| Product: Randori Recon | Category: Attack Surface Management |
| Company: Randori Inc. | Review date: March 2021 |

This review is part of the April 2021 assessment of the Attack Surface Management (ASM) product category. If you haven’t read the category overview, you might want to check it out – it explains the category’s basics, use cases, and the general value proposition. Our testing methodology explains both how we interact with vendors and how we tested these products. In short, ASM products aim to discover and manage an organization’s external digital assets. This approach extends far beyond assets with an IP address, however, including everything from certificates to S3 buckets to DNS misconfigurations.
Company background
Randori was founded in 2018 by Brian Hazzard, CEO, and David "moose" Wolpoff, CTO. With backgrounds in product management, business development, vulnerability research, and offensive security, the pair form a solid team, combining business and technical acumen. The company closed a healthy $20 million Series A just at the beginning of the COVID-19 pandemic for a total of $30 million. The A round was led by Harmony Partners with seed investors .406 Ventures, Accomplice and Legion Capital also participating.
The company employs 30, split between Denver, Colorado and Waltham, Massachusetts. While the company is a bit too young for year-over-year growth rates to be meaningful, Randori’s strong early traction could show promise for the ASM market. We will be interested to see in the next few years if this traction is due to a strong general interest in ASM, or if the flexibility of Randori’s particular approach to this market is what sets it apart (more on that in the product review).
Review summary
The most notable aspect of Randori’s platform is that it is split into two parts: Recon and Attack. Recon is a fully automated SaaS product that gathers information about a company’s exposed digital assets through both passive and active methods. Recon is the product we’ll be focusing on for this review, as it most closely resembles the other ASM products we’re testing in this market. Recon hit the market a little over a year ago, in February 2020.
Randori’s other product, Attack aims to go deeper with Recon’s findings. Customers can request attacks on specific findings, which will queue them up for Randori’s ‘HOC’ (Hacker Operations Center) to look at more closely. This HOC is made up of offensive security experts who effectively perform miniature penetration tests as requested by customers.
The Attack offering makes a lot of sense, as finding staff and budget to validate controls can be a challenge. As with many other modern security products, false positives are a key challenge for ASM – a challenge humans are still best-suited to solve, regardless of what the machine learning cognoscenti may claim.
Randori's overall approach can be described in a few steps. The first two steps are common across nearly all ASM vendors, but after that, Randori's own approach and IP is leveraged to narrow the list down to items that are truly concerning and justify a sense of urgency.
- Customer provides some base data to start with.
- Randori discovers core assets and expands outward.
- "Attackable" components are identified.
- The Target Temptation score is applied and used to prioritize.
- Customers review findings and approve findings they want to authorize for further validation
- Automated processes attempt to exploit these findings. If successful, Randori's Hacker Operations Center will attempt to move laterally and achieve predefined objectives.
Steps 1-4 are part of Randori's Recon product, while steps 5 and 6 are part of the Attack product, which aims to validate findings using experienced penetration testers.
Target market: mid-to-large enterprises that don’t have the skills or time to perform regular reconnaissance, or organizations looking to reduce time spent on manual recon activities.
Time-to-value: 30 minutes for initial account setup and team configuration; a few hours before initial results become available. Expect to spend 8-16 hours digging through initial results, which will vary depending on the size of the organization’s external footprint.
Maintaining value: Expect to spend 2-4 hours per week reviewing new findings as notification emails arrive.
Total cost: Pricing is an annual subscription based on number of employees. Randori declined to share specific pricing information, but we can still estimate labor costs. In a mid-sized enterprise (100-2,000 employees), we’ve estimated four hours of junior analyst time, two hours of analyst time and one hour of senior analyst time to do the initial analysis of Randori results and configuration of the tool. Based on our average salary estimates, this labor totals $302.87. For ongoing analysis work, we’ve estimated two hours of junior analyst time per week, which totals $3,499.60 per year.
