If you work in the IT trenches, there has likely come a moment while you were sitting in your office, reviewing the latest news about current phishing campaigns, when you suddenly looked up and cast your eyes across the floor, pondering a very basic question: just what are your users doing with all those malicious emails that you know are washing up in their inboxes despite your best efforts to stem the tide?

Most organizations these days have deployed multiple layers of security to monitor and protect their networks, servers, and endpoints. But no matter how good your anti-virus and Exchange security software is, no matter how granular the logging available for review may be, you know there are two things you still can't guarantee.
You can't guarantee that your users will never be forced to deal with increasingly sophisticated malicious emails, all of them driven by proven social engineering schemes cooked up and road-tested by malicious parties.
Worse, you can't tell your boss that you have deep insight how your users are actually handling those phishing emails. The best you can do is wait for all your organization's various layers of security to alert you that something is amiss (and then hope it isn't too late to head off disaster).
So, as you watch your users staring intently at their screens, it's difficult not to wonder: just what are they doing?
Let us show you, using actual phishing emails reported by customers who have deployed the Phish Alert Button (PAB). In what follows we will take you through all-too-common examples of what we see users doing every day when handling phishing emails. Fair warning: it ain't pretty.
Say It Ain't So, Joe!
When your users show up for work every day, most of them have one primary concern: doing their jobs as quickly, efficiently and effectively as they can. Although they have been told that security should be on their minds, most will have little experience dealing with savvy bad actors. And the decisions they make when actually confronted with live phishing emails reflect that inexperience.
One of more common decisions that employees make when they encounter suspicious emails is to hit the Reply button in order to confirm that those worrisome emails are, in fact, safe to open.
What all too many of these employees do not realize, however, is that the answers they receive will be from bad guys operating from compromised emails accounts. And you can guess what these fraud artists are telling your users.
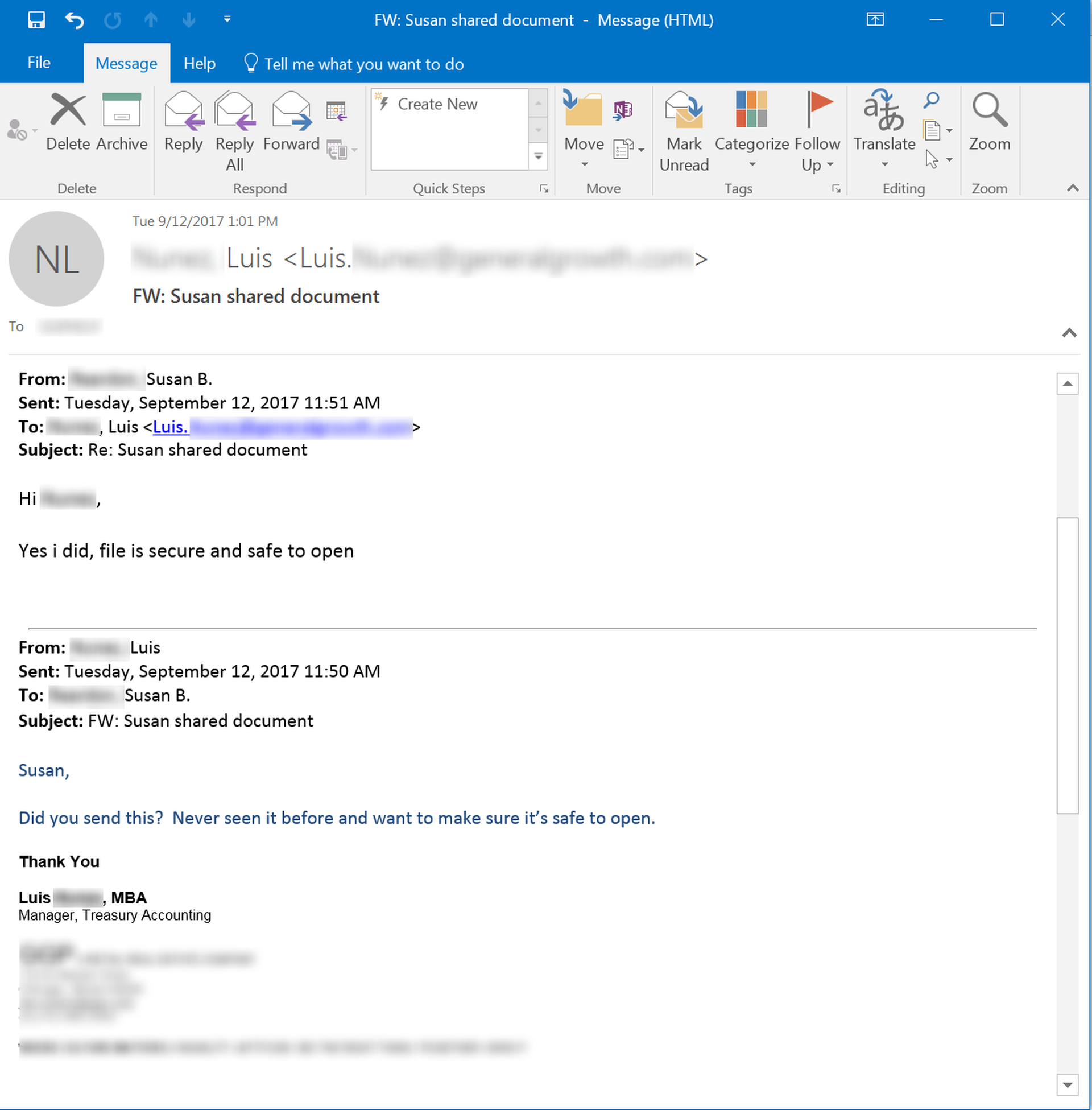
Some of these bad guys are so confident in their ability to pull the wool over your users' eyes that they're even willing to subtly taunt them.
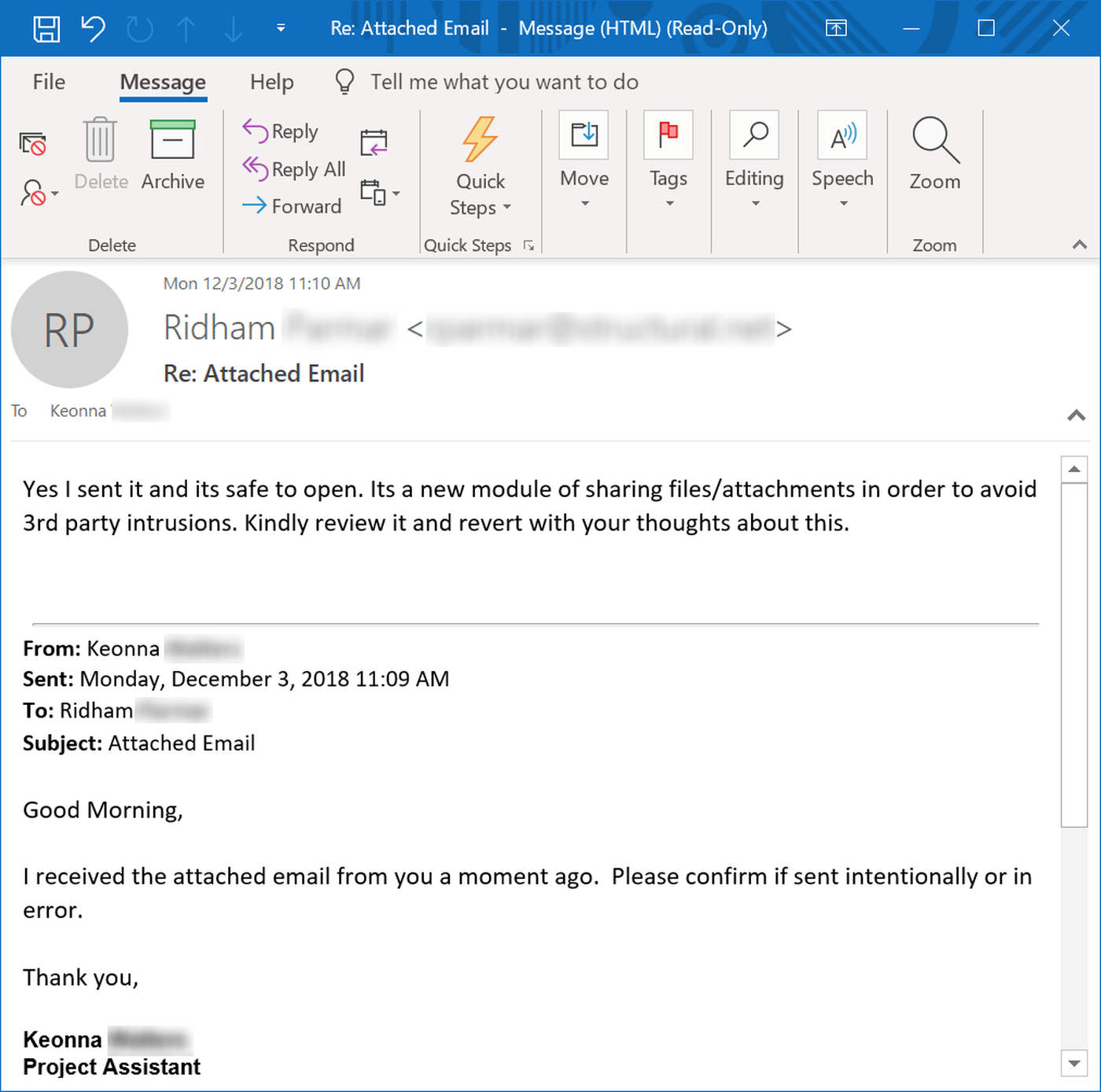
When users see a familiar name in the From: line of an email, the temptation to trust what comes from those familiar email accounts will be powerful.
