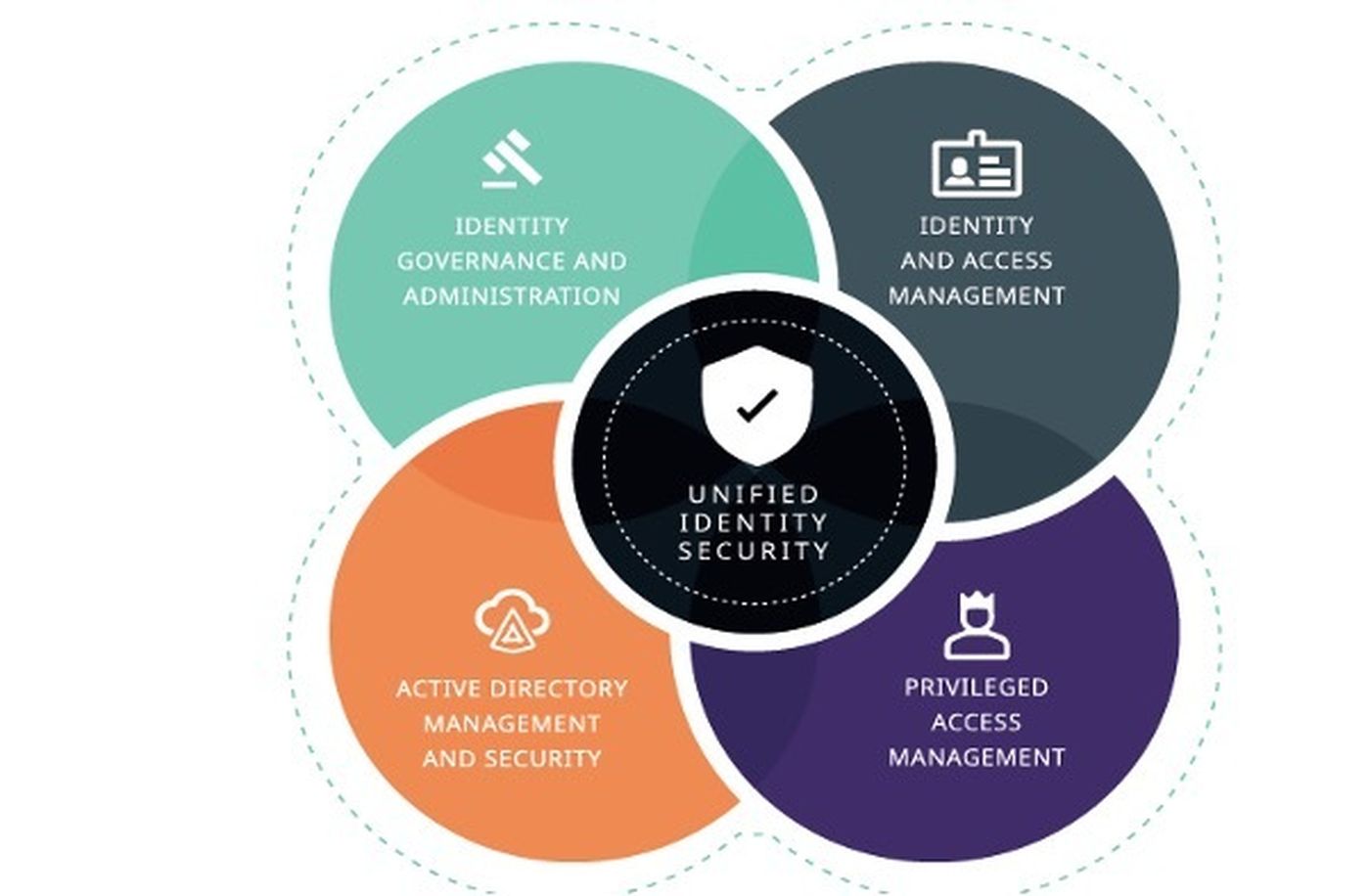
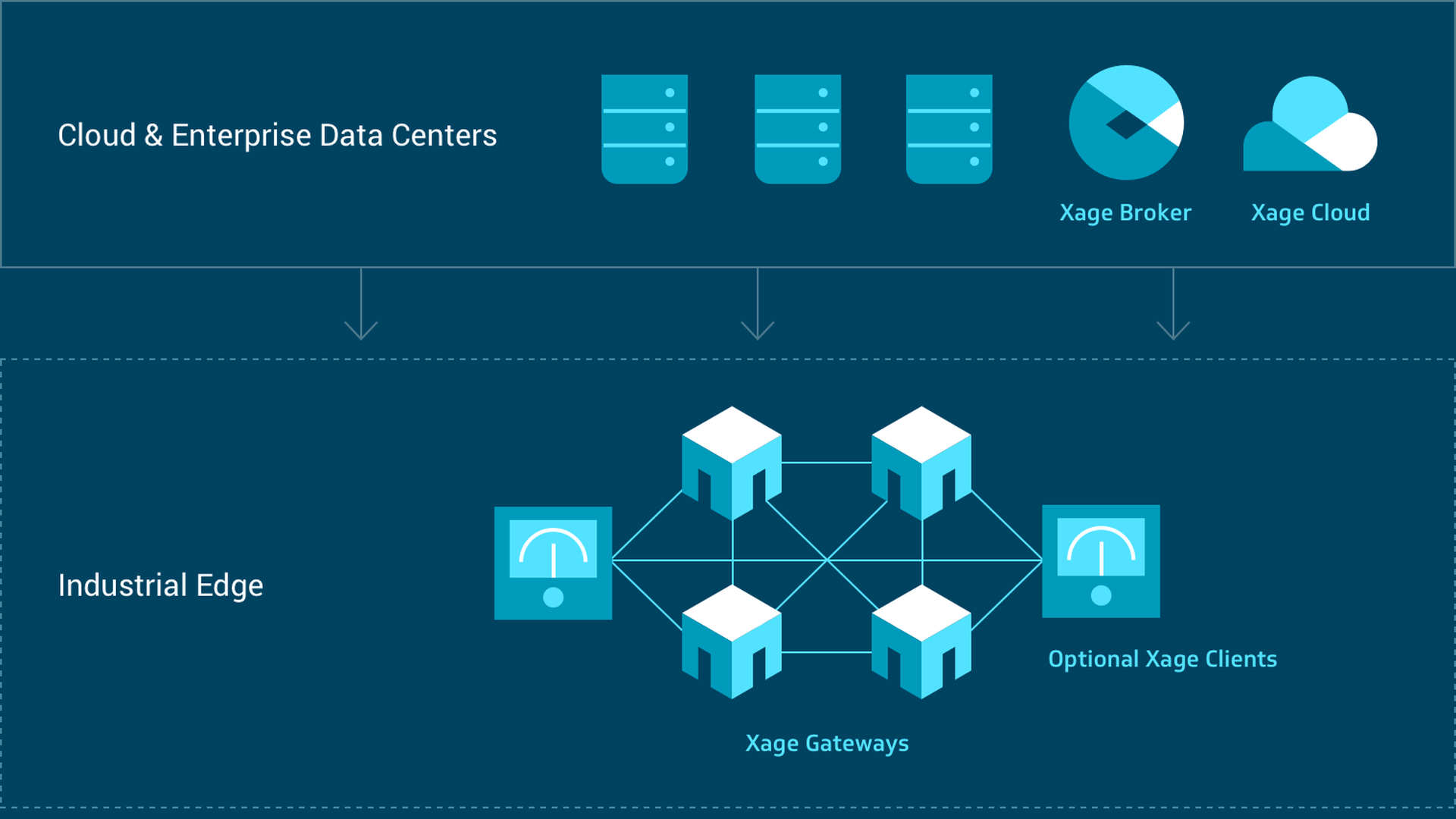
As a core pillar of zero trust, identity and access strategies protect recognize the need to track and protect the range of identities across the enterprise – human or machine – to detect and prevent breaches.
Products recognized in this category address the identity management life cycle in an enterprise environment, including password management, user provisioning and enterprise-access management.