Strengths: Nice filtering system. Automated tagging is innovative and useful. Ability to set status, affiliation, and impact aid management. The ability to queue discrete items for attack by the Hacker Operations Center (HOC) is unique in this market. IPv6 findings are innovative.
Weaknesses: No ability to leave notes for other team members. User experience can be a bit confusing at times - clicking links can lead around in circles. Limited asset types – very IP/host focused.
Conclusion: For anyone focused on identifying and reducing attack surface quickly, Randori should be on your shortlist.
Deployment and configuration
When an account is created, the necessary resources are provisioned automatically. Recon is entirely SaaS-based – initial setup and configuration activities can be done in a few minutes. Recon is one of only two ASM products tested that requires a second factor (TOTP in this case) to be set up during the account creation.
The Randori platform is initially seeded with a single domain. It’s possible to add additional networks, domains, or hostnames as needed in the settings menu. Additional team members can also be added in the settings menu. Four roles are available: Recon, Attack, Admin, and Observer. The first two control access to Randori’s two primary products. The latter two control whether the account can manage settings and whether the account is read-only.
Usage
After logging in, Randori presents the dashboard, which is a well-organized mix of high-level statistics and high-profile findings. In a big red box, "Top Priorities" are listed.
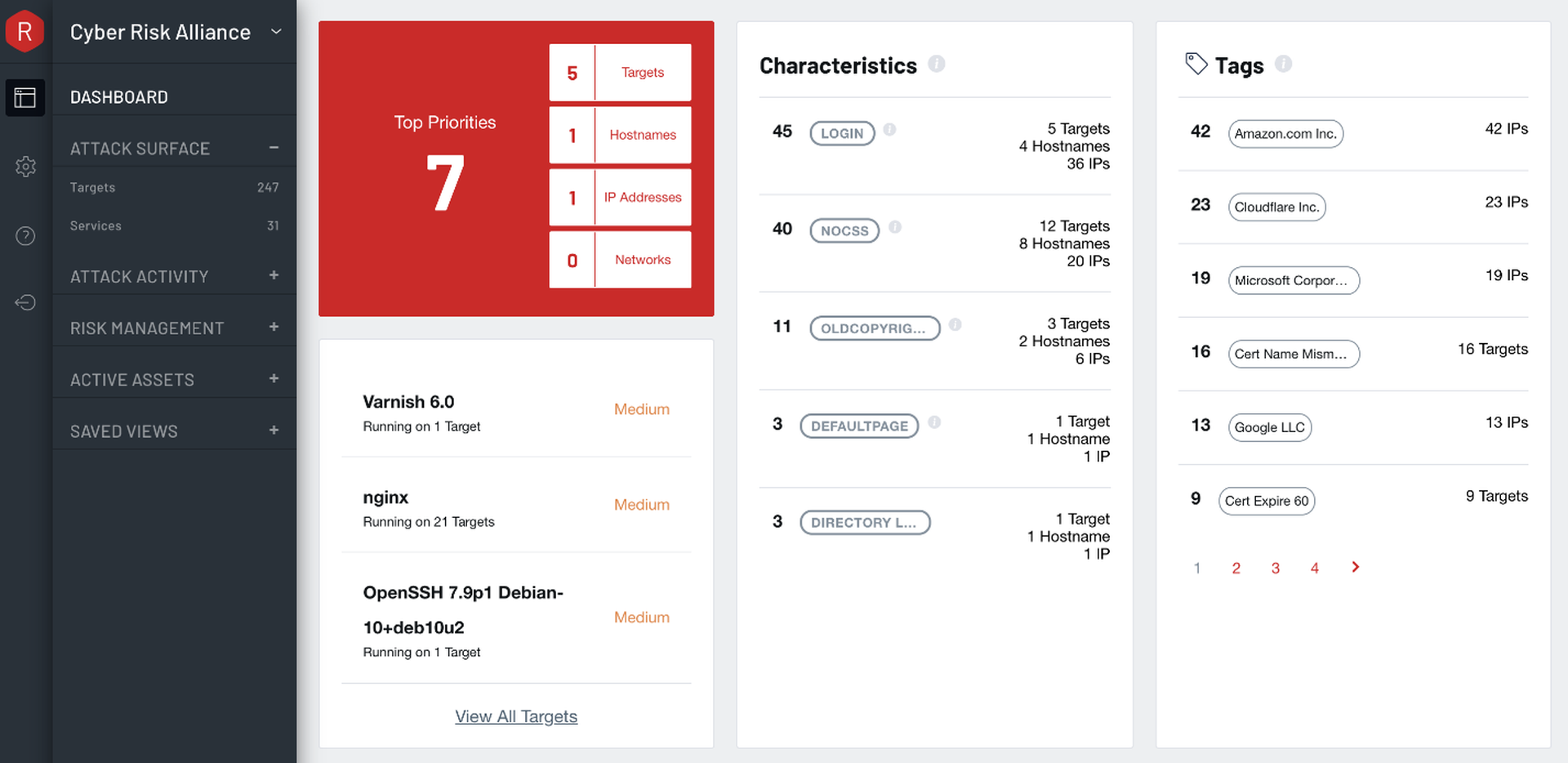
Immediately, on this screen, we can see the number of targets and services discovered. In addition to top priorities, we can see a few of the more highly rated findings. Most of all, we see that tags are broadly used in the product (and to good effect).
The automatically-applied tags are of particular interest. Under the heading of Characteristics is a mix of tags that would interest any penetration tester or red teamer. Websites with elements that provide valuable attack surfaces (login pages) or that signify an unmanaged or abandoned property (default pages, directory listings) are tagged accordingly. Some clever ideas show up here as well. A site tagged as having no cascading style sheets (CSS) could signify a bare-bones configuration interface with default credentials. An old copyright in the page footer could suggest an abandoned server running old, vulnerable software.
The final column on the dashboard screen introduces a different kind of prepopulated tag – one that identifies assets that belong to popular cloud services. These tags also include certificate status (e.g. expired, about to expire)