Sharing the Wealth
Another common behavior we see among users dealing with malicious emails is a troubling tendency to share and forward those emails, most of them laden with malicious links or attachments. And every person who receives those emails represents another opportunity for the bad guys to capture login credentials or drop malware inside your network.
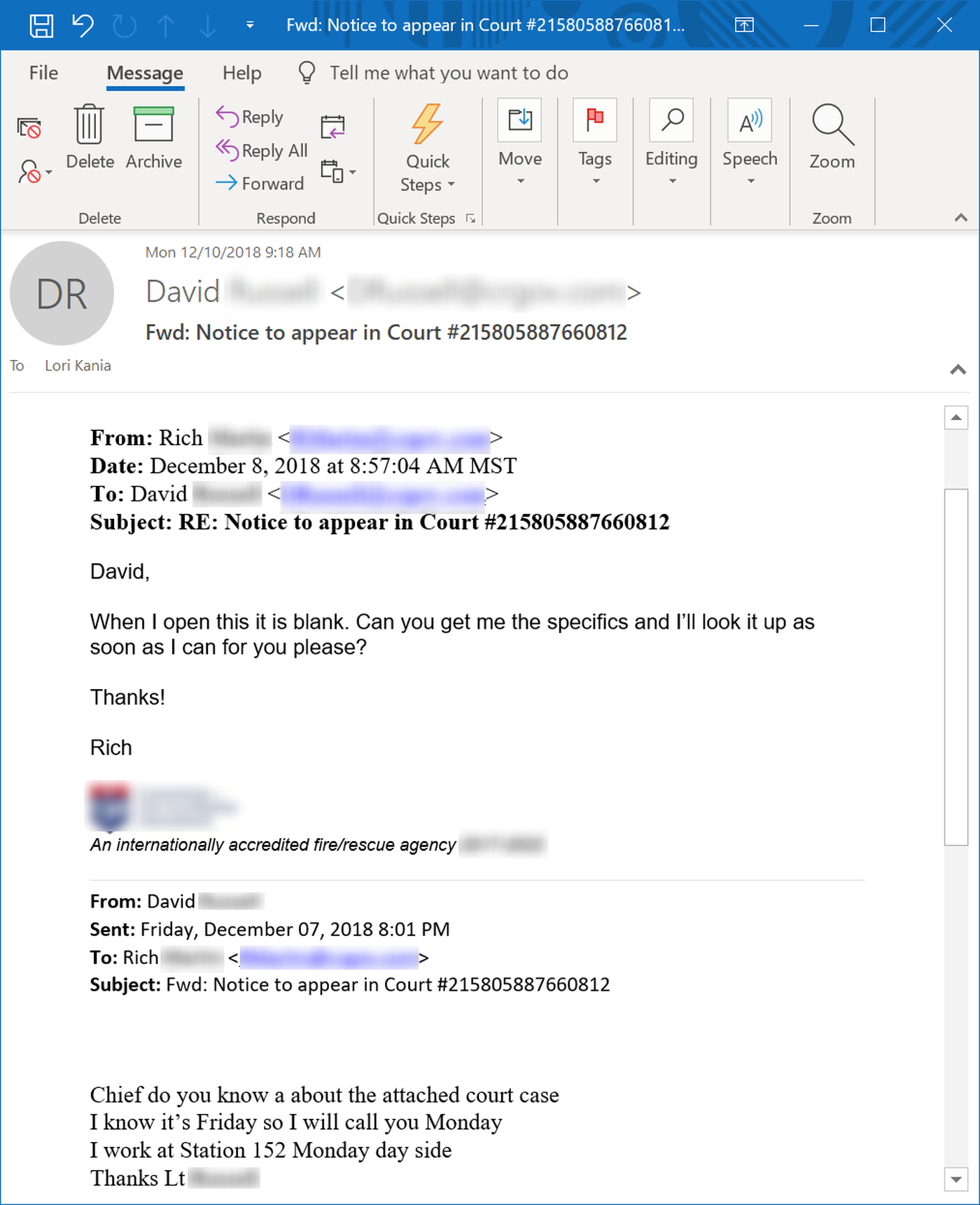
Many users forward on malicious emails without little awareness that in doing so they are doing the work of malicious parties. This particular user, having received a fake court notice with a malicious, thought it only reasonable to alert his boss. The boss, of course, opened the malicious attachment straightaway.
Even when users do suspect that danger may be lurking within emails they have received, they still forward those malicious emails to others. When they do, they inadvertently kick off a chain of forwards, exposing multiple users to malicious links and attachments.
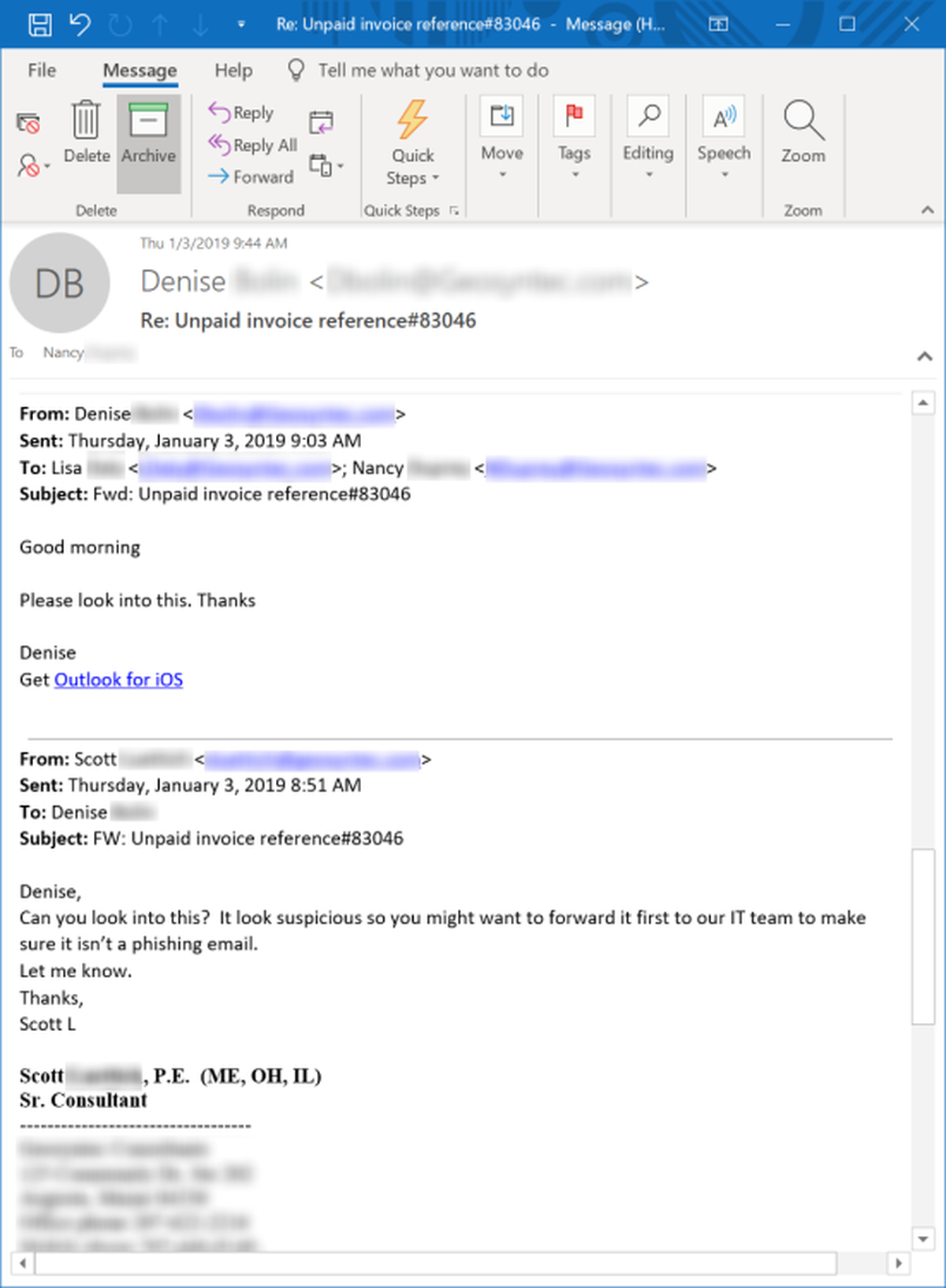
Consider this senior consultant at an engineering consulting firm who receives a fake invoice phish and proceeds to sets off a chain of forwards by instructing a junior consultant to look into it.
