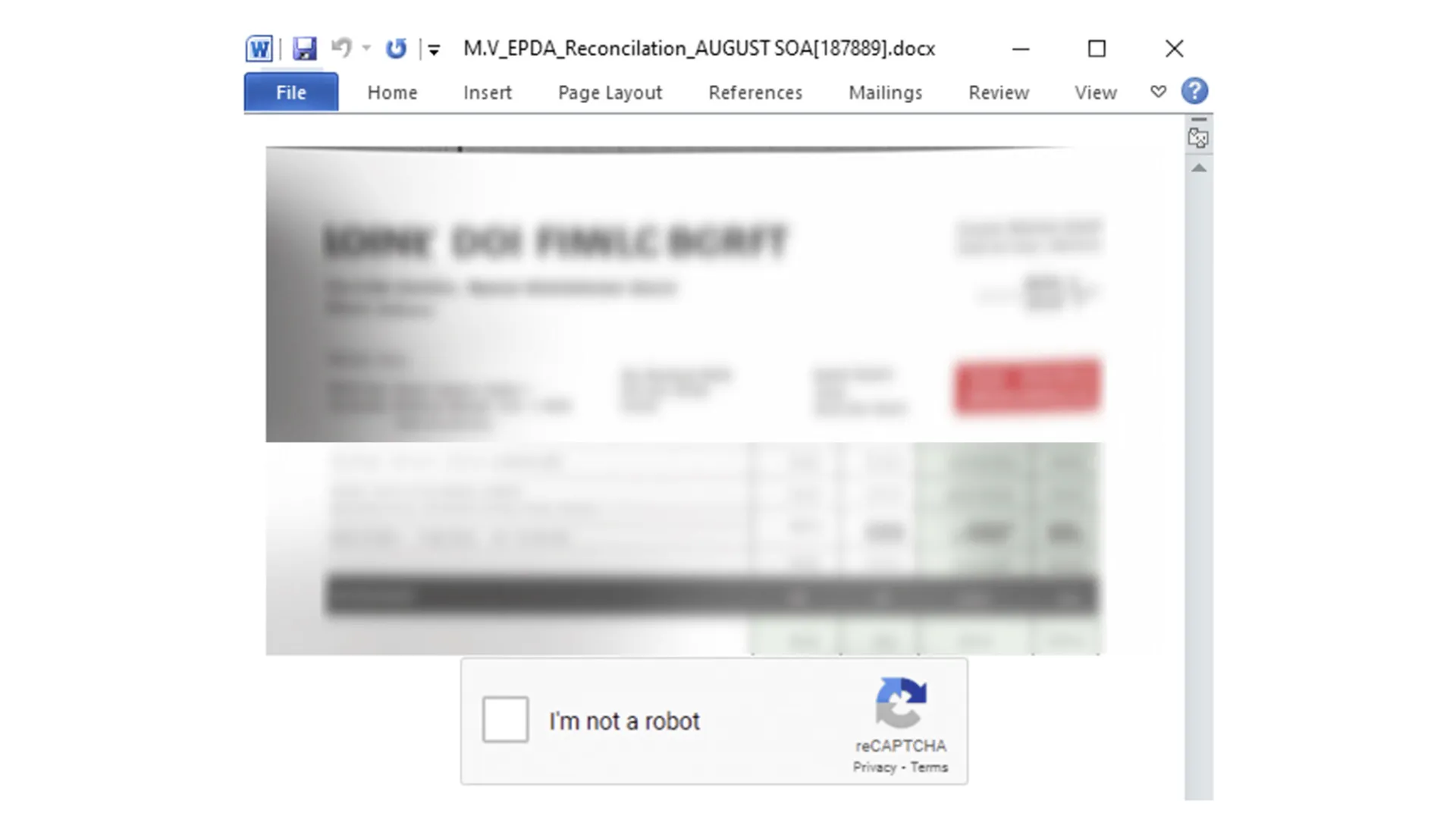
First off, the Word Doc, delivered via a phishing email attachment, was displayed as a blurred image along with a fake reCAPTCHA. Once clicked, an embedded link executes a malicious file for the initial loader, which initiates several functions across four stages.
The second stage initiates multiple functions to establish persistence, and to ensure persistence, it duplicates an EXE file into a directory to ensure the file “audacity.exe.exe” runs automatically even if the device is restarted.
The RedLine Clipper (also known as ClipBanker) specializes in stealing cryptocurrencies and “originates from the URL https://softwarez[.]online/javau[.]exe. It is a .NET executable file that has been packed using SmartAssembly,” Lin wrote. The malware does this by manipulating the user’s clipboard activities to substitute the destination wallet address with one belonging to the attacker.
The Agent Tesla malware logs keystrokes, has access to the clipboard and scans the device’s disk to uncover credentials and other data. It also transmits the information it gathers to its command-and-control server through various channels, including HTTP(S), SMTP, FTP, and even a designated Telegram channel, according to Lin. Agent Tesla establishes itself as an auto-run entry within the system registry.
The OriginBotnet is stored as “david.exe” and has a range of capabilities, including collecting sensitive data, establishing communications with its C2 server, and downloading additional files from the server to execute keylogging or password recovery functions on compromised devices, wrote Lin.