An unknown party has been targeting developers of the popular online game Roblox, seeding more than a dozen open-source software packages they use with information-stealing malware called "Luna Grabber."
The campaign, discovered by researchers at ReversingLabs, uses typo-squatting and a number of sophisticated obfuscation tactics to entice users into downloading fake versions of commonly used software on npm, a popular open source software library. While in many cases those packages still contain the legitimate code developers are looking for, they also include a multi-stage malware attack that can deploy Luba Grabber on a victim’s web browser, their Discord application and other sources.
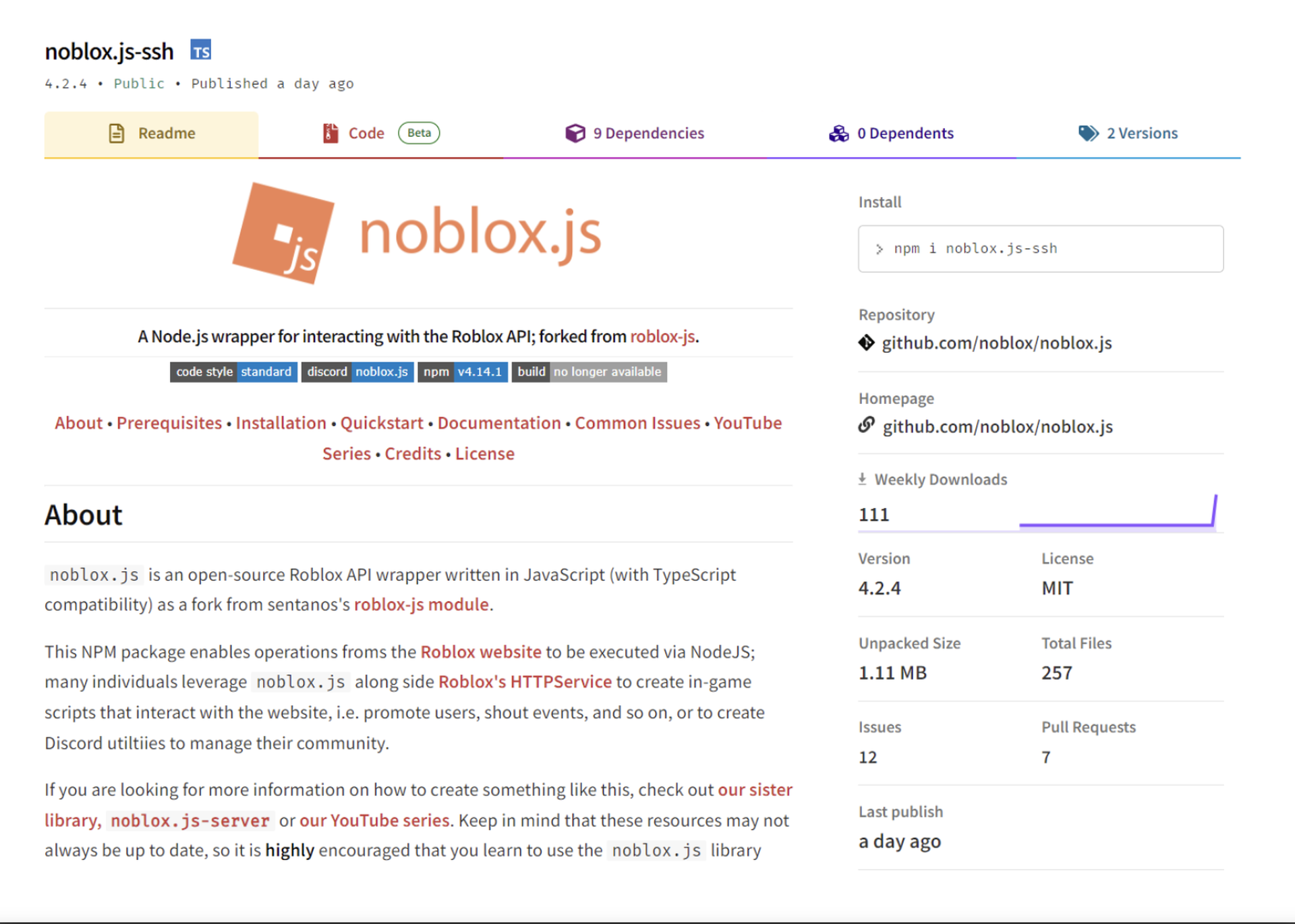
The malware was initially discovered as part of ReversingLabs “routine monitoring” of npm, identifying one such package called noblox.js-vps that was “clearly typo-squatting” the name of a legitimate Roblox API wrapper. In a post published Tuesday, threat researcher Lucija Valentić wrote that the stolen information could potentially be leveraged in future attacks.
“The use of the Luna Grabber ‘turnkey’ open source malware [can] generate malicious executables that act as bait in phishing and supply chain attacks, gathering sensitive information from targeted developers,” wrote Valentić.
Npm is one of the largest open source software repositories in the world, but the observed impact of the campaign thus far has been muted compared with other open source campaigns: just under 1,000 users have downloaded the infostealer across more than a dozen discovered software packages. Many of the identified packages have since been removed, but ReversingLabs noted the campaign remains ongoing.
Roblox is an online video game platform where, similar to games like Minecraft, users can build virtual worlds and levels for others to play in. Since the COVID-19 pandemic, its popularity has exploded: according to data analytics reporting firm DemandSage, the game currently boasts more than 66 million daily active users and 214 million monthly active users.
It’s not the first time that developers of the wildly popular gaming platform have been targeted by hackers. In 2021 another unidentified party used a similar method, typosquatting the noblox.js to deliver ransomware to victims.