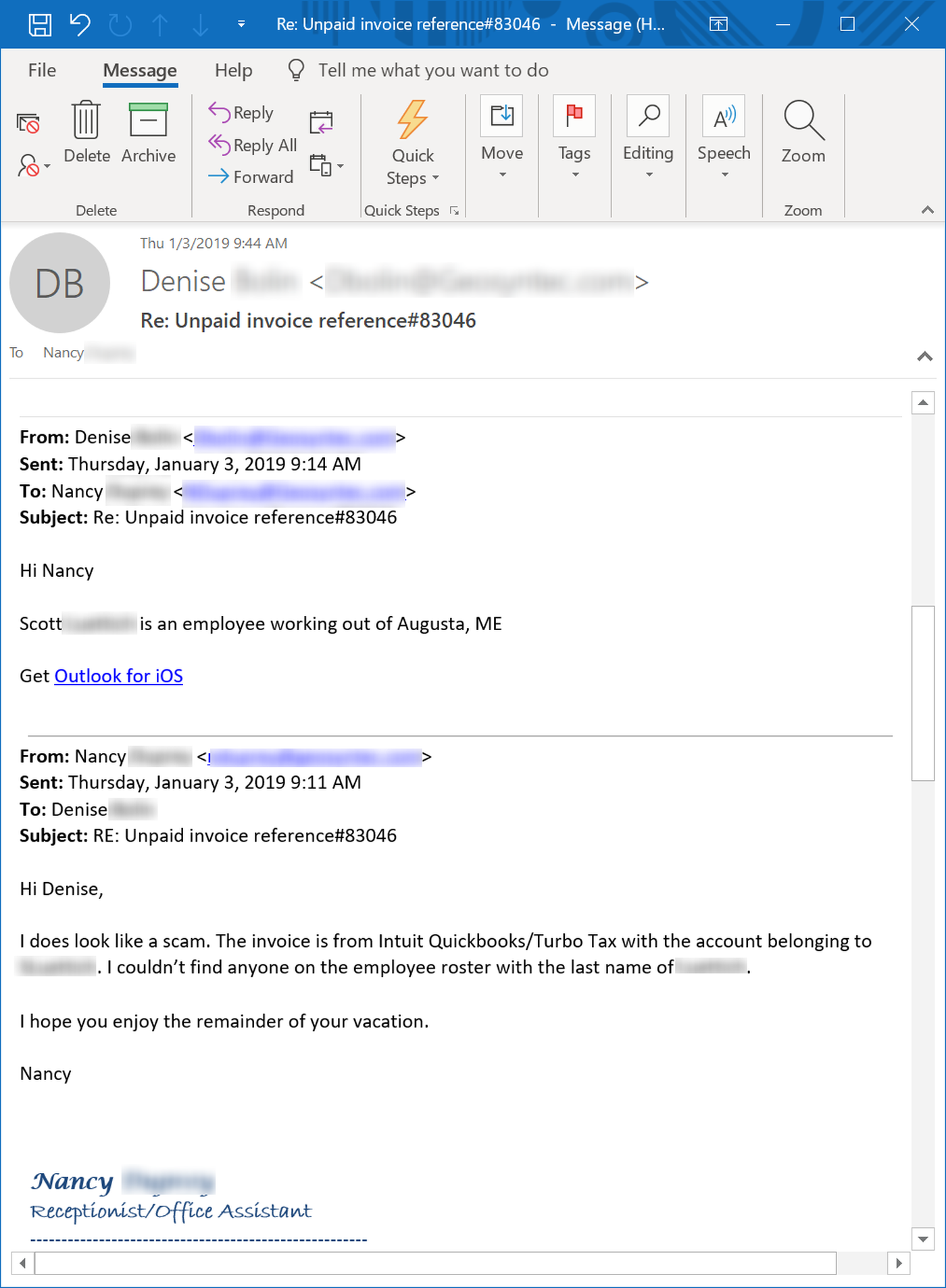
The whole mess eventually lands in the lap of a lowly "Receptionist/Office Assistant" working in completely different office.
Note that at this point multiple employees have likely clicked the malicious link and absolutely no one has checked the original email with IT, despite suggestions to do just that.
Asking for More
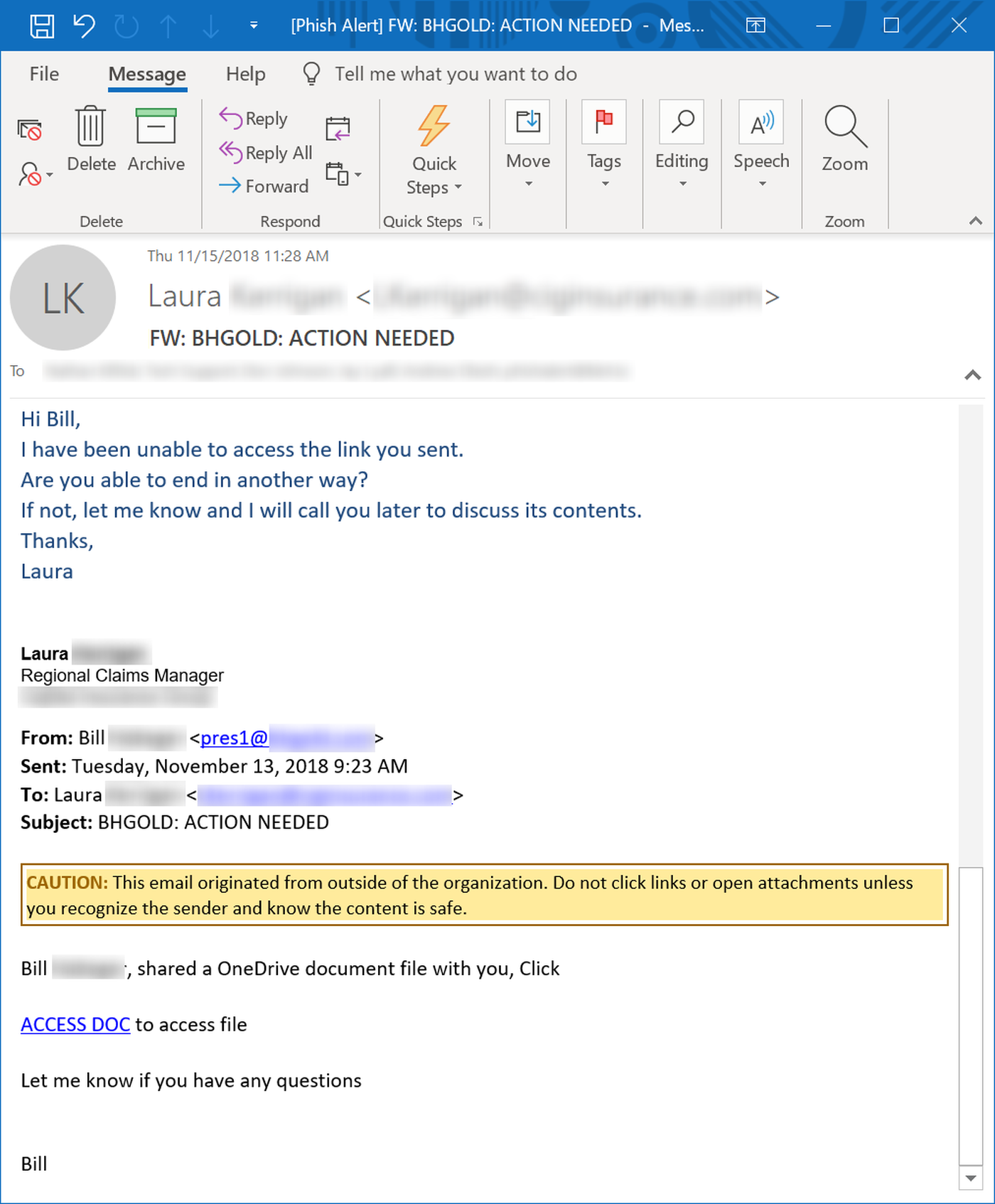
Users can remain oblivious to email-borne threats even in the face of obvious alarms -- like odd behavior when they attempt to open malicious attachments and links. Determined to do their jobs, such users can find themselves blithely inviting malicious actors to provide them with still more opportunities to compromise their PCs as well as the networks of their employers.
