Honeypots focused on tracking activity on database servers based in Russia, Ukraine, Poland, the UK, China, and the U.S. found that Microsoft SQL (MSSQL) made up 93% of all attack activity.
In a blog post June 13, Trustwave’s SpiderLabs said its study shows that security teams have to take database security very seriously.
“This means using strong, unique passwords and unusual usernames, using strong and secure authentication, disabling default accounts and enabling multi-factor authentication,” said the researchers
The SpiderLabs researchers said security teams should also keep a close eye on who’s trying to access the system and with which privileges, as well as keeping software up to date and to conduct frequent security audits. They added that the lopsided results around MSSQL convinced them to do another study around MSSQL that will come out later this month.
While the UK had the most MSSQL attacks (21.84%), China (21.49%) was a close second followed by Ukraine (19.52%), Russia (17.54%), Poland (11.54%), and the United States (8.08%). The attacks carried out against MSSQL instances were very intense. According to Shodan, there are over 450,000 MSSQL instances available on the internet with more than 133,000 instances located in China.
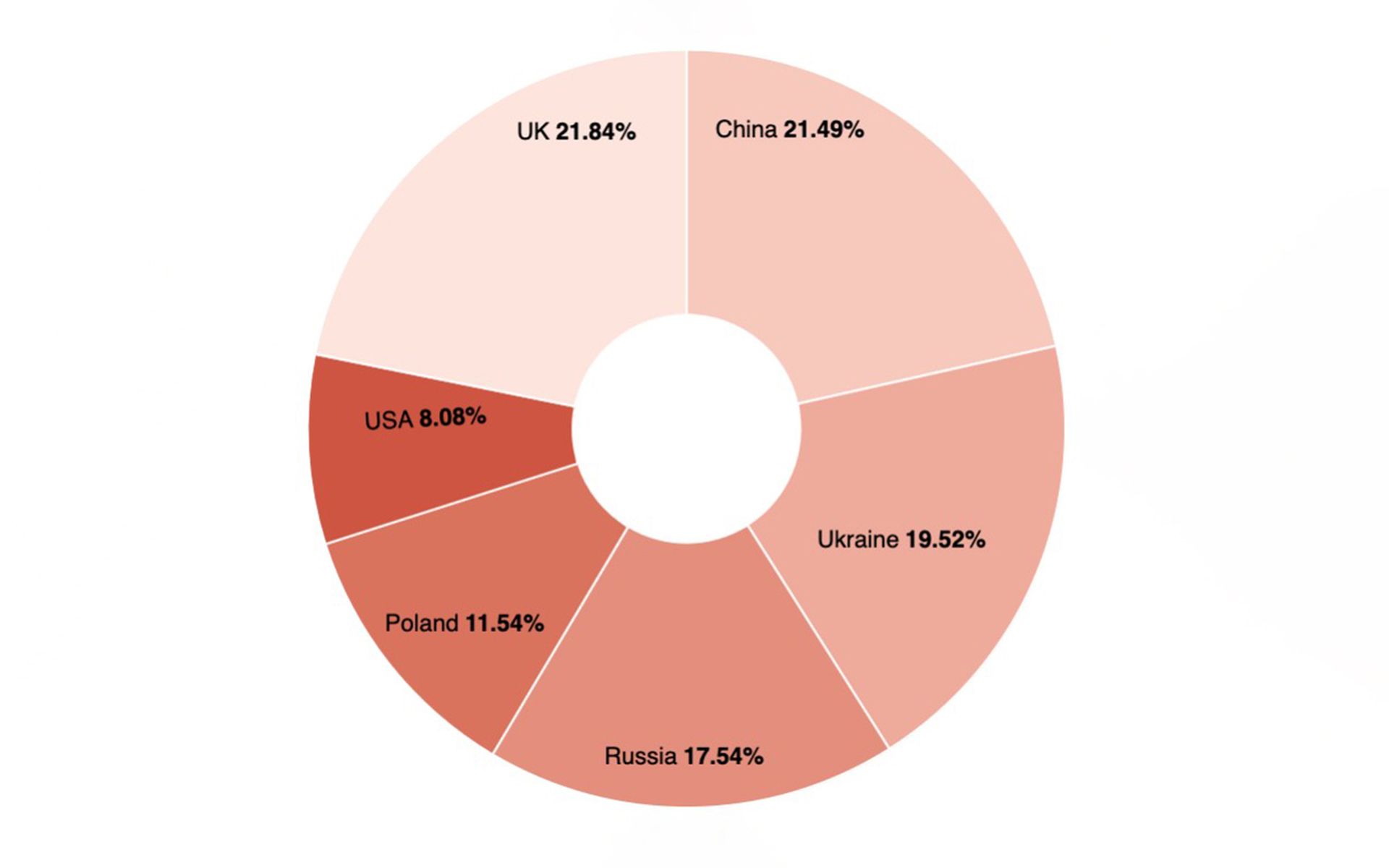
SpiderLabs said it’s possible the UK and China had so many attacks because they are a global communications hub for many industries and corporations. On the other hand, sensors in Ukraine and Russia (the center of the most recent hostilities) have also had a very difficult time with somewhat similar scores.
The researchers were somewhat surprised by the high attack activity recorded on the tcp/6379 port for the Redis database. Redis, the second most attacked database, was launched in 2009, but it’s becoming more popular at companies and also among attackers. According to Shodan, Redis instances are above 270,000, while instances with open port 6379/tcp are above 600,000 — so it makes sense this database has become attractive to attackers.
Along with MSSQL and Redis, SpiderLabs set sensors on the following other databases: MySQL, MongoDB, PostgreSQL, Oracle DB, IBM DB2 (Unix/Win), Cassandra, and Couchbase. The database servers were listening on their default TCP ports.
Setting up such honeypots have become a vital piece of defense intelligence when leveraged correctly and objectively analyzed, said Andrew Barratt, vice president at Coalfire. Barratt said security teams can use this data to offer proof of the ongoing hostility on the internet.
“Often the question of ‘does this really happen’ comes up from executive leaders, and honeypots provide some interesting insights into tactics being deployed that can make the need for cyber defense budgets more real,” said Barratt.
Joseph Carson, chief security scientist and Advisory CISO at Delinea, said the latest blog from Trustwave highlights where cybercriminals have more automation and experience with different types of databases. Carson said attackers tend to try and automate as many known exploits as possible and credential-based attacks so when new databases appear on the public internet the automated bots focus and attack them with increased intensity.
“Less common databases tend to be less targeted, but the attackers who have more experience and get hands on will likely have more success,” said Carson. “So it comes as no surprise that MSSQL is a top target due to its common usage, however, the hope is that the best security practices are in place such as multi-factor authentication, strong privileged access controls and patch management to ensure that all known and common vulnerabilities are patched.”





