Vendor: Illusive Networks
Price: $25 per endpoint, per year
Contact: www.illusivenetworks.com
Quick Read
What it does: Illusive Networks Attack Detection System uses agentless automation to detect and disarm attackers, disrupt their decision-making process, and stop further movements.
What we liked: It’s a powerful, agentless deception product that delivers direct endpoint visibility without the vulnerability often associated with continuous detection. We really like the Attacker View, which provides a great visualization of attack surfaces and potential areas for lateral movement within an environment.
Security pros will find Illusive Networks Attack Detection System a next-generation deception solution that uses agentless automation to detect and disarm attackers, disrupt their decision-making process, and stop further movements. The realistic decoys eliminate high-risk pathways to crown jewels, compel attackers to reveal themselves early in the lifecycle, and trigger real-time forensic capture that accelerates incident response.
The hard truth about cyber security is that it’s inherently unfair. Hackers have many opportunities to infiltrate environments and need to succeed only once to achieve their goals, whereas defenders must defend themselves against every attack to achieve theirs. Illusive flips the advantage of this asymmetrical battle to defenders and blue teams. Illusive Networks Attack Detection System plants fake data on endpoints to create a hostile environment and to detect attackers early in the attack cycle, alerting security teams to their presence and putting the pressure back on adversaries. With so many automated tools, this solution creates more manual work for attackers and less work for security professionals.
Illusive Networks focuses primarily on protecting against living-off-the-land attacks aimed at credential and connection data exploitation. It deploys onto production systems agentless, highly authentic, and containerized deceptions that target attackers specifically. The product requires a policy violation for deceptive data to become visible so normal end-users should never see any deceptions. Full operating system decoys and honey pots are available in addition to production decoys, creating a rich and unique deceptive story for every environment.
Illusive Networks Attack Detection System reduces the true attack surface even as it uses deception to create the illusion of an expanded attack surface. The Attack Surface Manager functions as a basic, cyber hygiene tool at its core. It removes excess credentials, connections, and pathways to critical assets to harden the network and shrink the attack surface. The Illusive deception tool analyzes the credentials and connections within an environment, identifies the objects that pose a security risk, and then removes them safely. It also identifies policy violations and errant credentials, connections, and attack pathways and cleans them off the system.
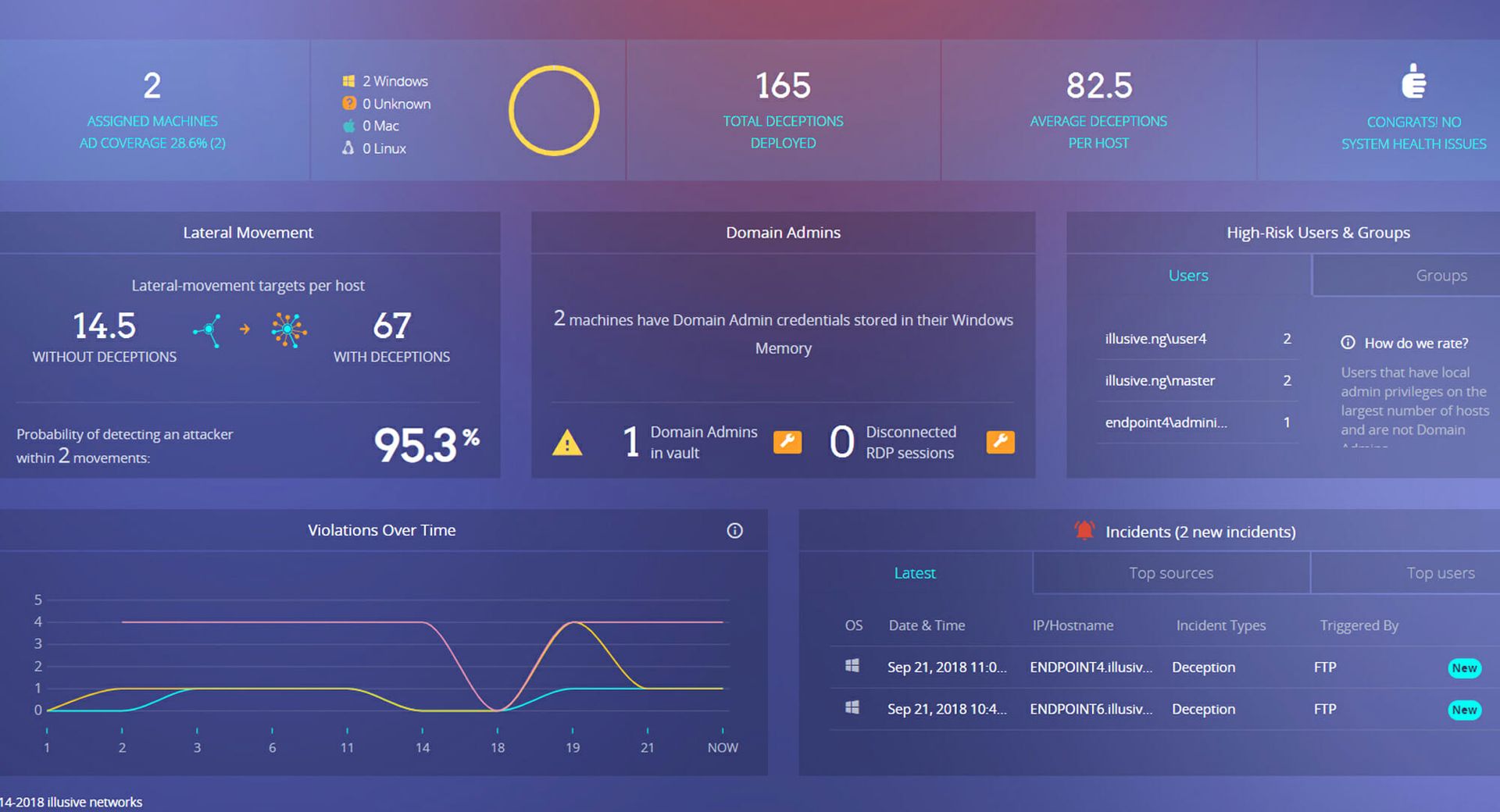
The attractive dashboard effectively displays helpful information, such as high-risk users and groups and incidents to provide information that’s consumable by tier 1 analysts and incident responders alike. The Attacker View offers a great visualization of attack surfaces as well as potential areas for lateral movement within an environment. Incident investigation pages include full forensic timelines and valuable information such as the triggering process, PowerShell history, and desktop screenshots.
Overall, security pros will Illusive Networks Attack Detection System a powerful, agentless deception product. It delivers direct endpoint visibility without the vulnerability often associated with continuous detection. Attack Surface Manager protects against lateral movements, while source-based forensics pull threat intelligence and detection data directly from the source production systems to ensure that organizations always have the most relevant attack information.
Pricing runs $25 per endpoint, per year for 1,000 endpoints and includes 8/5 support. 24/7 support is available for an additional fee.