We recently observed this depressing phenomenon after users received a phishing email delivered unwittingly by Dropbox itself and pointing to a malicious file hosted on a compromised Dropbox account. A number of users confused by that malicious file ended up posting their email addresses to a virtual "wall of shame":

Indeed, we often see users stymied by the inexplicable behavior of malicious links and attachments demonstrating their willingness to go the extra mile to get their hands on files they do not realize are malicious.
Pleading Ignorance
And then there are the users who simply throw up their hands when the bad guys ask them to engage in dangerous behavior. This particular user tried to plead ignorance when asked by the bad guys to assist with a wire fraud scheme.
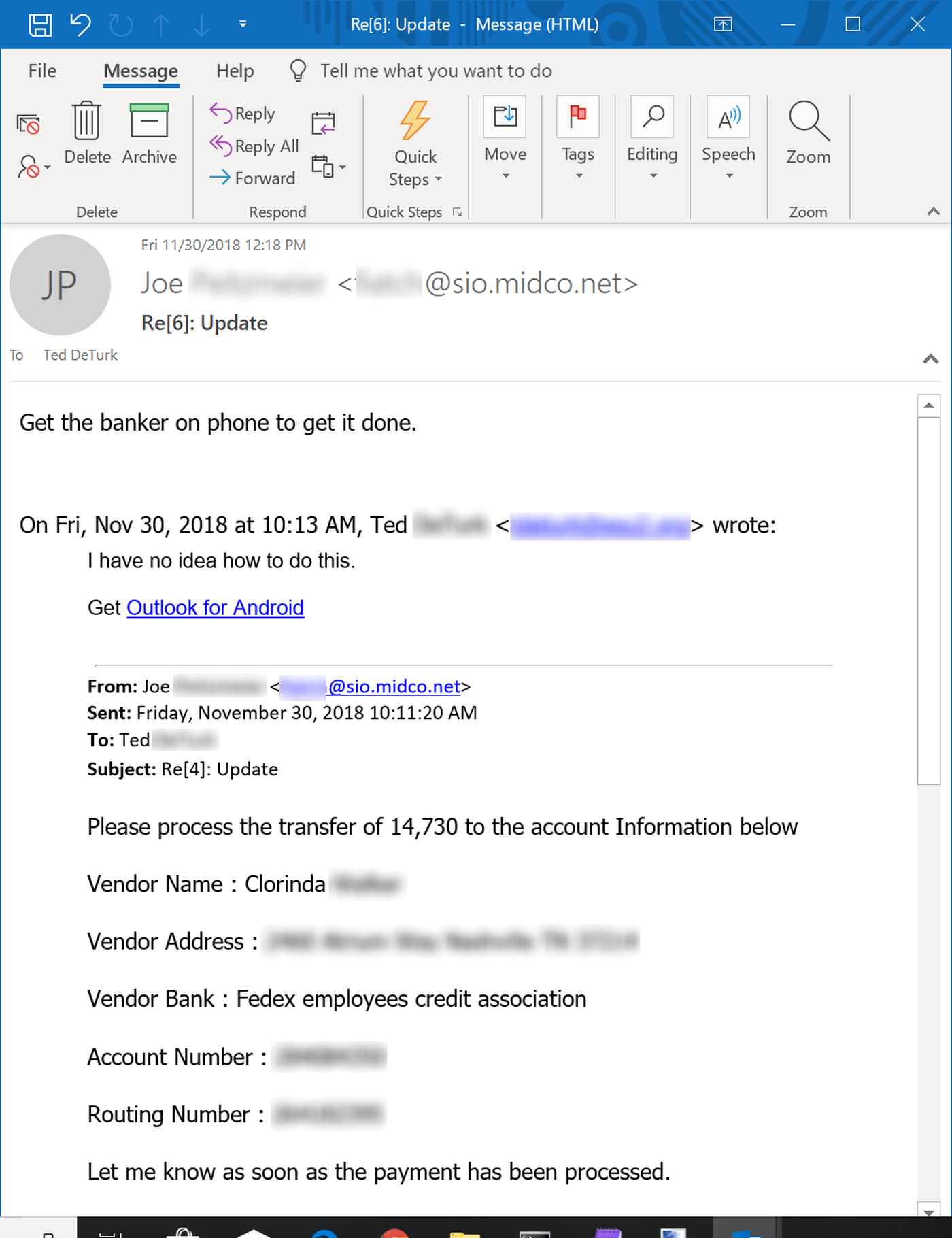
Unsurprisingly, the bad guy in this case was having none of it. Fortunately, the user here clicked the Phish Alert Button (PAB) instead of forwarding this request to others in his organization who might have been able to perform the wire transfer.
Eager Beavers
Not many users are willing to resort to the ignorance excuse when dealing with bad guys posing as senior executives within their organization, though. It is much more common to observe users all too willing and eager to spring into action when the bad guys come calling.