The remainder of the dashboard focuses on summaries and historical trends. Randori's Target Temptation scores are useful, indicating the likelihood an asset would attract an attacker’s attention. This approach is similar to some of the work vulnerability prioritization vendors like Kenna have done. Randori has a patent pending on its approach to calculating these scores.
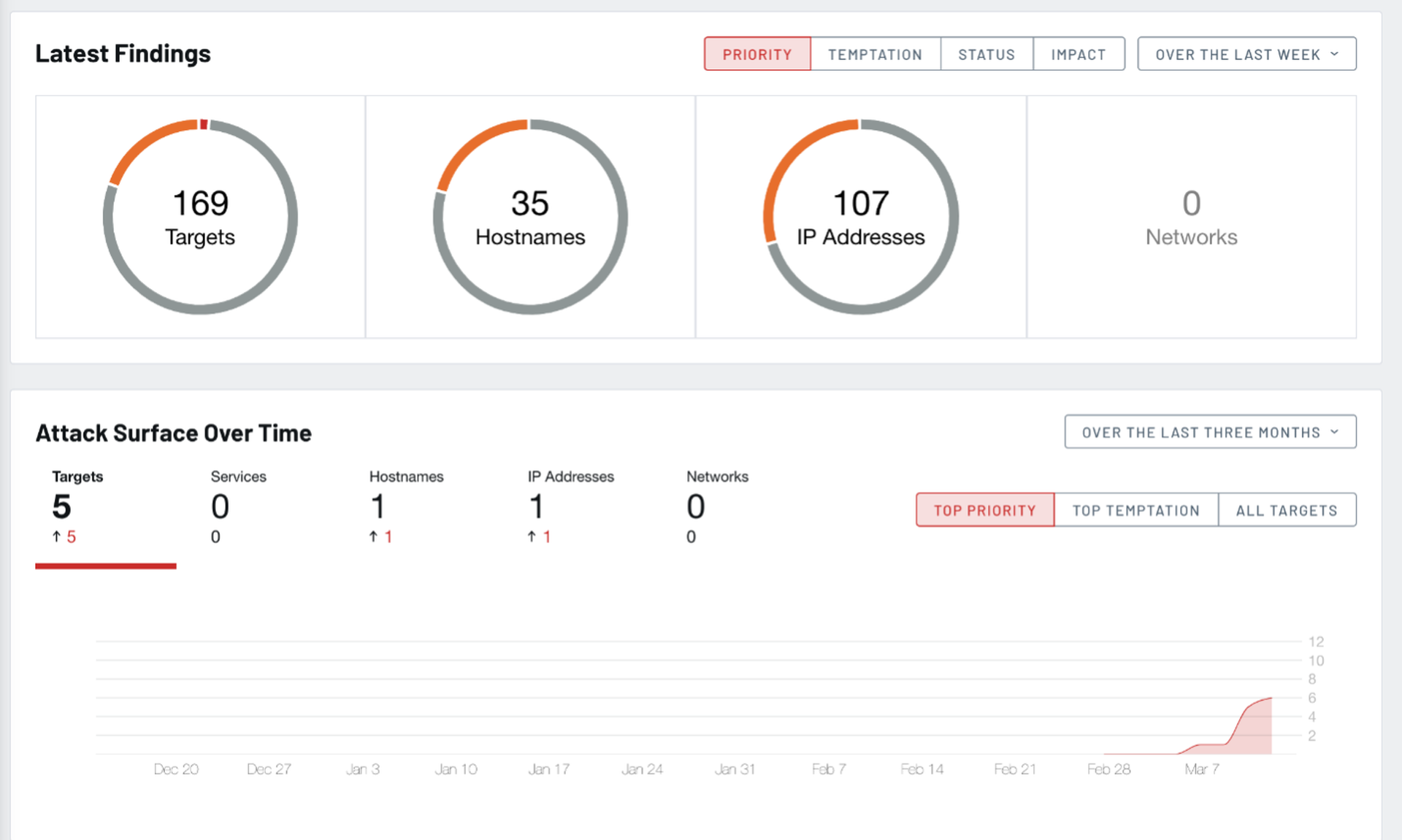
Getting down to business, clicking most things on the dashboard, or on the left-hand navigation pane brings us to a list view for each type of element: targets, services, hostnames, IP addresses, networks, and people (social reconnaissance for phishing campaigns). The header for each list contains some useful information - notably a summary of the selected list and any active filters or sorting.
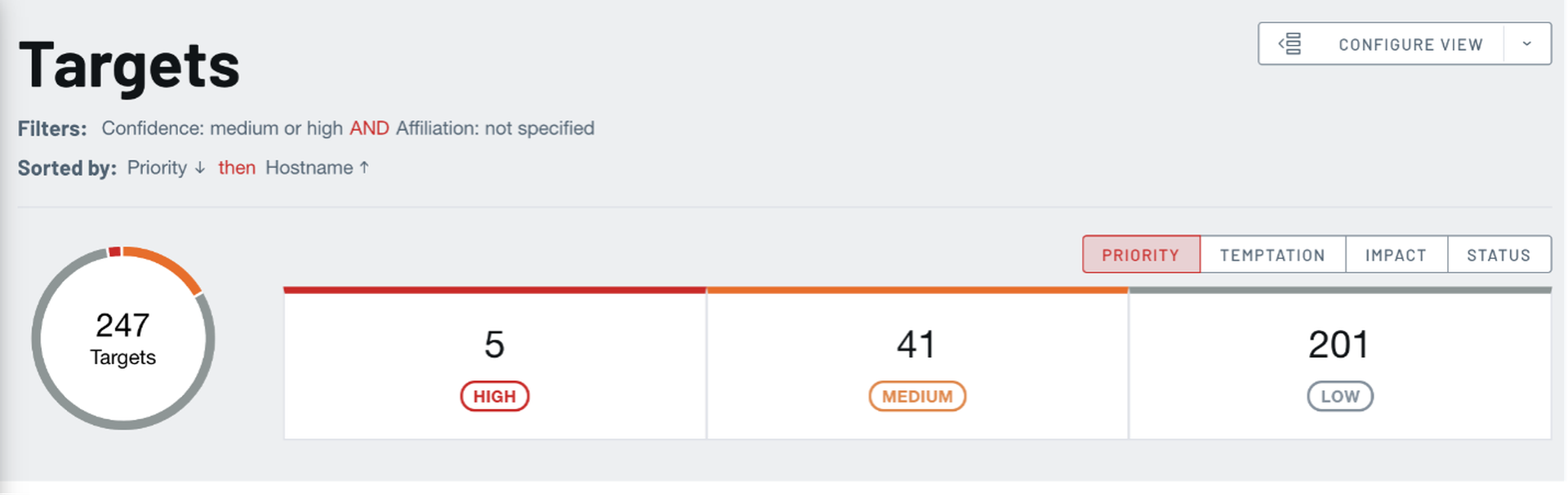

Filters and sorting are capable and essential here, especially when the list of findings gets large. Commonly used filters can easily be saved for easy access later.
The list itself is also quite flexible. Columns vary depending on the type of list, but most include status, impact and tags, which are useful for initially organizing findings. The Targets list additionally includes a thumbnail of website screenshots and details of software, versions, domain names and IP addresses.