Ashlee Benge, director of threat intelligence advocacy at ReversingLabs, told SC Media that unlike many other popular games, the average developer making Roblox levels is likely to be younger, unattached to a larger corporate or business entity and less sophisticated about threats from open-source software.
Years ago, she said there was a similar burst of activity targeting Minecraft developers. Now “the new big thing seems to be Roblox.”
“I think it’s preying on a lot of people who may not have the security awareness to actually vet the third-party libraries they’re using, or they see something and say this is very similar to the package name I was looking for, they must have changed the name,” said Benge. “These aren’t necessarily the targets that would have robust security infrastructure or may be educated enough to even think to evaluate a third-party library.”
It also marks a rare instance of an attacking using npm to carry out multi-stage malware attacks. They have traditionally been more prevalent on other open-source libraries, like PyPi, but as those libraries have introduced new authentication features for developers in an effort to crack down on software supply chain poisoning, malicious actors could be migrating to other repositories in response.
The versions of Luna Grabber malware found so far appear to be oddly constrained in the information they collect. The analyzed samples were only stealing very basic system configuration information, but further examination found that the malicious actors could have been pilfering much more.
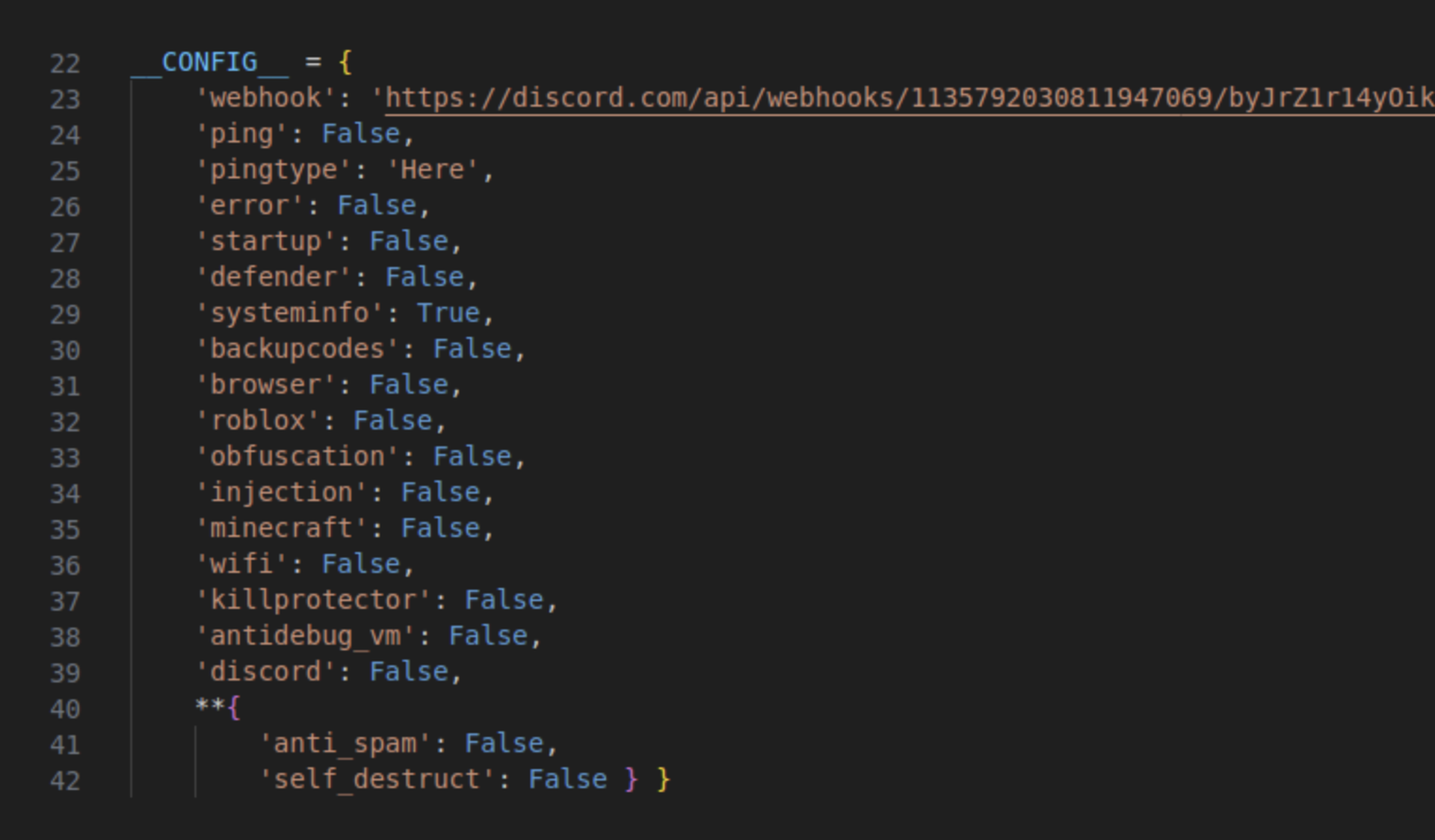
That kind of restraint could indicate a potential testing phase or dry run for a more substantial set of attacks later.
“Usually we see sort of a testing of the waters with these types of attacks, where there will be a small-scale campaign, they’ll sort of sniff out [questions like] ‘what is my reach?’ and ‘what kind of information am I getting?’, ‘who is downloading this?’, ‘what is that they’re running?’” said Benge. “Then afterwards, provided that was successful … there would later be a larger-scale attack that was launched and that would probably look to either extort people of funds or steal sensitive information.”