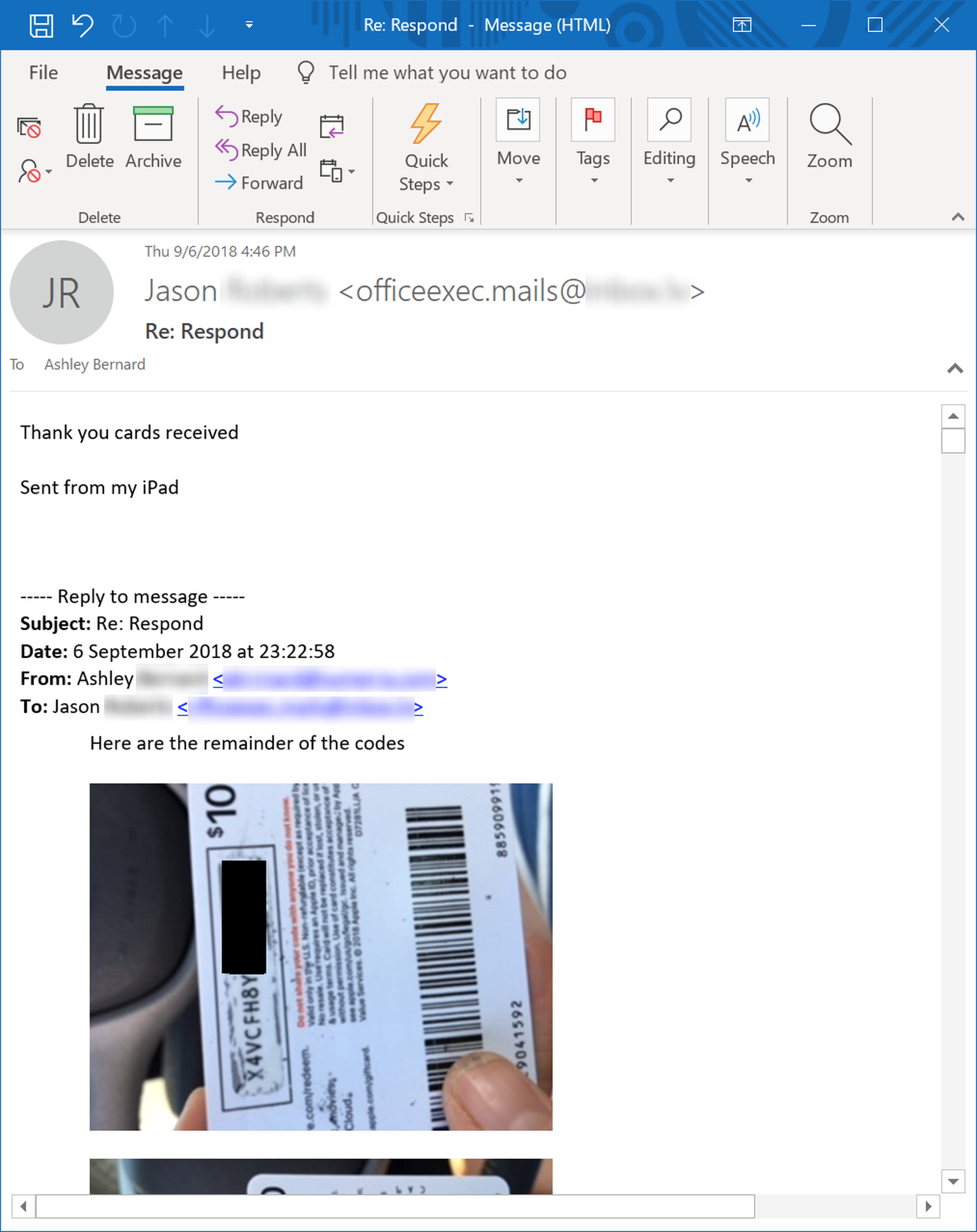
One of the more alarming cases we witnessed recently involved an employee named Ashley, who fell victim to one of the more prevalent phishing campaigns currently in use: the iTunes gift card phish.
Asked by a bad guy posing as her boss to purchase a whopping twenty $100.00 iTunes gift cards, Ashley promptly hopped in her car and drove around town, hitting multiple stores (because no single store would allow her to buy more than four or five cards at a time), then sitting in her car and emailing screenshots of each card's scratch-off code. Worse she put the entire $2000.00 in gift cards on her own personal credit card.
Targeted in yet another form of CEO fraud phishing, Phyllis was so helpful in getting her boss's direct deposit data changed that even the bad guys posing as her boss were impressed, wishing her "compliments of the seasons."
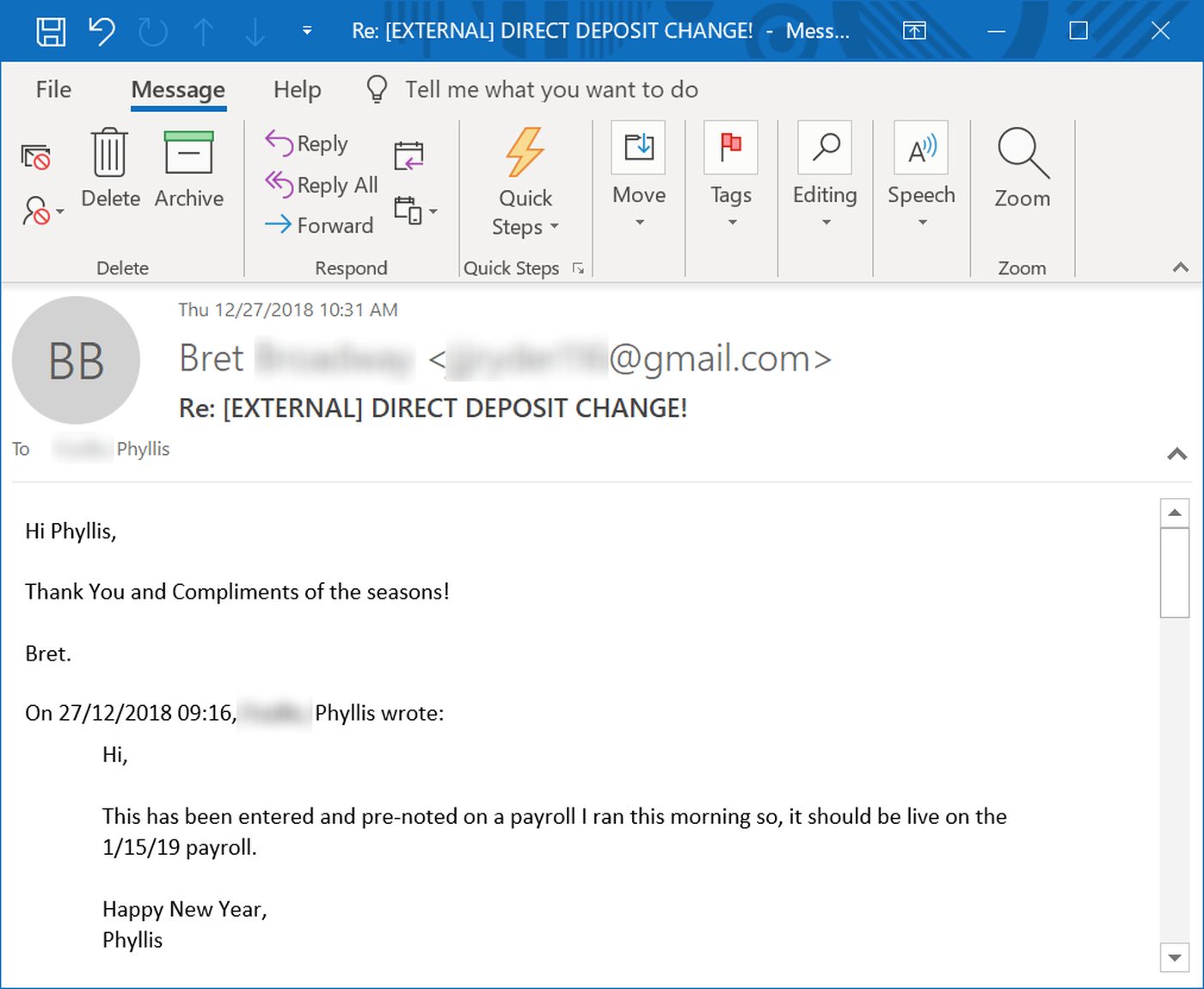
Decidedly less impressed was her actual boss, who found that Phyllis was handing over his paycheck to the bad guys when she helpfully cc'ed his work email address:
