In 1904, a German physicist named Christian Hülsmeyer patented the telemobiloscope, an early precursor to what we now call radar. At the time, military leaders were quick to seize on the many advantages that radar brought to detecting enemy aircraft and ships, yet it took decades before the British Royal Air Force put this innovative technology to work successfully to defend itself against German air attacks in the early days of World War II.
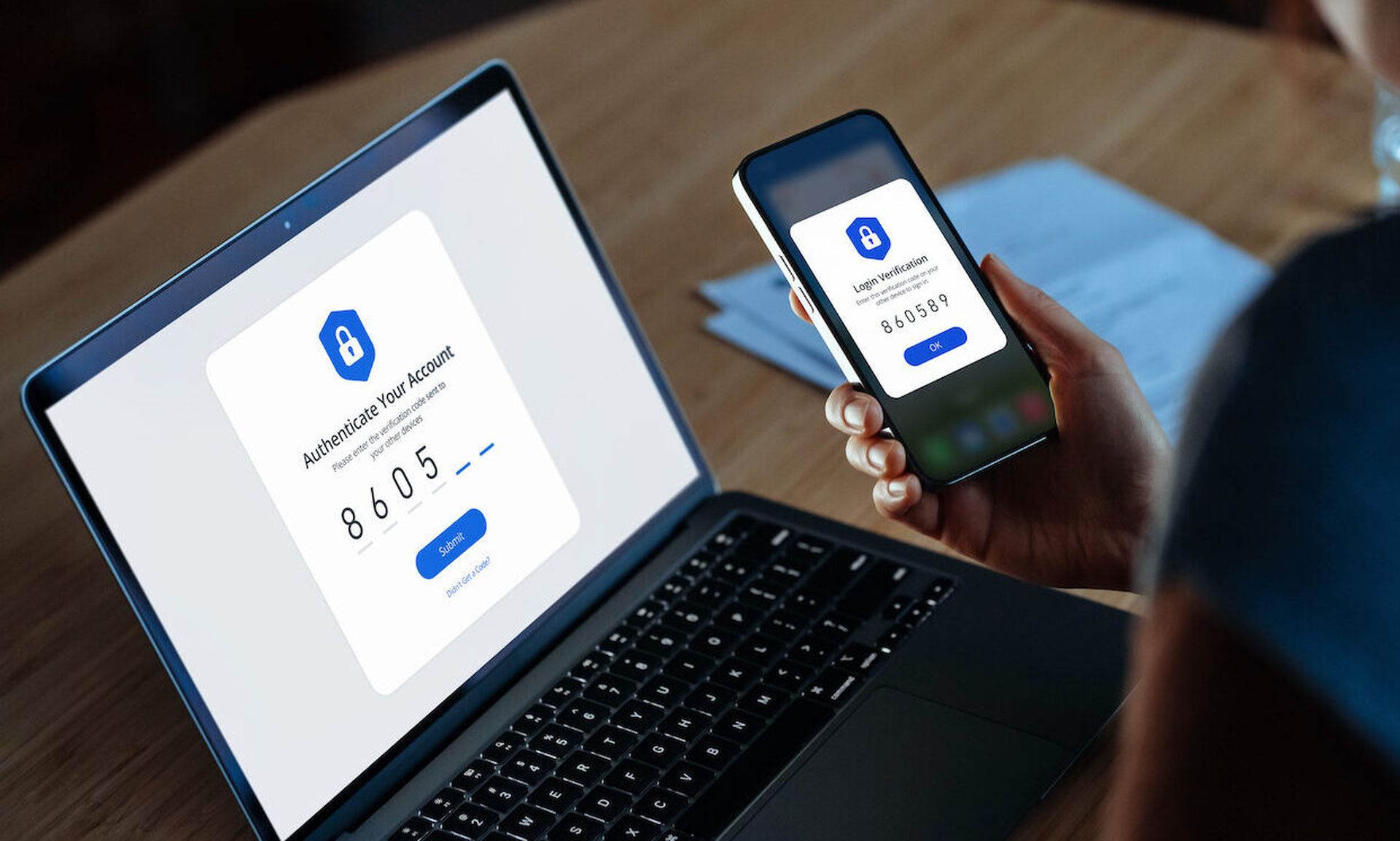
In a similar manner, a surprising number of enterprise organizations today continue to rely on antiquated methods of authentication such as passwords to protect some of their most valuable assets: user accounts and applications. These legacy methods continue to prevail, despite the fact that a superior solution has been available for many years now: multi-factor authentication (MFA).
MFA, which requires a user to verify their identity using more than one factor of authentication (something they have such as a mobile phone, biometric information, or a PIN code) has proven itself as a far superior way to safeguard digital assets and personal information. In fact, when properly configured, MFA blocks 99% of attacks. Yet, despite its undeniable effectiveness, only 38% of enterprise organizations have deployed MFA.
Why MFA adoption has stalled
Every day we see a new story about a business email compromise or an account takeover scam that succeeded in draining the bank accounts of a user. Not only does the consumer suffer financially, but the company likewise bears the brunt of reputational damage when their systems are abused. And in practically every case, these authentication systems are easily bypassed by simple social engineering techniques in which the user unwittingly offers up their credentials.
While most organizations recognize that deploying MFA would dramatically curtail or eliminate these incidents entirely, they continue to delay its implementation because of user experience challenges, cost, and increased technical debt.
Despite these challenges, organizations should strongly consider MFA as a way to thwart cyberattacks that are more sophisticated and frequent. With a few special considerations and strategies, organizations can make MFA much more approachable and easier to implement. Here are four ways to accelerate MFA adoption:
- Make it easy to set up and use: We need to make the process for setting up and managing MFA as simple and intuitive as possible. The more complicated the process, the less likely users will adopt it. Start by offering multiple authentication options to users, such as SMS codes, biometrics, email verification or physical tokens, allowing users to choose the method that best suits their needs and comfort level.
- Educate stakeholders on the benefits of MFA: Too many people still don’t understand the basics of MFA, why it’s important, and why it’s worth the investment. Informed users who understand the security benefits of MFA are more likely to adopt it in the short-term, and also help evangelize its usage.
- Embrace a phased implementation strategy: Because authentication serves as the de facto entry point to the dozens or hundreds of applications that an organization uses every day, it’s often challenging to determine the best jumping off point. Implementing a phased approach allows for better management of the transition while reducing the risk of disruption. It also offers an opportunity to test and refine the new system in a live environment before it’s fully rolled out.
- Complement MFA with risk-based authentication: If users are asked to authenticate with MFA even if they log in multiple times on the same day from the same location, it can cause needless friction that hampers the experience. Depending on the nature of the application and the sensitivity of its contents, consider using risk-based authentication that identifies anomalous user signals before asking for an additional authentication factor. This approach stops attackers getting access to user accounts even if they have gotten past one layer of authentication, while also letting legitimate users in.
Attackers will surely see businesses that continue to rely on obsolescent authentication methods as softer targets. Just as the telemobiloscope represented an early step towards the transformative technology of radar, think of MFA as part of the evolution towards a future where digital security becomes more robust, reliable, and user-friendly. Organizations that embrace modern authentication tactics can more effectively navigate the complexities of our digital age, protecting their assets, and also the trust and confidence of their users.
Slavik Markovich, co-founder and CEO, Descope