Tags are freeform and can be used to group findings, making it easy to filter on tags later on. Impact is a classic low, medium, high qualifier that is similar to an asset criticality score you might see in an asset or vulnerability management product. Statuses make it easy to apply decisions and next actions to findings. The default statuses include: needs investigation, needs resolution, needs review, accepted and mitigated.
It's also possible to unaffiliate findings if they're determined to be false positives (or re-affiliate when mistakes are made).

In any screen, the plus (+) beside every entry expands to display additional information. This information includes first and last seen dates, tags, characteristics and description of the target. Particularly useful are three additional elements: a breakdown of the Target Temptation score and its makeup, custom notes from Randori's offensive security experts and the discovery path.
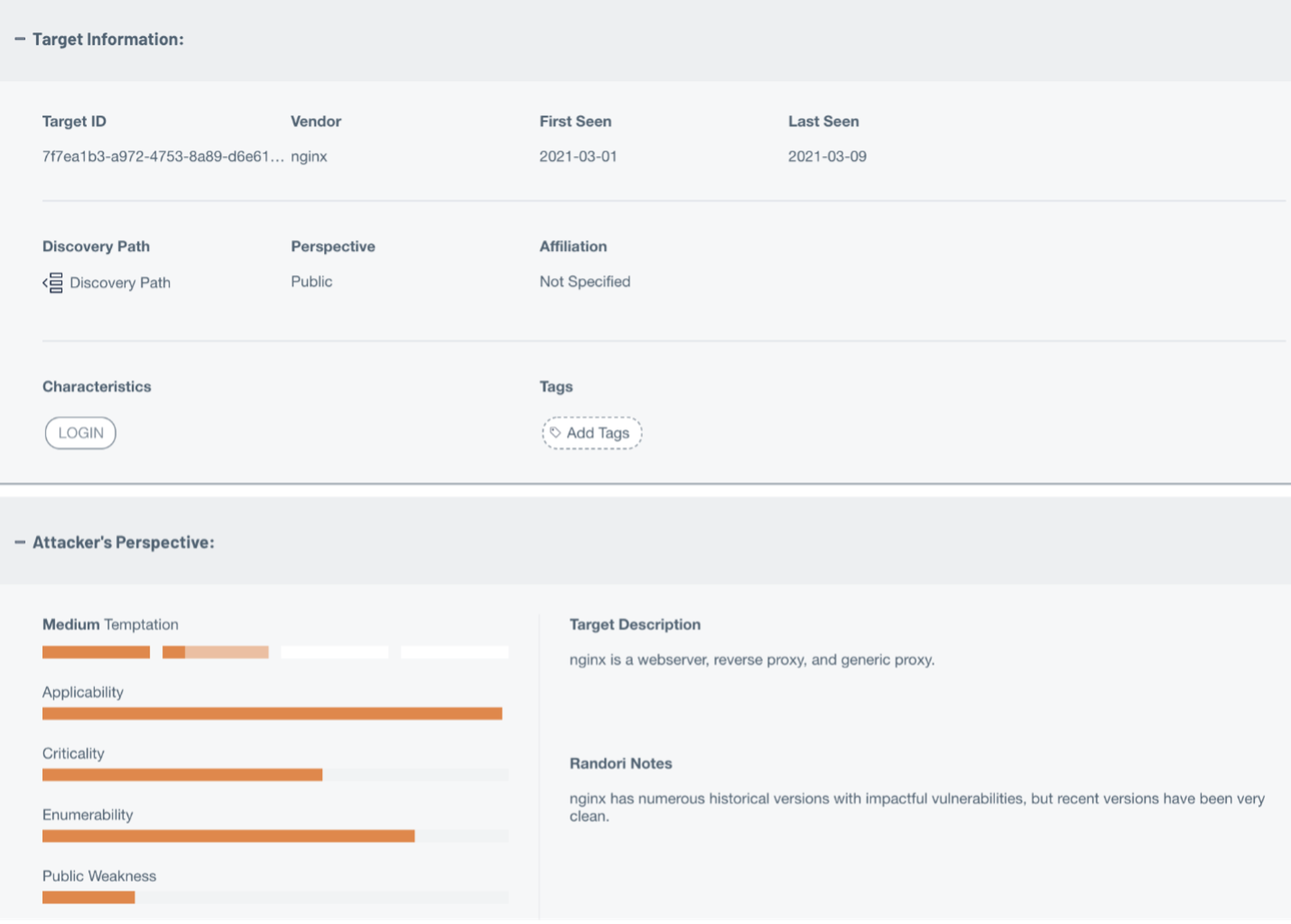

The discovery path is particularly useful when trying to determine the legitimacy of a finding. Since Randori uses a multitude of techniques to discover attack surface, it's important to understand how it arrived to a particular element. The discovery path lists both the assets and techniques used to get from point A to point B (and points C and D, and so on).
Maintenance
Plan to spend between one and four hours per week investigating new attack surface findings, depending on the size of your organization’s Internet footprint and the rate of change to it.
Randori sends weekly email digests summarizing any new assets discovered. Immediate alerts are sent for any high priority findings.
Notable Integrations
- Axonius (asset management)
- LogicHub (SIEM/SOAR)
- Splunk (SIEM/SOAR)
- ServiceNow (ticketing)
Support
Randori offers 24/7 support and a dedicated customer success manager. This dedicated manager will be the primary point-of-contact for any requests, questions or issues. The onboarding process includes a kickoff call of sorts, where the customer is introduced to their customer success manager and receives some initial training on using the product. This is after the customers’ console has been populated with some findings, making the training more effective, since the customer gets to work within their own environment.
In our experience, a 30-minute hands-on walkthrough of the product can massively reduce support issues and questions down the line. We recommend customers always take the time to go through these introductions and take advantage of them when offered.
Pricing
Randori Recon is available with an annual subscription based on company size (measured by employee count). Randori Attack is available as an add-on subscription. Randori did not share specific pricing information.