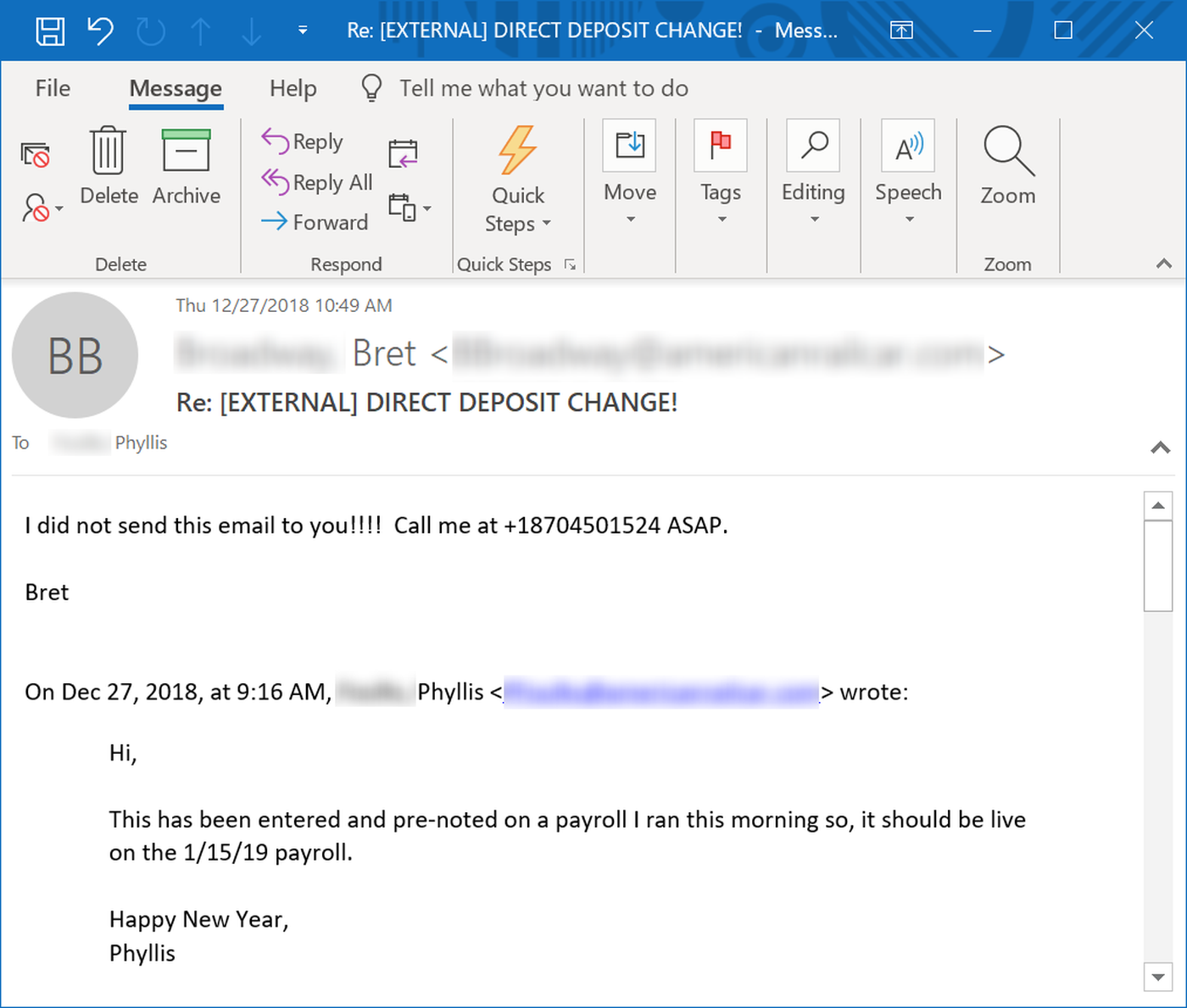
Ignoring the Obvious
Some users are just clueless and overly eager to get stuff done or keep their bosses happy. Others, however, deliberately ignore obvious signs of trouble when handling malicious emails. And while it's one thing to ignore red flags when opening a link or attachment on one's own PC, it's quite another to blow through an explicit warning from an anti-virus program, as this employee did...
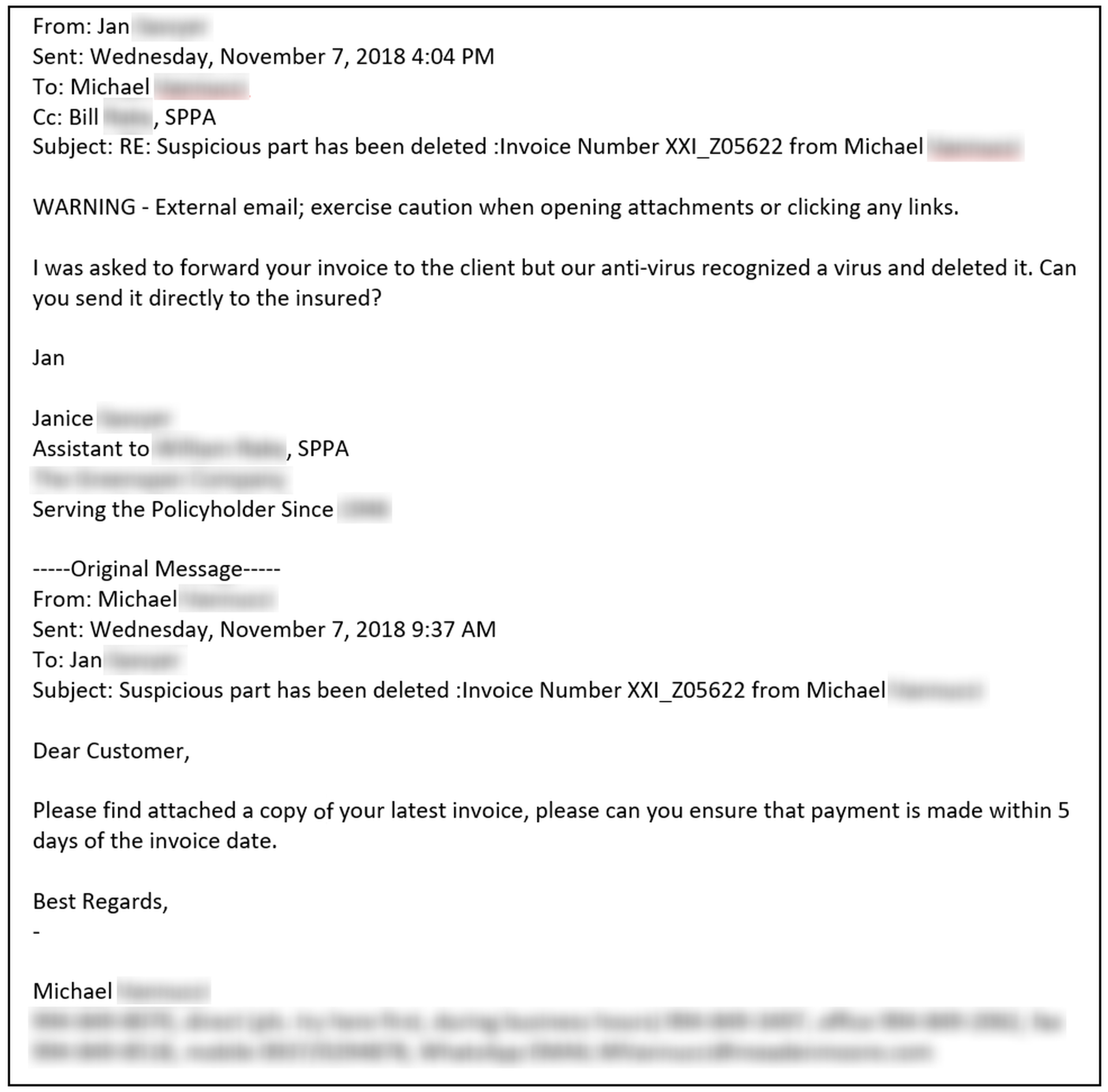
...and then request the bad guys themselves send on that same malware to one of the organization's customers or clients. Once again, this kind of response simply provides the bad guys more opportunities to sow destruction and chaos.
Unfortunately, it's not just lay users who are prone to ignoring malicious threats, even when those threats are staring them in the face. Less experienced IT employees are perfectly capable of doing much the same.
We had to chuckle at this response from one organization's help desk when a user reported the opening salvo in an obvious email scam:
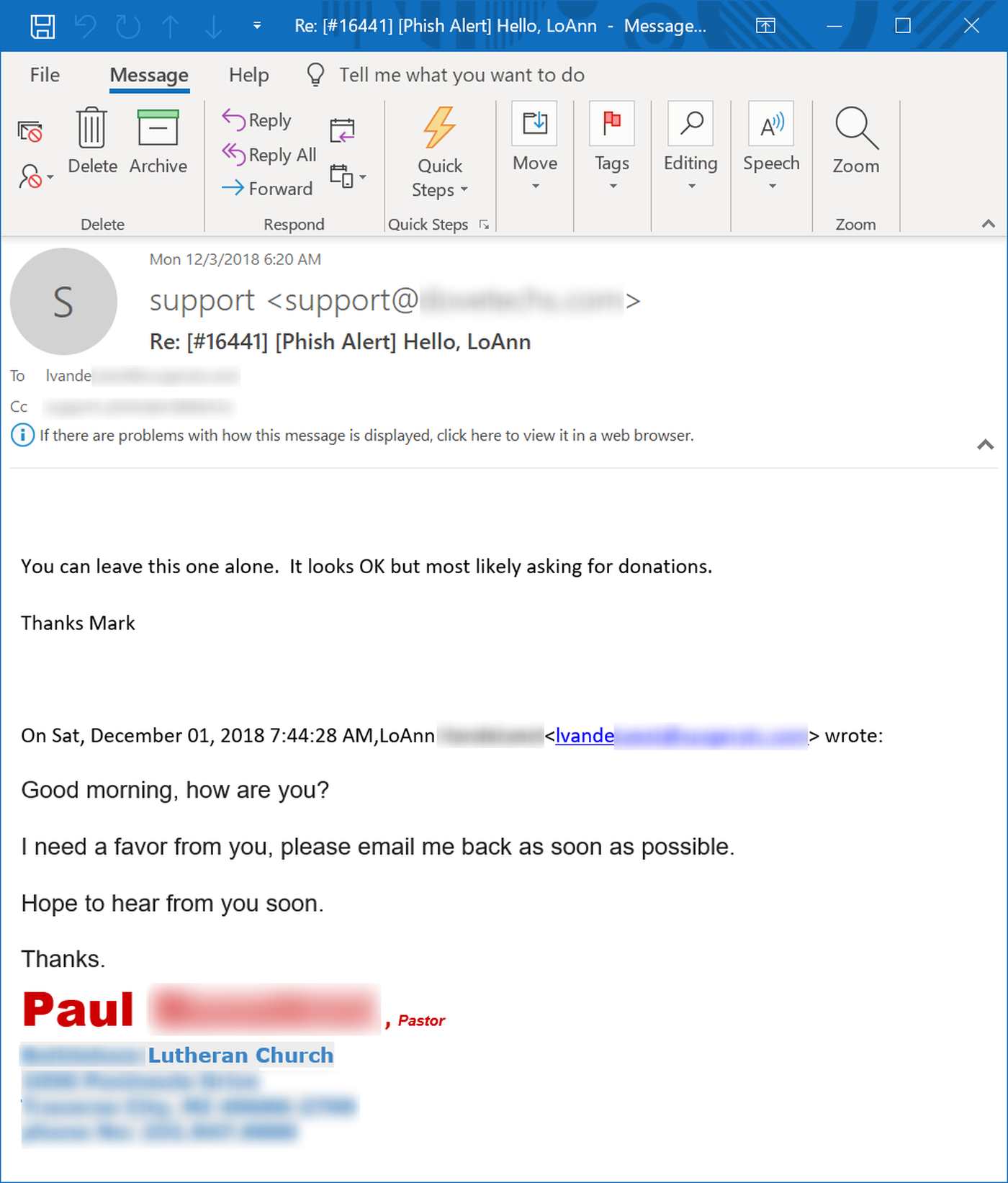
Yes, the malicious party spoofing Pastor Paul would almost undoubtedly be asking for "donations," just not the charitable kind.
There's also something darkly humorous in this exchange between another user and his organization's help desk. When the user received a fake invoice phish from the compromised email account of someone named "Joseph F," he had several good reasons to suspect a rat, not the least of which was the fact that the organization's anti-virus had flagged the attachment as malicious. But there was another reason.
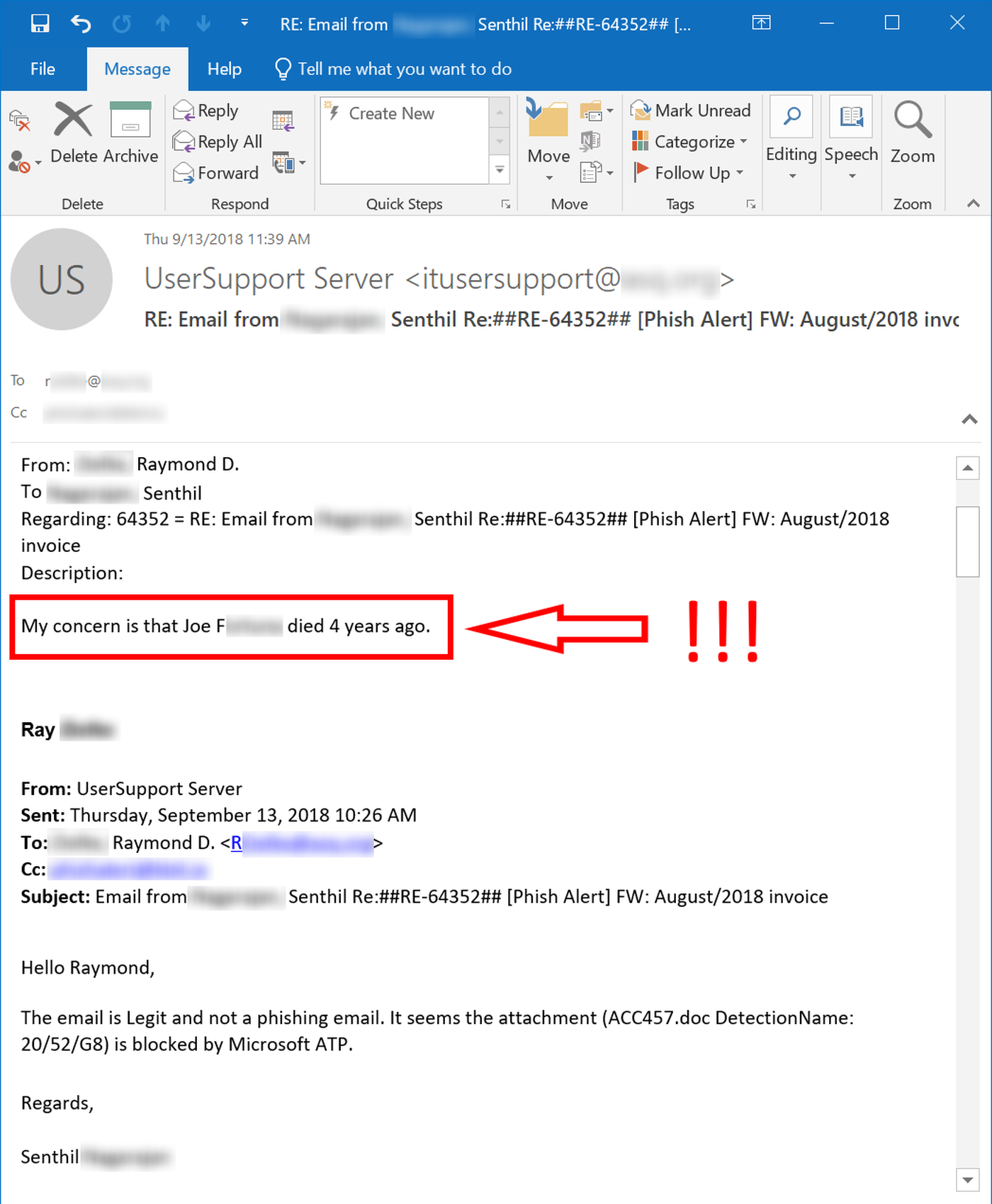
The bad guys have a lot of tricks up their sleeves. Even they, however, haven't quite figured out how to get dead guys to send emails from six feet under.
Users (sometimes) Get a Clue
As depressing as it can be to watch users scoring "own goals" for Team Bad Guys, we do occasionally see signs of hope. Sometimes users do manage to come up with the right answers when the bad guys come knocking -- even if does take a few minutes for the light bulb to blink on.
Consider this user, who received a fairly standard CEO fraud email requesting her to change the direct deposit details for the head of finance.