Security program fit
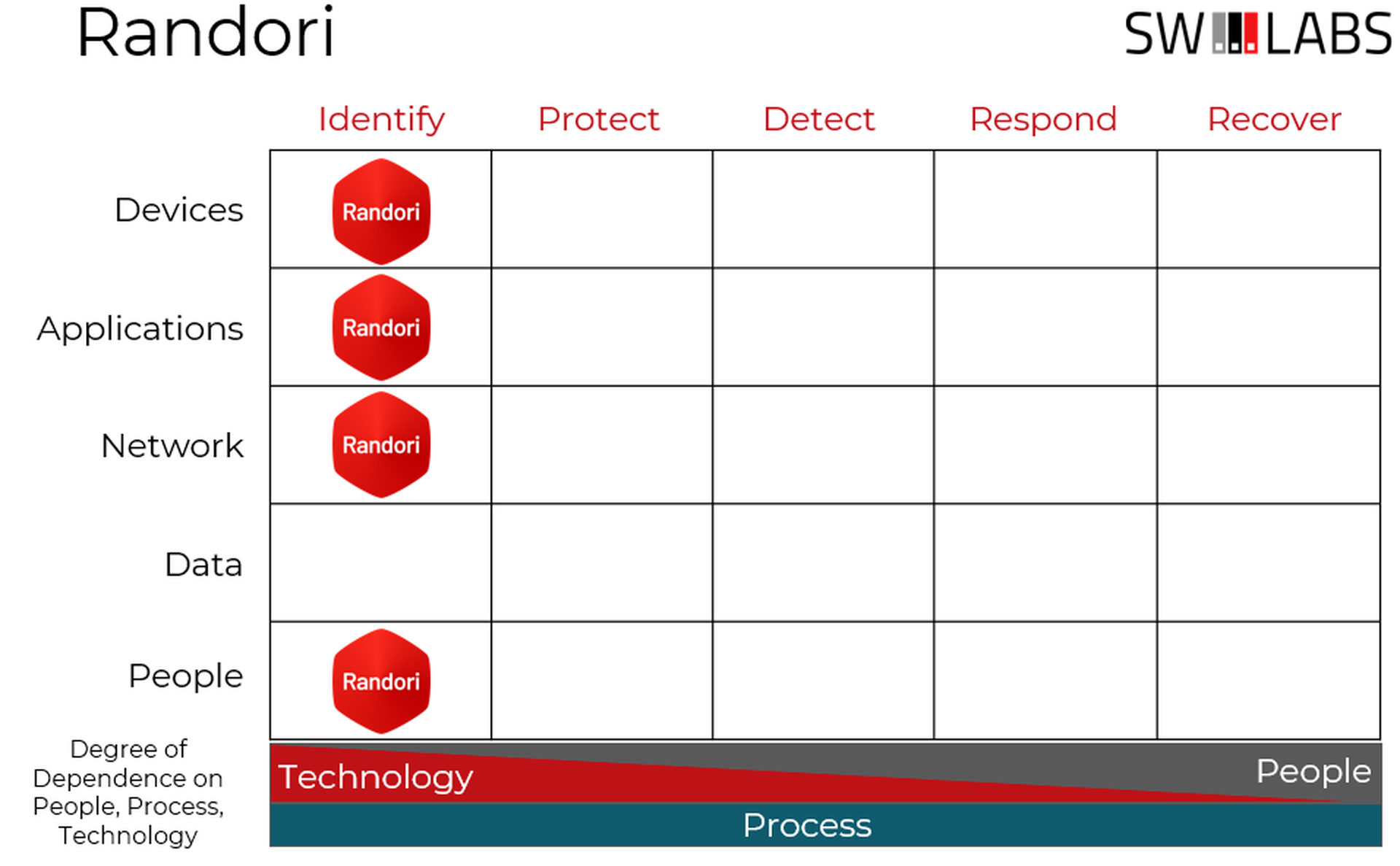
Randori Recon, like other products focused on discovering vulnerabilities and misconfigurations, fits solidly within the Identify column of the Cyber Defense Matrix.
Conclusion
While Randori might not collect as many types of assets as some competitors, their prioritization capabilities and ability to pull insights from the assets that are collected make it worth a look. Additionally, if you have a real need to validate findings or add offensive security capabilities, the ability to add on the Randori Attack product should push this one to the top of your list.