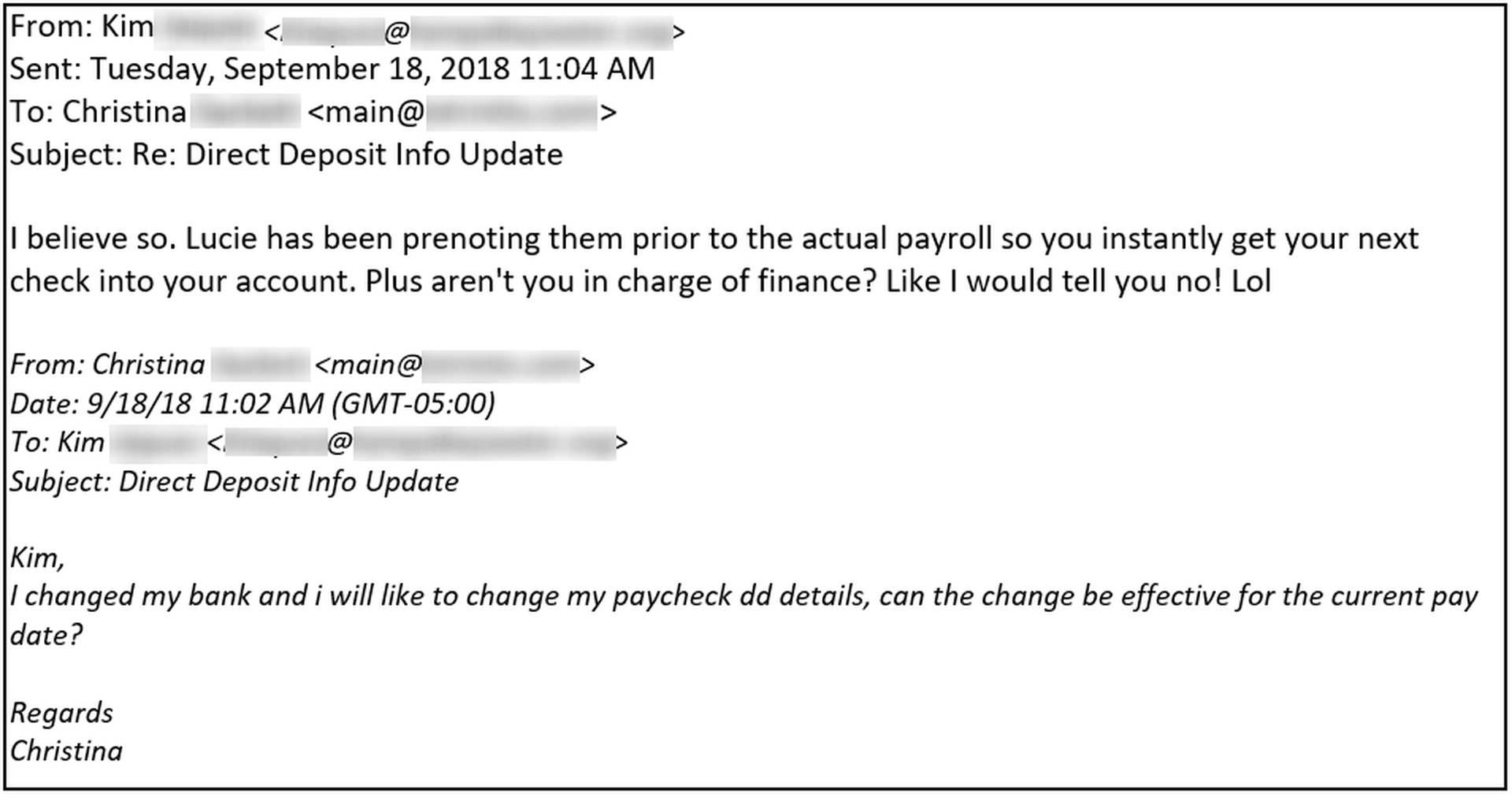
Apparently Kim chewed a bit more on her lighthearted observation -- the proverbial gears turning in her mind -- before deciding to report this phishing email to her IT department via the Phish Alert Button (PAB).
Bad Guys Get a Clue
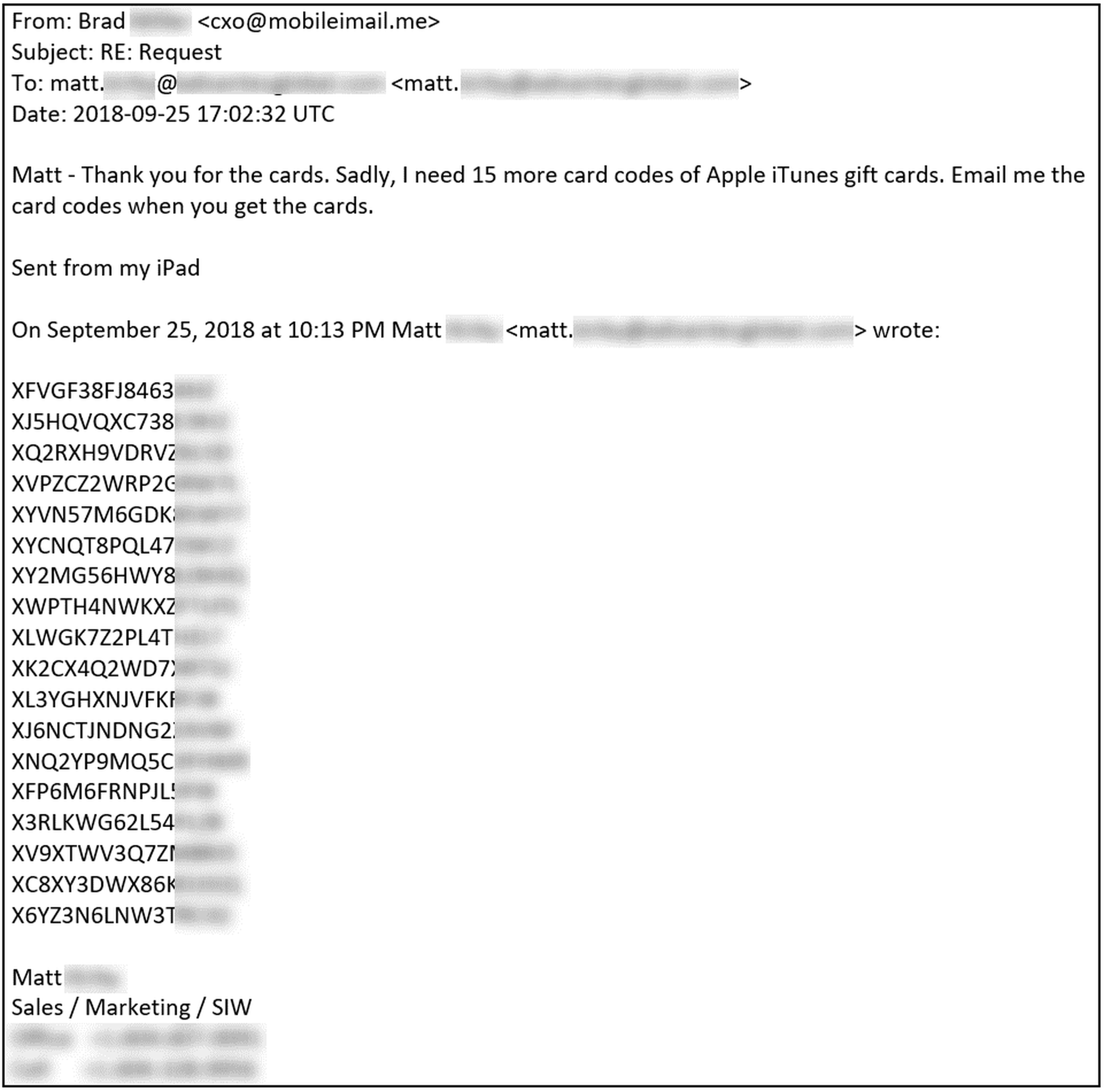
The bad guys can also think on their feet, though. Like poor Ashley, whose encounter with the bad guys we considered earlier, Matt also found himself bamboozled into providing close to $2000.00 in iTunes gift cards to a malicious actor spoofing one of his bosses.
Not being an idiot, the bad guy quickly realized he had hooked a sucker and made the obvious play.
Conclusion
Your users and employees are your organization's greatest strength. Those same employees, however, can also prove to be your biggest headache -- a real life bonified security threat -- if they haven't been properly trained on how to recognize and respond to the malicious emails landing in their inboxes on a daily basis.
Instead of sitting in your office, wondering what your employees and users are doing and dreading the next sign that malware is inside the wire or your company's bank accounts drained, a better course of action is to turn your users into security assets. Step your users through New-school Security Awareness Training, test their resilience in face of threats through simulated phishing campaigns, then give them the tools to report phishing emails directly to your IT department so that you and your users can live in the light instead dreading disaster in the dark.



